Exploring Virtual Private Clouds (VPC) in AWS: The Backbone of Secure Cloud Networking
 Jasai Hansda
Jasai Hansda
At the heart of this secure and efficient cloud networking lies the concept of Virtual Private Clouds (VPCs) in AWS.
An Analogy
Imagine a Gated Community Within the Cloud City
Think of a bustling metropolis – that's the AWS cloud infrastructure. A VPC is like a gated community within this city, offering a dedicated space for your resources. This gated community analogy perfectly captures the essence of a VPC:
- City = AWS Cloud: The entire AWS cloud infrastructure represents the city, with various resources like compute power, storage, and networking spread across different zones.
- Gated Community = VPC: Your VPC is a secure, isolated section within the city, specifically designed for your resources. Just like a gated community provides controlled access for residents, a VPC offers a dedicated and secure space for your cloud resources.
- Security Gate = VPC Security Groups: The security gate at the entrance of the gated community functions similarly to VPC security groups. These groups define who (incoming traffic) and what (specific ports and protocols) can access your resources within the VPC. Just like the security gate controls who enters the community, security groups define which traffic is allowed into your VPC.
Individual Houses = Subnets: Imagine each house within the gated community as a subnet. VPCs are divided into subnets, each associated with an Availability Zone (AZ), which acts as logical subdivisions within your VPC. You can assign specific security policies and launch resources within these subnets based on their function. Similar to how different neighborhoods within a gated community might have specific rules or restrictions, subnets allow you to segment your resources within the VPC for enhanced security and organization.
- Private Roads = Private IP Addresses: The private roads within the gated community represent the private IP addresses assigned to resources within your VPC. These private IP addresses are not publicly routable and can only be accessed from within the VPC, ensuring the privacy of your resources. Just like residents within a gated community have private addresses for their homes, your resources have private IP addresses within the VPC.
- Internet Gateway (Optional) = Controlled Public Access: An internet gateway in a VPC is like a single guarded entry point from the gated community to the broader city. It allows controlled access to the public internet for specific resources within the VPC if needed. While the community is private, a controlled access point (internet gateway) can be established to allow residents (resources) to interact with the outside world (internet) under certain conditions.
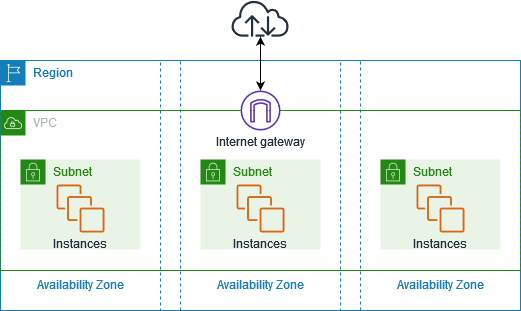
The Journey of Data through an Internet Gateway
In an AWS VPC, the maximum number of subnets you can create depends on the address prefix size (CIDR block) you choose for your VPC. Understand CIDR
Understanding the flow of data through an Internet Gateway provides insights into its crucial role in network communication:
Outbound Communication: When a device in the private network starts communication with an external server on the Internet, the data goes through the Internet Gateway. The Internet Gateway performs NAT, assigning the communication a public IP address and forwarding the data to the destination server on the Internet.
Inbound Communication: External entities on the Internet that want to communicate with devices in the private network send data to the public IP address linked to the Internet Gateway. The Internet Gateway, based on its routing and firewall rules, directs the incoming data to the appropriate device within the private network.
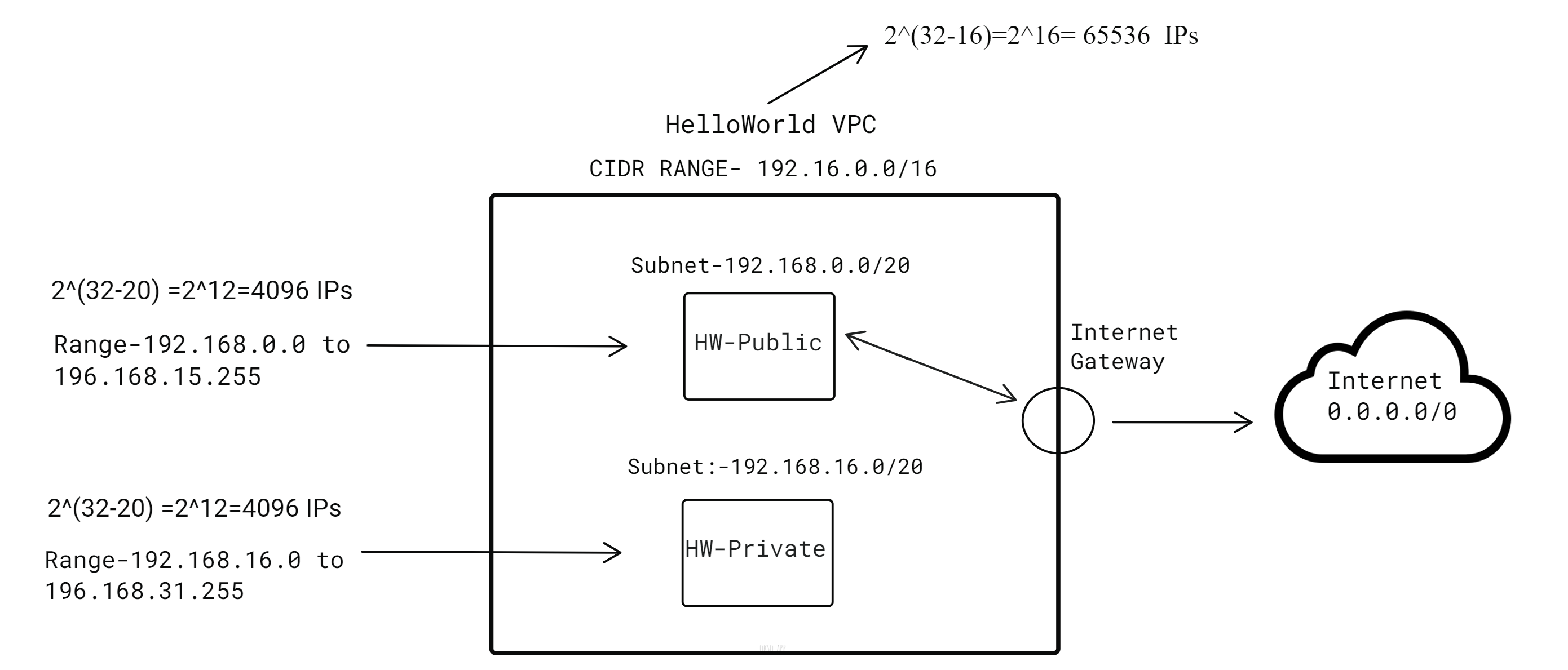
Let's see this example:
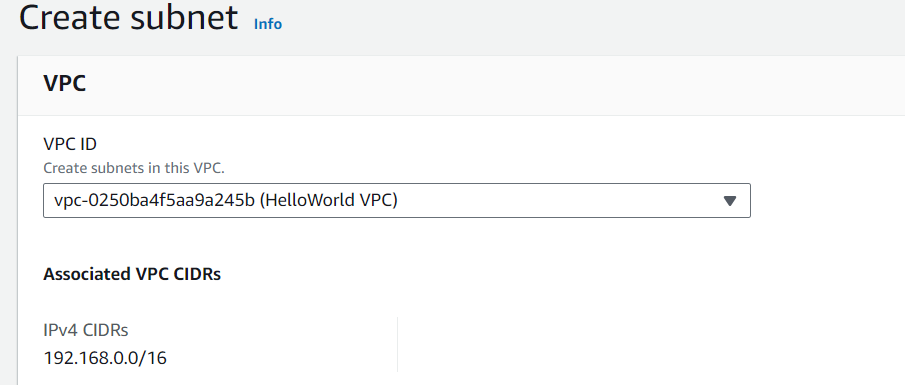
We can observe the HelloWorld VPC, which has a designated IP address range. This range is defined by a CIDR block, 192.168.0.0/16, allowing for a large number of IP addresses within the VPC (65,536 IPs in this case).
The HelloWorld VPC is structured to include multiple subnets, each with its own range of IP addresses. In this case, we have two subnets named HW-Public (192.168.0.0/20) and HW-Private (192.168.16.0/20). (These names are just for identification purposes; they do not make any subnet public. All subnets work within its private network.) Subnet Calculator**-**Calculate the IP range.
Determining the Number of Hosts on a Subnet
These subnets can be spread across different availability zones to ensure high availability and fault tolerance.
Within the HelloWorld VPC, private subnets are used to host resources that do not need direct access to the internet, such as databases and application servers to enhance security. In this case, HW-Private is the subnet that does not have any direct access to the internet.
On the other hand, public subnets are configured with a route to an internet gateway, allowing resources like web servers to communicate with the outside world. In this case, HW-Public becomes a public subnet when configured with an internet gateway.
The internet gateway connects the VPC to the internet, controlling the flow of data in and out. When a resource in a public subnet needs internet access, the data goes through the internet gateway. This gateway ensures that only authorized traffic is allowed, providing a secure and controlled access point.
By carefully designing the HelloWorld VPC with appropriate subnets and an internet gateway, we can achieve a balance between security and accessibility. This setup allows for efficient network communication while protecting sensitive resources from unauthorized access.
How a Subnet Knows It's Attached to an Internet Gateway in a VPC
A subnet in a VPC itself doesn't directly "know" if it's attached to an internet gateway. Subnet information is stored in a separate entity called a route table. The route table associated with the subnet dictates how traffic is routed within the VPC and to the internet (if applicable).
Here's how it works:
Route Tables: Each subnet in a VPC is associated with a route table. This table contains a set of rules that define how to route traffic for different destinations.
Route Entries: A route entry specifies a destination (CIDR block) and the target (next hop) for reaching that destination.
Internet Gateway Route: For a subnet to access the internet, the route table must have a specific route entry. This entry typically has a destination of "0.0.0.0/0" (representing all internet traffic) and a target of the VPC's internet gateway.
Let's write a route table for above example:
Route Table for HW-Private subnet-
| Target | Destination |
| LOCAL | 192.168.0.0/16 |
The route table for the HW-Private subnet includes only a local route, which directs traffic within the VPC's IP range (192.168.0.0/16). This ensures that resources within the HW-Private subnet can communicate with other resources in the VPC but do not have direct access to the internet.
Route Table for HW-Public subnet-
| Target | Destination |
| LOCAL | 192.168.0.0/16 |
| Internet Gateway(IGW) | 0.0.0.0/0 |
The route table for the HW-Public subnet includes both a local route for internal VPC communication and an additional route that directs all internet-bound traffic (0.0.0.0/0) to the internet gateway. This setup allows resources in the HW-Public subnet to access the internet while maintaining internal communication within the VPC.
Creating a Virtual Private Cloud (VPC) in AWS
Creating a VPC in AWS involves several steps, each essential for setting up a secure and functional network environment. A VPC allows you to launch AWS resources, such as EC2 instances, in a virtual network that you define. Here’s a detailed guide to creating a VPC in AWS:
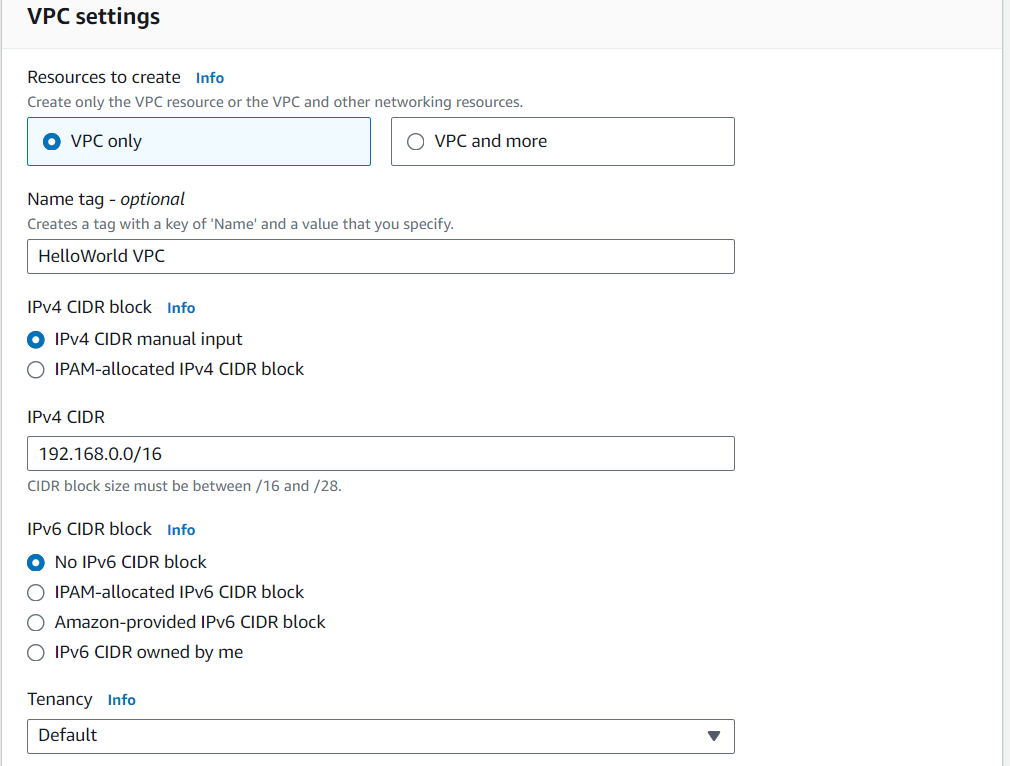
Step 1: Create the VPC
Navigate to the VPC dashboard in the AWS Management Console.
Click on "Create VPC."
Provide a name for your VPC and specify an IPv4 CIDR block (e.g., 192.168.0.0/16).
Optionally, you can assign an IPv6 CIDR block.
Choose the tenancy option (default or dedicated).
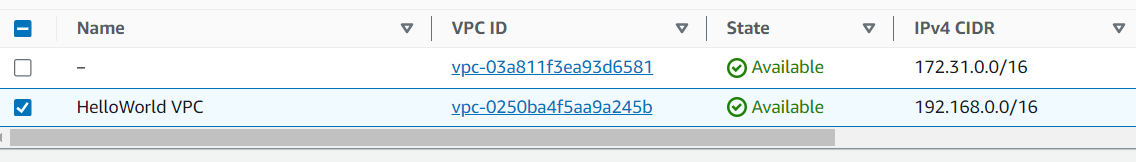
VPC Created
Step 2: Create Subnets
After creating the VPC, you need to create subnets to segment your network.
Click on "Create subnet" and select your VPC from the dropdown.
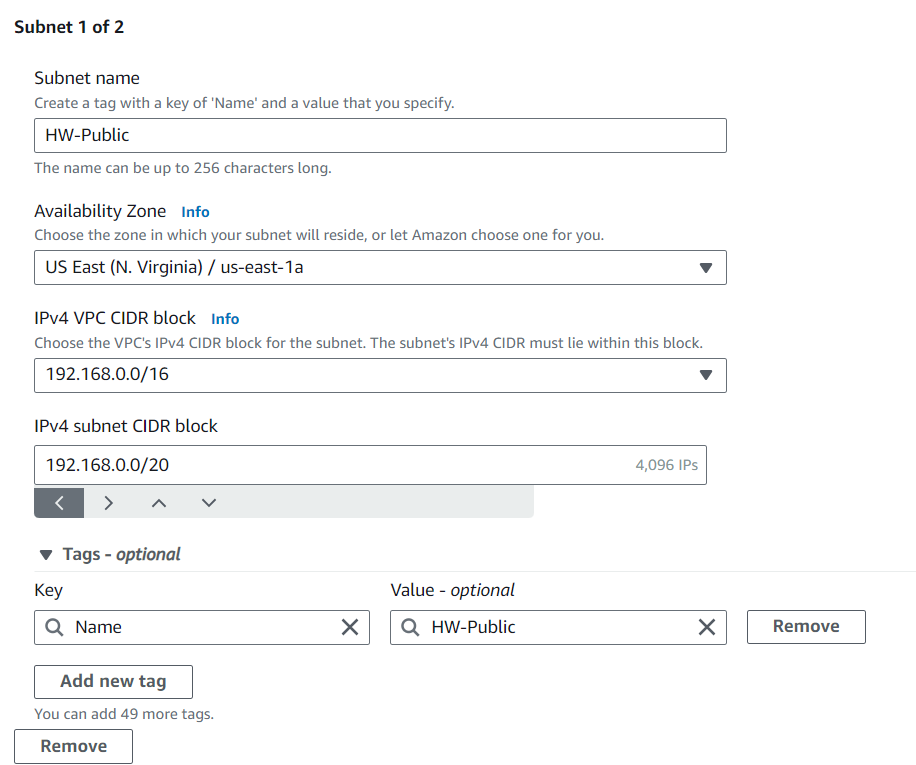
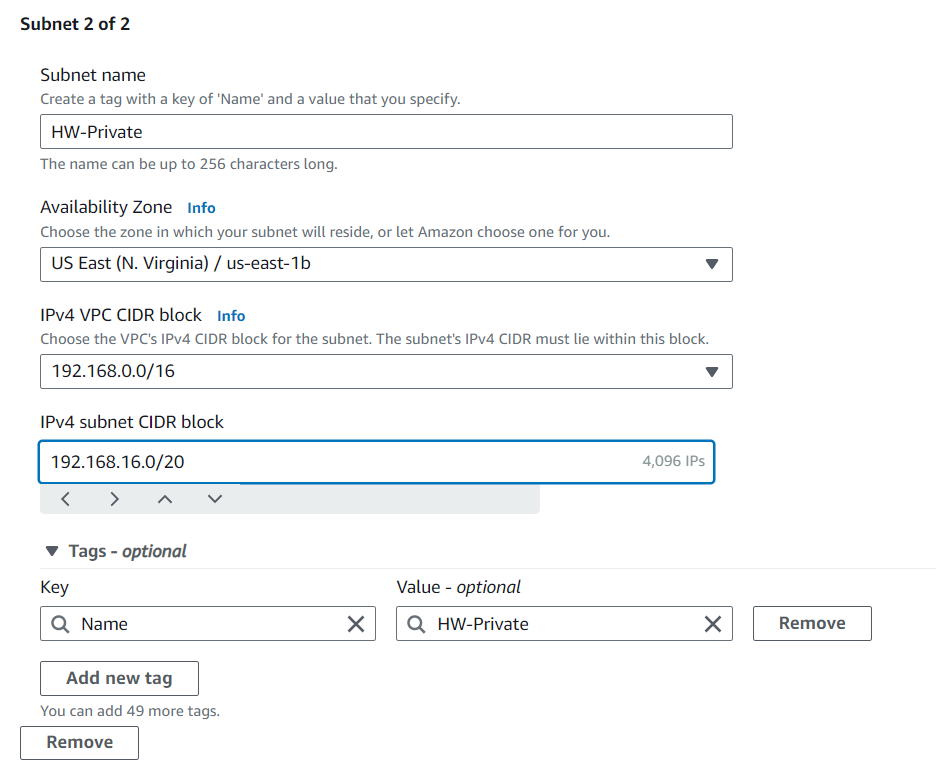
Specify a subnet name, availability zone, and IPv4 CIDR block (e.g., 192.168.0.0/20 for a public subnet and 192.168.16.0/20 for a private subnet).
Repeat the process to create additional subnets as needed.
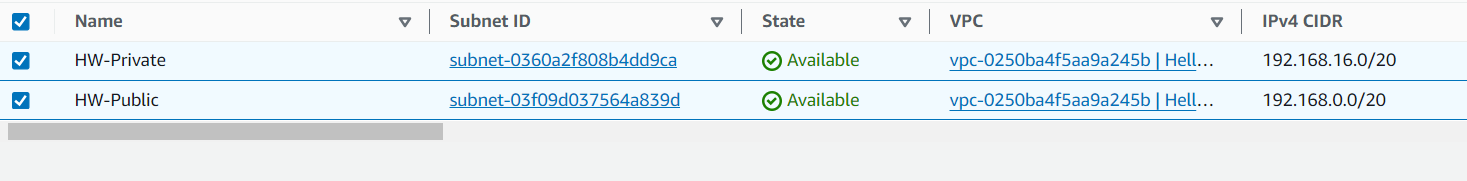
Subnets Created
Step 3: Internet Gateway
To enable internet access for your public subnet, create an Internet Gateway (IGW).
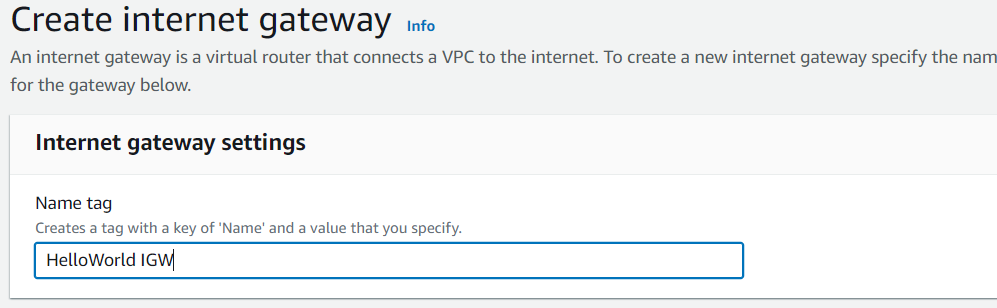
Attach the IGW to your VPC.
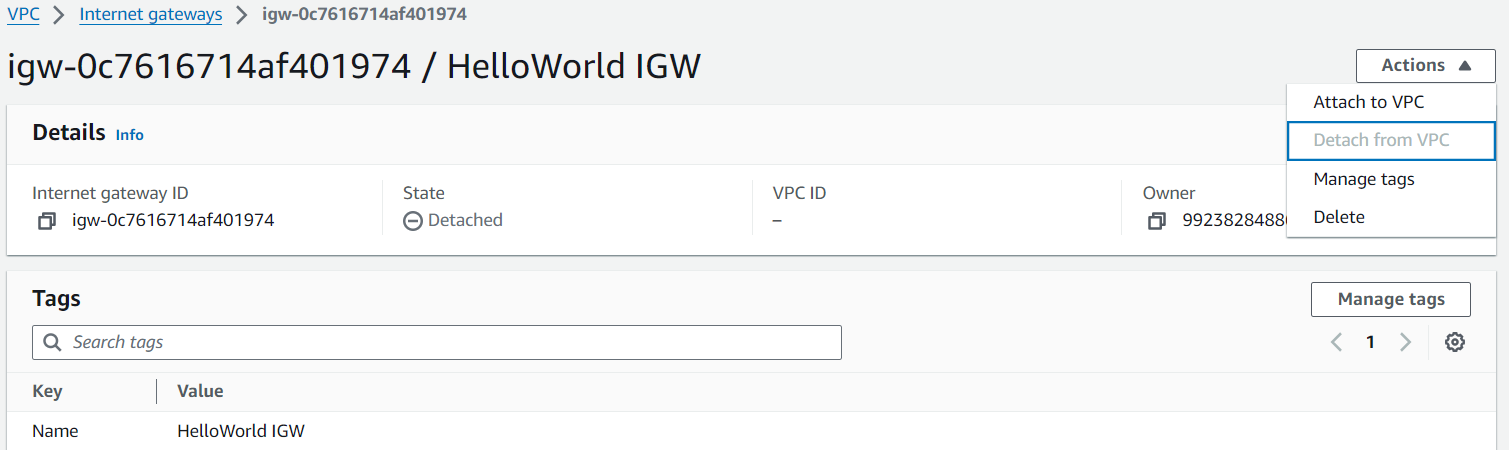
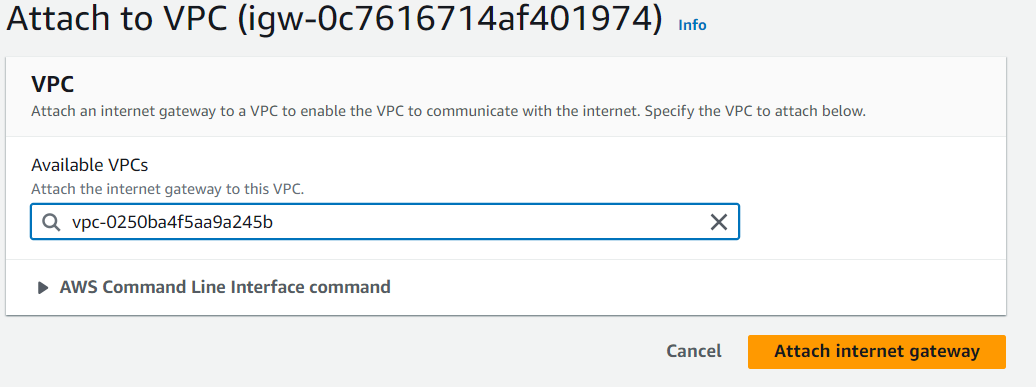
Step 4: Configure Route Tables
Each subnet is associated with a route table that controls the traffic routing.
Navigate to the "Route Tables" section and create a new route table for your VPC.
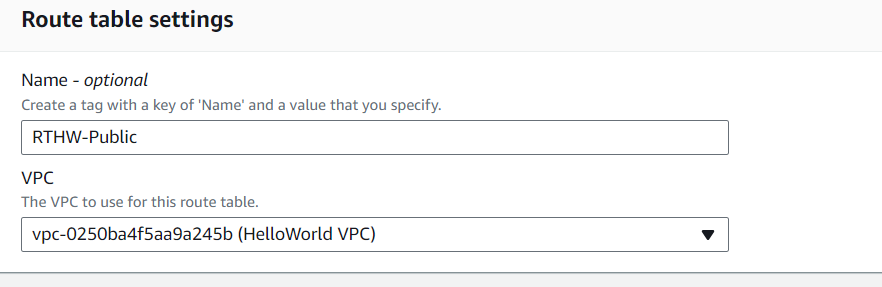
Add routes to the route table. For a public subnet, add a route with a destination of "0.0.0.0/0" and target the Internet Gateway (IGW).
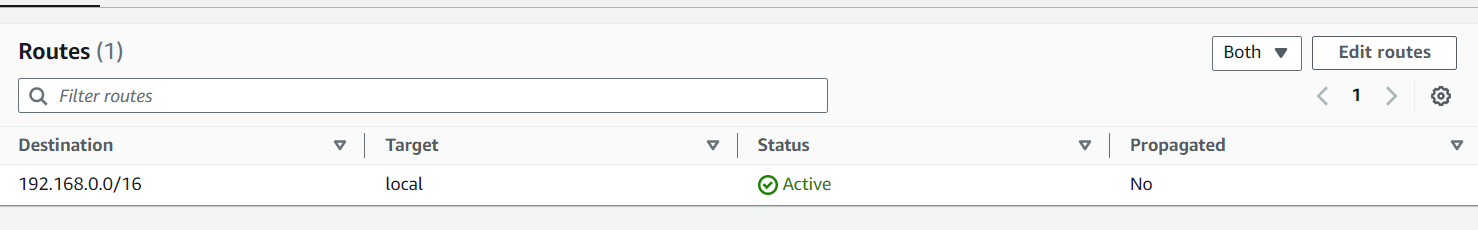
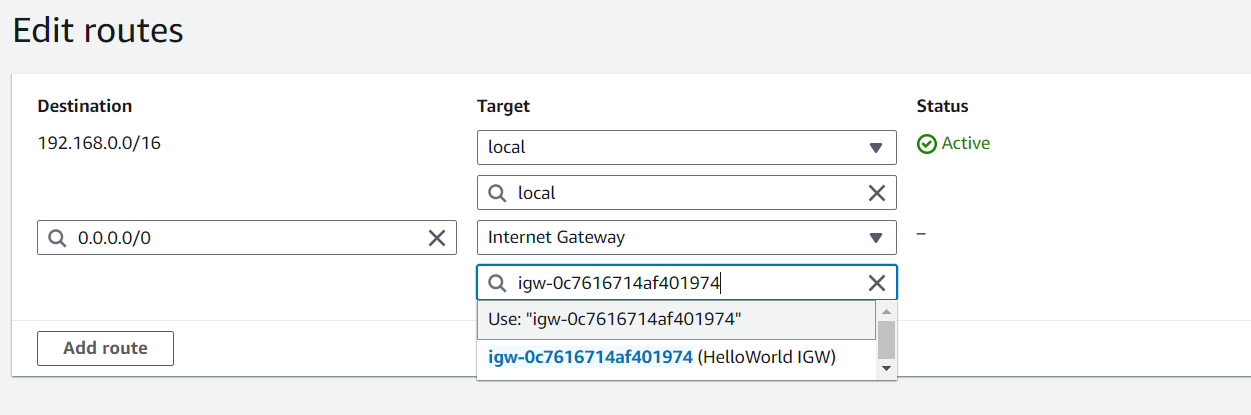
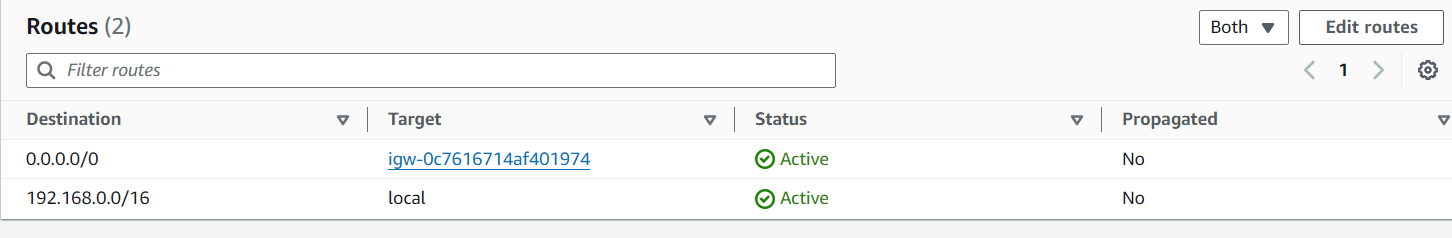
For a private subnet, ensure the route table only includes local routes (e.g., 192.168.0.0/16).
The route table has been created but is not attached to any subnet. So, edit subnet associations and select which subnet will be associated with this route table.
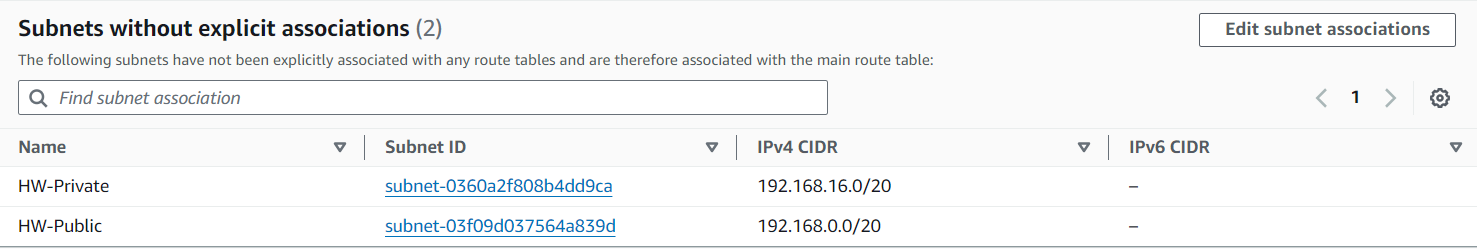
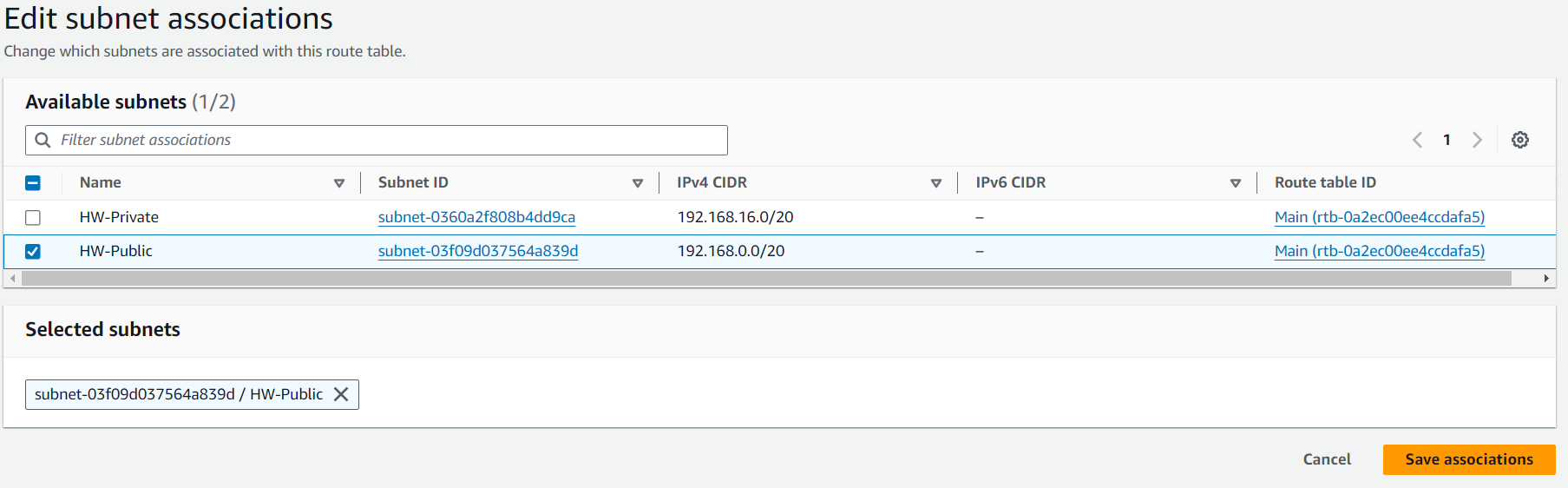
Now, finally, you will see the route table associated, in this case with HW-Public.
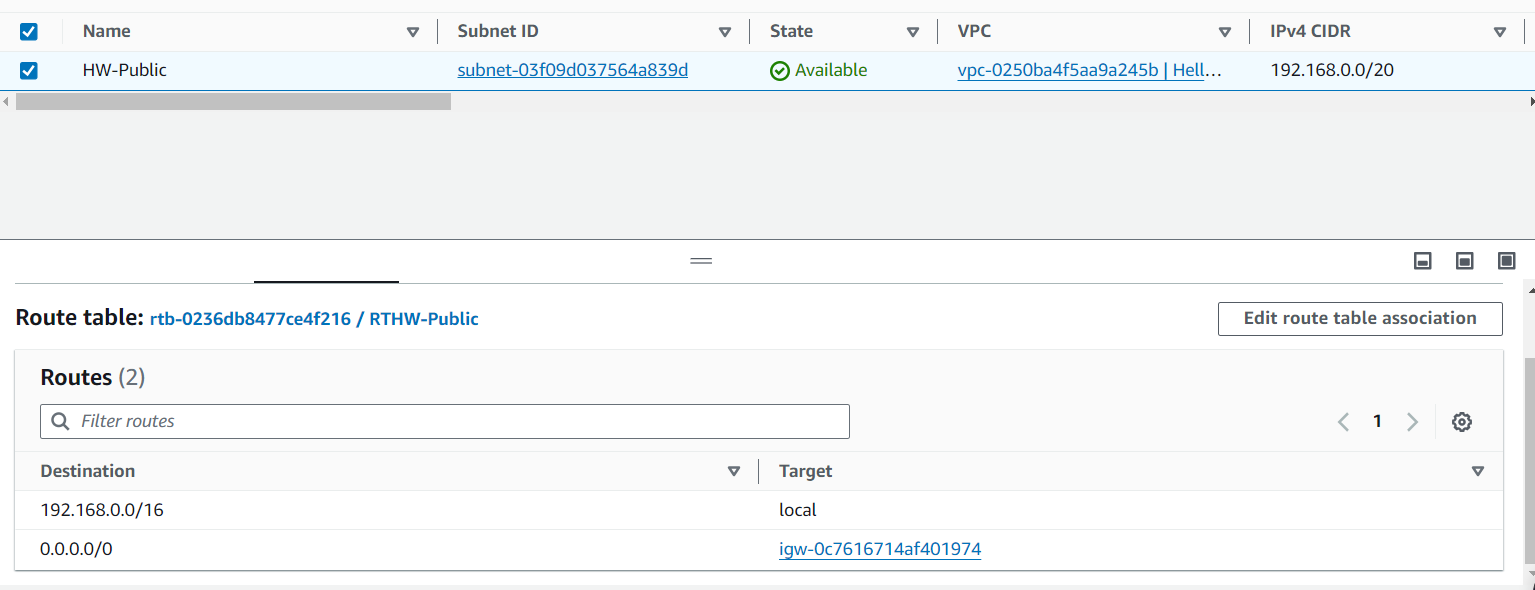
By following these steps, you can create a well-structured VPC in AWS, enabling you to manage and secure your resources efficiently. This setup provides a robust foundation for deploying applications and services in the cloud.
Conclusion
Virtual Private Clouds (VPCs) in AWS provide secure, isolated environments for your resources. By understanding VPC components like subnets, security groups, and internet gateways, you can create a secure and scalable network. Using VPCs ensures your applications and data are protected while staying connected to the internet.
Subscribe to my newsletter
Read articles from Jasai Hansda directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jasai Hansda
Jasai Hansda
Software Engineer (2 years) | In-transition to DevOps. Passionate about building and deploying software efficiently. Eager to leverage my development background in the DevOps and cloud computing world. Open to new opportunities!