Amazon Bedrock Studio Workspace 👨💻| Perfect Tool for Builders and Explorers to share GenAI apps within the Organization 🧗
 Raghul Gopal
Raghul GopalTable of contents
- Introduction to Amazon Bedrock Studio Workspace:
- Relationship between Amazon Bedrock Studio Workspace and Amazon DataZone:
- 5 Step Process to Create Your Amazon Bedrock Studio Workspace
- Decoding Permission Boundaries:
- Decoding Service Role for Amazon Bedrock Studio Workspace:
- Decoding Provisioning Role for Amazon Bedrock Studio Workspace:
- Decoding Amazon OpenSearch Serverless Encryption Policy

Hello Folks 👋👋,
This is Raghul Gopal, an AWS Community Builder (ML & GenAI) 🥷, a Research freak who is an enthusiast in AI & AGI Research 🔍 📈
Introduction to Amazon Bedrock Studio Workspace:
Think of a Typical Workspace as shown below where the developers work on a project. They need a unique app where the developers and builders contribute their work and other builders would like to see the project that you have built using a foundational model using Bedrock. Then, Amazon Bedrock Studio Workspace will be your application.

With Amazon Bedrock Studio, anyone inside your company may create apps and experiment with Amazon Bedrock models without requiring an AWS account. Using the Amazon Bedrock interface, build a Bedrock Studio workspace and invite users to become members in order to grant them access to Bedrock Studio.
Users may leverage the workspace's knowledge bases, guardrails, and creation projects to experiment with Amazon Bedrock models. You must configure Single Sign-On (SSO) interaction with the IAM Identity Center and your company's Identity Provider (IDP) in order to provide user access.
Users in your company might be individual members or groups in the workspace. You may give users a link to sign in to Amazon Bedrock Studio.
Relationship between Amazon Bedrock Studio Workspace and Amazon DataZone:
An efficient way to categorize, find, share, and manage data from AWS, on-premises, and outside sources is with Amazon DataZone, a data management solution. With fine-grained controls, it enable administrators and data stewards to oversee and regulate data access while guaranteeing proper context and permission levels.
Through the use of machine intelligence, Amazon DataZone facilitates data governance, establishes connections for data sharing, and streamlines the process of finding and classifying data. Furthermore, Amazon Bedrock Studio Workspace, a feature of Amazon DataZone, makes it simpler for builders to share data, knowledge bases, and GenAI applications.
The following resource list will be generated during the setup of a Bedrock Studio workspace:
AWS CloudFormation: To safely construct and manage resources in your account, Amazon Bedrock Studio leverages CloudFormation stacks. Every resource (project, application, or component) that is generated in your workspace generates a CloudFormation stack, which is then erased when the resource is removed. These stacks are used to handle all other resources developed by Amazon Bedrock Studio and are deployed using the provisioning role provided during workspace formation.
AWS Identity and Access Management (IAM): Upon resource creation, Amazon Bedrock Studio automatically generates IAM roles. While certain roles are employed by components internally, others provide builders the ability to carry out particular tasks. By default, builder roles are generated using the
AmazonDataZoneBedrockPermissionsBoundarypermission boundary and scoped down to the bare minimum of resources required.Amazon S3: For every project, an S3 bucket is built to hold data files like Knowledge Base files or API schemas for functions, as well as app and component specifications.
Amazon Bedrock Studio: Apps and components may establish guardrails, knowledge bases, and Amazon Bedrock agents within Bedrock Studio.
AWS Lambda: The knowledgebase and function components of Amazon Bedrock Studio make use of Lambda functions.
AWS Secrets Manager: The function's component's API credentials are kept in Secrets Manager.
Amazon CloudWatch: To store data on the Lambda functions generated by components, log groups are established in your account. Check out Amazon Bedrock Studio logs for further details.
5 Step Process to Create Your Amazon Bedrock Studio Workspace
Step 1: Set up AWS IAM Identity Center for Amazon Bedrock Studio
Step 2: Create permissions boundary, service role, and provisioning role
Step 3: Create an Amazon Bedrock Studio workspace
Step 4: Create an Amazon OpenSearch Serverless encryption policy
Step 5: Add workspace members
The important stuff behind Bedrock Studio is to know what permission boundaries, service roles, provisioning roles, and the use of Amazon OpenSearch Serverless Encryption Policy. Let’s decode them below.
Decoding Permission Boundaries:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "BedrockEnvironmentRoleKMSDecryptPermissions",
"Effect": "Allow",
"Action": [
"kms:Decrypt",
"kms:GenerateDataKey"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:ResourceTag/EnableBedrock": "true"
}
}
},
{
"Sid": "BedrockRuntimeAgentPermissions",
"Effect": "Allow",
"Action": [
"bedrock:InvokeAgent"
],
"Resource": "*",
"Condition": {
"Null": {
"aws:ResourceTag/AmazonDataZoneProject": "false"
}
}
},
{
"Sid": "BedrockRuntimeModelsAndJobsRole",
"Effect": "Allow",
"Action": [
"bedrock:InvokeModel",
"bedrock:InvokeModelWithResponseStream",
"bedrock:RetrieveAndGenerate"
],
"Resource": "*"
},
{
"Sid": "BedrockApplyGuardrails",
"Effect": "Allow",
"Action": [
"bedrock:ApplyGuardrail"
],
"Resource": "*",
"Condition": {
"Null": {
"aws:ResourceTag/AmazonDataZoneProject": "false"
}
}
},
{
"Sid": "BedrockRuntimePermissions",
"Effect": "Allow",
"Action": [
"bedrock:Retrieve",
"bedrock:StartIngestionJob",
"bedrock:GetIngestionJob",
"bedrock:ListIngestionJobs"
],
"Resource": "*",
"Condition": {
"Null": {
"aws:ResourceTag/AmazonDataZoneProject": "false"
}
}
},
{
"Sid": "BedrockFunctionsPermissions",
"Action": [
"secretsmanager:PutSecretValue"
],
"Resource": "arn:aws:secretsmanager:*:*:secret:br-studio/*",
"Effect": "Allow",
"Condition": {
"Null": {
"aws:ResourceTag/AmazonDataZoneProject": "false"
}
}
},
{
"Sid": "BedrockS3ObjectsHandlingPermissions",
"Action": [
"s3:GetObject",
"s3:PutObject",
"s3:GetObjectVersion",
"s3:ListBucketVersions",
"s3:DeleteObject",
"s3:DeleteObjectVersion",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::br-studio-228947353622-*"
],
"Effect": "Allow"
}
]
}

A permission boundary is an advanced feature for using a managed policy to set the maximum permissions that an identity-based policy can grant to an IAM entity.
Because the provisioning role is able to create IAM roles, the use of a permissions boundary allows you to restrict what roles can be created by a provisioning role.
Decoding Service Role for Amazon Bedrock Studio Workspace:

To manage your Amazon Bedrock Studio Workspace, you need to create a service role that lets Amazon DataZone manage your workspaces.
Permission to Manage an Amazon Bedrock Studio Workspace with Amazon DataZone
Data Zone – Grants Access to DataZone so that Bedrock Studio can manage the resources created as part of Bedrock Studio Workspace.
RAM – Grants the ability to get resource share associations.
Bedrock – Grants the ability to invoke Amazon Bedrock Models.
KMS – Allows the provisioning role to access the KMS Key that you use for encrypting your workspace – Optional
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "DomainExecutionRoleStatement",
"Effect": "Allow",
"Action": [
"datazone:GetDomain",
"datazone:ListProjects",
"datazone:GetProject",
"datazone:CreateProject",
"datazone:UpdateProject",
"datazone:DeleteProject",
"datazone:ListProjectMemberships",
"datazone:CreateProjectMembership",
"datazone:DeleteProjectMembership",
"datazone:ListEnvironments",
"datazone:GetEnvironment",
"datazone:CreateEnvironment",
"datazone:UpdateEnvironment",
"datazone:DeleteEnvironment",
"datazone:ListEnvironmentBlueprints",
"datazone:GetEnvironmentBlueprint",
"datazone:CreateEnvironmentBlueprint",
"datazone:UpdateEnvironmentBlueprint",
"datazone:DeleteEnvironmentBlueprint",
"datazone:ListEnvironmentBlueprintConfigurations",
"datazone:ListEnvironmentBlueprintConfigurationSummaries",
"datazone:ListEnvironmentProfiles",
"datazone:GetEnvironmentProfile",
"datazone:CreateEnvironmentProfile",
"datazone:UpdateEnvironmentProfile",
"datazone:DeleteEnvironmentProfile",
"datazone:UpdateEnvironmentDeploymentStatus",
"datazone:GetEnvironmentCredentials",
"datazone:ListGroupsForUser",
"datazone:SearchUserProfiles",
"datazone:SearchGroupProfiles",
"datazone:GetUserProfile",
"datazone:GetGroupProfile"
],
"Resource": "*"
},
{
"Sid": "RAMResourceShareStatement",
"Effect": "Allow",
"Action": "ram:GetResourceShareAssociations",
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"bedrock:InvokeModel",
"bedrock:InvokeModelWithResponseStream",
"bedrock:GetFoundationModelAvailability"
],
"Resource": "*"
}
]
}
Decoding Provisioning Role for Amazon Bedrock Studio Workspace:

To allow Amazon Bedrock Studio to create resources in a user’s account, such as the guardrail component, you need to create a provisioning role.
Permissions to manage Amazon Bedrock Studio are given below.
IAM
Cloud Formation
Bedrock
AOSS
Lambda
Logs
KMS
S3
Secrets Manager
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AmazonDataZonePermissionsToCreateEnvironmentRole",
"Effect": "Allow",
"Action": [
"iam:CreateRole",
"iam:GetRolePolicy",
"iam:DetachRolePolicy",
"iam:AttachRolePolicy",
"iam:UpdateAssumeRolePolicy"
],
"Resource": "arn:aws:iam::*:role/DataZoneBedrockProjectRole*",
"Condition": {
"StringEquals": {
"iam:PermissionsBoundary": "arn:aws:iam::228947353622:policy/AmazonDataZoneBedrockPermissionsBoundary",
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
},
"Null": {
"aws:ResourceTag/AmazonDataZoneEnvironment": "false"
}
}
},
{
"Sid": "AmazonDataZonePermissionsToServiceRole",
"Effect": "Allow",
"Action": [
"iam:CreateRole",
"iam:GetRolePolicy",
"iam:DetachRolePolicy",
"iam:AttachRolePolicy",
"iam:UpdateAssumeRolePolicy"
],
"Resource": [
"arn:aws:iam::*:role/BedrockStudio*",
"arn:aws:iam::*:role/AmazonBedrockExecution*"
],
"Condition": {
"StringEquals": {
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
},
"Null": {
"aws:ResourceTag/AmazonDataZoneEnvironment": "false"
}
}
},
{
"Sid": "IamPassRolePermissionsForBedrock",
"Effect": "Allow",
"Action": [
"iam:PassRole"
],
"Resource": "arn:aws:iam::*:role/AmazonBedrockExecution*",
"Condition": {
"StringEquals": {
"iam:PassedToService": [
"bedrock.amazonaws.com"
],
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
}
}
},
{
"Sid": "IamPassRolePermissionsForLambda",
"Effect": "Allow",
"Action": [
"iam:PassRole"
],
"Resource": [
"arn:aws:iam::*:role/BedrockStudio*"
],
"Condition": {
"StringEquals": {
"iam:PassedToService": [
"lambda.amazonaws.com"
],
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
}
}
},
{
"Sid": "AmazonDataZonePermissionsToManageCreatedEnvironmentRole",
"Effect": "Allow",
"Action": [
"iam:DeleteRole",
"iam:GetRole",
"iam:DetachRolePolicy",
"iam:GetPolicy",
"iam:DeleteRolePolicy",
"iam:PutRolePolicy"
],
"Resource": [
"arn:aws:iam::*:role/DataZoneBedrockProjectRole*",
"arn:aws:iam::*:role/AmazonBedrock*",
"arn:aws:iam::*:role/BedrockStudio*"
],
"Condition": {
"StringEquals": {
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
}
}
},
{
"Sid": "AmazonDataZoneCFStackCreationForEnvironments",
"Effect": "Allow",
"Action": [
"cloudformation:CreateStack",
"cloudformation:UpdateStack",
"cloudformation:TagResource"
],
"Resource": [
"arn:aws:cloudformation:*:*:stack/DataZone*"
],
"Condition": {
"ForAnyValue:StringLike": {
"aws:TagKeys": "AmazonDataZoneEnvironment"
},
"Null": {
"aws:ResourceTag/AmazonDataZoneEnvironment": "false"
}
}
},
{
"Sid": "AmazonDataZoneCFStackManagementForEnvironments",
"Effect": "Allow",
"Action": [
"cloudformation:DeleteStack",
"cloudformation:DescribeStacks",
"cloudformation:DescribeStackEvents"
],
"Resource": [
"arn:aws:cloudformation:*:*:stack/DataZone*"
]
},
{
"Sid": "AmazonDataZoneEnvironmentBedrockGetViaCloudformation",
"Effect": "Allow",
"Action": [
"bedrock:GetAgent",
"bedrock:GetAgentActionGroup",
"bedrock:GetAgentAlias",
"bedrock:GetAgentKnowledgeBase",
"bedrock:GetKnowledgeBase",
"bedrock:GetDataSource",
"bedrock:GetGuardrail"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
}
}
},
{
"Sid": "AmazonDataZoneEnvironmentDeleteGuardrailViaCloudformation",
"Effect": "Allow",
"Action": [
"bedrock:DeleteGuardrail"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
}
}
},
{
"Sid": "AmazonDataZoneEnvironmentBedrockAgentPermissions",
"Effect": "Allow",
"Action": [
"bedrock:CreateAgent",
"bedrock:UpdateAgent",
"bedrock:DeleteAgent",
"bedrock:ListAgents",
"bedrock:CreateAgentActionGroup",
"bedrock:UpdateAgentActionGroup",
"bedrock:DeleteAgentActionGroup",
"bedrock:ListAgentActionGroups",
"bedrock:CreateAgentAlias",
"bedrock:UpdateAgentAlias",
"bedrock:DeleteAgentAlias",
"bedrock:ListAgentAliases",
"bedrock:AssociateAgentKnowledgeBase",
"bedrock:DisassociateAgentKnowledgeBase",
"bedrock:UpdateAgentKnowledgeBase",
"bedrock:ListAgentKnowledgeBases",
"bedrock:PrepareAgent"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
},
"Null": {
"aws:ResourceTag/AmazonDataZoneProject": "false"
}
}
},
{
"Sid": "AmazonDataZoneEnvironmentOpenSearch",
"Effect": "Allow",
"Action": [
"aoss:CreateAccessPolicy",
"aoss:DeleteAccessPolicy",
"aoss:UpdateAccessPolicy",
"aoss:GetAccessPolicy",
"aoss:ListAccessPolicies",
"aoss:CreateSecurityPolicy",
"aoss:DeleteSecurityPolicy",
"aoss:UpdateSecurityPolicy",
"aoss:GetSecurityPolicy",
"aoss:ListSecurityPolicies"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
}
}
},
{
"Sid": "AmazonDataZoneEnvironmentOpenSearchPermissions",
"Effect": "Allow",
"Action": [
"aoss:UpdateCollection",
"aoss:DeleteCollection",
"aoss:BatchGetCollection",
"aoss:ListCollections",
"aoss:CreateCollection"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
},
"Null": {
"aws:ResourceTag/AmazonDataZoneProject": "false"
}
}
},
{
"Sid": "AmazonDataZoneEnvironmentBedrockKnowledgeBasePermissions",
"Effect": "Allow",
"Action": [
"bedrock:CreateKnowledgeBase",
"bedrock:UpdateKnowledgeBase",
"bedrock:DeleteKnowledgeBase",
"bedrock:CreateDataSource",
"bedrock:UpdateDataSource",
"bedrock:DeleteDataSource",
"bedrock:ListKnowledgeBases",
"bedrock:ListDataSources"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
},
"Null": {
"aws:ResourceTag/AmazonDataZoneProject": "false"
}
}
},
{
"Sid": "AmazonDataZoneEnvironmentBedrockGuardrailPermissions",
"Effect": "Allow",
"Action": [
"bedrock:CreateGuardrail",
"bedrock:CreateGuardrailVersion",
"bedrock:ListGuardrails",
"bedrock:ListTagsForResource",
"bedrock:TagResource",
"bedrock:UntagResource",
"bedrock:UpdateGuardrail"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
},
"Null": {
"aws:ResourceTag/AmazonDataZoneProject": "false"
}
}
},
{
"Sid": "AmazonDataZoneEnvironmentLambdaPermissions",
"Effect": "Allow",
"Action": [
"lambda:AddPermission",
"lambda:CreateFunction",
"lambda:ListFunctions",
"lambda:UpdateFunctionCode",
"lambda:UpdateFunctionConfiguration",
"lambda:InvokeFunction",
"lambda:ListVersionsByFunction",
"lambda:PublishVersion"
],
"Resource": [
"arn:aws:lambda:us-east-1:228947353622:function:br-studio*",
"arn:aws:lambda:us-east-1:228947353622:function:OpensearchIndexLambda*",
"arn:aws:lambda:us-east-1:228947353622:function:IngestionTriggerLambda*"
],
"Condition": {
"StringEquals": {
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
},
"Null": {
"aws:ResourceTag/AmazonDataZoneEnvironment": "false"
}
}
},
{
"Sid": "AmazonDataZoneEnvironmentLambdaManagePermissions",
"Effect": "Allow",
"Action": [
"lambda:GetFunction",
"lambda:DeleteFunction",
"lambda:RemovePermission"
],
"Resource": [
"arn:aws:lambda:us-east-1:228947353622:function:br-studio*",
"arn:aws:lambda:us-east-1:228947353622:function:OpensearchIndexLambda*",
"arn:aws:lambda:us-east-1:228947353622:function:IngestionTriggerLambda*"
],
"Condition": {
"StringEquals": {
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
}
}
},
{
"Sid": "ManageLogGroups",
"Effect": "Allow",
"Action": [
"logs:CreateLogGroup",
"logs:PutRetentionPolicy",
"logs:DeleteLogGroup"
],
"Resource": [
"arn:aws:logs:*:*:log-group:/aws/lambda/br-studio-*",
"arn:aws:logs:*:*:log-group:datazone-*"
],
"Condition": {
"StringEquals": {
"aws:CalledViaFirst": "cloudformation.amazonaws.com"
}
}
},
{
"Sid": "ListTags",
"Effect": "Allow",
"Action": [
"bedrock:ListTagsForResource",
"aoss:ListTagsForResource",
"lambda:ListTags",
"iam:ListRoleTags",
"iam:ListPolicyTags"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:CalledViaFirst": "cloudformation.amazonaws.com"
}
}
},
{
"Sid": "AmazonDataZoneEnvironmentTagsCreationPermissions",
"Effect": "Allow",
"Action": [
"iam:TagRole",
"iam:TagPolicy",
"iam:UntagRole",
"iam:UntagPolicy",
"logs:TagLogGroup",
"bedrock:TagResource",
"bedrock:UntagResource",
"bedrock:ListTagsForResource",
"aoss:TagResource",
"aoss:UnTagResource",
"aoss:ListTagsForResource",
"lambda:TagResource",
"lambda:UnTagResource",
"lambda:ListTags"
],
"Resource": "*",
"Condition": {
"ForAnyValue:StringLike": {
"aws:TagKeys": "AmazonDataZoneEnvironment"
},
"Null": {
"aws:ResourceTag/AmazonDataZoneEnvironment": "false"
},
"StringEquals": {
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
}
}
},
{
"Sid": "AmazonDataZoneEnvironmentBedrockTagResource",
"Effect": "Allow",
"Action": [
"bedrock:TagResource"
],
"Resource": "arn:aws:bedrock:us-east-1:228947353622:agent-alias/*",
"Condition": {
"StringEquals": {
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
},
"ForAnyValue:StringLike": {
"aws:TagKeys": "AmazonDataZoneEnvironment"
}
}
},
{
"Sid": "PermissionsToGetAmazonDataZoneEnvironmentBlueprintTemplates",
"Effect": "Allow",
"Action": "s3:GetObject",
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
},
"StringNotEquals": {
"aws:ResourceAccount": "${aws:PrincipalAccount}"
}
}
},
{
"Sid": "PermissionsToManageSecrets",
"Effect": "Allow",
"Action": [
"secretsmanager:GetRandomPassword"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
}
}
},
{
"Sid": "PermissionsToStoreSecrets",
"Effect": "Allow",
"Action": [
"secretsmanager:CreateSecret",
"secretsmanager:TagResource",
"secretsmanager:UntagResource",
"secretsmanager:PutResourcePolicy",
"secretsmanager:DeleteResourcePolicy",
"secretsmanager:DeleteSecret"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
},
"Null": {
"aws:ResourceTag/AmazonDataZoneEnvironment": "false"
}
}
},
{
"Sid": "AmazonDataZoneManageProjectBuckets",
"Effect": "Allow",
"Action": [
"s3:CreateBucket",
"s3:DeleteBucket",
"s3:PutBucketTagging",
"s3:PutEncryptionConfiguration",
"s3:PutBucketVersioning",
"s3:PutBucketCORS",
"s3:PutBucketPublicAccessBlock",
"s3:PutBucketPolicy",
"s3:PutLifecycleConfiguration",
"s3:DeleteBucketPolicy"
],
"Resource": "arn:aws:s3:::br-studio-*",
"Condition": {
"StringEquals": {
"aws:CalledViaFirst": [
"cloudformation.amazonaws.com"
]
}
}
},
{
"Sid": "CreateServiceLinkedRoleForOpenSearchServerless",
"Effect": "Allow",
"Action": "iam:CreateServiceLinkedRole",
"Resource": "*",
"Condition": {
"StringEquals": {
"iam:AWSServiceName": "observability.aoss.amazonaws.com",
"aws:CalledViaFirst": "cloudformation.amazonaws.com"
}
}
}
]
}
Decoding Amazon OpenSearch Serverless Encryption Policy

Amazon Bedrock uses Amazon OpenSearch Serverless (OSS) collections with the projects that workspace members create. To safeguard member data in the collections, you need to create an encryption policy for the collections in the workspace domain. Workspace members aren't able to create a project until you create the policy.
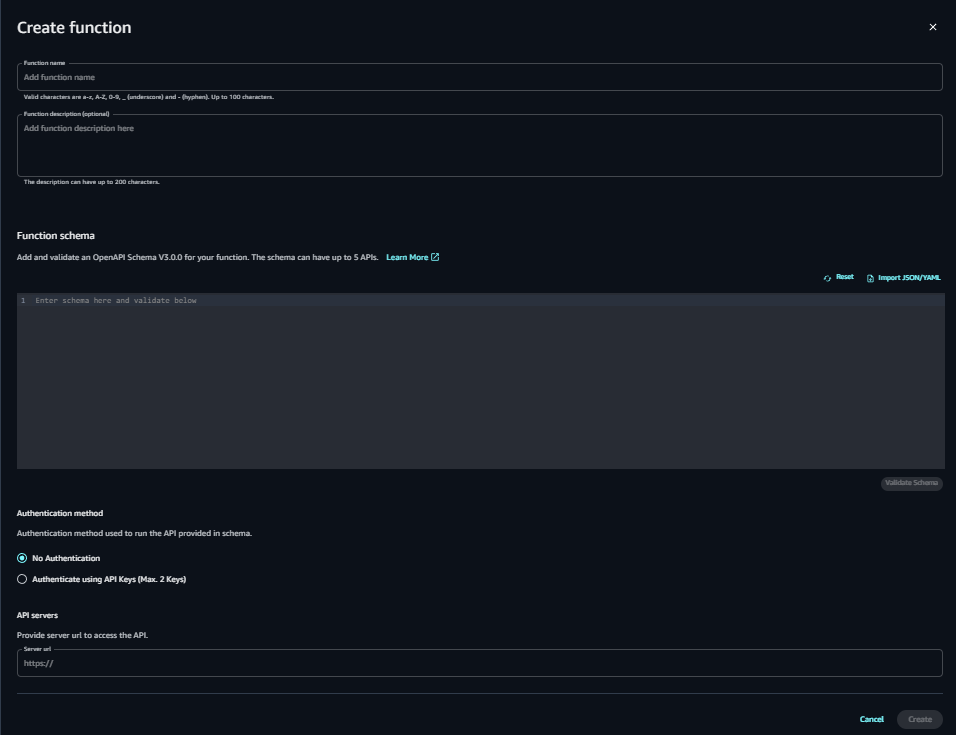
I've attached the screenshots of the sample playground, project setup, knowledge bases, Guardrails, and function setup in Amazon Bedrock Studio Workspace. You can choose the Embedding models of your choice available in Amazon Bedrock. Right now, only OpenSearch Serverless has been serving as a vector store for RAG Implementations. You can also create your function schema and provide your function authentication to run your API. You are supposed to give the Server URL to access the APIs.
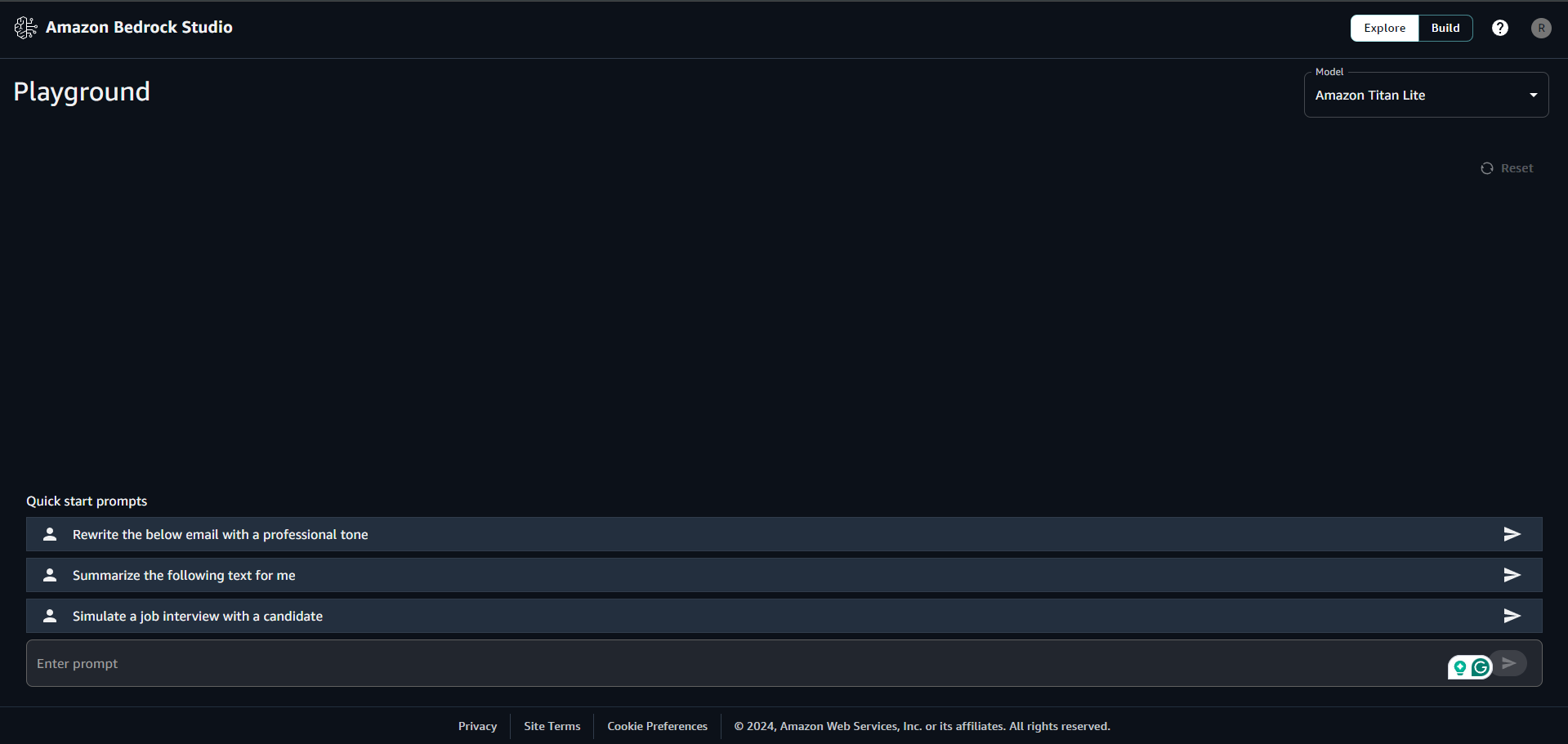
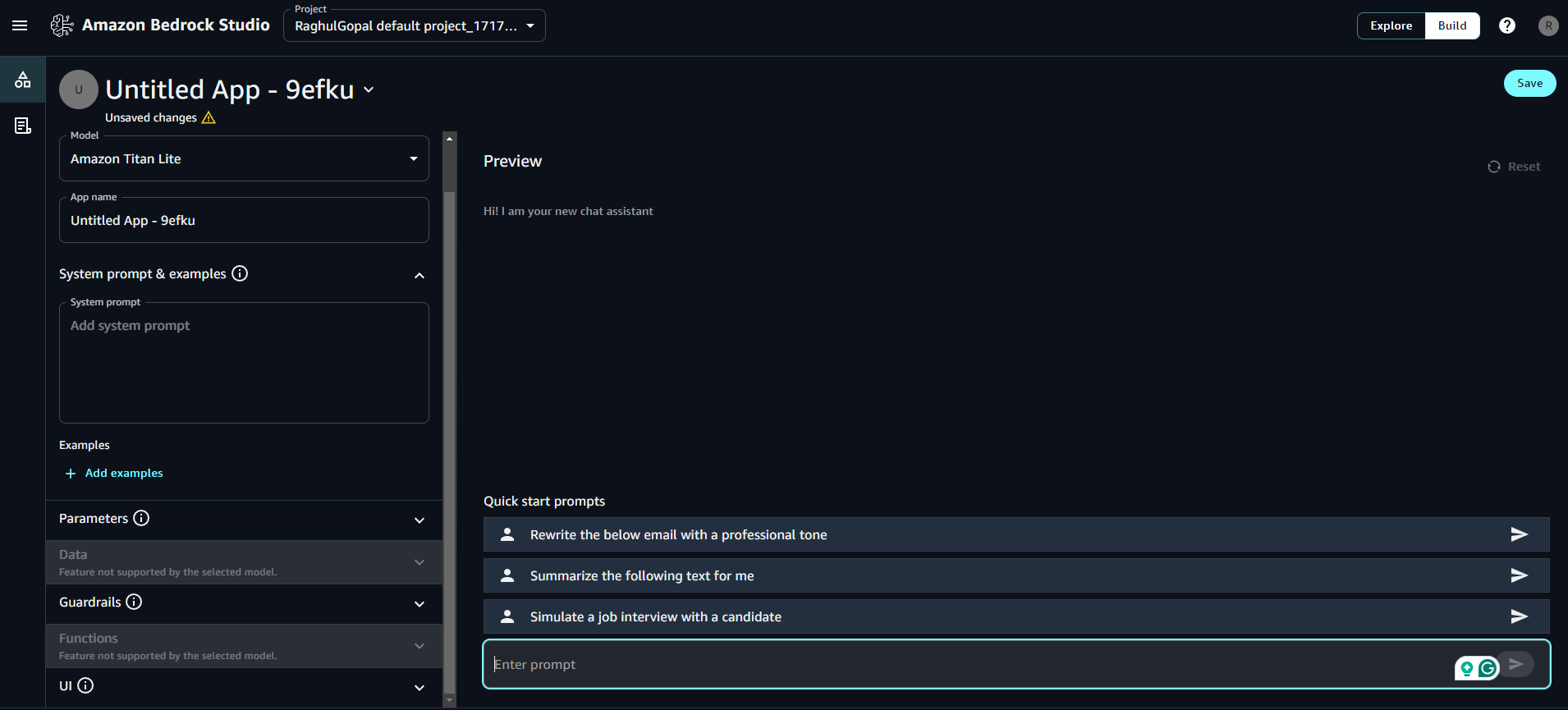
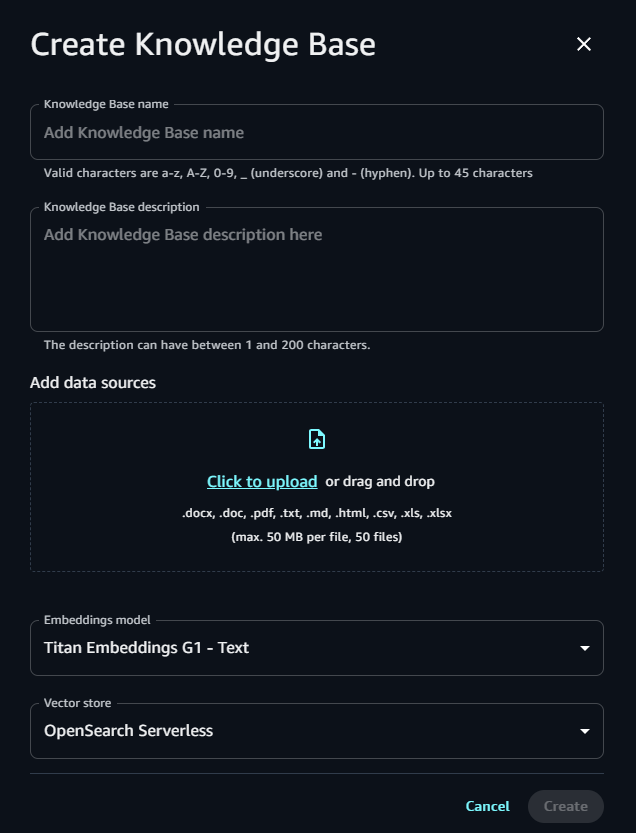
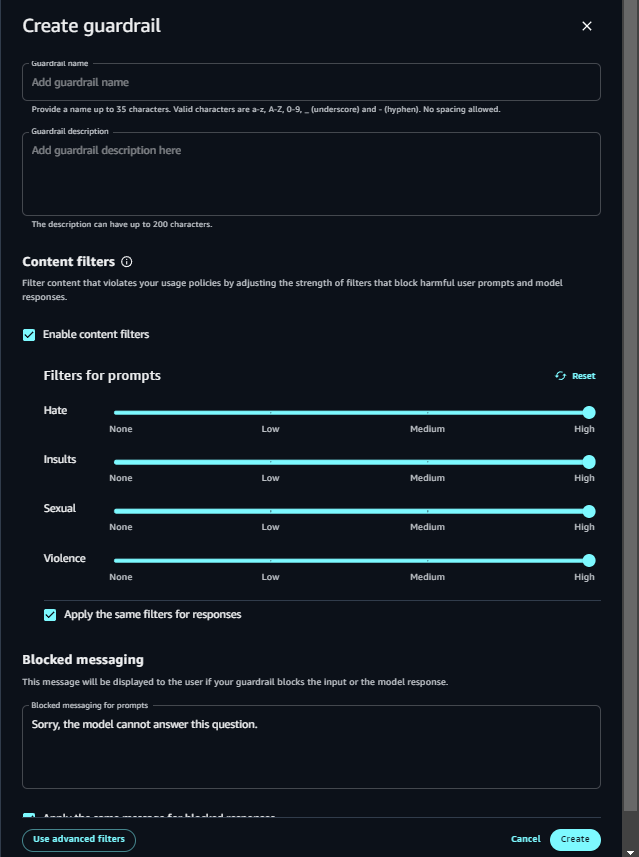
Watch this YouTube video for a better understanding: https://youtu.be/5s0QjakWbCg?si=FkOa36JgvLvB1pU9
That's it for now. Happy AI, Happy Coding. Let's look at the new series of outcomes of Generative AI.
Stay Connected with me
🔗 Raghul Gopal Linkedin: https://www.linkedin.com/in/raghulgopaltech/
🔗Raghul Gopal YouTube: https://www.youtube.com/@rahulg2980
📒Subscribe to my Newsletter: Subscribe on LinkedIn https://www.linkedin.com/build-relation/newsletter-follow?entityUrn=7183725729254158336
Subscribe to my newsletter
Read articles from Raghul Gopal directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Raghul Gopal
Raghul Gopal
I'm Raghul Gopal, an AWS Community Builder (Machine Learning & Generative AI) at Amazon Web Services. Certified in DeepLearning.AI Specializations and Generative AI Technologies, I'm all about collaboration for groundbreaking research in GenAI. Cloud Computing is my playground, especially on AWS! Holding certifications as an AWS Cloud Practitioner, AWS Developer Associate, and AWS Machine Learning Specialty, I'm on a mission to deliver high-impact training to colleges and firms, emphasizing the transformative power of AI in day-to-day tasks and migration. Passionate about sharing knowledge, I love shedding light on the AI impacts on firms, with a particular focus on implementing Generative AI on AWS to supercharge workflows.