Security vs Sharing permissions in NTFS
 MDG developer
MDG developer
Lately, as part of one of my projects, I had to deal with NTFS and File Shares. I needed to understand the difference between security permissions and sharing permissions, as both affect the user's ability to access these shares
A bit of context
In the context of NTFS (New Technology File System), used primarly by Microsoft Windows operative systems, security permissions and sharing permissions are two layers of access control for files. These permissions operate at differnt levels and in different scenarios.
Security Permissions
Security permissions, also know as NTFS permissions, are applied directly to files and folders on a NTFS-formatted volume.
The key concept here is that NTFS permissions are applied specifically to files and folders at a computer level**.** We will explore this idea futher later on.
For know, it is important to keep in mind that NTFS permissions specify what actions users and groups can perform on files and folders locally.
List of permissions
Full Control: Users can read, write, modify, delete, and change permissions of the file or folder.
Modify: Users can read, write, modify, and delete the file or folder.
Read & Execute: Users can view and run executable files, including scripts.
List Folder Contents: Users can view the names of files and subfolders within the folder.
Read: Users can view the contents of the file or folder.
Write: Users can write to the file or add files to a folder.
A quick example
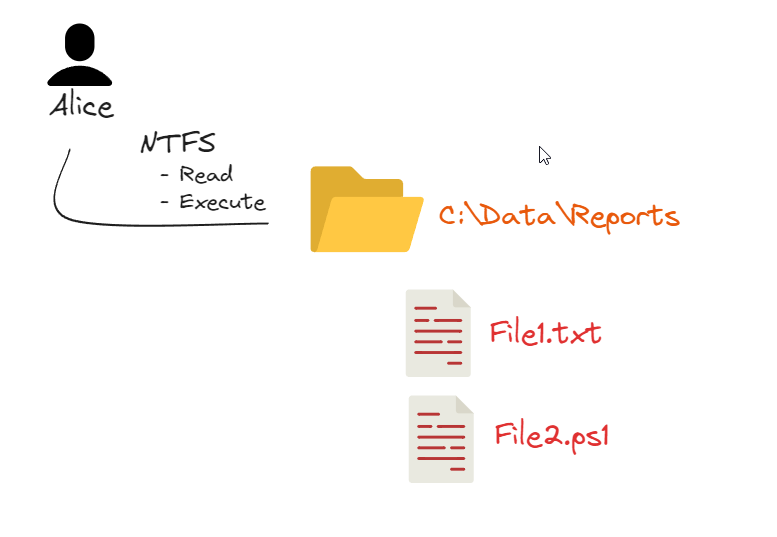
This example shows that Alice can open and read the files in the Reports folder, but cannot modify or delete them.
We are still not talking about sharing in any way. In this example Alice is a User of the Computer, so no sharing permission have been configured yet.
Sharing permissions
Sharing permissions are applied to shared folders, so now we need to share the folder/files to apply this kind of permissions. In this case, the permissions are used to control access over the network.
List of permissions
Full Control: Users can read, change, and delete files and folders within the shared folder.
Change: Users can read, execute, and modify files and folders, but not change the sharing permissions.
Read: Users can only view the contents of the shared folder and its files.
Example
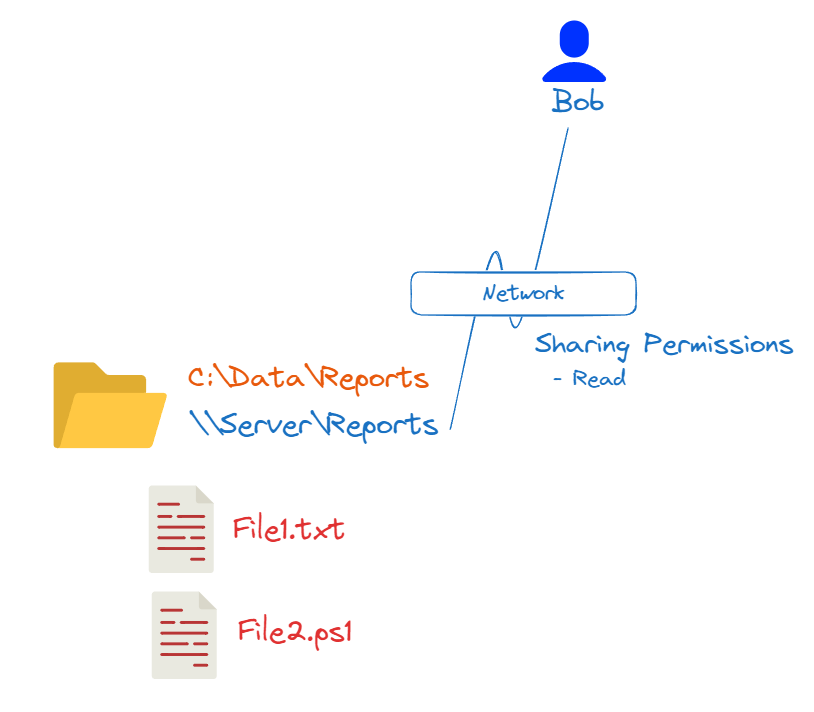
In this example, the folder has been shared as "Reports" (indicated by \\Server\Reports in blue), and user Bob has sharing permissions to read de folder. This means Bob will be able to access \\Server\Reports through network and read the contents of the folder.
The permissions combined
Now is the moment to understand how both concepts work together. We need to consider each permission as different layer, much like the layers of an onion 😉, so that the most restrictive permissions apply.
IIt is important to remember that both types of permissions are necessary. Depending on how they are configured, the absence of either type of permission can restrict or completely prevent a user from interacting with the files in specific ways or accessing them at all.
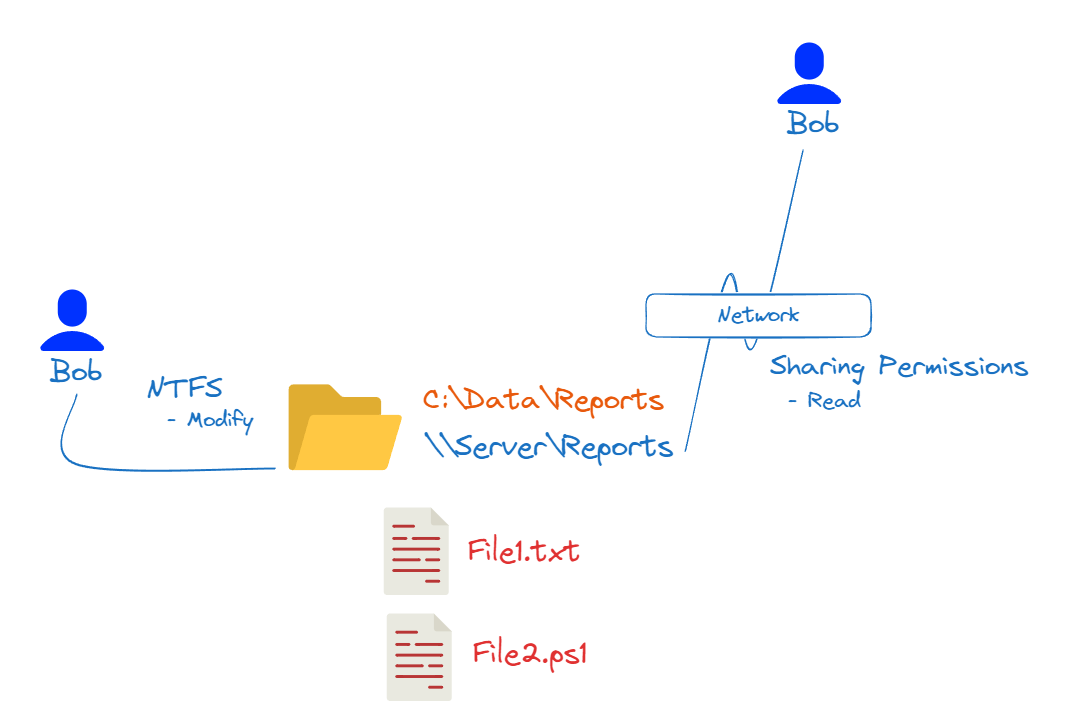
In this last scenario, when Bob accesses the folder locally, he can modify the files. However, when he accesses the folder over the network, the sharing permissions limit him to read-only access. This is because the sharing permissions are more restrictive than the NTFS permissions.
Additional Note: The Everyone identity
The Everyone identity is a special built-in group in Windows that represents all users who access the system, including authenticated users, guest accounts, and even users accessing the system over the network. It is a catch-all group that simplifies the permission management.
In a shared network scenario, setting Full Control to Everyoneeliminates the NTFS permissions layer for that folder entirely. This allows unrestricted access to all users, removing any NTFS restrictions previously in place.
Subscribe to my newsletter
Read articles from MDG developer directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
