3.1 The Network Landscape: Multiplexing, Handshakes, and Security Essentials
 Vijay Kumar Singh
Vijay Kumar Singh
Introduction to the Transport and Application Layers
The first three layers of a network model allow nodes on a network to communicate with other nodes on their own or different networks.
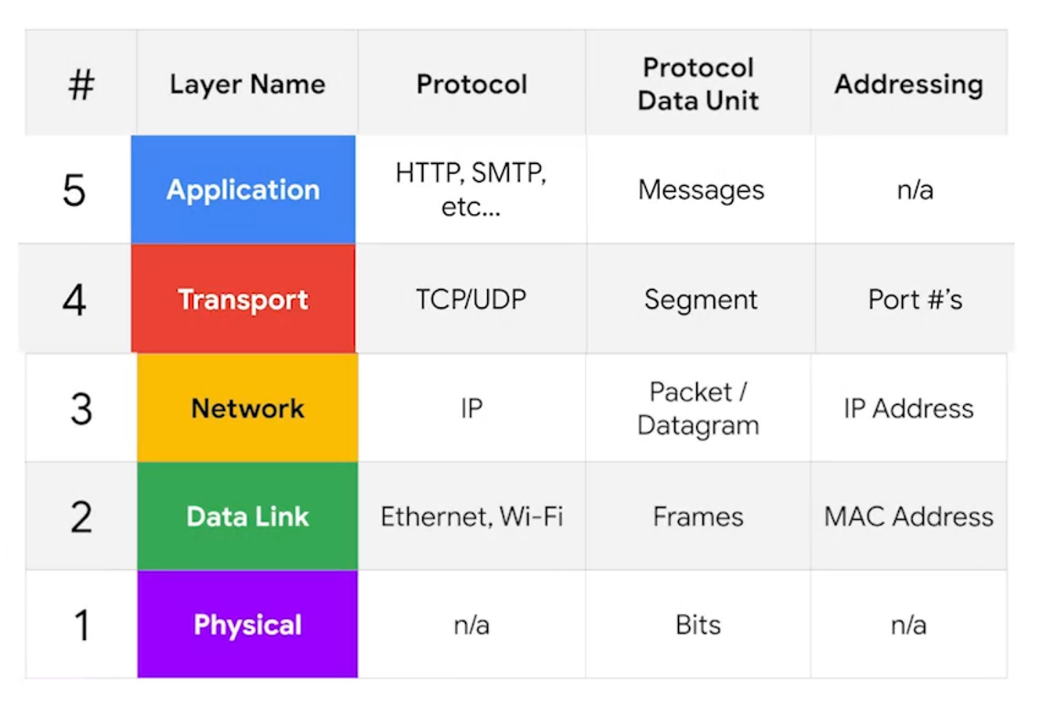
The real aim of computer networking is not just for computers to send data to each other, but for the programs running on these computers to communicate.
This is where the transport and application layers come into play.
The transport layer directs traffic to specific network applications.
The application layer enables these applications to communicate in a manner they understand.
Navigating the Network: Multiplexing, TCP vs. UDP, The Handshakes, and Firewalls
In the complex world of computer networks, understanding the fundamental concepts is like decoding the language of the digital world. Among these concepts lie multiplexing and demultiplexing, the disparities between TCP and UDP, the intricacies of the three-way handshake, and the indispensable role of firewalls in safeguarding networks. Let us embark on a journey through these essential elements of networking, unraveling their complexities and uncovering their significance.
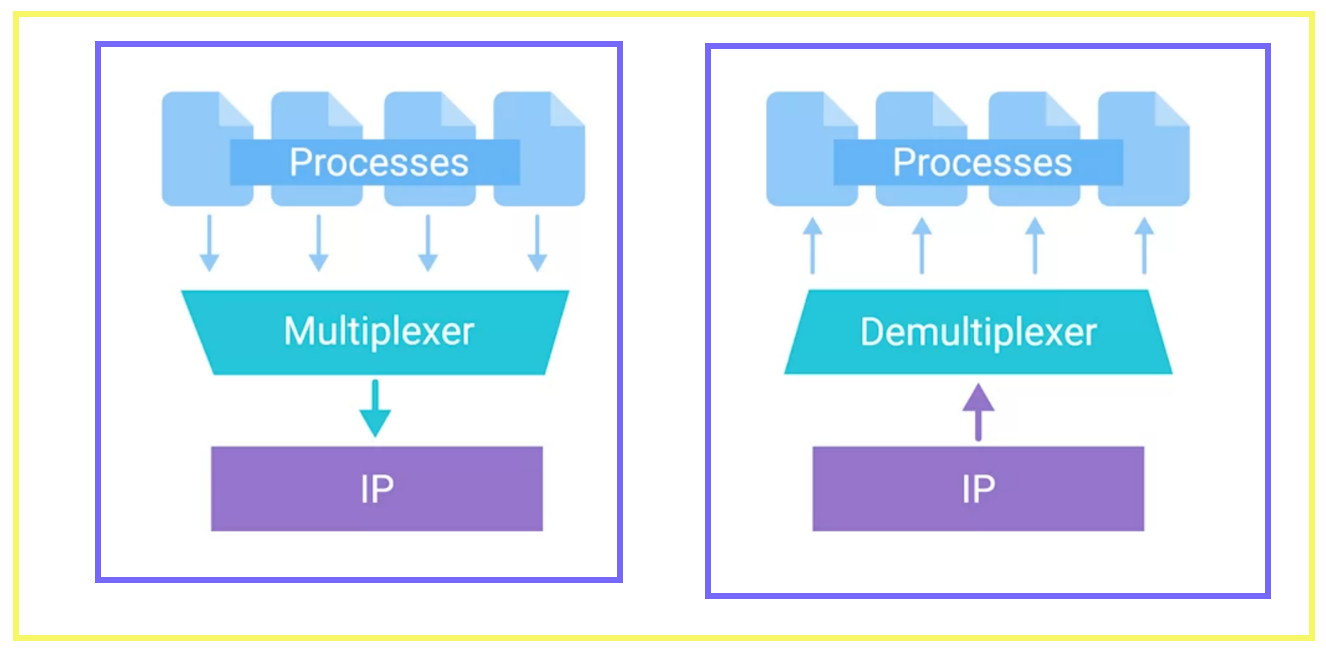
Multiplexing and Demultiplexing: Bridging Connections
At the heart of network communication lies the concept of multiplexing and demultiplexing. Imagine a bustling highway with multiple lanes, each carrying a stream of vehicles to different destinations. Similarly, in the realm of networking, multiplexing allows multiple data streams to be combined into a single transmission channel, optimizing bandwidth utilization and facilitating efficient data transfer.
Multiplexing operates at various layers of the network stack, including the physical, data link, and transport layers. At the physical layer, techniques such as frequency division multiplexing (FDM) and time division multiplexing (TDM) allocate distinct frequencies or time slots to different signals, enabling concurrent transmission over a shared medium.
Moving up the layers, data link layer multiplexing, exemplified by techniques like multipoint-to-point configuration and frame relay, enables multiple devices to share a single communication channel while maintaining data integrity and addressing individual endpoints.
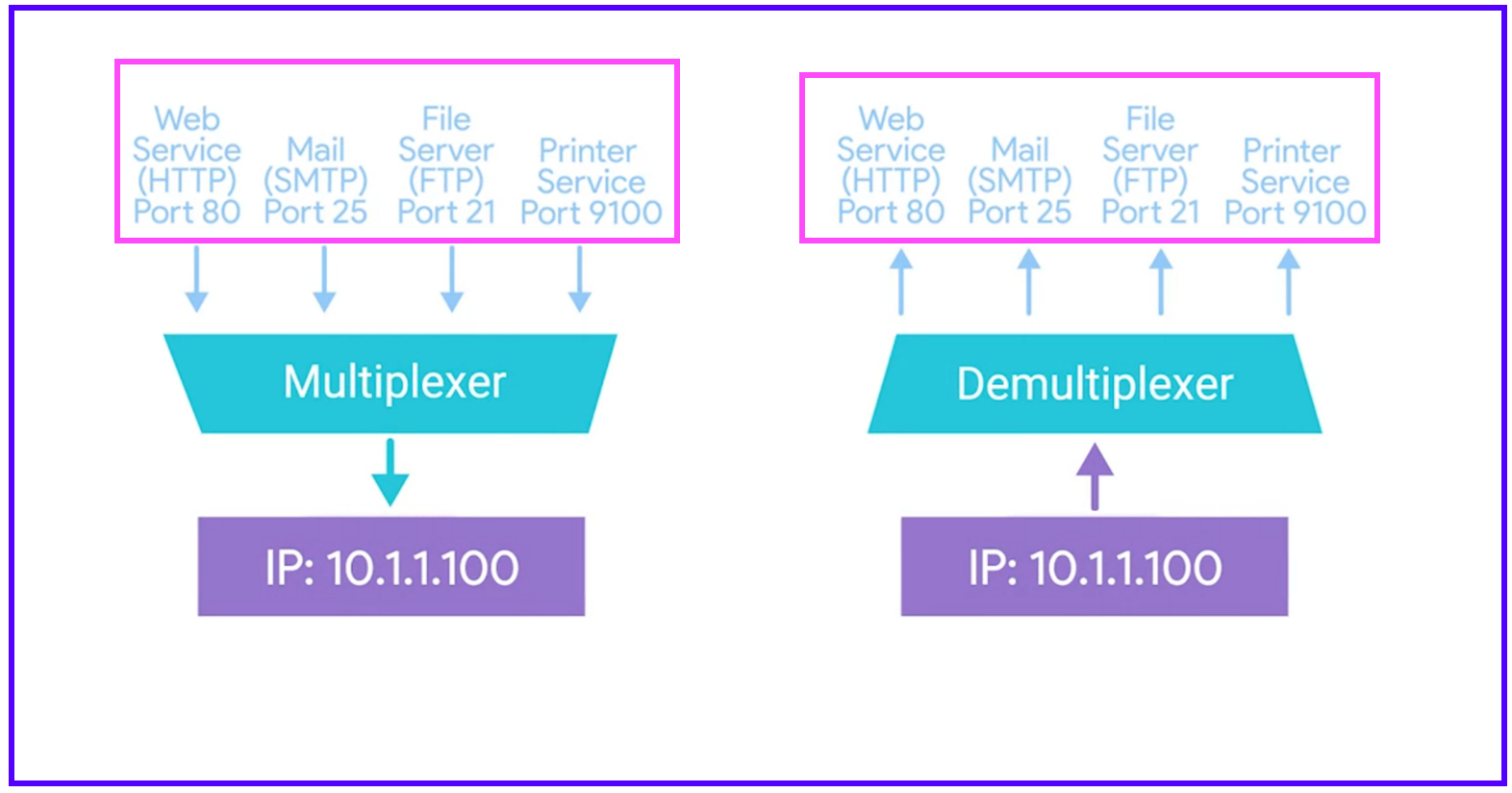
Finally, at the transport layer, protocols like TCP and UDP employ port numbers to demultiplex incoming data packets, directing them to the appropriate application or service running on the destination host. Demultiplexing serves as the gatekeeper, ensuring that each data stream reaches its intended recipient unscathed, thus facilitating seamless communication across networks.
TCP vs. UDP: Contrasting Communication Paradigms
In the realm of transport layer protocols, two stalwarts stand out: Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). While both protocols facilitate data transmission between devices, they differ significantly in their approach and characteristics.
TCP is frequently lauded as the dependable backbone of the internet, ensuring data integrity and sequential delivery. Through mechanisms like connection establishment, acknowledgment, and retransmission, TCP guarantees the reliable delivery of data packets, making it ideal for applications where accuracy and completeness are paramount, such as web browsing, file transfer, and email communication.
In contrast, UDP embraces a leaner, more expedient philosophy. As a connectionless protocol, UDP bypasses the complexities of connection setup and confirmation, prioritizing speed and efficiency at the expense of guaranteed delivery. While UDP sacrifices certain reliability features, it excels in scenarios where real-time data transmission and low-latency communication are critical, such as streaming media, online gaming, and voice over IP (VoIP) applications.
The Handshake: Establishing Trust
Three-way Handshake:
Central to the TCP communication paradigm is the venerable three-way handshake, a ritualistic dance between sender and receiver, culminating in the establishment of a reliable connection. This intricate choreography involves three key steps:
SYN (Synchronize): The journey begins with the client (initiator) sending a SYN packet to the server, signaling its intent to initiate a connection. This packet contains a sequence number, a random value chosen by the client to initiate communication.
SYN-ACK (Synchronize-Acknowledge): Upon receiving the SYN packet, the server responds with a SYN-ACK packet, acknowledging the client's request and indicating its readiness to establish a connection. The SYN-ACK packet contains both an acknowledgment of the client's sequence number and the server's own sequence number.
ACK (Acknowledge): Finally, the client acknowledges the server's response by sending an ACK packet, confirming the establishment of a bidirectional communication channel. With both parties synchronized and acknowledgments exchanged, data transmission can commence with confidence.
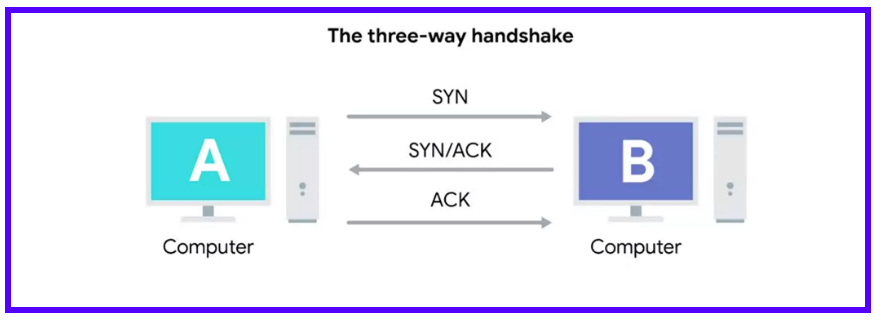
The TCP flags, embedded within the packet headers, play a pivotal role in orchestrating this intricate dance. From SYN to ACK, these flags serve as the cues that guide the flow of communication, ensuring that each step is executed with precision and adherence to protocol.
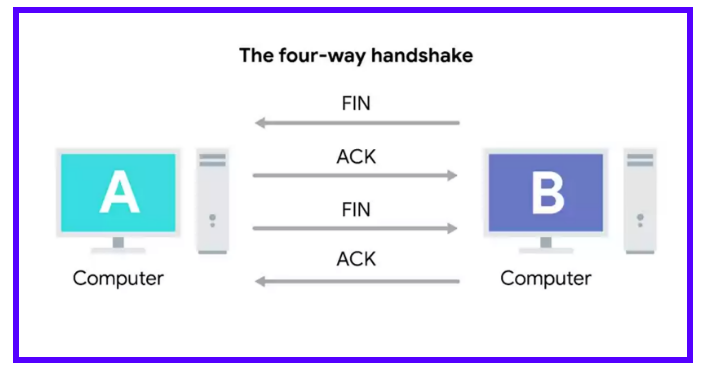
Four-way Handshake:
When a device is ready to close the connection, it sends a FIN flag which is acknowledged by the other computer with an ACK flag.
If the other computer is also ready to close the connection, it sends a FIN flag which then gets acknowledged by the first computer.
This exchange is known as the Four-way Handshake.
Connection-oriented and Connectionless Protocols
TCP is a connection-oriented protocol. It establishes a connection to ensure all data is properly transmitted.
A connection at the transport layer means every data segment sent is acknowledged. This helps both ends understand which data has been delivered and which hasn't.
Connection-oriented protocols are crucial due to the complexities of the internet. Traffic may not reach its destination due to various issues such as line errors, congestion, or physical disruptions like a cut fiber cable.
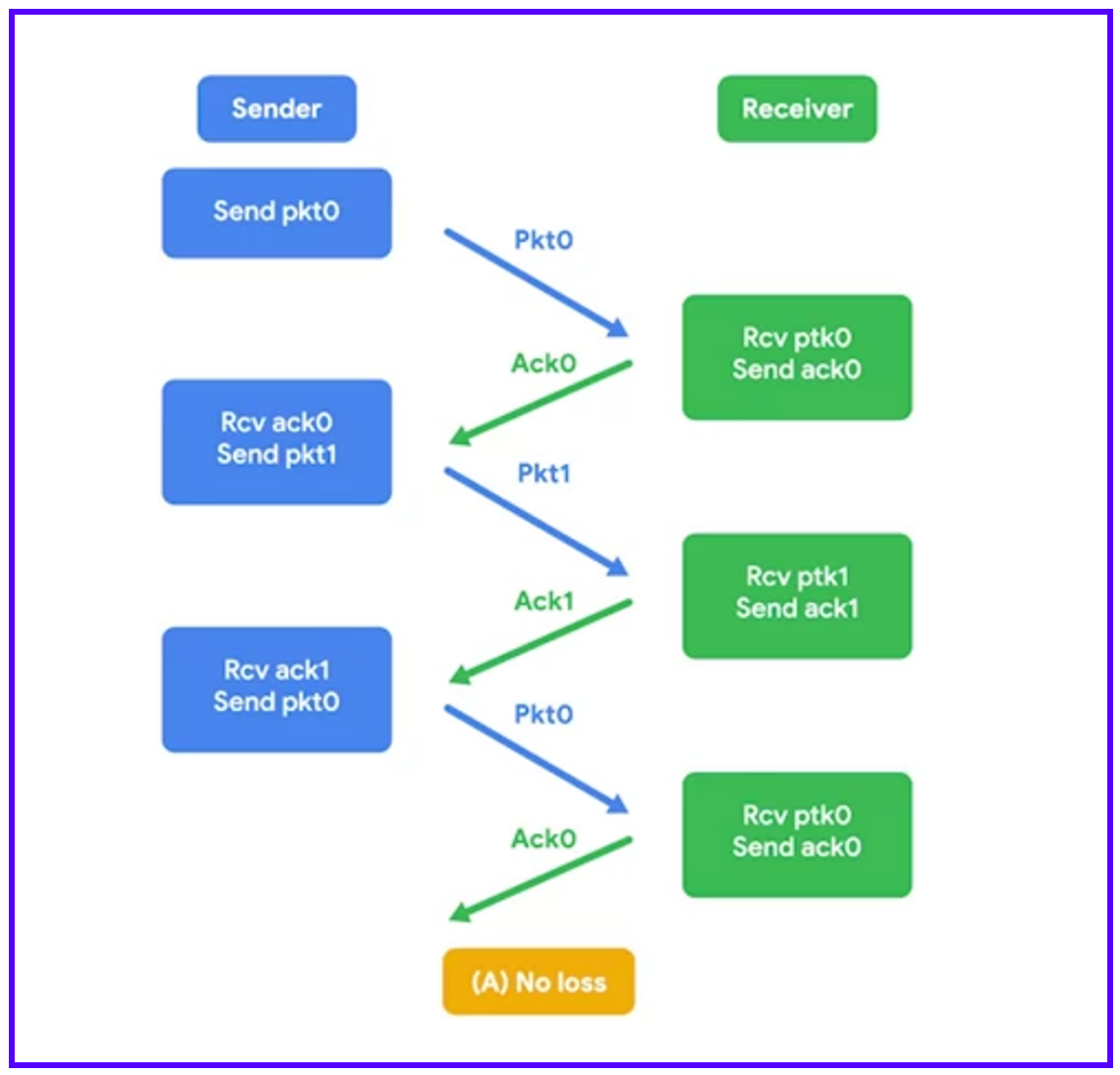
TCP protects against these issues by forming connections and maintaining a constant stream of acknowledgments.
Lower-level protocols like IP and Ethernet use check sums to confirm the correctness of received data. However, they do not resend data that doesn't pass this check. This decision is up to the transport layer protocol, like TCP.
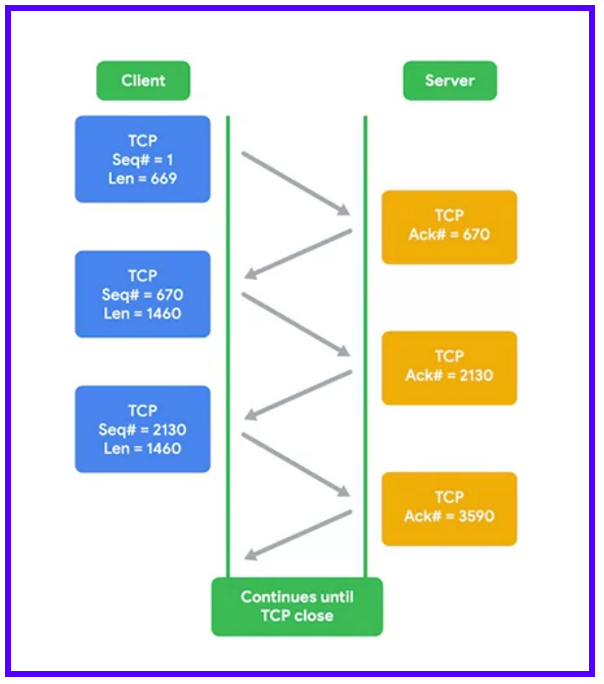
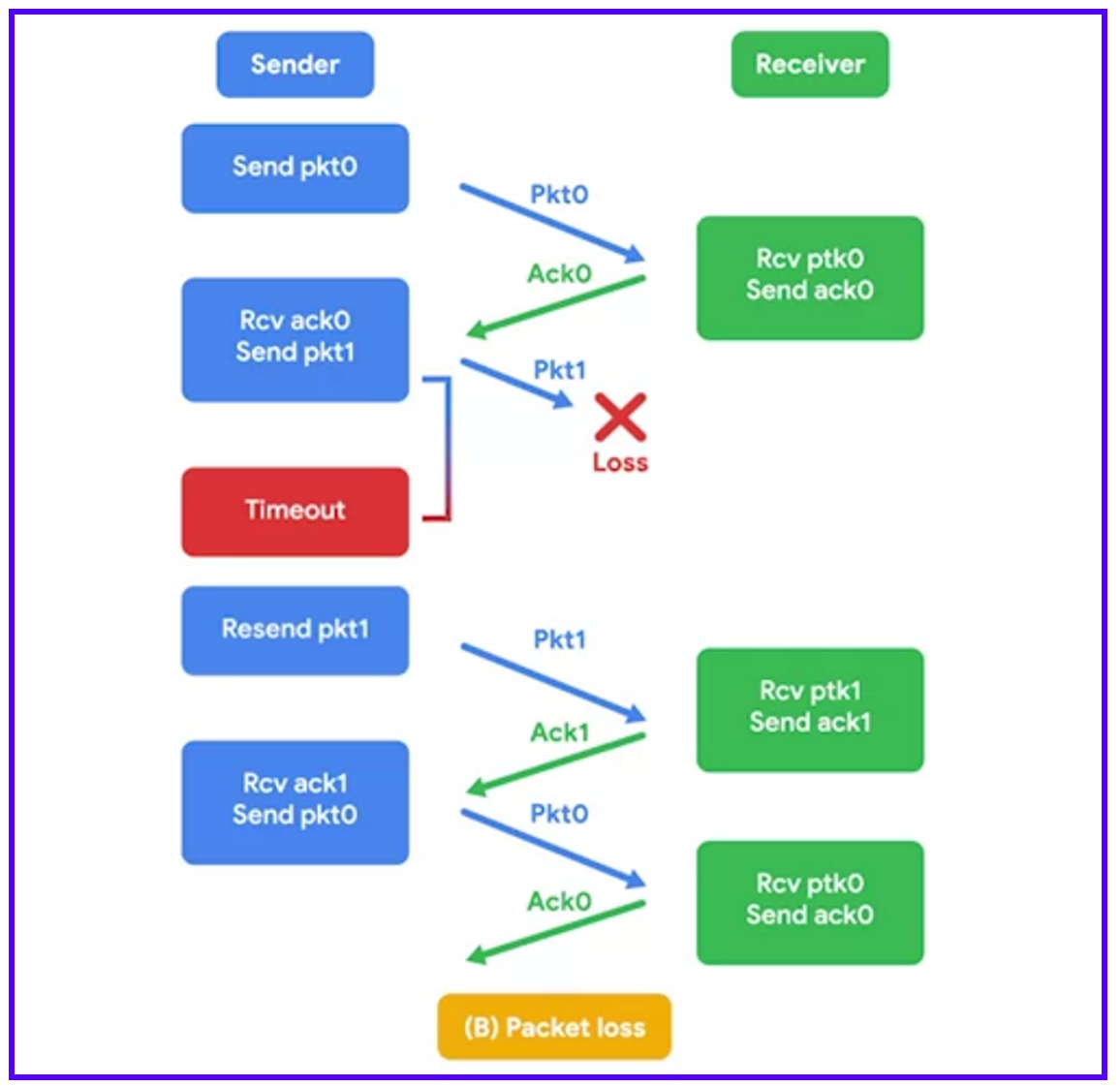
TCP can decide to resend data because it expects an acknowledgment (ACK) for every bit of data it sends.
Sequence numbers are vital. They allow data to be reassembled in the correct order, regardless of the order in which they arrive.
Connection-oriented protocols like TCP have significant overhead. They require connection establishment, a constant stream of acknowledgments, and connection termination. This results in a lot of extra traffic.
In contrast, UDP (User Datagram Protocol) is a connectionless protocol. It doesn't rely on connections or acknowledgments. You simply set a destination port and send the packet.
UDP is useful for non-critical messages. An example is streaming video where it doesn't significantly impact the viewing experience if a few frames are lost.
By eliminating the overhead of TCP, UDP may allow for higher quality video. This is due to more bandwidths being available for actual data transfer instead of connection and acknowledgment overhead.
Firewalls: Guardians of the Gateway
As networks traverse the vast expanse of cyberspace, they encounter numerous threats lurking in the shadows. Firewalls are the unsung heroes of network security, standing vigilant at the boundaries of our digital domains. They serve as robust sentinels, fortifying the perimeters of networks and repelling the advances of wicked cyber intruders. With a firewall in place, the integrity of a network's data and resources remains shielded from the relentless threats that lurk in the vast cyber wilderness..
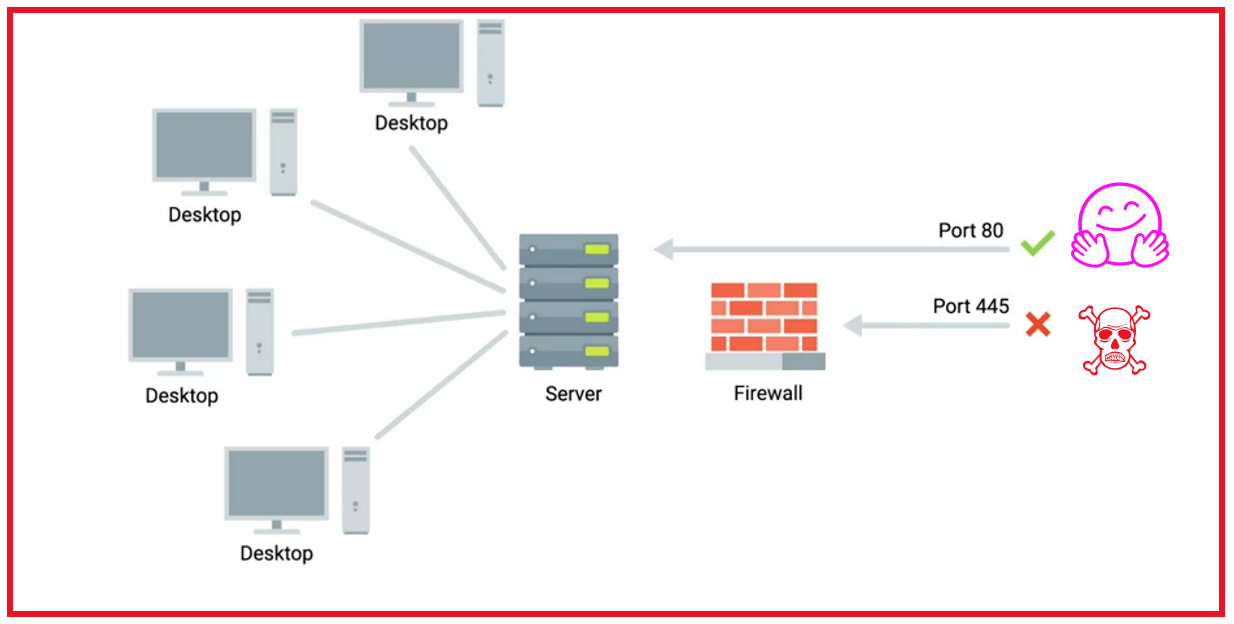
At its core, a firewall is a security appliance or software application designed to monitor and control incoming and outgoing network traffic based on predetermined security rules. By scrutinizing data packets against a set of predefined criteria, such as IP addresses, port numbers, and packet contents, firewalls act as gatekeepers, allowing legitimate traffic to pass while blocking or filtering unauthorized or potentially harmful communications.
Firewalls operate at various layers of the network stack, from basic packet filtering at the network layer to sophisticated application-layer inspection and deep packet inspection (DPI) techniques. Whether deployed as hardware appliances, software solutions, or cloud-based services, firewalls serve as the first line of defense in safeguarding networks against a diverse array of cyber threats, including malware, intrusion attempts, and denial-of-service (DoS) attacks.
In addition to traditional perimeter firewalls, modern network architectures often incorporate additional security measures, such as intrusion detection and prevention systems (IDPS), virtual private networks (VPNs), and network segmentation strategies, to bolster defenses and mitigate risk.
Conclusion: Navigating the Network Landscape
In the ever-evolving landscape of computer networks, understanding the core principles and mechanisms that underpin communication is essential for engineers, administrators, and users alike. From the intricacies of multiplexing and demultiplexing to the nuanced differences between TCP and UDP, from the ritualistic dance of the three-way handshake to the vigilant guardianship of firewalls, each concept plays a vital role in shaping the fabric of modern connectivity.
As we traverse the digital highways and byways, let us not merely navigate but comprehend the underlying infrastructure that enables our interconnected world to thrive. With knowledge as our compass and understanding as our guide, we embark on a journey of exploration and discovery, unraveling the mysteries of the network one packet at a time.
Subscribe to my newsletter
Read articles from Vijay Kumar Singh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Vijay Kumar Singh
Vijay Kumar Singh
I'm Vijay Kumar Singh, a Linux, DevOps, Cloud enthusiast learner and contributor in shell scripting, Python, networking, Kubernetes, Terraform, Ansible, Jenkins, and cloud (Azure, GCP, AWS) and basics of IT world. 💻✨ Constantly exploring innovative IT technologies, sharing insights, and learning from the incredible Hashnode community. 🌟 On a mission to build robust solutions and make a positive impact in the tech world. 🚀 Let's connect and grow together! #PowerToCloud