OSI Model (Open System Interconnection)
 Olpu Siva Reddy
Olpu Siva Reddy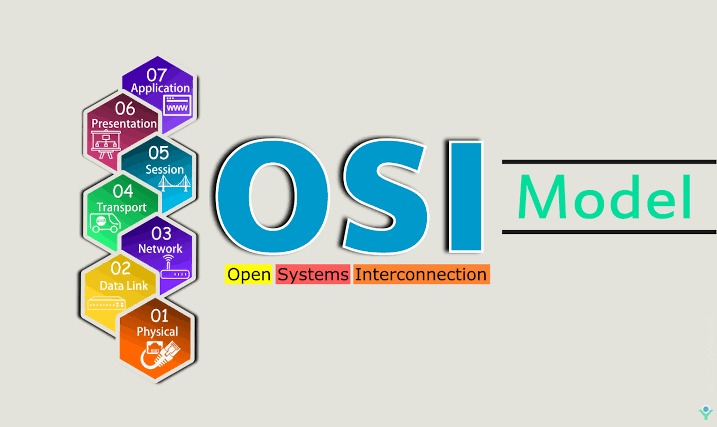
OSI model defines how the data is transferred between the two devices.
In the most basic form, if the two computers are based on same architecture and connected with LAN Cable and sharing data with the help NIC (Network interface card) that forms a network.
What if one device is based on windows and other is MAC OS, then how these computers are communicate?
So, in order to accomplish a successful communication between the two different architectures of devices or networks, 7 layer OSI model was introduced by ISO in the year 1984.
Introduction:
OSI model is a reference model, that describes the communication between the two connected devices in a network. OSI model divides the entire communication process into 7 layers, each layer has a specific function and all layers works together for seamless communication between the two devices.
The OSI Model Architecture Contains seven layers :
Application Layer
Presentation Layer
Session Layer
Transport Layer
Network Layer
Data link Layer
Physical Layer
Detailed overview of each Layer
Application Layer :
Application Layer is the top most layer in OSI model, the data unit in this layer called Data. All the major network applications uses this Application layer, applications like Google chrome, Mozilla Firefox, Outlook, File Transfer etc.
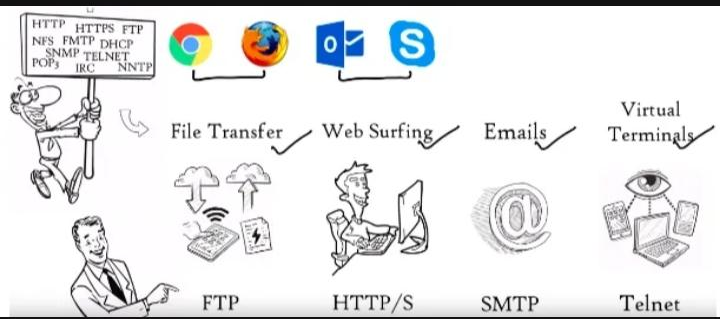
The Application layer consists of some protocols such as HTTP, HTTPs, FTP, POP3, SMTP, these protocols provides some services to the network applications.
HTTP/S: Hypertext Transfer Protocol, is an application Layer protocol, it was designed for communication between web browsers and web servers. HTTPs provides more security than HTTP. (Or) It is used to load or retrieve web pages from servers securely over the internet.
FTP : It is application Layer protocol, used for the transfer of files from server to client on a network.
SMTP - used by electronic mail transfer of webservers for to send and receive mail messages.
Presentation Layer
The presentation Layer receives Data from Application layer, that data is in the form of Alphabets and numbers. So, the machine can't understand Alphabets and numbers. So, Presentation Layer problems three main operations on that data, the operations are
Translation: As we know the presentation Layer receives Data from Application layer is in the form of Alphabets and numbers, So it gets converted into machine readable i.e in the form of 0's and 1's.
Compression : Data compression means reducing the size, by preserving data. This data compression can be achieved by the following technologies i.e
A. Lossy Compression : it is technology that lowers the size of data by deleting unnecessary information
B. Lossless Compression : it is a technology that lowers the size of original data but not up to greater extent, this type of technology can be preferred to transfer data using TCP protocol, because TCP focuses on delivery of message rather than the Speed.
Encryption/Decryption : to maintain integrity of data, the data needs to be encrypted at sender's end and decrypted at the receiver's end. This ensures the data data in not tampered or misused by any hacker as data travels along with the network.
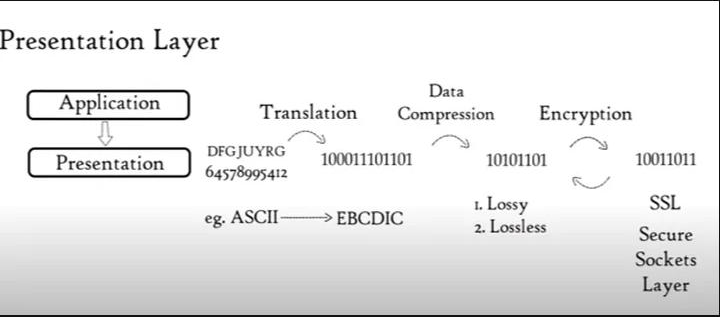
Finally, the presentation Layer is responsible for data translation, data compression and data encryption and Decryption.
Session Layer :
The Session Layer receives Data from the Presentation layer, and it is responsible for establishing, maintaining, and terminating the sessions between the end-user applications. It performs three basic functions:
Session management : Session management is the process of securing multiple requests to a service from the same user.
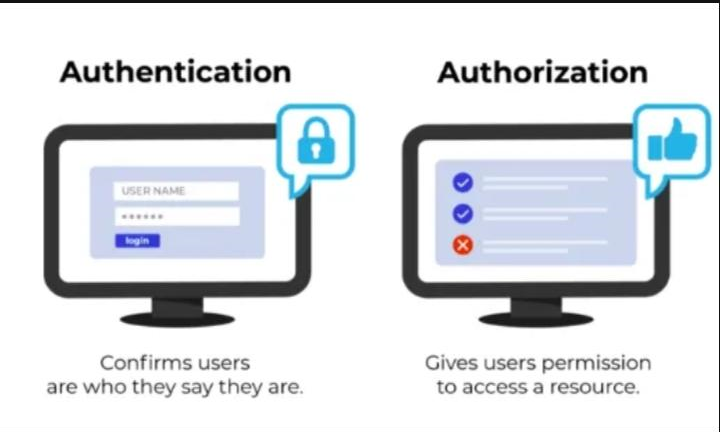
Authentication : it is the process of verifying the user who you are, this can be done by asking user to enter credentials like username and password. If the user entered records are matched then session gets created between client and server
Authorization : Authorization is the process of giving the user permission to access a specific resource.
Transport Layer:
The transport layer receives Data from the session layer, the transport layer divides the data from session layer into smaller units called segments.
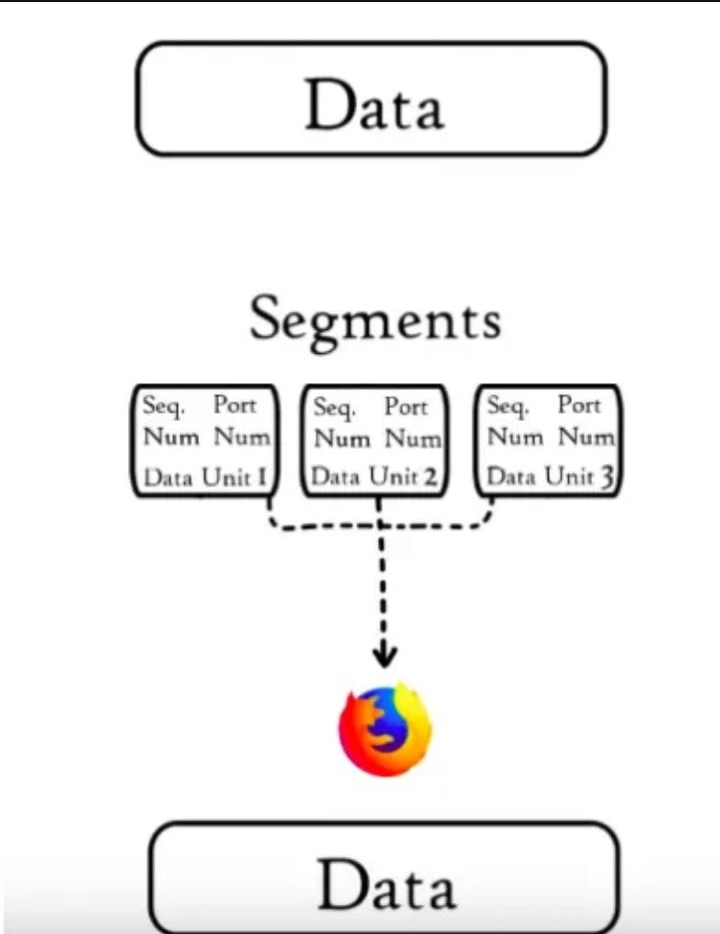
The Transport layer responsible for end to end delivery of a message from source to destination with the help of protocols like TCP or UDP
TCP : Transmission control protocol, it is a connection oriented protocol and reliable which means it focuses more on delivery of content rather than speed. TCP provides feedback and TCP is slower than UDP.
UDP : User datagram Protocol, it is a connection less protocol, and unreliable which means it focuses on speed of the message i.e how fast the message is delivered to destination rather than the delivery of content. UDP doesn't provides feedback, UDP is faster than TCP.
TCP provides functions like
Segmentation : Data received from the session layer gets divided into smaller units called segments and for each segment transport layer adds source and destination port number and sequence number that forms a Segment.
Port number, helps to identify each segment to its corresponding destination, whereas sequence number helps to reassembles data segments before it is presented to user.
Flow control : Transport layer controls the amount of data that is being transmitted.
Example — A server is sending the data at 50 Mbps to the client, and client has the capability to receive data at 10 Mbps. So, client with the help of transport layer sends request to the server to slowdown the data speed up to 10Mbps to manage data flow, so that no data gets lost and increases system performance.
Error control : Transport layer helps in error control, if some data doesn't arrive to the destination, the transport layer with the help of Automatic repeat Request schemes retransmit the lost data or corrupted data.
Network Layer:
The Network Layer received segments from the transport layer, now network layer assigns Source and Destination IP addresses to that segment to form a packet. IP addresses are assigned to ensure that data packets reach the correct destination.
The Network Layer is responsible for routing of packets from one network to another network with the help of Router. If the source and destination devices are in same N/W then there is no need of Router. The Network Layer is responsible for Logical Addressing, Routing, Path determination.
Logical Addressing: Assigning Sender and Receiver IP Addresses to the Segment, this process is called Logical Addressing.
Routing: Routing is the process of moving data packets from source to destination, routing always selects the best shortest path for the packet to reach destination.
Path determination: it is the process of finding the best path for the packet to reach destination. many devices can be connected in a network, choosing the best path for packet to reach destination. it uses various protocols to select the shortest path like OSPF, BGP, IS-IS.
Data Link Layer:
The data link layer receives packets from network layer, the data link adds Mac address, head and trail bits for the packet that forms a Frame. The data unit in the data link layer is called Ethernet Frame.
The data link layer is divided into two layers i.e Medium Access Control & Logical link control.
Medium Access Control: The Mac Sub Layer is responsible for Data encapsulation and Accessing the media, the mac sublayer adds header and trailer bits to the packet received from network layer. the header contains the MAC addresses of sender and receiver. the trailer contains 4 bytes of error checking data used to detect errors in the received frame.
For Accessing the Media, the data link layer uses CSMA/CD (Carrier sense multiple access/collision detection. In this method the devices in a network sense the carrier before transmitting data over a network, if the carrier is in used then the devices in a network wait until when the line is clear.
What is MAC Address ?
It is a unique 6 byte address embedded in the NIC of a device by its manufacturer.
Logical Link Layer:
The logical link layer offers Flow control and Error control
The Flow control restricts the amount of data sent by receiver.
Example — A server is sending the data at 50 Mbps to the client, and client has the capability to receive data at 10 Mbps. So, client with the help of transport layer sends request to the server to slowdown the data speed up to 10Mbps to manage data flow, so that no data gets lost and increases system performance.
Error Control: Error control is responsible for error detection and retransmission, error detection can be done by using error checking bytes added in the trailer of frame. The retransmission can be done using Automatic Repeat Request or ARQ, the receiver sends an ACK to sender when a frame is received, when the ACK is not received from receiver then sender sends the frame again. So, if the frame gets lost/ damaged then sender wont receive ACK signal from receiver then sender sends frame again this process is called retransmission.
Physical Layer:
The Physical layer receives frames from the data link layer, the physical layer divides the frames into raw bits (Also known as Signals) and then it transmits the raw data over the channel to reach the destination. These signals can be electrical signals in case of transmission is happening over copper wire (or) if the signal is light then transmission can be happening on optical fiber (or) if the signal is waves then transmission can be happening on air.
In this way the OSI Model helps to transfer data between two devices that are connected over the internet.
Subscribe to my newsletter
Read articles from Olpu Siva Reddy directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
