Security in VPC: Understanding NACLs and Security Groups in AWS
 Jasai Hansda
Jasai Hansda
When working with AWS (Amazon Web Services), managing the security of your network is crucial. Two primary tools for this purpose are Network Access Control Lists (NACLs) and Security Groups (SGs). Both serve as firewalls but operate at different levels and have distinct characteristics. Let's dive into their features and differences.
In the below image we can see two levels of security NACL and security group
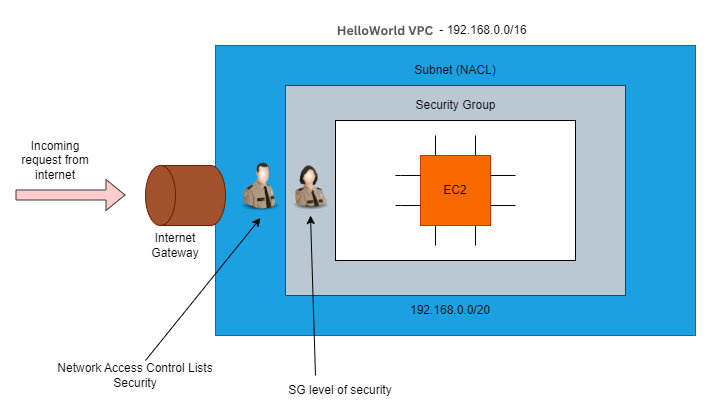
Network Access Control Lists (NACLs)
Subnet-Level Firewall: NACLs function as firewalls at the subnet level within your VPC (Virtual Private Cloud). They control inbound and outbound traffic to and from the subnet, applying rules to all instances within it.
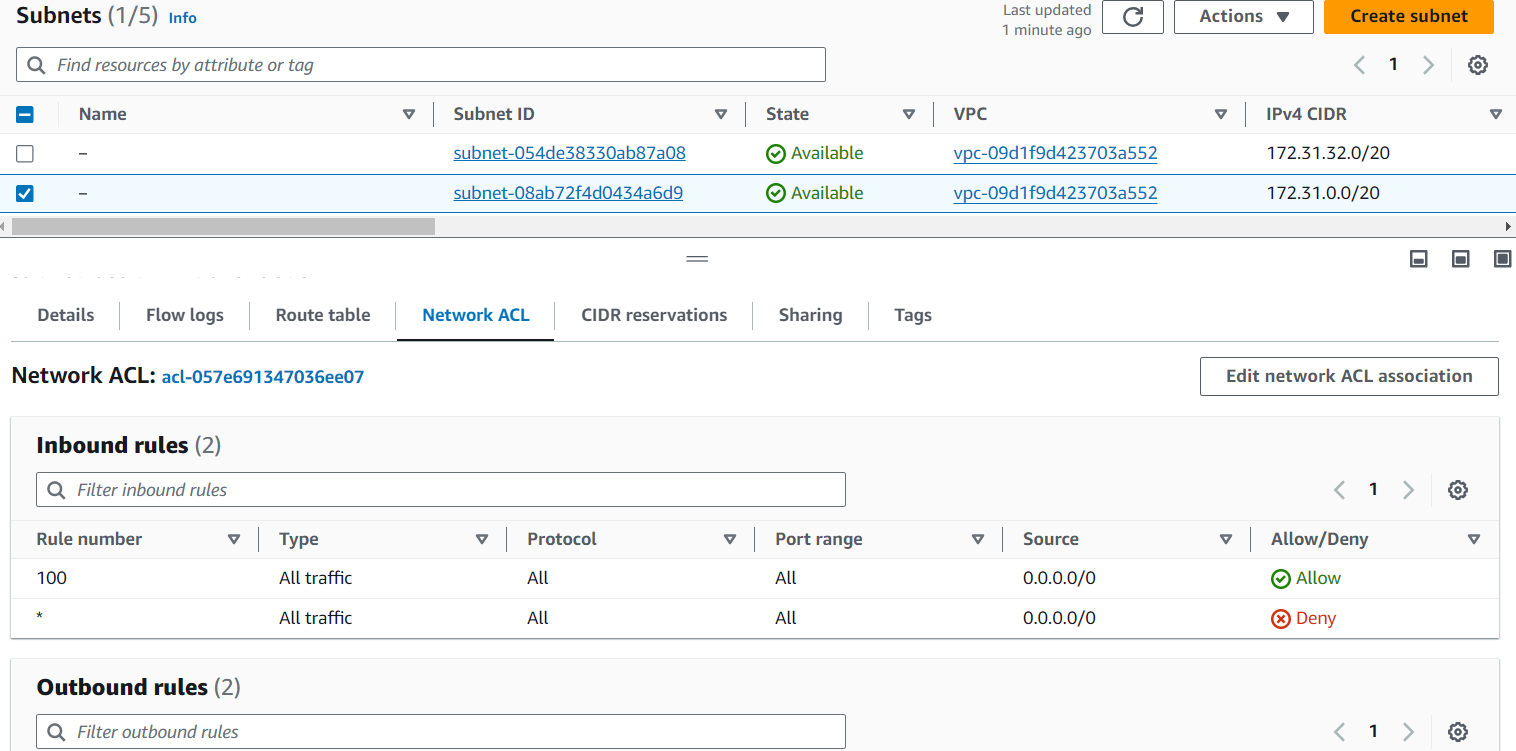
Stateless Filtering: NACLs are stateless, meaning they do not keep track of the state of connections. Each packet is evaluated against the NACL rules individually, regardless of whether it is part of an existing connection.
(Filtering refers to the process of controlling what data flows through a system. Imagine a bouncer at a club.
Stateful filtering: The bouncer remembers faces and checks if someone has already entered with a valid ID.
Stateless filtering: The bouncer only checks IDs at the door, not caring if someone snuck in another way.)
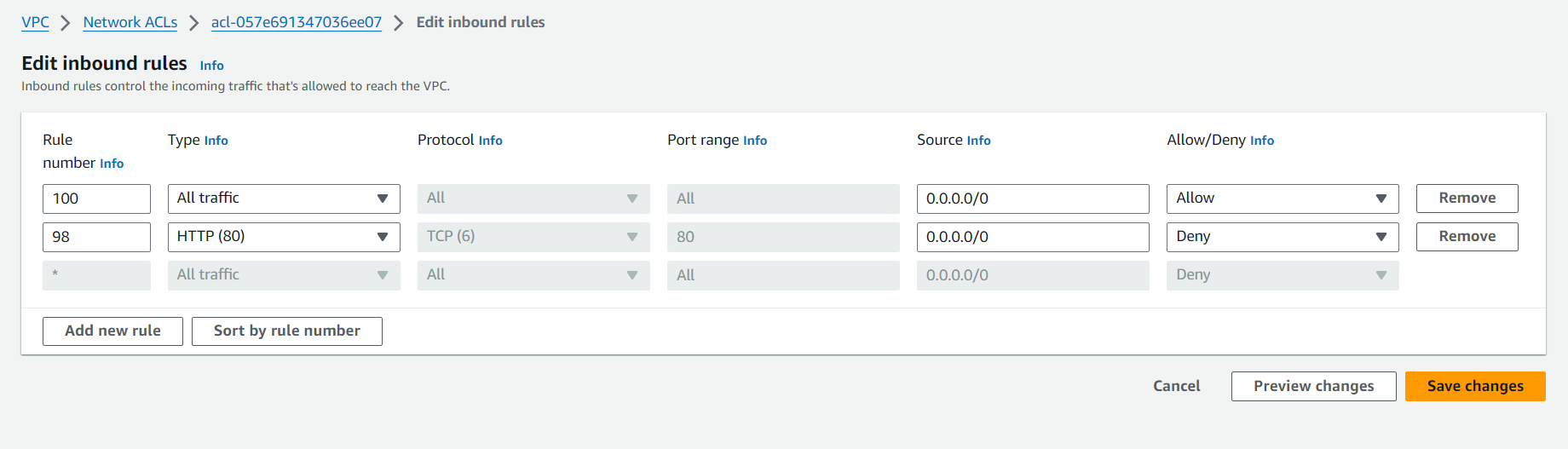
Default Behavior: By default, NACLs allow all inbound and outbound traffic. This means that unless you specify otherwise, any traffic is permitted through the NACL. There's an implicit "deny all" rule at the end (represented by an asterisk "*"). If no other rule matches, traffic is denied.
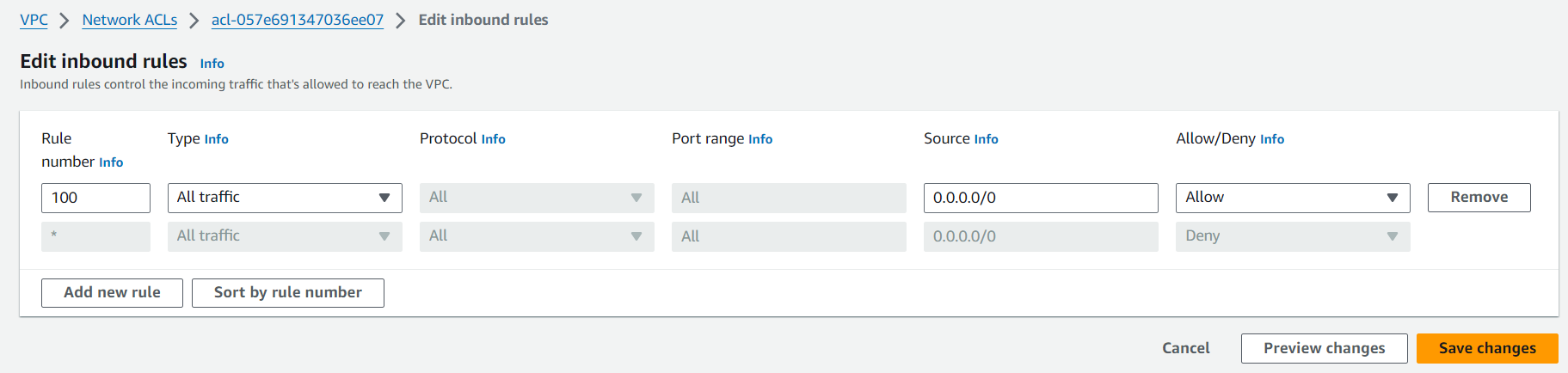
Rule Evaluation: NACL rules are evaluated in order, starting from the lowest numbered rule. This sequence is crucial because the first rule that matches the traffic type is applied, and no further rules are considered.
So, in the example below, you can see that rule no. 98 is the lowest numbered rule. In this case, it will deny the traffic from port 80.
Security Groups (SGs)
Instance-Level Firewall: Security Groups act as firewalls at the instance level. They control the inbound and outbound traffic for individual EC2 (Elastic Compute Cloud) instances.
Stateful Filtering: Unlike NACLs, Security Groups are stateful. This means that if an inbound rule allows traffic in, the corresponding outbound traffic is automatically allowed, and vice versa.
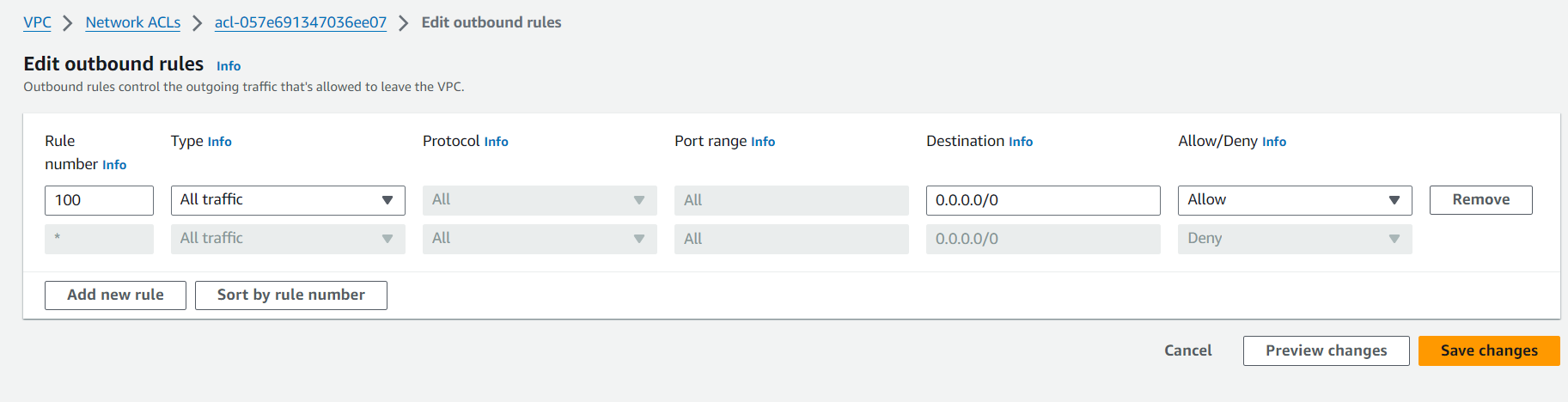
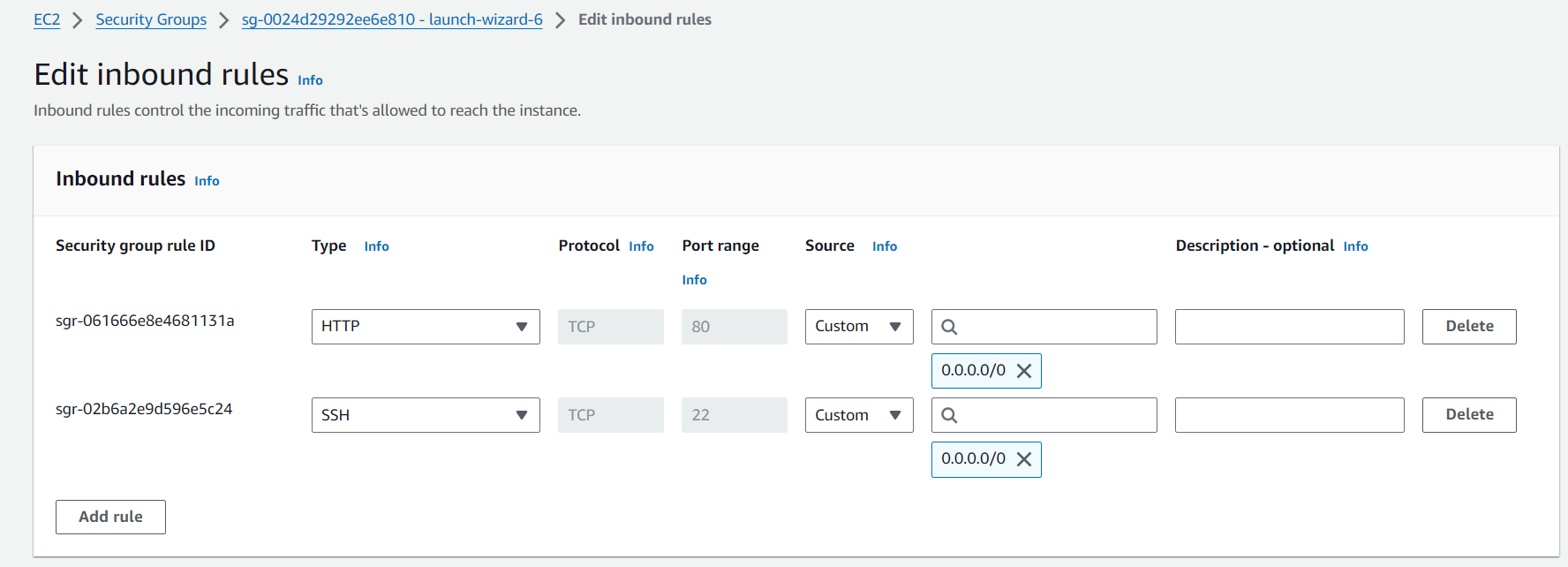
Default Behavior: By default, Security Groups block all inbound traffic and allow all outbound traffic. This ensures that no unsolicited inbound traffic can reach your instances unless explicitly allowed by your rules.
Here, in inbound rules, if any rule is not present, it will be blocked by default.
By default, the outbound rule allows all traffic.
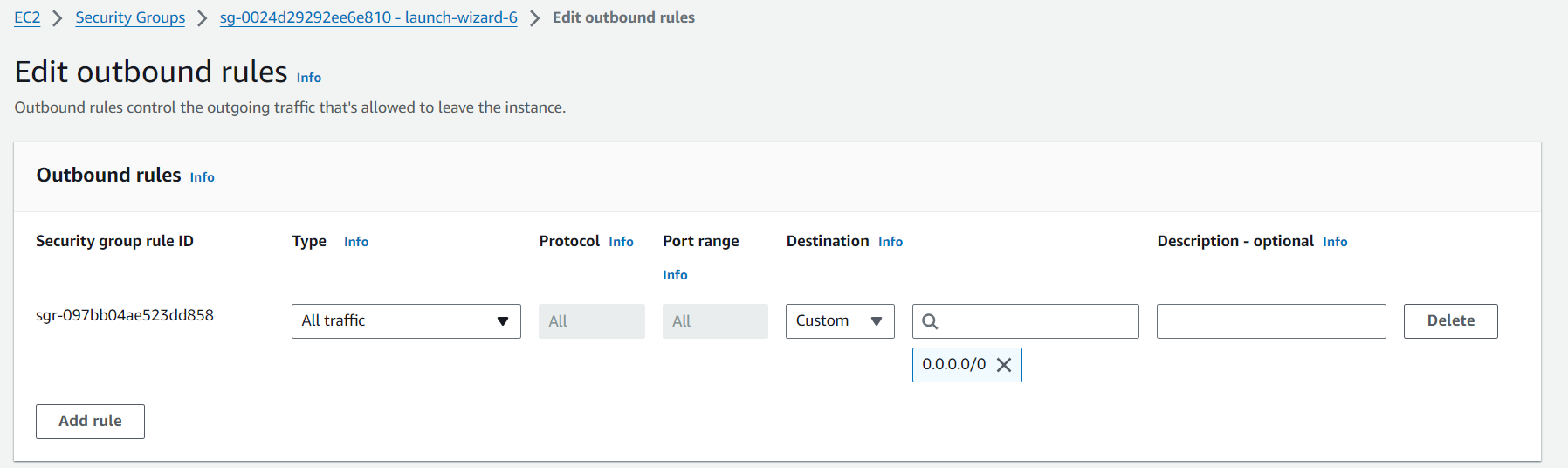
Rule Evaluation: Security Group rules are evaluated differently from NACLs. Since they are stateful, the order of rules does not matter. If any rule allows the traffic, it is permitted. The rule that grants the most access (allows the traffic) takes precedence. This means even if a later rule denies the traffic, the earlier permissive rule allows it
Example:
Rule 1: Allow SSH access (TCP port 22) from anywhere (0.0.0.0/0). This is a very permissive rule.
Rule 2: Allow HTTP traffic (TCP port 80) only from a specific IP address (e.g., 10.0.1.100). This is a more restrictive rule.
Scenario:
If someone tries to access the instance via SSH (port 22) from an IP address other than 10.0.1.100, the following happens:
Rule 1 and 2 are evaluated.
Rule 1 is more permissive as it allows access from anywhere for SSH.
Even though Rule 2 denies access from other IPs for port 80, it doesn't affect the SSH access allowed by Rule 1.
The SSH connection is successful (assuming proper credentials are provided).
Key Differences
Level of Operation: NACLs operate at the subnet level, affecting all instances within a subnet. Security Groups operate at the instance level, affecting only the specific instance they are associated with.
Statefulness: NACLs are stateless, requiring explicit rules for both inbound and outbound traffic. Security Groups are stateful, simplifying rule management by automatically allowing related traffic.
Default Rules: NACLs allow all traffic by default, while Security Groups block all inbound traffic and allow all outbound traffic by default.
Rule Processing: NACLsevaluate rules in numerical order, stopping at the first match. Security Groups evaluate all rules without regard to order, allowing traffic if any rule matches.
Analogy
Imagine an airport with two security checkpoints:
NACL (Passport Officer):
This checkpoint is at the entry gate (like a subnet), controlling everyone entering the airport (like traffic flow).
The passport officer (like an NACL) checks everyone's documents (like traffic packets).
They have a set of rules (like NACL rules):
Valid passport (like allowed protocol)
Valid visa for the destination country (like allowed port)
The officer checks documents in a specific order (like rule evaluation order).
If everything matches a rule (valid documents for the destination), they allow entry (permit traffic).
If any document is invalid or there's no matching rule, they deny entry (block traffic).
There's a final, implicit rule: "Deny entry if no valid documents" (like a default deny-all rule).
Security Guard (Security Group):
This checkpoint is at the boarding gate (like an instance).
Security guards (like security groups) only check passengers for specific flights (like specific instances).
They may have additional rules (like security group rules):
Boarding pass for the specific flight (like allowed traffic from another security group).
Carrying any prohibited items (like denying specific ports).
Unlike passport officers, guards check everyone regardless of order (all rules evaluated).
If any rule allows boarding (e.g., valid boarding pass), the passenger can proceed (traffic allowed).
Even if another rule denies boarding (e.g., prohibited item), the passenger can still go if the first rule allows it (most permissive wins).
There's no default rule here. By default, passengers can board if they have a boarding pass (outbound traffic typically allowed).
In essence:
NACLs act as a general check for everyone entering the airport (like traffic entering the subnet), ensuring they have the necessary documentation (valid protocols and ports).
Security groups provide more specific checks for passengers at boarding gates (like instances), ensuring they are authorized for that specific flight (traffic flow to and from the instance).
This analogy highlights how NACLs and security groups work together to secure your network traffic in an AWS VPC.
Conclusion
Understanding the differences between NACLs and Security Groups is essential for designing secure and efficient AWS architectures. NACLs provide a broad, subnet-level control, suitable for coarse-grained security policies, while Security Groups offer fine-grained control at the instance level, ideal for specific application needs. By leveraging both, you can create a layered security approach, enhancing the overall security posture of your AWS environment.
Subscribe to my newsletter
Read articles from Jasai Hansda directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jasai Hansda
Jasai Hansda
Software Engineer (2 years) | In-transition to DevOps. Passionate about building and deploying software efficiently. Eager to leverage my development background in the DevOps and cloud computing world. Open to new opportunities!