API Gateway Deployment Using AWS CloudFormation
 Mahira Technology Private Limited
Mahira Technology Private Limited

Introduction :-
This document provides instructions and an explanation of the AWS CloudFormation template for deploying an API Gateway. The template defines a set of AWS resources and configurations to create the API Gateway, custom domains.
Template Structure
The CloudFormation template is written in YAML format and is structured as follows:
AWSTemplateFormatVersion: Specifies the template version.
Transform: Uses the
AWS::Serverless-2016-10-31transform.Parameters: Input parameters for customization.
Conditions: Conditional logic based on parameter values.
Resources: Definitions of AWS resources.
Outputs: Stack outputs for reference.
Deployment Steps
Follow these steps to upload and create the CloudFormation stack using the AWS Management Console:
- Sign in to the AWS Management Console: Log in to your AWS account if you haven’t already.
2. Navigate to CloudFormation: Go to the AWS CloudFormation service from the AWS Management Console.
3. Click the “Create stack” button.
4. Upload the CloudFormation template file (YAML).
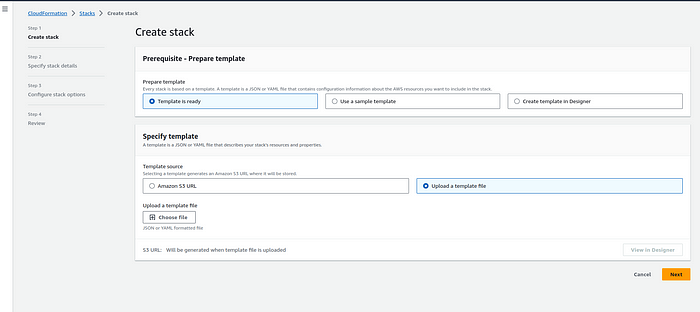
Yaml File :
AWSTemplateFormatVersion: '2010–09–09'
Transform: AWS::Serverless-2016–10–31
Description: 'AWS CloudFormation Template Api Gateway.'
Parameters:
EnvironmentName:
Description: Environment name for the application - [dev/staging/production]
Type: String
AllowedValues:
- dev
- staging
- production
ApiGatewayName:
Type: String
Default: aip-api-gw
CorsAllowOrigins:
Type: String
Description: Comma seperated list of origins from where API calls are allowed
DomainName:
Type: String
CertificateArn:
Type: String
Route53HostedZoneId:
Type: String
JwtIssuer:
Type: String
FrontendAppClientId:
Type: String
Conditions:
DomainNotEmpty: !Not [!Equals [!Ref DomainName, '']]
Resources:
ApiGateway:
Type: AWS::ApiGatewayV2::Api
Properties:
Name: !Sub ${EnvironmentName}-${ApiGatewayName}
Description: AIP Api Gateway
ProtocolType: HTTP
Version: '0.1'
CorsConfiguration:
AllowCredentials: true
AllowHeaders:
- '*'
AllowMethods:
- OPTIONS
- GET
- POST
- PUT
- PATCH
- DELETE
AllowOrigins: !Split [',', !Ref CorsAllowOrigins]
MaxAge: 0
RestApiAuthorizer:
Type: AWS::ApiGatewayV2::Authorizer
Properties:
ApiId: !Ref ApiGateway
AuthorizerType: JWT
IdentitySource:
- '$request.header.Authorization'
JwtConfiguration:
Issuer:
!Ref JwtIssuer
Name: JwtAuthorizer
ApiLogGroup:
Type: AWS::Logs::LogGroup
Properties:
LogGroupName: !Sub '/aws/API-Gateway/${AWS::StackName}/access-logs'
RetentionInDays: 7
ApiStage:
Type: 'AWS::ApiGatewayV2::Stage'
Properties:
StageName: !Ref EnvironmentName
AutoDeploy: true
ApiId: !Ref ApiGateway
AccessLogSettings:
DestinationArn:
Fn::GetAtt: [ApiLogGroup, Arn]
RouterDomainName:
Type: 'AWS::ApiGatewayV2::DomainName'
Condition: DomainNotEmpty
Properties:
DomainName: !Ref DomainName
DomainNameConfigurations:
- EndpointType: REGIONAL
CertificateArn: !Ref CertificateArn
CertificateName: !Ref DomainName
ApiMapping:
Type: 'AWS::ApiGatewayV2::ApiMapping'
Condition: DomainNotEmpty
Properties:
DomainName: !Ref RouterDomainName
ApiId: !Ref ApiGateway
Stage: !Ref ApiStage
DNSRecordSet:
Type: AWS::Route53::RecordSet
Condition: DomainNotEmpty
Properties:
HostedZoneId: !Ref Route53HostedZoneId
Type: A
Name: !Ref DomainName
AliasTarget:
DNSName:
Fn::GetAtt: RouterDomainName.RegionalDomainName
HostedZoneId:
Fn::GetAtt: RouterDomainName.RegionalHostedZoneId
Outputs:
Region:
Description: 'Region'
Value: !Ref AWS::Region
ApiGatewayLogGroup:
Description: 'Api Gateway Log Group'
Value:
Fn::GetAtt: [ApiLogGroup, Arn]
Export:
Name: !Sub '${AWS::StackName}-ApiGatewayLogGroup'
ApiGatewayEndpoint:
Description: 'Api Gateway Endpoint'
Value: !Sub 'https://${ApiGateway}.execute-api.${AWS::Region}.amazonaws.com/${EnvironmentName}/'
Export:
Name: !Sub '${AWS::StackName}-ApiGatewayEndpoint'
ApiGatewayId:
Description: 'Api Gateway ID'
Value: !Ref ApiGateway
Export:
Name: !Sub '${AWS::StackName}-ApiGatewayId'
ApiGatewayJWTAuthorizer:
Description: 'Api Gateway JWT Authorizer'
Value: !Ref RestApiAuthorizer
Export:
Name: !Sub '${AWS::StackName}-ApiGatewayJWTAuthorizer'
5. Specify Stack Details:
Enter a Stack name for your deployment.
Provide parameter values as needed, such as
EnvironmentName,ApiGatewayName, and others.Review and acknowledge the capabilities (if required).
You can set additional stack options or tags if necessary.
6. Review and Create:
Review the stack details and configuration.
Click “Create stack” to initiate the deployment.
7. Monitor Stack Creation:
The CloudFormation stack creation process will begin.
Monitor the stack events in the AWS Management Console.
Once the stack creation is successful, the API Gateway will be deployed.
After successful stack creation, you can find the following outputs for reference:
Region: The AWS region where the stack was deployed.
ApiGatewayLogGroup: The CloudWatch Logs log group for the API Gateway.
ApiGatewayEndpoint: The endpoint URL of the API Gateway.
ApiGatewayId: The ID of the API Gateway.
ApiGatewayJWTAuthorizer: The JWT authorizer for the API Gateway.
conclusion :-
AWS CloudFormation is a valuable tool for deploying and managing AWS resources, including API Gateway. By following best practices and leveraging the capabilities of CloudFormation, you can streamline your API Gateway deployment process, improve infrastructure management, and ensure the reliability and scalability of your APIs.
Subscribe to my newsletter
Read articles from Mahira Technology Private Limited directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Mahira Technology Private Limited
Mahira Technology Private Limited
A leading tech consulting firm specializing in innovative solutions. Experts in cloud, DevOps, automation, data analytics & more. Trusted technology partner.