NetworkPolicy in Kubernetes with example
 Gaurav Kumar
Gaurav Kumar
Introduction
In Kubernetes we can deploy as many as pods which is for different application or have specific usage, by default in Kubernetes cluster all pods can communicate to each other but If we want some specific pods to not be communicated by other pod we can apply Network Policy on that and can disable Ingress traffic to pod and Egress traffic from that Pod. This will ensure that our Pod will be secure from unauthorized access.
Why we need Network Policies?
In a Kubernetes environment, pods can be dynamically scheduled across any available nodes. This fluidity makes traditional network security measures, like IP-based firewall rules, inadequate. Network Policies fill this gap by allowing administrators to define and enforce rules which dictate how pods can communicate with each other or to external resources. This ensures that only authorized traffic flows between pods, which can prevent potential data leaks.
Types of Kubernetes Network Policies
Ingress Policies
Egress Policies
Understanding Network Policies by example
Let's understand Network Policies by deploying two pods and then applying Network Policies on it and then will check whether it is still able to communicate with other pod or not.
Step-1: Creating two Deployment named
Here I am creating two deployment named pod-1 & pod-2 using nginx image for that we need to create two files dep-1.yaml and dep-2.yaml and we need to put the below code into that.
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: pod-1
name: pod-1
spec:
replicas: 1
selector:
matchLabels:
app: pod-1
template:
metadata:
labels:
app: pod-1
spec:
containers:
- image: nginx
name: nginx
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: pod-2
name: pod-2
spec:
replicas: 1
selector:
matchLabels:
app: pod-2
template:
metadata:
labels:
app: pod-2
spec:
containers:
- image: nginx
name: nginx
Now apply both deployments using below command.
kubectl apply -f dep-1.yaml
kubectl apply -f dep-2.yaml
Step-2: Verifying Pods communication without applying Network Policies
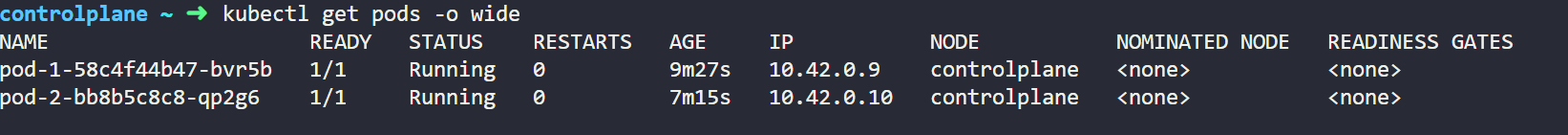
As we know that pods can communicate with each other if we will not enforce any Network Policies on them so let's verify that for that we need to get the IP details assigned to our pod, for that we need to type below command and output will show the IP address assigned to that pod.
kubectl get pods -o wide
Here below we can see that it has shown the IP address of both pod-1 and pod-2.
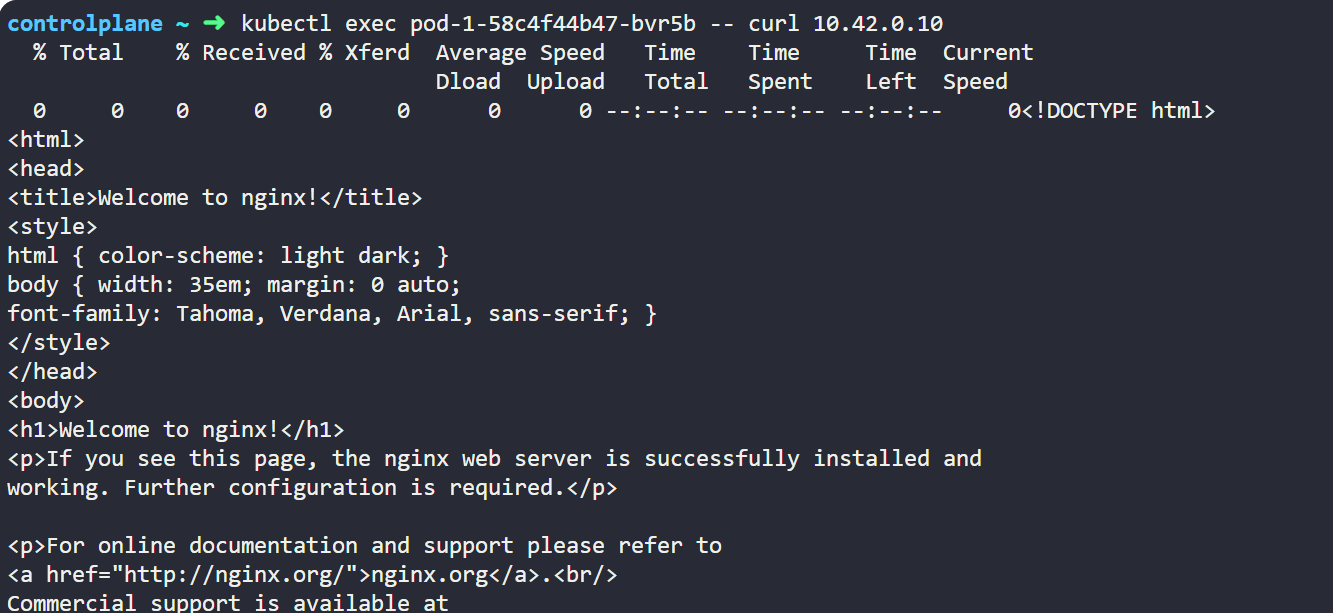
Now Let's get into pod-1 and try to communicate with pod-2 by its IP address. For that we need to type below command.
kubectl exec <pod-1-name> -- curl <pod-2-IP>
When we will give the above command we will see that it has successfully communicated with pod-2 and will see below output.
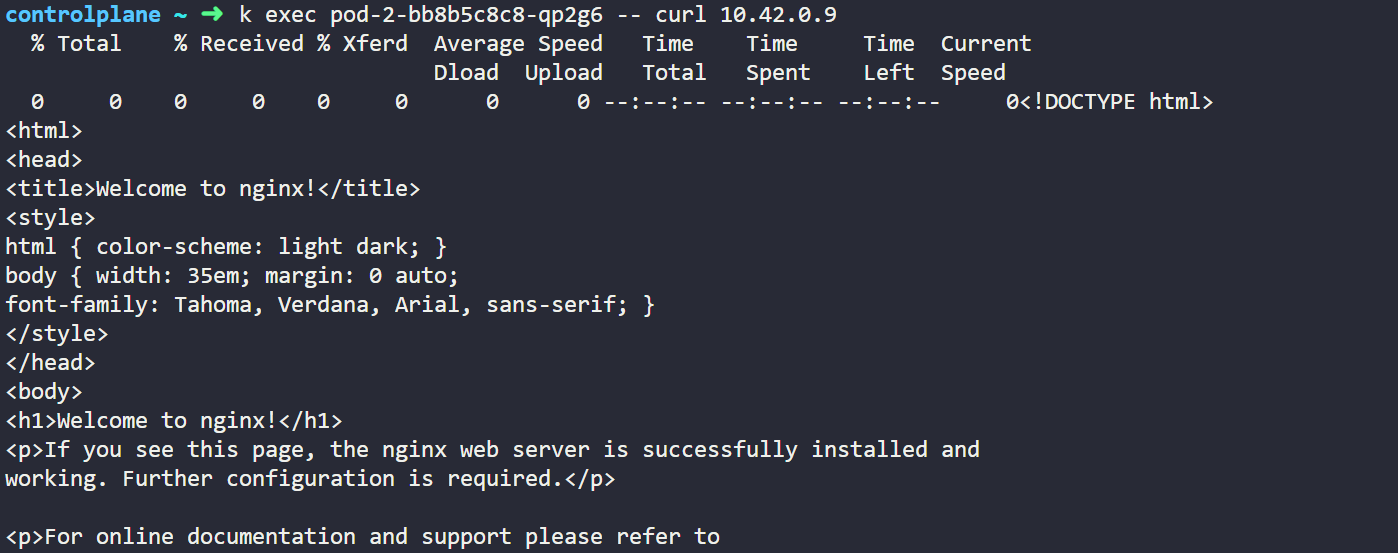
Now Let's do the same but now from pod-2 to pod-1 communication, we will follow same steps.
kubectl exec <pod-2-name> -- curl <pod-1-IP>
We will again found that pod-2 can also communicate with pod-1 without any issues which we can verify with below output.
Step-3: Applying Network Policies on pod-1
Now let's apply network policies on pod-1, for that we need to create a file named np.yaml and we need to put below code into that.
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-ingress-from-pod-2
namespace: default
spec:
podSelector:
matchLabels:
app: pod-1
policyTypes:
- Ingress
- Egress
ingress:
- from:
- podSelector:
matchLabels:
app: pod-2
ports:
- protocol: TCP
port: 80
egress: []
Here in the above Network Policies file we have several things to understand which is explained below.
podSelector:
It selects pods to which this policy applies, here in our case we are applying this Network Policies on pod-1 that's why we have provided app as pod-1.
policyTypes:
Here we specify which policies we want to apply on mentioned pod, ingress, egress or both type of traffic in our case we have specified both.
ingress:
Here we have from section under that we have podSelector where we need to specify from which pod we want ingress traffic to come from in our case it is allowing ingress traffic from pod-2.
ports:
It specifies allowed ports for the traffic which is 80 in our case and TCP as a protocol.
egress:
Here in egress section since I have defined it as empty so it will block all egress or outgoing traffic from pod-1.
Now let's apply this Network Policy and then we will check the communication now.
kubectl apply -f np.yaml
Step-4: Verifying Communication after applying Network Policy
Now we have applied Network Policy on pod-1 and in that we have blocked all outgoing (egress) traffic from pod-1 and only allowed incoming traffic from pod-2.
Let's first check that whether pod-1 is still able to communicate with pod-2 or not because we have blocked all outgoing traffic from it.
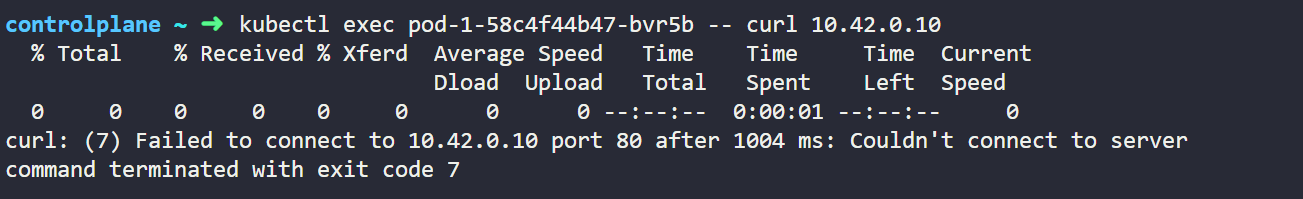
kubectl exec <pod-1-name> -- curl <pod-2-IP>
We can see by below output that now pod-1 is not able to communicate with pod-2.
Now let's verify whether pod-2 can communicate with pod-1 or not as we have enabled incoming traffic to pod-1.
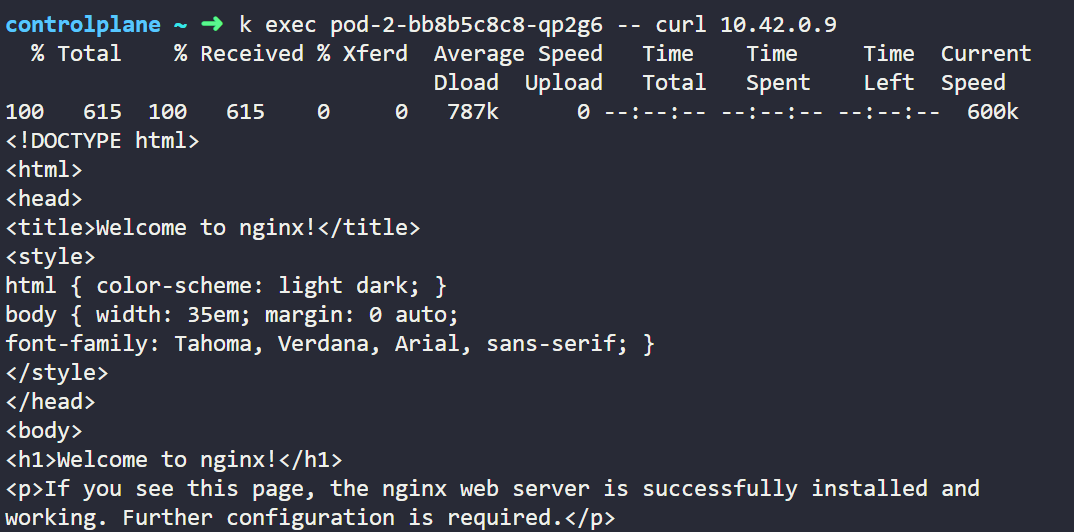
kubectl exec <pod-2-name> -- curl <pod-1-IP>
We can see that pod-2 can still communicate with pod-1 which we can verify from below output.
So we have understood the concept of Network Policies in Kubernetes and also we have verified that from deployments. That's it from my end. For more such content follow my blogs.
Subscribe to my newsletter
Read articles from Gaurav Kumar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Gaurav Kumar
Gaurav Kumar
I am working as a full time DevOps Engineer at Tata Consultancy Services from past 2.7 yrs, I have very good experience of containerization tools Docker, Kubernetes, OpenShift. I have good experience of using Ansible, Terraform and others.