Mastering Cybersecurity: Day 4 of the 100-Day Challenge
 Mallika Gautam
Mallika Gautam
CIA Traid Model
Let's get started!
The CIA triad is a model that helps inform how organizations consider risk when setting up systems and security policies. As a reminder, the three letters in the CIA triad stand for confidentiality, integrity, and availability.
Confidentiality means that only authorized users can access specific assets or data. Sensitive data should be available on a "need to know" basis, so that only the people who are authorized to handle certain assets or data have access.
Integrity means that the data is correct, authentic, and reliable. Determining the integrity of data and analyzing how it's used .
Availability means that the data is accessible to those who are authorized to access it. Inaccessible data isn't useful and can prevent people from being able to do their jobs.
Use of the CIA triad to protect organizations
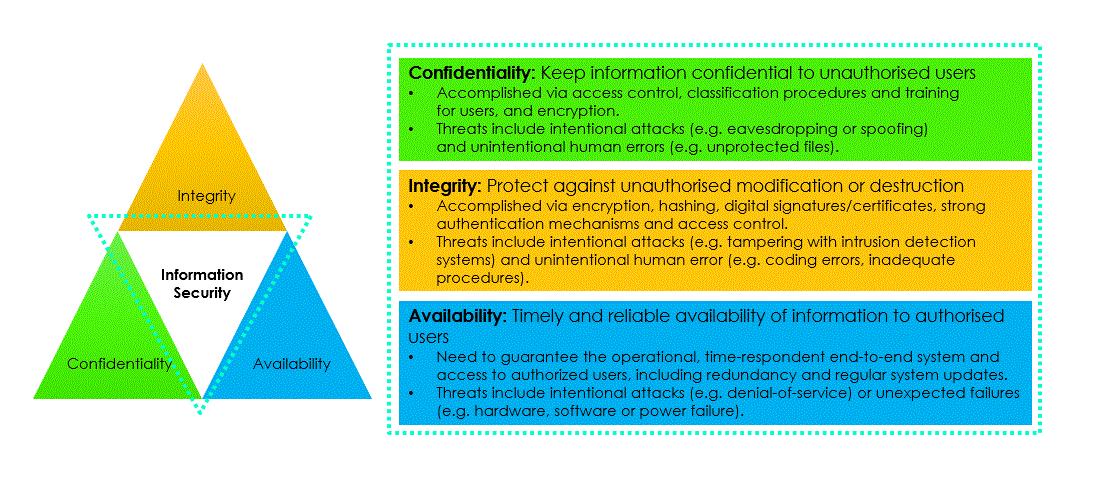
The CIA triad is a model that helps inform how organizations consider risk when setting up systems and security policies. It is made up of three elements that cybersecurity analysts and organizations work toward upholding: confidentiality, integrity, and availability. Maintaining an acceptable level of risk and ensuring systems and policies are designed with these elements in mind helps establish a successful security posture, which refers to an organization’s ability to manage its defense of critical assets and data and react to change.
Confidentiality is the idea that only authorized users can access specific assets or data. In an organization, confidentiality can be enhanced through the implementation of design principles, such as the principle of least privilege. The principle of least privilege limits users' access to only the information they need to complete work-related tasks. Limiting access is one way of maintaining the confidentiality and security of private data.
Integrity is the idea that the data is verifiably correct, authentic, and reliable. Having protocols in place to verify the authenticity of data is essential. One way to verify data integrity is through cryptography, which is used to transform data so unauthorized parties cannot read or tamper with it (NIST, 2022). Another example of how an organization might implement integrity is by enabling encryption, which is the process of converting data from a readable format to an encoded format. Encryption can be used to prevent access and ensure data, such as messages on an organization's internal chat platform, cannot be tampered with.
Availability is the idea that data is accessible to those who are authorized to use it. When a system adheres to both availability and confidentiality principles, data can be used when needed. In the workplace, this could mean that the organization allows remote employees to access its internal network to perform their jobs. It’s worth noting that access to data on the internal network is still limited, depending on what type of access employees need to do their jobs. If, for example, an employee works in the organization’s accounting department, they might need access to corporate accounts but not data related to ongoing development projects.
In conclusion, the CIA triad is a crucial framework for cybersecurity that helps organizations safeguard their data and systems. By focusing on confidentiality, organizations can protect sensitive information from unauthorized access. Ensuring data integrity maintains the accuracy and reliability of information, while availability guarantees that data is accessible to those who need it. Implementing the principles of the CIA triad allows organizations to manage risks effectively, maintain operational efficiency, and build a strong security posture to defend against potential threats.
Subscribe to my newsletter
Read articles from Mallika Gautam directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Mallika Gautam
Mallika Gautam
designer & cyber security student :)