Automating Amazon SES Domain Identity Verification Configuration with Terraform
 Mahira Technology Private Limited
Mahira Technology Private Limited

Introduction :-
In the realm of cloud infrastructure, managing email communications efficiently is a paramount concern. Amazon Simple Email Service (SES) is a powerful solution for sending and receiving emails, but ensuring your domain’s identity is verified is a crucial step in establishing trust with email recipients. In this guide, we’ll explore how to automate the configuration of SES domain identity verification using Terraform, streamlining the process and enhancing the reliability of your email delivery.
Pre-requestites :-
An Aws account with full access
Terraform should be installed on your local machine.
Deployment Steps for creating ses with domain identity verification:-
Create a directory with name ses_domain. Within the directory create terraform configuration files such as main.tf, variables.tf and provider.tf .
Below is the terraform code to create a ses_domain identities.
#main.tf
resource "aws_ses_configuration_set" "config_set" {
name = "config-set"
reputation_metrics_enabled = true
}
resource "aws_ses_domain_identity" "domain_identity" {
domain = var.domain_name
}
resource "aws_ses_domain_dkim" "dkim_identity" {
domain = aws_ses_domain_identity.domain_identity.domain
}
resource "aws_route53_record" "amazonses_dkim_record" {
count = 3
zone_id = var.zone_id
name = "${aws_ses_domain_dkim.dkim_identity.dkim_tokens[count.index]}._domainkey.${aws_ses_domain_identity.domain_identity.domain}"
type = "CNAME"
ttl = "300"
records = ["${aws_ses_domain_dkim.dkim_identity.dkim_tokens[count.index]}.dkim.amazonses.com"]
}
resource "aws_ses_domain_identity_verification" "domain_identity_verification" {
domain = aws_ses_domain_identity.domain_identity.id
depends_on = [aws_route53_record.amazonses_dkim_record]
}
#variables.tf
variable "zone_id" {
type = string
description = "route-53 zone id"
default = "13456789"
}
variable "domain_name" {
type = string
default = "mahiratechnology.com"
description = "route-53 domain name"
}
#provider.tf
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "5.54.1"
}
}
}
provider "aws" {
access_key = "***********"
secret_key = "***************"
region = "us-east-1"
}
Copy the above code into your terraform configuation files and open a terminal window.
Next navigate to your ses_domain directory and run terraform init command to intialize your configuration
Now run terraform plan and the run terraform apply to deploy your configuration.
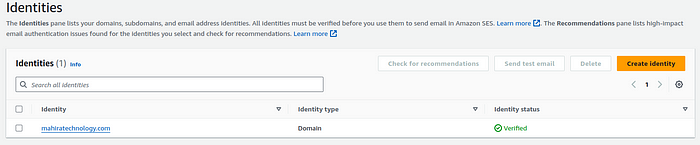
Confirm the deployment by typing “yes” in the terminal window and once the it’s done u can see the domain identity gets created in the ses.
Conclusion :-
Automating the SES domain identity verification process with Terraform not only simplifies the setup but also ensures consistency and reliability in your email delivery mechanisms. By harnessing the power of Infrastructure as Code, you empower your team to manage email infrastructure seamlessly, allowing for scalability and adaptability as your communication needs evolve. With this guide, you’ve taken a significant step toward enhancing your AWS SES configurations, contributing to a more efficient and robust email delivery system. Happy automating!
Subscribe to my newsletter
Read articles from Mahira Technology Private Limited directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Mahira Technology Private Limited
Mahira Technology Private Limited
A leading tech consulting firm specializing in innovative solutions. Experts in cloud, DevOps, automation, data analytics & more. Trusted technology partner.