𝐖𝐡𝐚𝐭 𝐚𝐫𝐞 𝐬𝐨𝐦𝐞 𝐰𝐚𝐲𝐬 𝐭𝐡𝐚𝐭 𝐲𝐨𝐮 𝐜𝐨𝐮𝐥𝐝 𝐦𝐚𝐤𝐞 𝐚𝐧 𝐄𝐂2 𝐢𝐧𝐬𝐭𝐚𝐧𝐜𝐞 𝐦𝐨𝐫𝐞 𝐬𝐞𝐜𝐮𝐫𝐞?
 Ayush Maggo
Ayush MaggoTable of contents
To enhance the security of an EC2 instance, I focus on three key areas: 𝐔𝐬𝐞𝐫 𝐀𝐜𝐜𝐞𝐬𝐬, 𝐍𝐞𝐭𝐰𝐨𝐫𝐤 𝐀𝐜𝐜𝐞𝐬𝐬, 𝐚𝐧𝐝 𝐒𝐲𝐬𝐭𝐞𝐦 𝐈𝐧𝐭𝐞𝐠𝐫𝐢𝐭𝐲.
𝐔𝐬𝐞𝐫 𝐀𝐜𝐜𝐞𝐬𝐬:
Control user access via AWS Identity and Access Management (IAM). Ensure that only authorized users can access the EC2 instance by assigning appropriate IAM roles and permissions.
𝐍𝐞𝐭𝐰𝐨𝐫𝐤 𝐀𝐜𝐜𝐞𝐬𝐬:
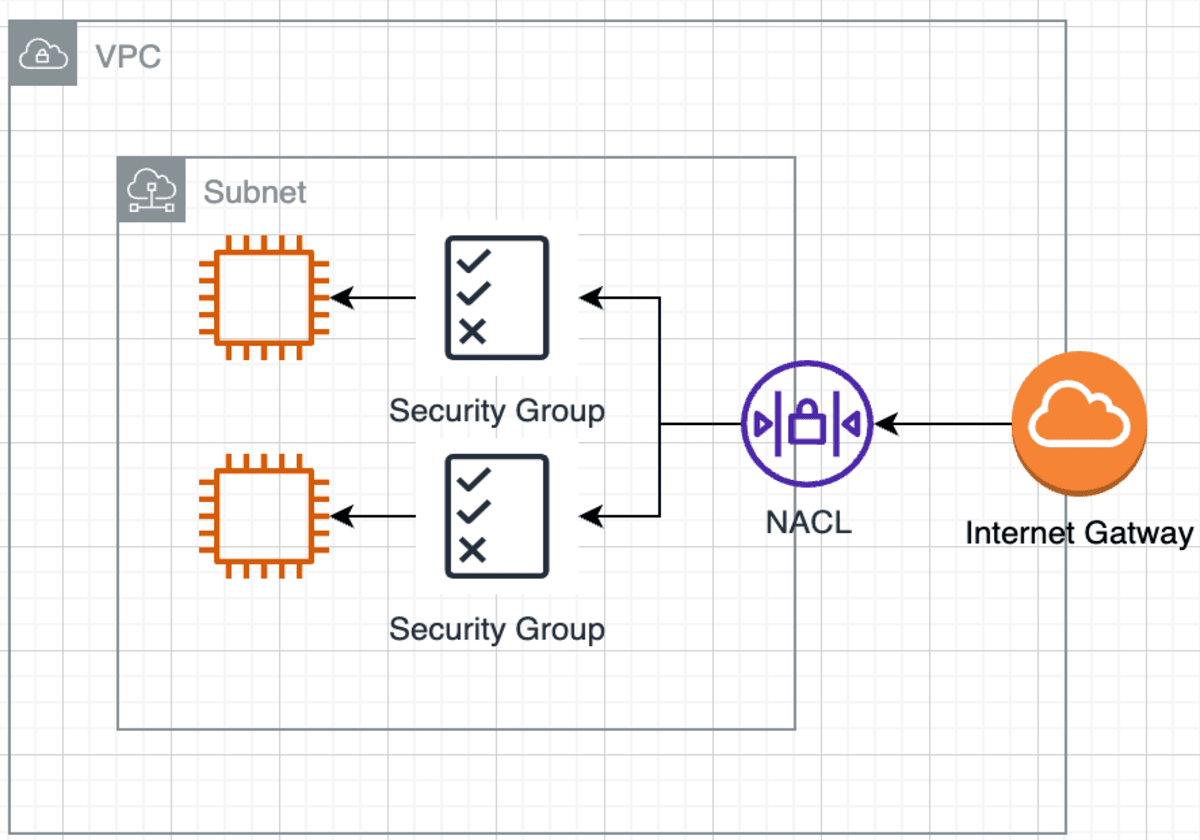
Utilize Security Groups to specify which IP addresses and ports are allowed to access your EC2 instance. Security Groups act as virtual firewalls to control inbound and outbound traffic.
Implement Network Access Control Lists (NACLs) to restrict access to specific services and ports within your instance. NACLs provide an additional layer of security at the subnet level.
Place your EC2 instance in a private subnet within a VPC to limit exposure to the internet and enhance security.
𝐒𝐲𝐬𝐭𝐞𝐦 𝐈𝐧𝐭𝐞𝐠𝐫𝐢𝐭𝐲:
Regularly check and update the operating system and installed packages. Keeping the system up-to-date helps protect against vulnerabilities and ensures the instance is secure.
By managing user access, controlling network access, and maintaining system integrity, you can significantly enhance the security of your EC2 instances.
Thank you for reading this blog, and I hope you found it informative. If you found this blog helpful, please like, share, and follow me for more blog posts like this in the future.
Subscribe to my newsletter
Read articles from Ayush Maggo directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ayush Maggo
Ayush Maggo
As a devops engineer with 3 years of experience, my work involves deploying and managing scalable cloud infrastructure on AWS, utilizing Kubernetes for container orchestration, and automating CI/CD pipelines with Jenkins, while integrating DevSecOps practices for secure and compliant infrastructure. I Implement Infrastructure as Code (IaC) with Terraform to ensure efficient, reproducible, and version-controlled infrastructure management. Leveraging Docker to ensure consistent application environments across development, testing, and production, and monitor system performance with Prometheus and Grafana. Focused on driving continuous improvement, enhancing system reliability, and delivering robust solutions that align with business objectives and drive digital transformation.