Docker Day 6: Docker Networking Essentials
 Rachana
Rachana
Docker networking allows containers to communicate with each other and with the outside world, enabling the creation of complex multi-container applications. Docker provides several networking options to facilitate communication between containers, including bridge networks, host networks, overlay networks, etc.
In this Blog, we will be diving deep into bridge network and host network in Docker, along with a practical demonstration.
Bridge Networks
Consider a scenario of microservices architecture where, different components of the application are deployed on different containers as independent services. In such scenarios, Docker must provide isolation between services while allowing them to communicate with each other.
Bridge Networks are used in such scenarios.
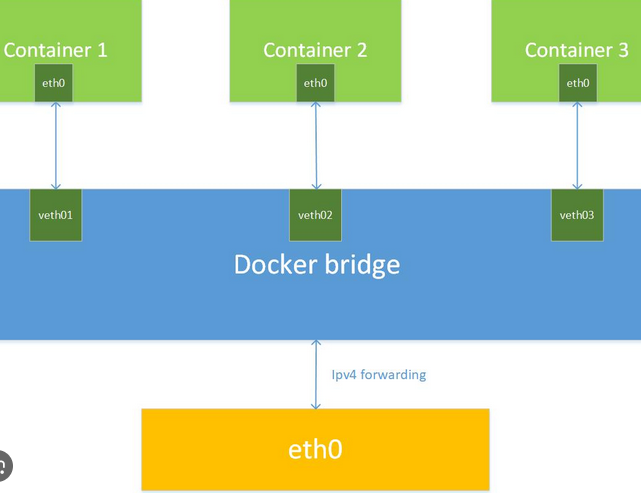
It is the default mode of networking in Docker containers. Every container created are of the type 'bridge network' by default.
Each container in a bridge network gets its own IP address.
Containers within the same bridge network can communicate with each other directly by their container name.
Docker automatically creates a bridge network named
bridgewhen Docker Engine is installed.
Host Networks
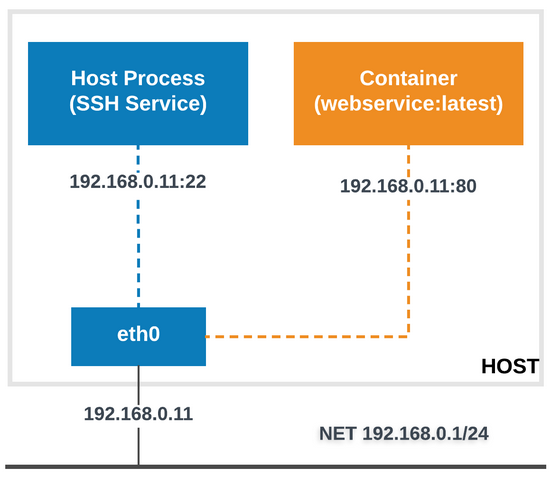
In some cases, you may have applications that require maximum network performance without any network overhead introduced by Docker. Host networks allow containers to bypass Docker's network isolation and use the host network directly, providing the best possible network performance.
By running the container in host network mode, the application can directly access the host's network interfaces without any network address translation (NAT) or bridge routing overhead.
Containers share the network namespace with the host system.
Each container has the same network interface as the host, and their network communication is not isolated.
Offers higher network performance compared to bridge networks because there is no overhead for network address translation (NAT) or bridge routing.
Custom Bridge Networks
In scenarios where there is a requirement for the containers to be isolated from each other, Host networks cannot be used. For example, if one container hosted the login page and other hosted the payments page, these containers must be isolated to ensure that the payments page is highly secure. If both these containers were of the type host network, it would provide a common path to both the containers from the host, compromising its security.
In these situations it is advised to create a Custom Bridge Network and separate the paths to access the containers from the host.
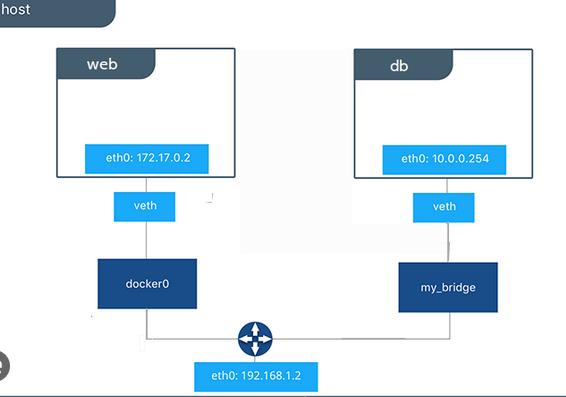
Here, a custom bridge network named my_bridge is created to isolate and secure the DB container.
Practical Demonstration
Bridge Network
Create a container named
login, using the nginx imagedocker run -d --name login nginx:latestCreate another container named
logoutdocker run -d --name logout nginx:latestSince these containers are directly created without specifying any network type, it will be of the type
bridge networkas it is the default network in Docker.Verify this by
docker inspect login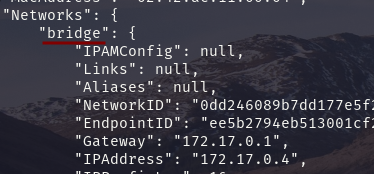
docker inspect logout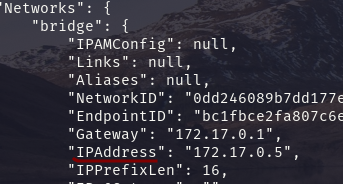
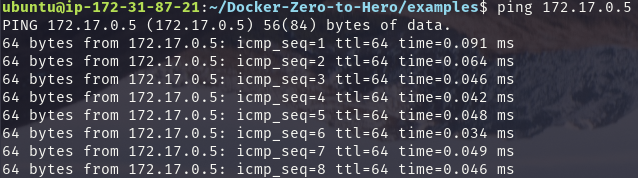
Try pinging its IP from the host(Docker Daemon) and it will work
Host Network
Create a container named
host-demoof the type Host networkdocker run -d --name host-demo --network=host nginx:latestdocker inspect host-demo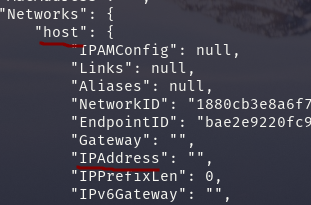
Docker does not create a separate network namespace for the container. Instead, the container shares the network namespace of the host system. As a result, the container does not have its own isolated network stack(IP), and it uses the network interfaces of the host directly.
Custom Bridge Network
First, create a network named
secure-networkdocker network create secure-networkThis network by default will be of the type bridge, check by
docker network lsCreate a container using this
secure-networkdocker run -d --name finance --network=secure-network nginx:latestCheck the network type of the finance container
docker inspect finance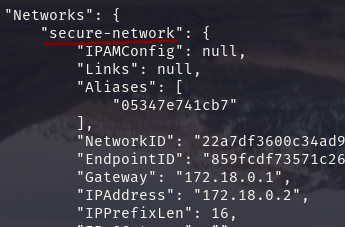
Try pinging the IP of the finance container
docker exec -it login /bin/bash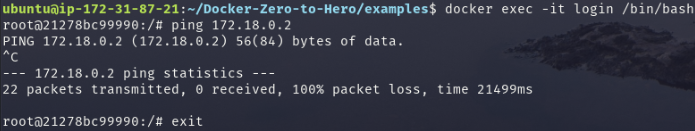
It can be observed that the container created from a custom bridge network is highly secure as we cannot ping it, unlike containers using bridge network.
Summary
In conclusion, Docker networking is a fundamental aspect of containerized applications, enabling seamless communication between containers and the outside world. By understanding and utilizing different networking options such as bridge networks, host networks, and custom bridge networks, developers can optimize their applications for performance, security, and scalability. Whether you need isolated environments for sensitive components or high-performance networking for demanding applications, Docker provides the flexibility to meet your needs. Through practical demonstrations, we have seen how to implement and verify these networking configurations, empowering you to build robust and efficient containerized solutions.
Good Day To y'all :)
Subscribe to my newsletter
Read articles from Rachana directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Rachana
Rachana
Hi to the fellow tech enthusiasts out there! 👋 I am an aspiring Cloud and DevOps Engineer ☁️ With strong foundation in containerization technologies like Docker and Kubernetes🐳 Capable of building resilient, secure and cost optimized infrastructure on AWS cloud - AWS SAA certified.☁️🔒 Currently learning to build CI/CD pipelines using Jenkins, github-actions, AWS CodePipeline, and many more.🛠️🔄 Exploring other tools like Ansible for configuration management and Terraform for Infrastructure as Code(IaC).🧩📜 Let's connect, learn and grow together! 🌟🤝