Mr. Phisher - TryHackMe Walkthrough
 Vedant Kahalekar
Vedant Kahalekar
Task
I got this sketchy email with a weird-looking attachment. It's like, "Hey, enable macros!" 😬 What even are macros?
The Lowdown on Macros
Alright, here’s a quick rundown. A macro is like a shortcut that turns a single key press into a whole sequence of actions. For our TryHackMe adventure, we're talking about Office Macros – tiny programs that automate repetitive tasks, written in Visual Basic. 🖥️
Now, here’s the kicker: these macros can be a security nightmare. Hackers can use them to trick folks into running malicious code. This is where phishing comes in. Phishing is when bad actors send emails or messages that look legit but are actually traps. It’s a classic Social Engineering move – targeting human behavior rather than technology. 🎣
For more details, Microsoft’s learning platform has got your back: Macro malware and Phishing.
Bonus Brainiac Stuff 🧠
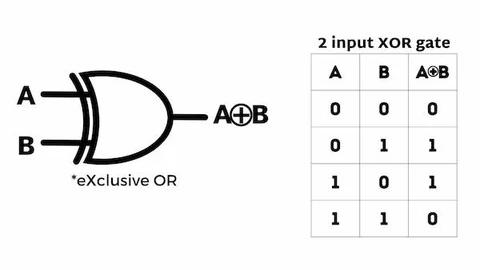
Ever heard of XOR? It's a binary operation that stands for exclusive or – a logic gate that outputs true only when exactly one of its inputs is true. So, it’s like a bouncer at a club: one guest is fine, but two? No entry! 🚫
Solution
First, we need to find the code of the macro and then analyze it. Here’s how you can do it:
Find the Macro
Start your machine and use Split Screen mode.
Navigate to the
/home/ubuntu/mrphisherfolder.Open the
MrPhisher.docmfile with Libre Office Writer.
Now let's analyze the file and see what macros are included:
Go to
Tools -> Macros -> Edit Macros.Search for macros in the folders:
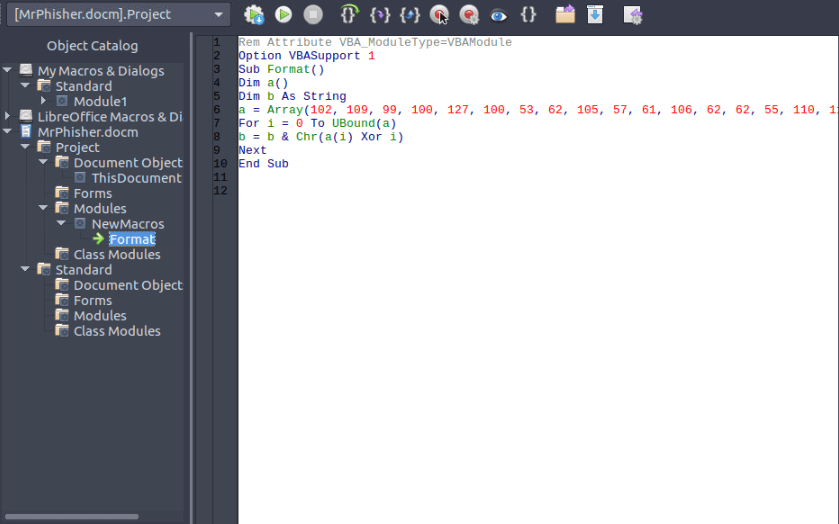
Under MrPhisher.docm -> Project -> Modules -> New Macros, we find a macro.
Analyze the Macro
The macro has the following code:
Rem Attribute VBA_ModuleType=VBAModule
Option VBASupport 1
Sub Format()
Dim a()
Dim b As String
a = Array(102, 109, 99, 100, 127, 100, 53, 62, 105, 57, 61, 106, 62, 62, 55, 110, 113, 114, 118, 39, 36, 118, 47, 35, 32, 125, 34, 46, 46, 124, 43, 124, 25, 71, 26, 71, 21, 88)
For i = 0 To UBound(a)
b = b & Chr(a(i) Xor i)
Next
End Sub
I've never worked with Visual Basic, but I can still make sense of the code using my knowledge of other programming languages. Here’s the gist:
We have an array
awith decimal values.There's a for-loop that iterates over the array. Each decimal value from the array is XORed with the iterator and appended to a string.
This looks like an encoding of a string, which might be the flag. So, I wrote a Python program to perform the exact steps and see the decoded text. This could also be done manually, but it would require an extra step of transforming to binary to perform the XOR operation.
Here’s my Python code:
b = ""
a = [102, 109, 99, 100, 127, 100, 53, 62, 105, 57, 61, 106, 62, 62, 55, 110, 113, 114, 118, 39, 36, 118, 47, 35, 32, 125, 34, 46, 46, 124, 43, 124, 25, 71, 26, 71, 21, 88]
for i in range(len(a)):
b += chr(a[i] ^ i)
print(b)
Running it will output a string that is indeed the flag: flag{REDACTED}
Thanks for sticking with us through this dive into macro mysteries and decoding adventures! 🕵️♂️ If you found this post helpful or intriguing, don't keep it to yourself – share it with your friends who are passionate about cybersecurity.
And hey, why not hit that subscribe button? By subscribing, you'll stay updated with the latest tips, tricks, and deep dives into the fascinating world of cybersecurity. Your support means a lot to us, and it helps us keep bringing you valuable content. Stay safe out there, and happy hunting! 🛡️🔐
Feel free to share your thoughts in the comments below, and let’s keep the conversation going. Until next time, stay curious and stay secure! 💻🌐
Don't forget to subscribe and share! Your fellow cybersecurity enthusiasts will thank you. 😀
Subscribe to my newsletter
Read articles from Vedant Kahalekar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Vedant Kahalekar
Vedant Kahalekar
Hi, my name is Vedant Kahalekar, and I am a Cyber geek, Computer Science student, content creator, and freelance photographer. I have a deep passion for technology, coding, and cybersecurity, and I spend most of my time learning about the latest trends and developments in the tech industry.