Part 4: The digital signature and non-repudiation.
 Sai Keerthan Kasula
Sai Keerthan Kasula
Previously, we discussed some cryptography operations, including encryption, decryption, and the concept of public key infrastructure.
Now, let's explore the process of generating a digital signature and how it is used for non-repudiation.
Have you ever wondered how digitally transmitted data is validated? What could be the process behind it? How does the receiver confirm that the data received is valid and untampered?
Let's get familiar with some terms before diving into the main process:
Digital Signature: A digital signature is an electronic, encrypted stamp of authentication on digital information such as email messages, macros, or electronic documents. It confirms that the information originated from the signer and has not been altered.
Hashing: Hashing is the practice of using an algorithm to map data of any size to a fixed length. This result is called a hash value, hash code, hash sum, or hash digest.
Non-repudiation: Nonrepudiation provides an assurance that the sender of data is provided with proof of delivery and the recipient is provided with proof of the sender's identity, To repudiate means to deny, so neither can later deny having processed the data.
The process of signing the data:
- Let us assume that the data / message below is to be signed, the communication involves a sender - Raj and the receiver - reetu.
Hi, My name is Raj. This is a test message from raj@hashnode.com
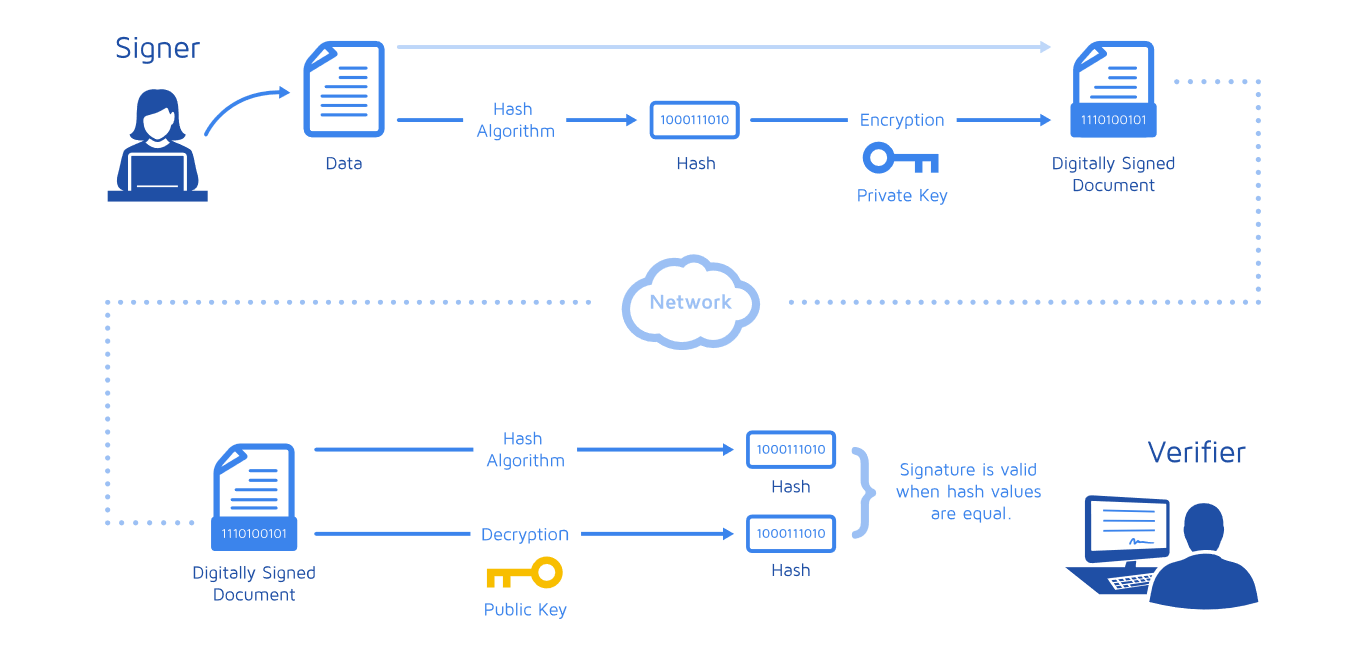
Initially, Raj Generates a hash value on the data: To generate a hash value on the above data, he is using SHA-256 algorithm using this tool.
The generated hash value is : 8239f28a9a70923387e7a002973a919e347dcf721702358d5b99d70fe36ff9ae
Note: This hash value is always 256 bits long. Hashing is a one-way process, meaning the hash value remains the same regardless of the file size or the computer used to compute it. Hashing ensures a unique value is assigned. You can test this by inputting the same data into the tool; it will always generate the same value.
Next, Raj encrypts the hash value using his private key. Encrypting this unique hash value ensures data integrity at the receiver's end. The encrypted hash is known as the "digital signature," signed by Raj, the sender.
The resultant encrypted hash is known as the "digital signature", signed by raj who is the sender.
Raj then sends the original data, the digital signature, and his public certificate to Reetu.
Process of verifying the data and the digital signature:
Using the mentioned hash algorithm from the received data, Reetu generates a hash value (let's call it H1) from the received data using the same hash algorithm.
Reetu uses Raj's public certificate to decrypt the digital signature (the encrypted hash value). This decrypted hash value is denoted as H2.
Reetu compares H1 and H2. If they match, Reetu can trust that the data she received is original and untampered.
This is the pictorial representation of the signing and verification processes:
Non repudiation:
Non-repudiation plays a crucial role in the signature and verification process, ensuring that the sender cannot deny having sent the data and the integrity of the data is maintained. Here's how non-repudiation is important:
Proof of Origin: The digital signature, created using the sender's private key, serves as proof that the data indeed came from the sender. Since only the sender has access to their private key, the signature verifies the sender's identity.
Integrity Check: The hashing process ensures that even the slightest change in the data will result in a completely different hash value. By comparing the hash value generated from the received data with the decrypted hash value from the digital signature, the receiver can verify that the data has not been altered during transmission.
Accountability: Non-repudiation holds the sender accountable for the data sent. Since the digital signature can be traced back to the sender, they cannot later deny having sent the data. This is particularly important in legal and commercial transactions.
Trust: It builds trust between the communicating parties. The receiver can be confident that the data is authentic and has not been tampered with, and the sender can be assured that their signature cannot be forged.
Legal Validity: In many jurisdictions, digital signatures are legally binding. Non-repudiation ensures that the sender cannot dispute the authenticity of their signature, providing legal protection to both parties in a transaction.
This way, the data transmitted from one node to another in the network will be verified through the above processes, ensuring data integrity, non-repudiation, and protection against data tampering.
In my next cryptography series article, let us explore how these processes are implemented using java and some dependent libraries.
Until then, consider following for such articles.
Happy Reading.
Sai Keerthan Kasula, Jr. Developer.
Subscribe to my newsletter
Read articles from Sai Keerthan Kasula directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Sai Keerthan Kasula
Sai Keerthan Kasula
Embracing this journey, eager to confront new challenges daily and strive towards becoming the best version of myself.