Mastering Cybersecurity: Day 7 of the 100-Day Challenge
 Mallika Gautam
Mallika Gautam
Phases of an incident response playbook
An incident response is an organization's quick attempt to identify an attack, contain the damage, and correct the effects of a security breach. An incident response playbook is a guide with six phases used to help mitigate and manage security incidents from beginning to end.
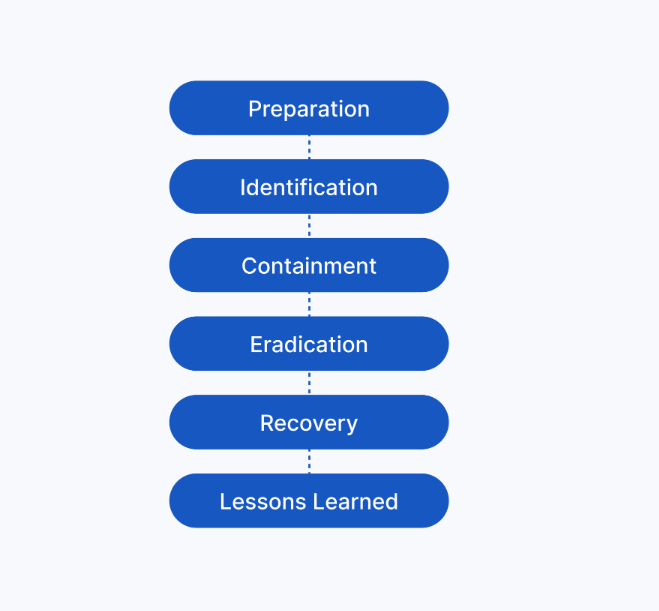
The first phase is preparation. Organizations must prepare to mitigate the likelihood, risk, and impact of a security incident by documenting procedures, establishing staffing plans, and educating users. Preparation sets the foundation for successful incident response. For example, organizations can create incident response plans and procedures that outline the roles and responsibilities of each security team member.
The second phase is detection and analysis. The objective of this phase is to detect and analyze events using defined processes and technology. Using appropriate tools and strategies during this phase helps security analysts determine whether a breach has occurred and analyze its possible magnitude.
The third phase is containment. The goal of containment is to prevent further damage and reduce the immediate impact of a security incident. During this phase, security professionals take actions to contain an incident and minimize damage. Containment is a high priority for organizations because it helps prevent ongoing risks to critical assets and data.
The fourth phase in an incident response playbook is eradication and recovery. This phase involves the complete removal of an incident's artifacts so that an organization can return to normal operations. During this phase, security professionals eliminate artifacts of the incident by removing malicious code and mitigating vulnerabilities. Once they've exercised due diligence, they can begin to restore the affected environment to a secure state. This is also known as IT restoration.
The fifth phase is post-incident activity. This phase includes documenting the incident, informing organizational leadership, and applying lessons learned to ensure that an organization is better prepared to handle future incidents. Depending on the severity of the incident, organizations can conduct a full-scale incident analysis to determine the root cause of the incident and implement various updates or improvements to enhance its overall security posture.
The sixth and final phase in an incident response playbook is coordination. Coordination involves reporting incidents and sharing information, throughout the incident response process, based on the organization's established standards. Coordination is important for many reasons. It ensures that organizations meet compliance requirements and it allows for coordinated response and resolution.
Conclusion
In conclusion, an effective incident response playbook is crucial for managing and mitigating security incidents. By following the six phases—preparation, detection and analysis, containment, eradication and recovery, post-incident activity, and coordination—organizations can systematically address breaches, minimize damage, and restore normal operations. This structured approach not only enhances immediate incident handling but also strengthens overall security posture, ensuring robust protection for critical assets and data.
Subscribe to my newsletter
Read articles from Mallika Gautam directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Mallika Gautam
Mallika Gautam
designer & cyber security student :)