Beyond Basics: Leveraging JSON Schema for API Security Testing
 Esther Okafor
Esther Okafor
Security testing is critical, yet many resources overlook the specifics of API testing. This gap poses challenges for QA engineers tasked with securing these crucial interfaces. This article delves into how JSON Schema can help QA professionals test APIs for security vulnerabilities.
Imagine a shield that can block unexpected attacks on your API. That's exactly what JSON Schema can be! It's a powerful tool that helps you define exactly what kind of data your API expects and how it should be formatted. This is crucial because unexpected data structures or values can be exploited by attackers to gain unauthorized access or manipulate your API's behaviour.
Here's how JSON Schema acts as your security champion:
Clear the Rules of Engagement: JSON Schema defines a contract for your API data. It specifies things like allowed data types (numbers, text, etc.), and acceptable formats (like date formats) and even sets limitations on the data (like minimum or maximum lengths). This clarity helps identify potential vulnerabilities where attackers might try to sneak in unexpected information.
Stop Hackers at the Gate: By enforcing data validation, JSON Schema acts like a security guard at the entrance of your API. It checks incoming data against the defined rules and rejects anything that doesn't match. This prevents malicious data from entering your API and causing harm.
Now that you've seen how JSON Schema acts as a shield, let us take a look at how it can help you become proactive in your API security testing:
Thinking Like a Hacker (But for Good):
Beyond the Obvious: Regular negative testing involves sending invalid data like empty fields or wrong values. JSON Schema allows us to go a step further. We can design test cases that explore truly unexpected data structures or values that wouldn't occur in normal use. This helps us identify vulnerabilities that attackers might exploit with unusual data formats.
Scenario: An API endpoint expects a JSON object with two fields:
"name"(string) and"age"(integer).{ "name":"jane", "age": 20 }Regular Negative Testing:
Sending an empty object
{}(might not reveal vulnerabilities related to unexpected data structures).Sending an object with missing fields (
{"name": "John"}): This might be caught by standard validation but doesn't explore unexpected structures.
JSON Schema Enhanced Negative Testing:
Unexpected Data Type: Send an object with "age" as a string instead of an integer (
{"name": "John", "age": "twenty-five"}). This could potentially exploit a vulnerability where the API doesn't handle non-numeric values for "age" correctly.Nested Data Structure: If the schema doesn't explicitly disallow nested structures, send an object with a nested object within the expected fields (
{"name": "John", "age": 30, "address": {"street": "123 Main St"}}). This explores whether the API can handle unexpected nested data that might bypass validation for the top-level fields.Additional Fields: Send an object with additional fields not defined in the schema (
{"name": "John", "age": 30, "secret_key": "abc123"}). This could potentially expose vulnerabilities where the API processes unexpected fields or leaks sensitive information through them.
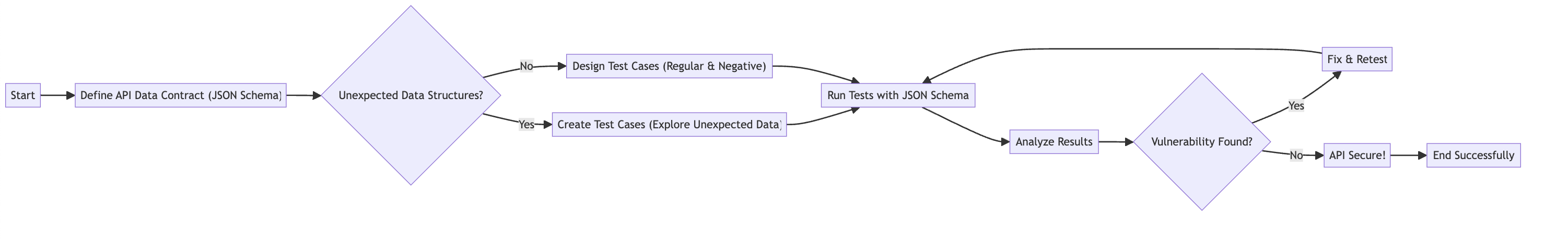
We've seen how JSON Schema acts as a shield and helps design smarter negative tests. Now, let's explore some advanced techniques that take your API security testing to the next level
Custom Validation Rules: Building a Security Fortress
JSON Schema libraries often allow you to define custom validation rules using programming languages. This lets you create even more robust security checks:
Blacklist the Bad Guys: Imagine having a list of known malicious keywords or data patterns that attackers might try to inject. JSON Schema allows you to define custom validation rules that check incoming data against this blacklist. Any data containing these red flags gets rejected, preventing potential injection attacks.
Enforce Data Format Strongholds: Some data types are particularly vulnerable to injection attacks if not formatted correctly. For example, enforcing a specific date format for a "birth_date" field can help prevent SQL injection attacks that exploit date parsing weaknesses.
These custom validation rules, combined with the core functionalities of JSON Schema, create a powerful security fortress for your API.
Automating Security Checks: Efficiency is Key
Testing frameworks like Postman or Jest can integrate with JSON Schema. This allows you to:
Write Security-Focused Test Cases: Define test cases that specifically focus on security vulnerabilities. You can use the expected JSON Schema and your custom validation rules within these test cases.
Automate the Repetitive: Imagine running the same security checks over and over again. By automating these tests with JSON Schema integration, you save time and ensure consistent security checks throughout the development process.
Case Studies: Bringing Theory to Practice
Case Study 1: Securing a Social Media Login API
A social media platform used JSON Schema to define the expected data
structure for user login requests. This schema included:
Required Fields: Username and password were marked as mandatory.
Data Type Validation: Username had a minimum length requirement to prevent brute-force attacks.
Custom Validation: The password field used a regular expression to enforce a combination of uppercase, and lowercase letters, numbers, and special characters, making it more resistant to password cracking attempts.
This approach helped identify and prevent potential vulnerabilities related to:
Missing Login Credentials: The schema ensured all required fields were present.
Brute-Force Attacks: Minimum username length requirement hindered automated login attempts.
Weak Passwords: Enforced password complexity made credential theft less impactful.
Challenges: Defining overly complex custom validation rules might introduce compatibility issues with older clients or require additional development effort.
Case Study 2: Validating Financial Transaction Data
A financial services company utilized JSON Schema to validate incoming and outgoing transaction data for their API. The schema ensured:
Data Accuracy: Fields like account numbers, amounts, and currencies adhered to specific formats and value ranges, reducing the risk of data errors and fraudulent transactions.
Missing Information: Required fields like transaction type and beneficiary details were flagged for missing data, preventing incomplete transactions.
This approach helped improve:
Data Integrity: Consistent data formats minimized errors during processing.
Fraud Detection: Schema validation acted as a first line of defence against attempts to manipulate transaction data.
Challenges: Keeping the schema up-to-date with evolving business requirements and new regulations might require ongoing maintenance.
The Future of Schema-Based API Security Testing
The future of API security testing with JSON Schema is promising:
Deeper Integration with Security Tools: Integration with security testing frameworks could enable automated vulnerability scanning based on defined JSON Schemas. This would streamline the process and provide a more comprehensive security assessment.
Evolving JSON Schema Features: Future versions of JSON Schema might introduce functionalities specifically designed for security testing, allowing for even more granular control over data validation and vulnerability detection.
Leveraging JSON Schema for API security testing is a game-changer for QA engineers, allowing you to define clear data rules and automate security checks. Say goodbye to unexpected attacks and hello to a more secure API ecosystem. 🛡️🔒
Want to learn more? Drop a comment below! 💬
Happy reading! 📖 Next article, we'll dive into a practical guide on how to write focused security tests in Postman and run them with Newman in your CI/CD pipeline. Thank you for reading! 🙏👋
Subscribe to my newsletter
Read articles from Esther Okafor directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Esther Okafor
Esther Okafor
Esther Okafor is a Quality assurance engineer passionate about delivering great user experience applications. Prioritizing quality over speed