Mastering Cybersecurity: Day 9 of the 100-Day Challenge
 Mallika Gautam
Mallika Gautam
Introduction to Network Communication
Networks help organizations communicate and connect. But communication makes network attacks more likely because it gives a malicious actor an opportunity to take advantage of vulnerable devices and unprotected networks. Communication over a network happens when data is transferred from one point to another. Pieces of data are typically referred to as data packets.
The TCP/IP Model
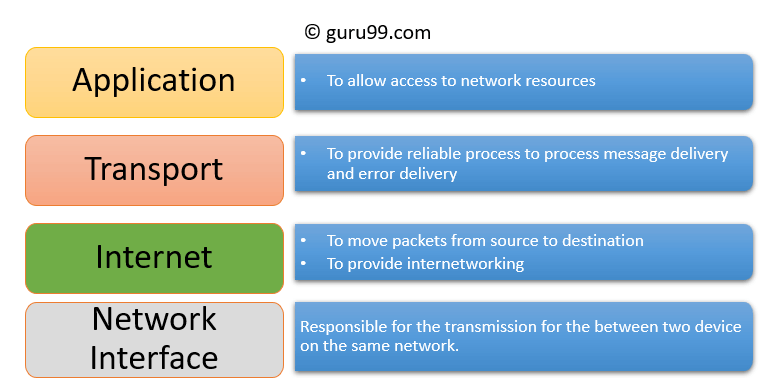
TCP/IP stands for Transmission Control Protocol and Internet Protocol. TCP/IP is the standard model used for network communication. Let's take a closer look at this model by defining TCP and IP separately. First, TCP, or Transmission Control Protocol, is an internet communication protocol that allows two devices to form a connection and stream data. The protocol includes a set of instructions to organize data, so it can be sent across a network. It also establishes a connection between two devices and makes sure that packets reach their appropriate destination. The IP in TCP/IP stands for Internet Protocol. IP has a set of standards used for routing and addressing data packets as they travel between devices on a network. Included in the Internet Protocol (IP) is the IP address that functions as an address for each private network.
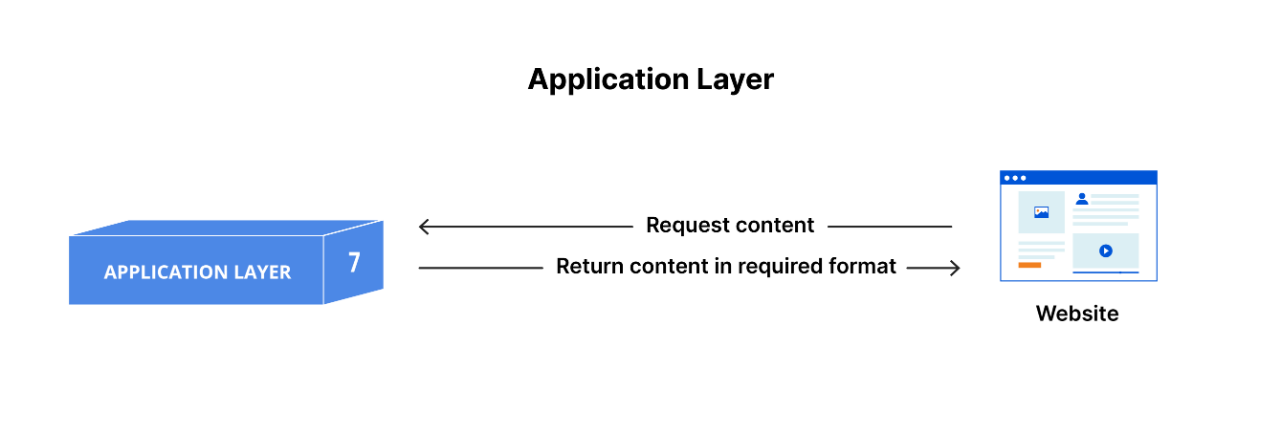
The TCP/IP model is a framework that is used to visualize how data is organized and transmitted across the network. The TCP/IP model has four layers. The four layers are: the network access layer, the internet layer, the transport layer, and the application layer. Knowing how the TCP/IP model organizes network activity allows security professionals to monitor and secure against risks.
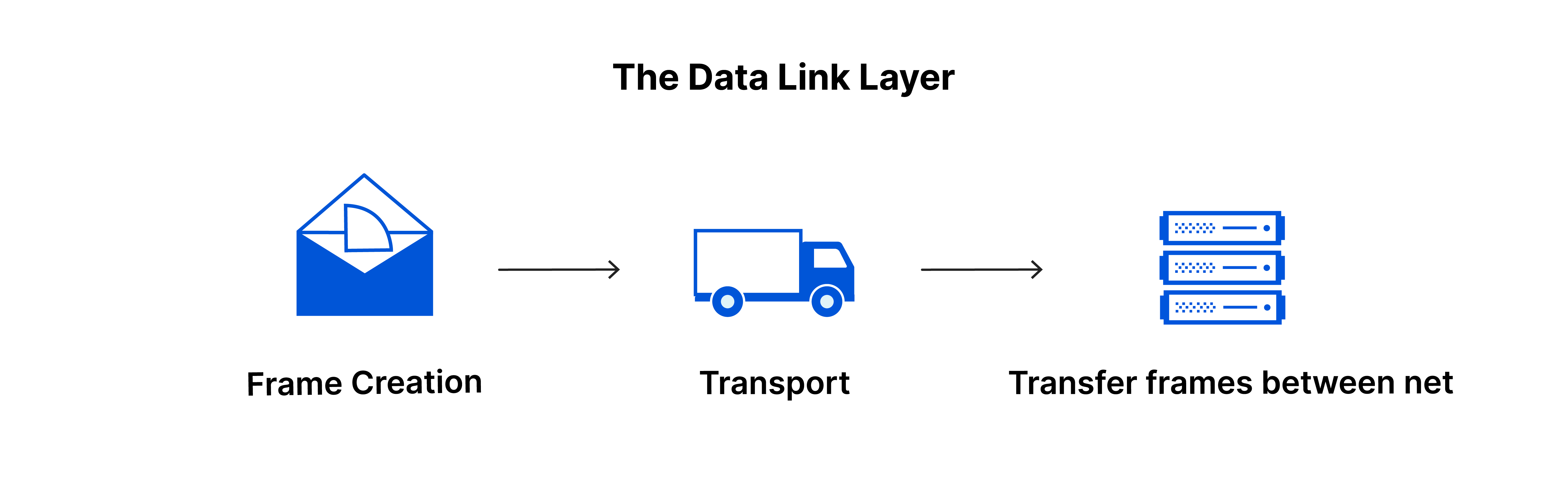
Layer one is the network access layer or Data Link Layer. The network access layer deals with creation of data packets and their transmission across a network. This includes hardware devices connected to physical cables and switches that direct data to its destination.
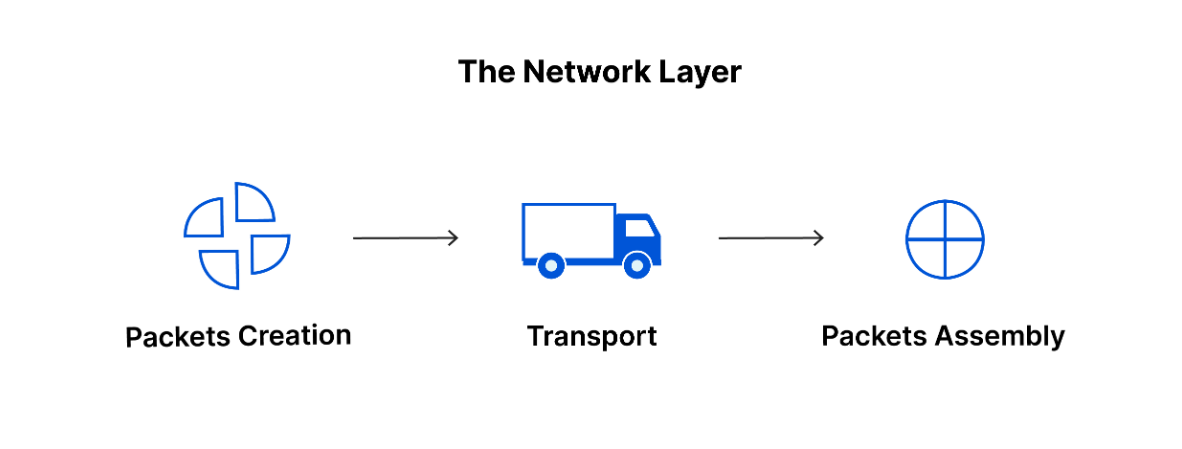
Layer two is the internet layer. The internet layer is where IP addresses are attached to data packets to indicate the location of the sender and receiver. The internet layer also focuses on how networks connect to each other. For example, data packets contain information that determines whether they will stay on the LAN or be sent to a remote network, like the internet.
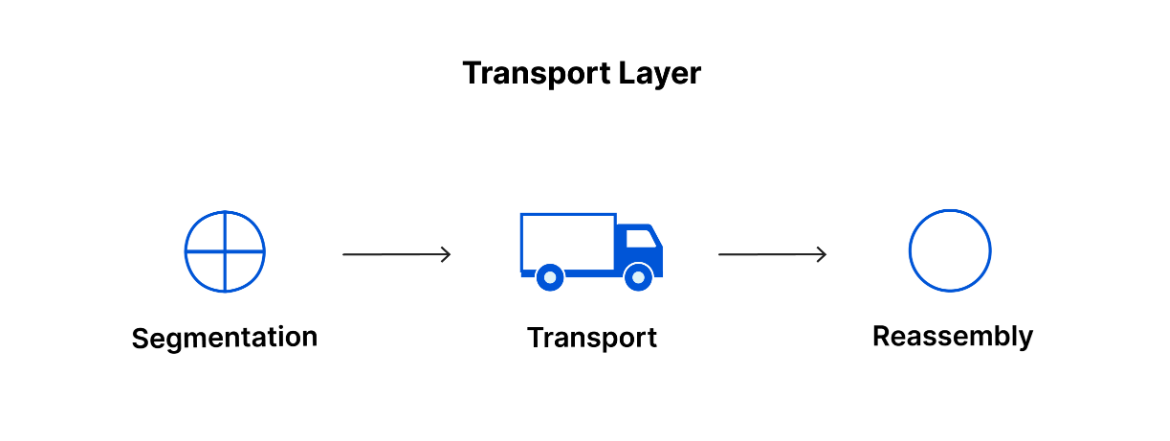
The transport layer includes protocols to control the flow of traffic across a network. These protocols permit or deny communication with other devices and include information about the status of the connection. Activities of this layer include error control, which ensures data is flowing smoothly across the network.
Finally, at the application layer, protocols determine how the data packets will interact with receiving devices. Functions that are organized at the application layer include file transfers and email services.
Conclusion
Network communication is fundamental for organizational connectivity, but it also introduces vulnerabilities that can be exploited by malicious actors. The TCP/IP model, comprising four layers—network access, internet, transport, and application—provides a framework for organizing and transmitting data securely across networks. Understanding this model is essential for security professionals to monitor and mitigate risks effectively, ensuring smooth and safe data transfer between devices.
Subscribe to my newsletter
Read articles from Mallika Gautam directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Mallika Gautam
Mallika Gautam
designer & cyber security student :)