Network Security Basics: Security Groups and Network ACLs Decoded
 Onwubiko Emmanuel
Onwubiko Emmanuel
This article will help you understand security groups and network access control lists (ACLs), as well as how they function and react to network traffic flow. By exploring the key differences between these two security mechanisms, you will gain insights into their roles in safeguarding cloud environments.
These two security features provide crucial protection from network attacks.
Here's what you'll discover:
What are Security Groups and how they work
Understanding Network ACLs (Access Control Lists)
What are Network ACLs? Network ACLs are an additional layer of security that act at the subnet level to control traffic in and out of one or more subnets within your VPC.
How do Network ACLs differ from Security Groups
But before we go deeper into this article we need to understand what a stateful and stateless firewall means.
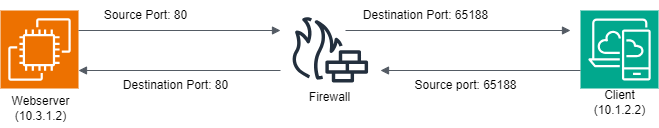
Stateful Firewall:
A stateful firewall allows the return of traffic automatically. A stateful firewall collects data regarding every connection made through it. All of these data points form profiles of “safe” connections. When a subsequent connection is attempted, it is checked against the list of attributes collected by the stateful firewall. If it has the qualities of a safe connection, it is allowed to occur. If not, the data packets are discarded. Data packets contain information about the data within them. A stateful firewall performs packet inspection, which checks the contents of packets to see if they pose threats.
Stateless Firewall:
A stateless firewall checks to see if there are any predefined rules that accompanies every traffic it analyses. Stateless firewalls make use of a data packet's source, destination, and other parameters to figure out whether the data presents a threat. These parameters have to be entered by either an administrator or the manufacturer via rules they set beforehand
Now that we understand what Stateful and Stateless firewalls are, let delve into security groups and Network ACLs.
Security groups:
Security groups serves as a key feature in cloud computing environments. They act as virtual firewalls for your instances to control inbound and outbound traffic. They are assigned at the instance level. They are also attached to the elastic network interface of the adapters connected the virtual machine instance being used (in this case EC2). Security groups can also be applied to instances in any subnet. It also serves as a stateful firewall.
Network ACLs:
The Network Access Control List (NACL) which is applied at the subnet level screens the traffic leaving and going into the subnet. They only apply to the traffic entering and exiting the subnet (Ingress and Egress traffic). It is a stateless firewall.
As a stateless firewall, NACLs do not keep track of the state of a connection. This means that each packet is evaluated independently, without any awareness of the context or state of other packets. Consequently, administrators need to create both inbound and outbound rules to control traffic flow effectively. For instance, if an inbound rule allows traffic from a particular IP address, a corresponding outbound rule must be explicitly defined to permit the return traffic.
NACLs operate based on a set of numbered rules that are evaluated in ascending order. Each rule either allows or denies traffic based on specified criteria such as protocol type, port number, and source or destination IP address.
| Security Group | Network ACLs |
| Operates at the Instance(Interface) level | Operates at the subnet level |
| Supports "allow" rules only | Supports "allow" and "delay" rules |
| Stateful firewall | Stateless firewall |
| Evaluates all rules | Processes rules in order |
| Applies to an instance only if associated with a froup | Automatically applies to all instances in the subnets it s associated with |
Conclusion
In this article, you learned about security groups and network access control lists (NACLs), including their functions and how they handle network traffic flow. We covered the differences between these two security mechanisms and provided practical examples of their use in cloud environments.
There is so much more to learn about security groups and NACLs. To deepen your understanding, check out the following resources:
Subscribe to my newsletter
Read articles from Onwubiko Emmanuel directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
Onwubiko Emmanuel
Onwubiko Emmanuel
Emmanuel is a Software Engineer || Cloud Engineer || Technical Writer || Technical Product Manager