Access Control - Horizontal Privilege Escalation
 Varkey Thomas
Varkey Thomas
An access control vulnerability when a non-administrative user can see another users personal information with similiar privileges. An example would be a user gaining access to the records of another user.
Horizontal privilege escalation attacks may use similar methods of exploit to vertical privilege escalation. It is a matter of changing the URL from the current users ID to the target users ID
The Lab:
The goal of this lab is to access another users account page via the GUID and submit the API key as the solution.
The lab starts out with the website homepage.
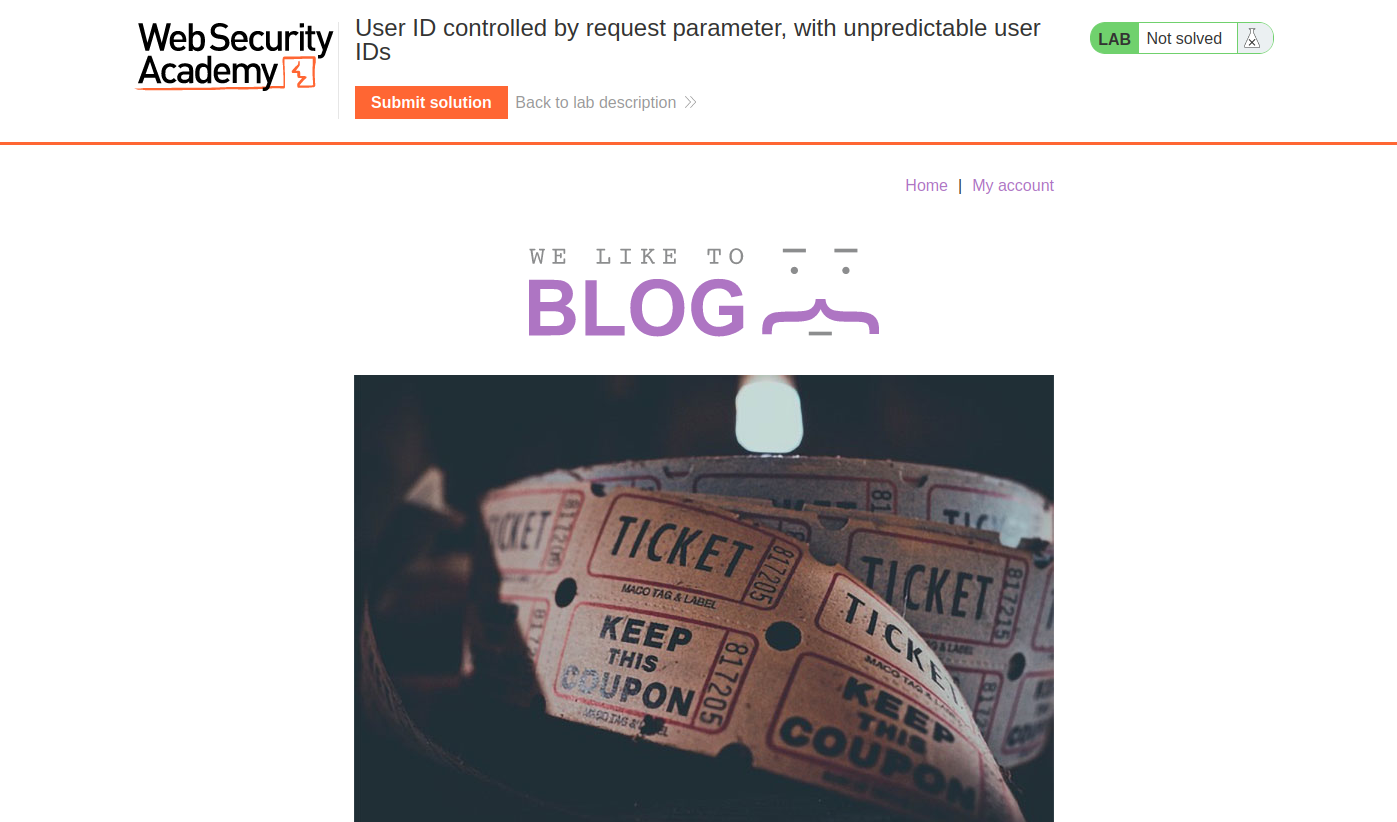
Login using current user credentials,
Using Zaproxy, the POST request details can be seen
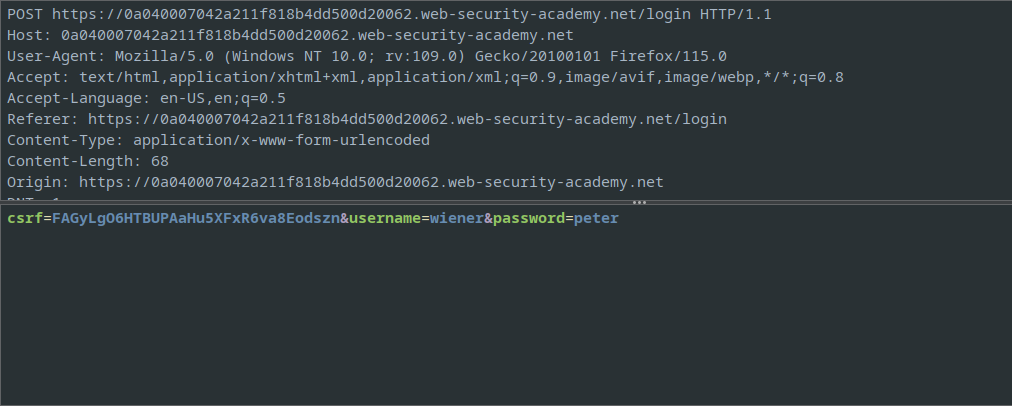
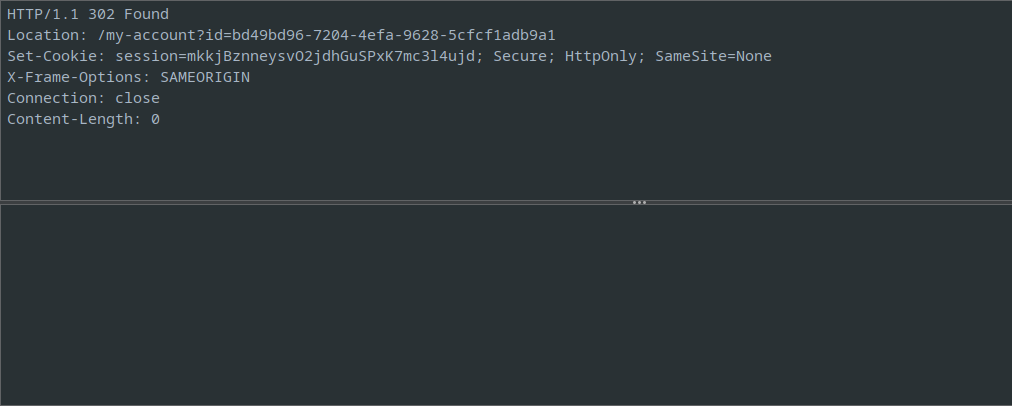
The GET request from the server shows the GUID for the current user
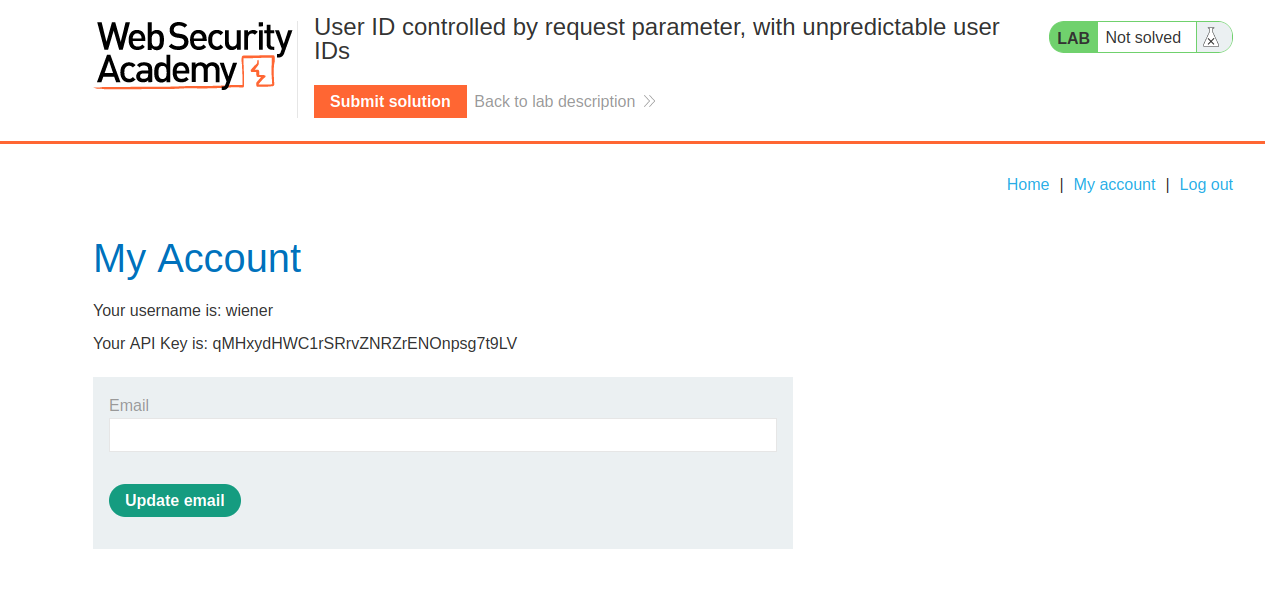
After having logged in as the current user, navigate back to the home screen. The next step is to find a post by the target user
The first post is one by the current user as displayed

After a little search, a post by the target user is found. By clicking the link, we go to the target user's page.
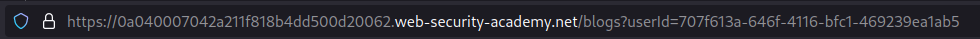
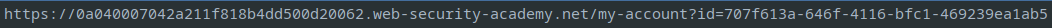
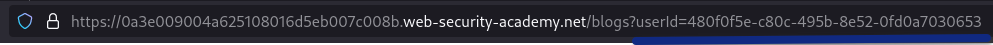
In the URL, we can see the GUID of the target user.
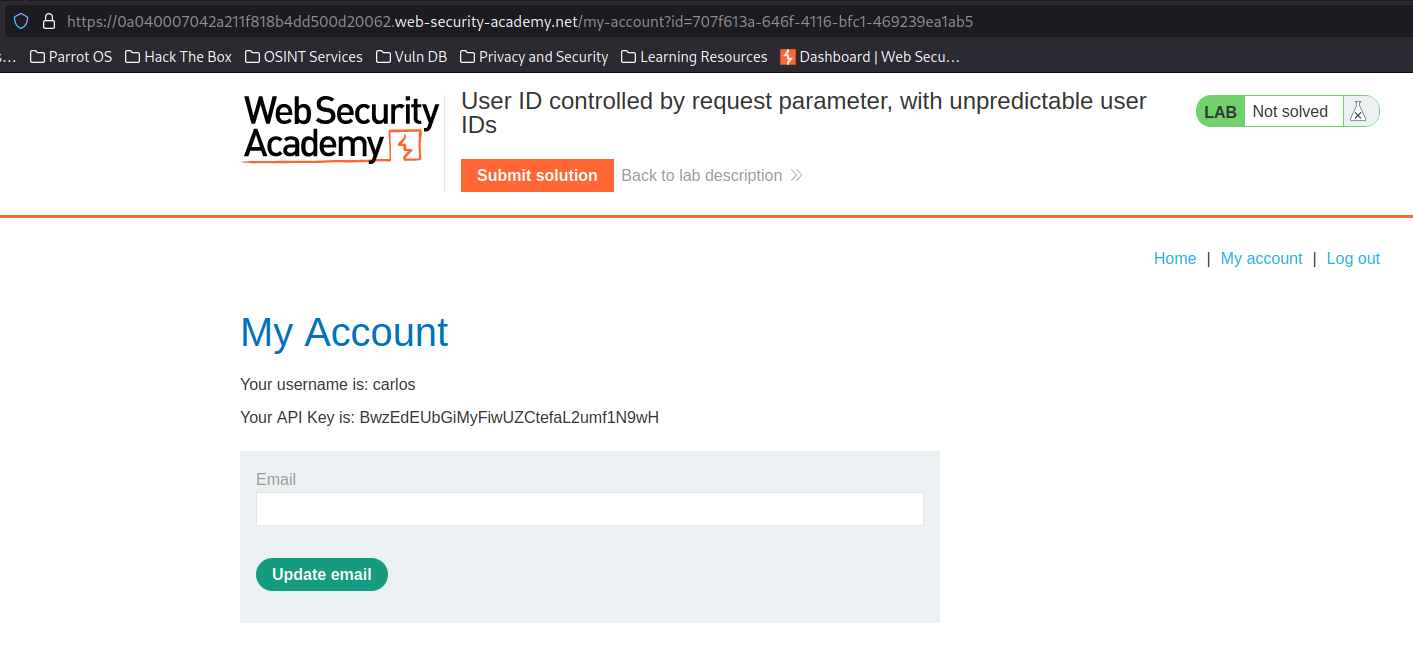
Going back to the current user profile page, after a small change to the userid in the URL,
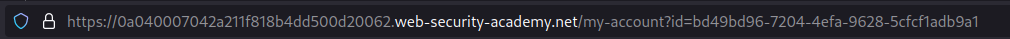
The target user profile page is accessed.
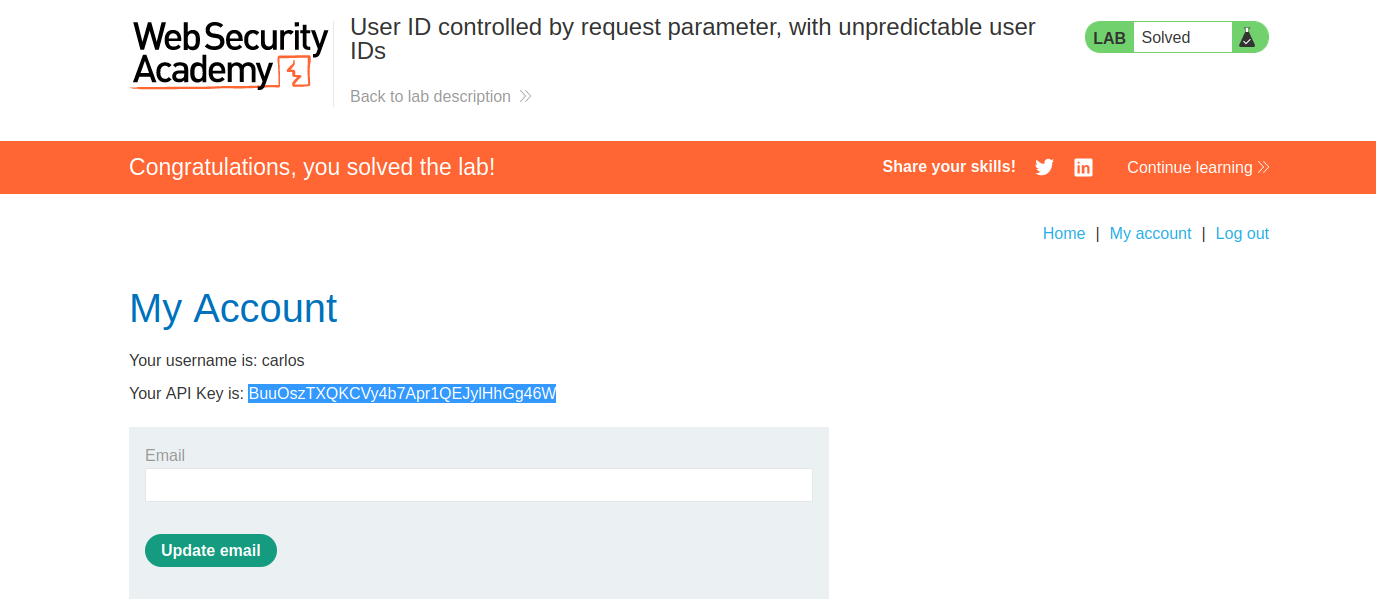
Next is a simple step of submitting the API key.
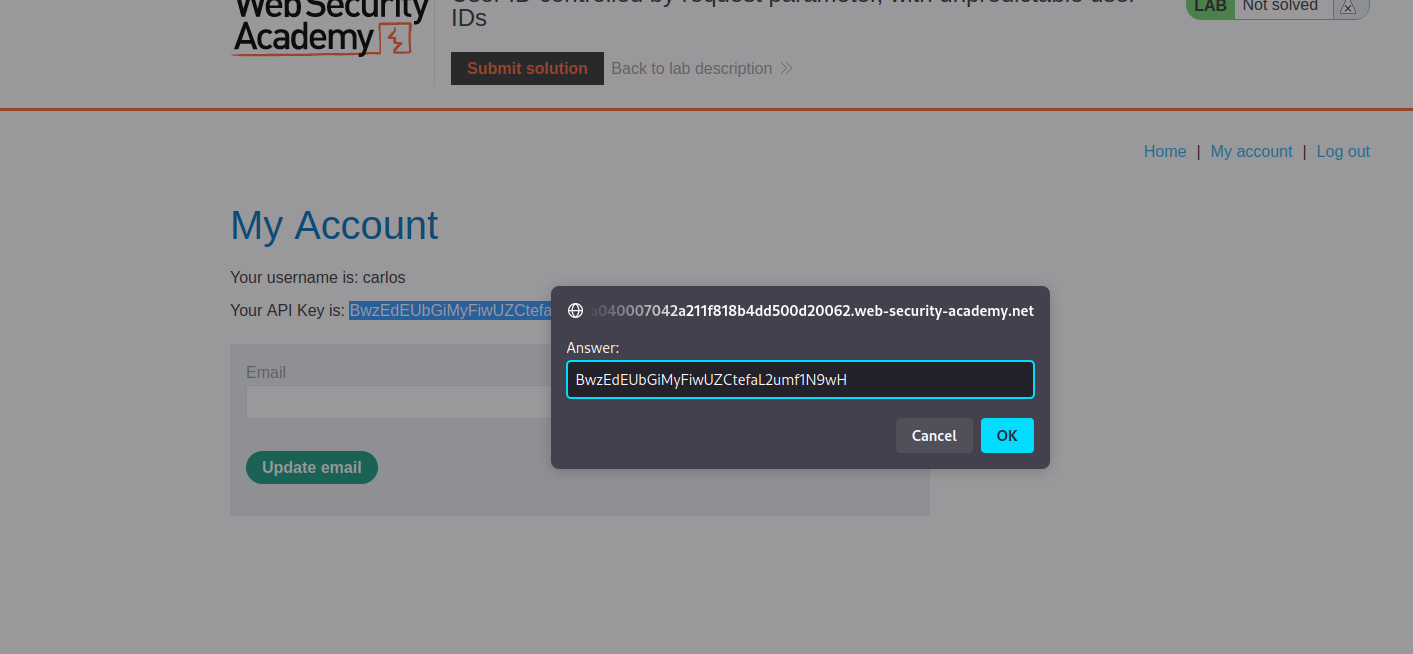
And the lab is completed
Then navigate back to the homepage start searching for articles authored by the target user
Click on the target user link displayed
Upon clicking the authors link, the guid can be viewed in the url
When logging into the account provided at the beginning of the lab, the GET and POST request can be examined using OWASP Zap
At login
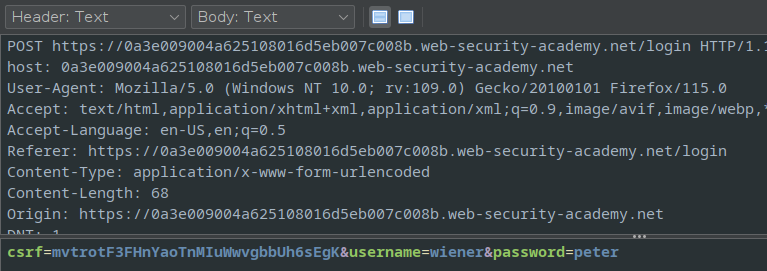
The post request
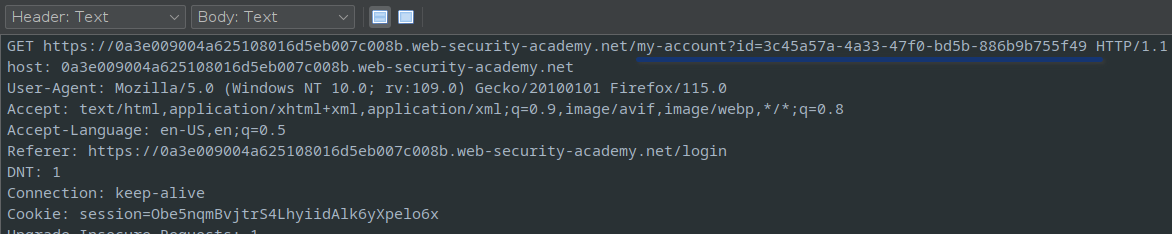
In the GET request, the GUID of the provided account is visible.
Next after a few articles, an article by the target user was found
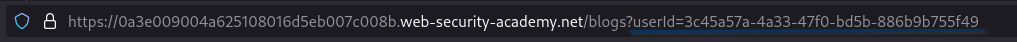
In the url, the GUID of the author can be seen. Using this GUID, it is possible to access the target account
To accomplish this, again go back to the login page and sign in with the provided credentials.
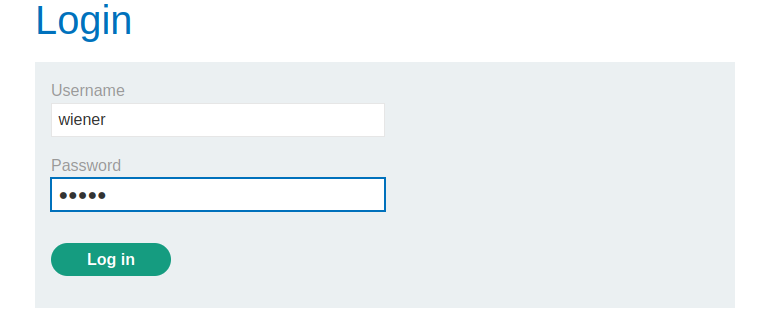
Using Zaproxy, after logging in, after the POST request
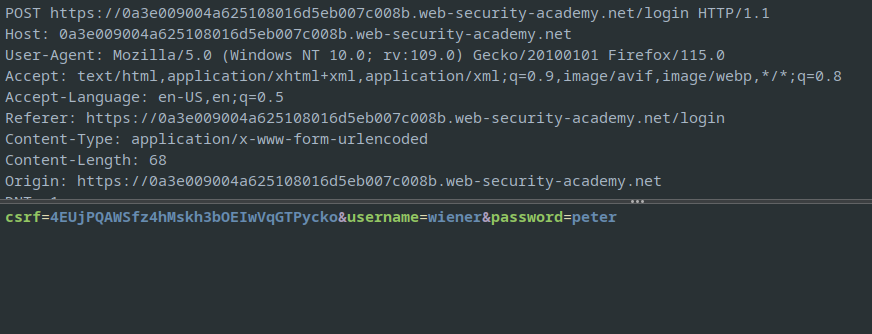
The next screen shows the GUID assigned for the user, which can be replaced with the target GUID
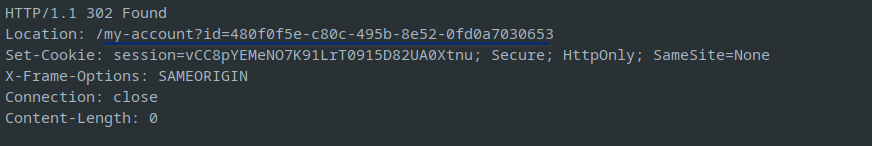
to
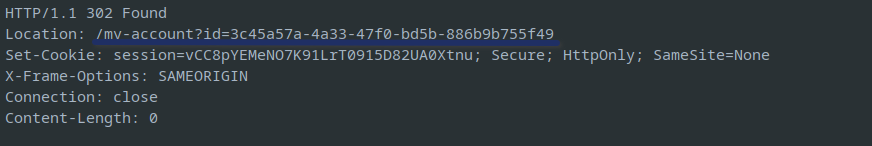
Once these steps are completed, access to the target user page will be granted Wikipedia https://en.wikipedia.org › wiki › Sweet_&Sour(film)  Sweet
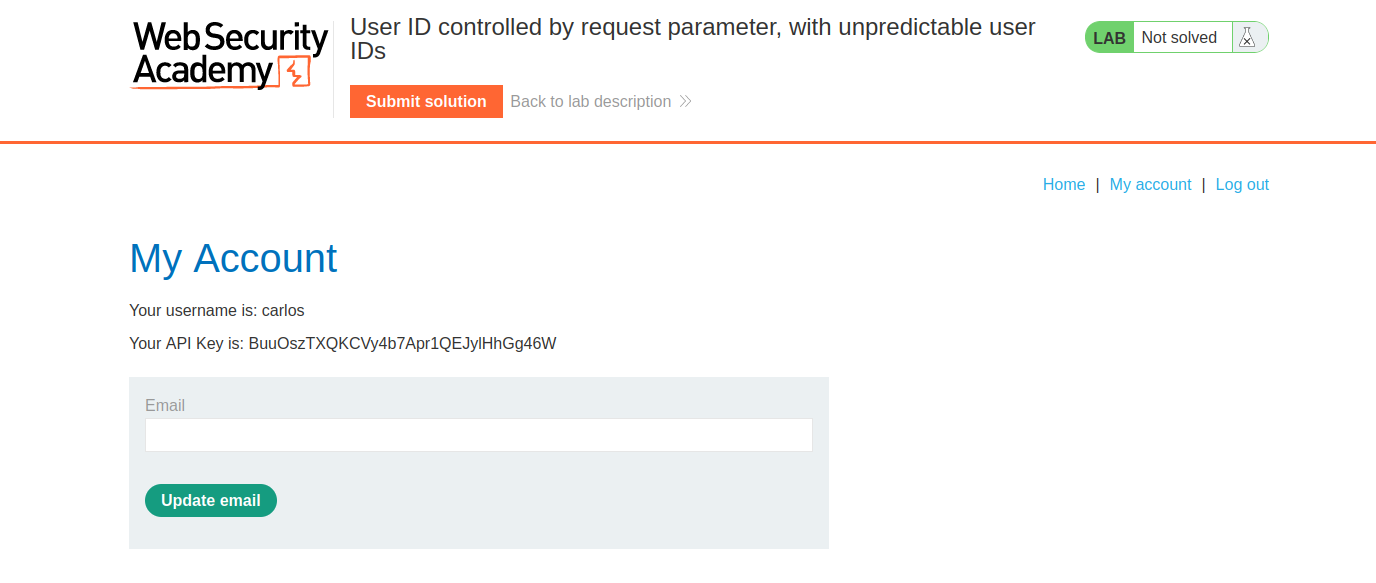
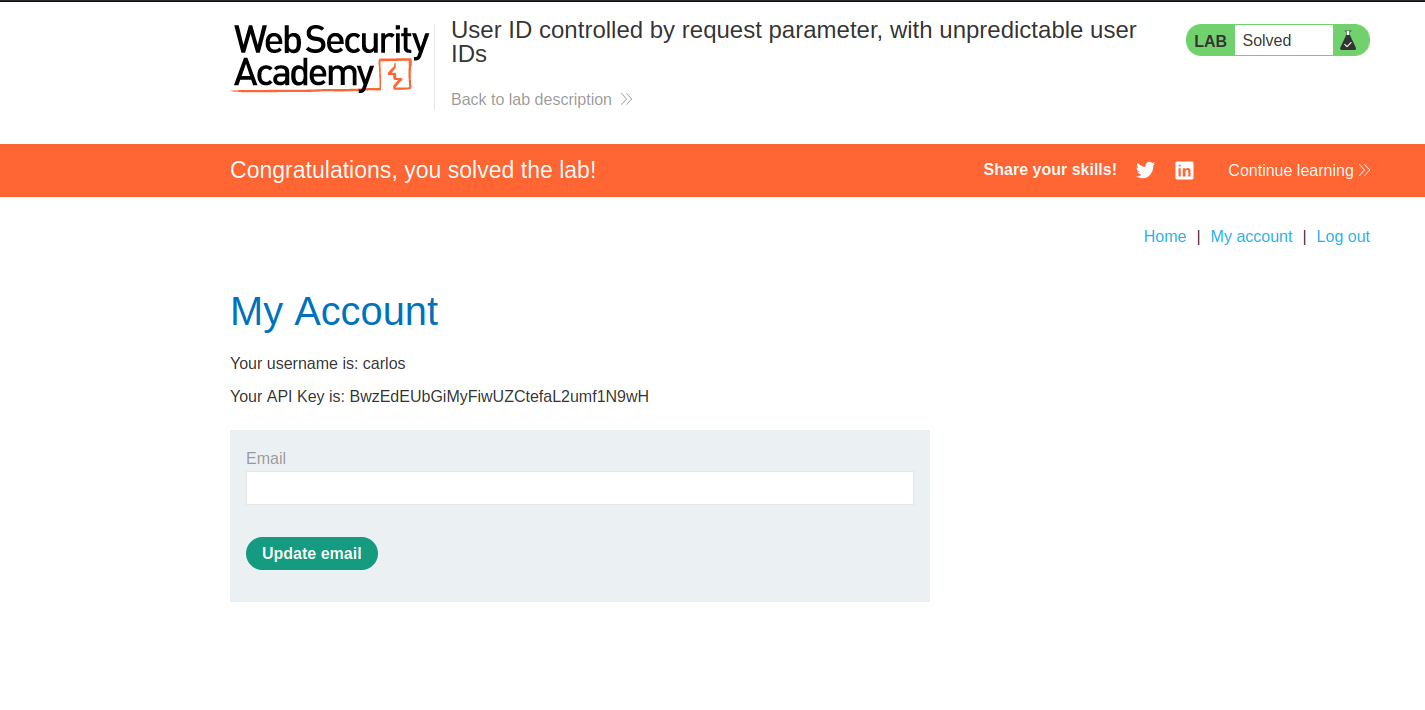
Then its a simple matter of copying the API key to the "Sumbit Solution" button
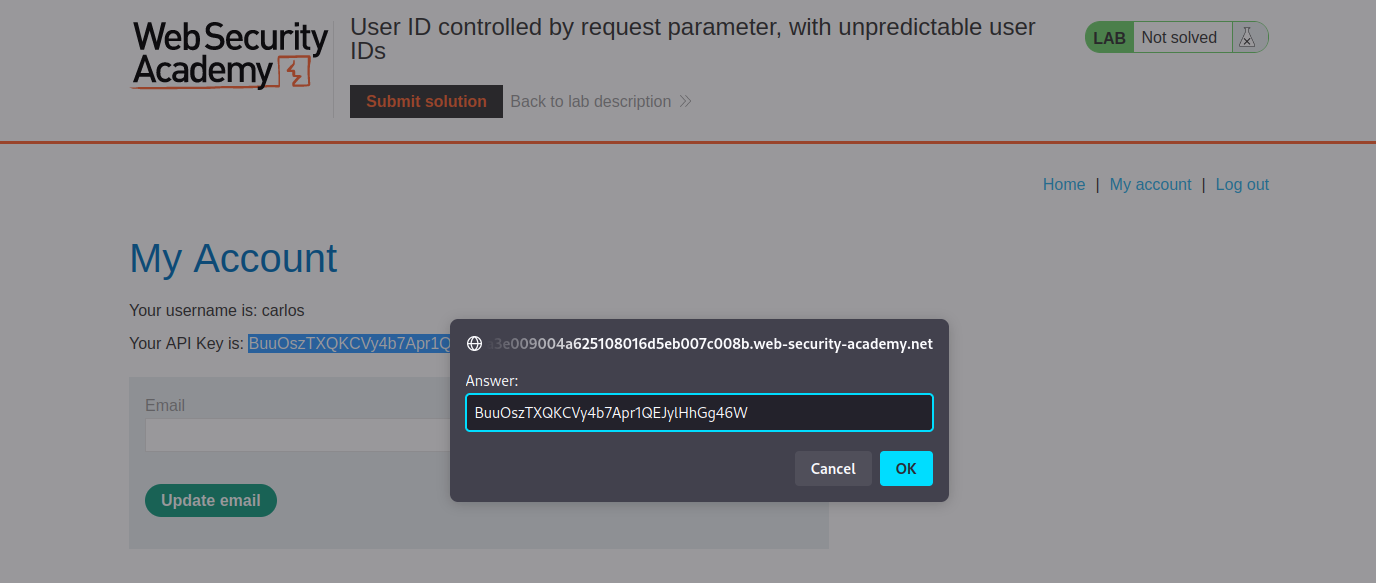
Once the key is submitted, the lab will be completed
Subscribe to my newsletter
Read articles from Varkey Thomas directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
