Day 2 - Network Services, Applications, DHCP, DNS and NAT
 Shreyas Ladhe
Shreyas Ladhe
Networking Services and Applications
Basics of Virtual Private Network
A virtual private network (VPN) is used by remote hosts to access a private network through an encrypted tunnel through a public network.
Once a VPN connection is made, the remote host is no longer considered remote. It is actually seen by the private network as a local host. Even though the network traffic may pass through many different routers or systems, it is seen by both ends as a direct connection.
The use of VPN can help reduce networking costs for organizations and businesses. The cost reduction is partially achieved because the VPN doesn’t require the use of a dedicated leased line to create the connection.
VPN types:
The site-to-site VPN allows a remote site’s network to connect to the main site’s network and be seen as a local network segment.
- VPN concentrators on both ends of a VPN will manage the connection.
The remote access VPN (host-to-site VPN) allows select remote users to connect to the local network.
A VPN concentrator on the local network will manage the connections coming from the remote users.
The remote system making the connection uses special software, called VPN client software, to make the connection.
The host-to-host VPN(SSL VPN) allows a secure connection between two systems without the use of VPN client software.
A VPN concentrator on the local network manages the connections.
The host seeking to connect uses a Web browser that supports the correct encryption technology (either SSL or TLS) to make the connection to the VPN concentrator.
Protocols used by Virtual Private Networks
Internet Protocol Security (IPsec)
Works at Layer 3 of the OSI model and above.
The most common suite of protocols to secure a VPN connection.
Can be used with the Authentication Header (AH) protocol
- AH only offers authentication services. no encryption
Can be used with Encapsulating Security Payload (ESP)
- ESP both authenticates and encrypts packets (the most popular method)
Both AH and ESP will operate in one of two modes
Can be used in transport mode between two devices (Eg. host to host VPN).
Can be used in tunnel mode—between two endpoints (Eg. site-to-site VPN).
IPSec implements Internet Security Association and Key Management (ISAKMP) by default.
- ISAKMP provides a method for transferring security key and authentication data between systems. outside of the security key generating process (a much more secure process).
Generic Routing Encapsulation (GRE)
GRE is a tunneling protocol that is capable of encapsulating a wide variety of network layer protocols.
It is often used to create a sub-tunnel within an IPsec connection.
- IPsec will only transmit unicast packets (one-to-one communication). In many cases, there is a need to transmit multicast (one-to-some communication) or broadcast (one-to-many communication) packets across an IPsec connection. By using GRE, this can be accomplished.
Point-to-Point Tunneling Protocol (PPTP)
An older VPN technology that supports dial-up VPN connections. On its own, it lacked native security features.
- Microsoft implementation included additional security by adding GRE.
Transport Layer Security (TLS) Protocol
TLS is a cryptographic protocol used to create a secure encrypted connection between two end devices or applications.
- It uses asymmetrical cryptography to authenticate end points and then negotiate a symmetrical security key, which is used to encrypt the session.
TLS has largely replaced the Secure Socket Layer protocol.
It Works at Layer 5 and above of the OSI model.
The most common use is in creating a secure encrypted Internet session (SSL VPN)
- All modern Web browsers support TLS.
Secure Socket Layer (SSL) Protocol
SSL is an older cryptographic protocol that is very similar to TLS.
The most common use is in Internet transactions.
- All modern Web browsers support SSL.
Due to issues with earlier versions of the protocol, it has largely been replaced by the TLS protocol.
- SSL v.3.3 has been developed to address the weaknesses of the earlier versions.
Network access services
Network interface controller (NIC)
It can also be called a network interface card.
The NIC is how a device connects to a network.
It works at two layers of the OSI model:
At Layer 2 (the data link layer), it provides the functional means of network communication by determining which networking protocols will be used (e.g., Ethernet and Point-to-Point Protocol). It also provides the local network node address through its burned in physical MAC address.
At Layer 1 (the physical layer), it determines how the network data traffic will be converted a bit at a time into an electrical signal that can traverse the network media being used.
Most modern computers come with at least one built in Ethernet NIC.
Routers and other network devices may use separate modules that can be inserted into the device to provide the proper NIC for the type of media they are connecting to and the networking protocol that is being used.
RADIUS (Remote Authentication DIal In User Service)
A remote access service that is used to authenticate remote users and grant them access to authorized network resources.
It is a popular AAA (Authentication, Authorization and Accounting) protocol used to help ensure that only authenticated end users are using the network resources they are authorized to use.
- The accounting features are very robust.
Only the requestor’s (the end user’s) password is encrypted.
TACACS+ (Terminal Access Controller Access-Control System Plus)
A remote access service that is used to authenticate remote devices and grant them access to authorized network resources.
It is a popular AAA protocol used to help ensure that only authenticated remote network devices are using the network resources they are authorized to use.
- The accounting features are not as robust as those of RADIUS.
All transmissions between devices are encrypted.
Other Services and Applications
RAS (Remote Access Services)
Not a protocol, but a road map.
A description of the combination of software and hardware required for a remote access connection. A client requests access from a RAS server, which either grants or rejects access.

Web services
Creating a means of cross communication.
Provides the means for communication between software packages or disparate platforms. It is usually achieved by translating the communication Into an XML (Extensible Markup Language)format.

Unified Voice services
Creating better voice communication systems.
A description of the combination of software and hardware required to integrate voice communication channels Into a network.
DHCP in the network
Static vs Dynamic IP Addressing
Most likely, a computer received its IP configuration from a DHCP (Dynamic Host Configuration Protocol) server. Not only did the server give the PC an IP address, but it also told the PC where the default gateway was – and more than likely – how to find the DNS server.
A computer will receive its IP configuration in one of two ways, statically (manually set) or dynamically(through a service like DHCP). Static address assignment works fine for a very small and stable network, but quickly becomes unwieldy and error prone as the network grows.
Static IP addressing
The administrator assigns an IP number and subnet mask to each host in the network.
- Each network interface that is going to be available to connect to the network requires this information.
The administrator assigns a default gateway location and DNS server location to each host in the network.
- These are required if access outside the network is going to be allowed (default gateway) and human friendly naming conventions are allowed to find network resources (DNS server).
Each time a change is made (Eg. a new default gateway is established) each IP configuration on each host must be updated.
Dynamic IP addressing
The administrator configures a DHCP server to handle the assignment process, which automates the process.
The DHCP server listens to a specific port for IP information requests.
Once it receives the request, the DHCP server responds with the required information.
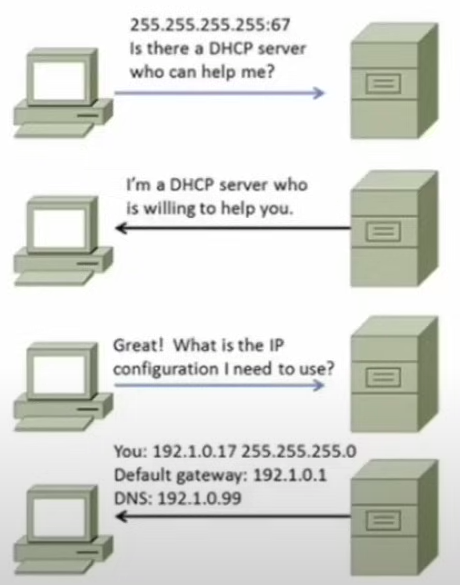
How does DHCP work?
Upon boot up, a PC that is configured to request an IP configuration, sends a DHCP discovery packet.
- The discovery packet is sent to the broadcast address: 255.255.255.255:67(UDP port 67).
The DHCP server receives the discovery packet and responds with an offer packet.
- The offer packet is sent to the MAC address of the computer using UDP port 68.
The computer receives the offer packet from the DHCP server and returns a request packet (requesting the proper IP configuration) to the DHCP server.
Once the DHCP server receives the request packet, it sends back an acknowledgement packet, which contains the required IP information.
Upon receipt of the acknowledgement packet, the PC changes its IP configuration to reflect the information received.
Components and process of DHCP
Ports used
PC sends discovery packet to 255.255.255.255:67.
DHCP sends the offer packet to the PC’s MAC address on port 68.
Address Scope
- Administrator configures the IP address range with one that is available to be handed out.
Address reservations
Administrator receives specific IP addresses to be handed out to specific MAC addresses. These are used for devices that should always have the same IP address (Eg. servers and routers).
Allows for these addresses to be changed from a central location instead of having to log in to each device separately.
Leases
Configuration parameters are only good for a specified amount of time.
Leases are configured by the administrator.
Options
Default gateway location
DNS server address (there can be more than one)
Time server address
Many additional options
Preferred IP configuration
A PC can have a preferred IP address.
The administrator can configure the DHCP server to either honor the preference or ignore it.
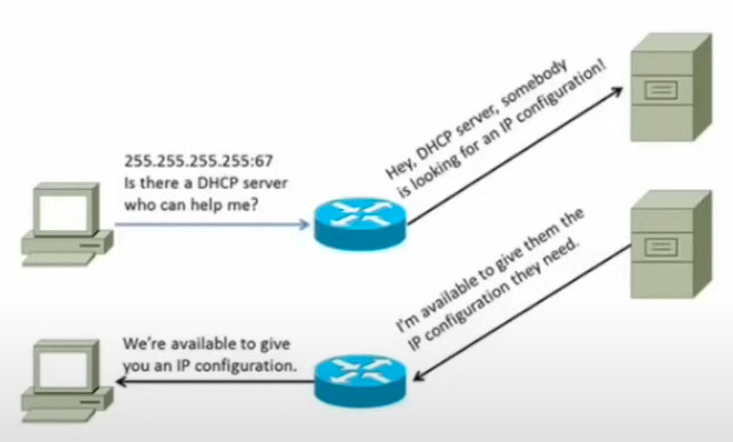
Under the right circumstances, a DHCP server isn’t required to reside on the local network segment.
Broadcast transmissions cannot pass through a router. If there is not a DHCP server on the local network segment, the router can be configured to be a DHCP relay. When a DHCP relay (which can also be called an IP helper) receives a discovery packet from a node, it will forward that packet to a network segment on which the DHCP server resides.
This allows for there to be fewer configured DHCP servers in any network, reducing the amount of maintenance that an administrator needs to perform.
Introduction to DNS service
DNS servers
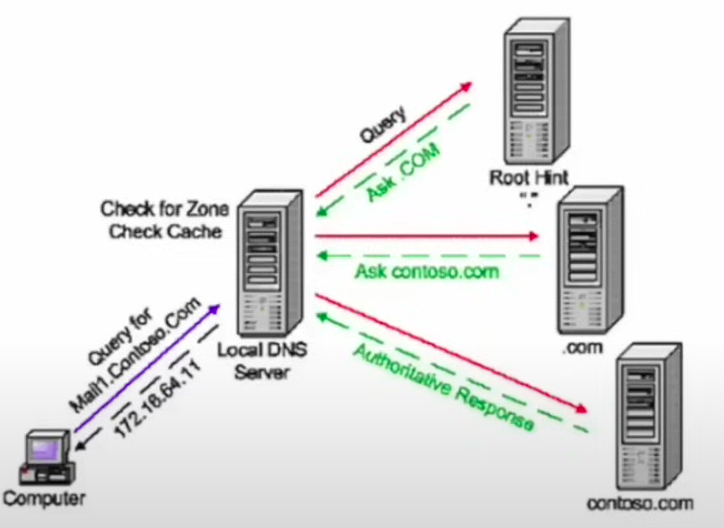
DNS is the process that maps human friendly names to IP addresses. Without it, we would have to memorize numerous IP addresses.
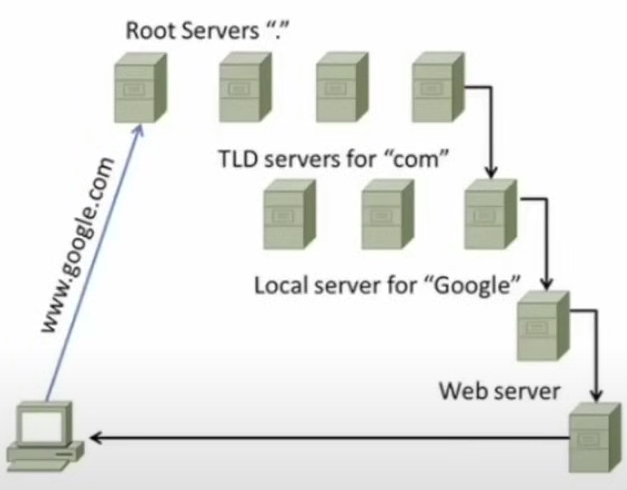
Domain Name System (DNS) is hierarchical (very structured) in nature. If the local DNS server apparatus doesn’t contain the record needed, it sends a request up the chain until a positive response is received (which gets back down to the original requestor). DNS does not require a FQDN (fully qualified domain name) in order to function.
Different Types of DNS servers
Local DNS server
- The server on the local network contains the HOSTS file that maps the FQDN to IP addresses in the local subdomain.
Top Level Domain (TLD) server
The server that contains the records for a top level domain.
Examples include: com, org, net, edu, gov , mil and int.
Each of these contain all of the information for their respective domains (kind of).
TLD servers do delegate down the second level to ease the load; however, the TLD server is the responsible server.
Root server
- The server that contains the records for the TLD servers.
Authoritative
An authoritative DNS server is one that responds to a request that has been specifically configured to contain the information.
An authoritative response comes from the DNS server that actually holds the original record.
Non-Authoritative
A non authoritative DNS server is one that responds to a request with DNS information that it received from another server.
A non authoritative response is not a response from the official name server of the domain. Instead it is a second or third hand response (or even further removed).
DNS records
A record
- Maps the host name to their IPv4 records.
AAAA record
- Maps the host name to their IPv6 records.
CNAME record
- Maps canonical (alias) names to hostnames.
PTR record
- Pointer record that points to a canonical name.
MX record
- Maps to the email server that is specified for a specific domain. It is the record that determines how email travels from sender to receipt.
Dynamic DNS
Dynamic DNS (DDNS)
Permits lightweight and immediate updates to a local DNS database. This is very helpful when the FQDN remains the same, but the IP address is able to change on a regular basis.
It is implemented as an additional service to DNS.
DDNS updating
A method of updating traditional name servers without the intervention of an administrator (no manual editing or inputting of the configuration files is required).
A DDNS provider supplies software that will monitor the IP address of a referenced system. Once the IP address changes, the software sends an update to the proper DNS server.
DDNS is useful when access is needed to a domain whose IP address is being supplied dynamically by an Internet Service Provider (ISP).
Introduction to network address translation
Purpose
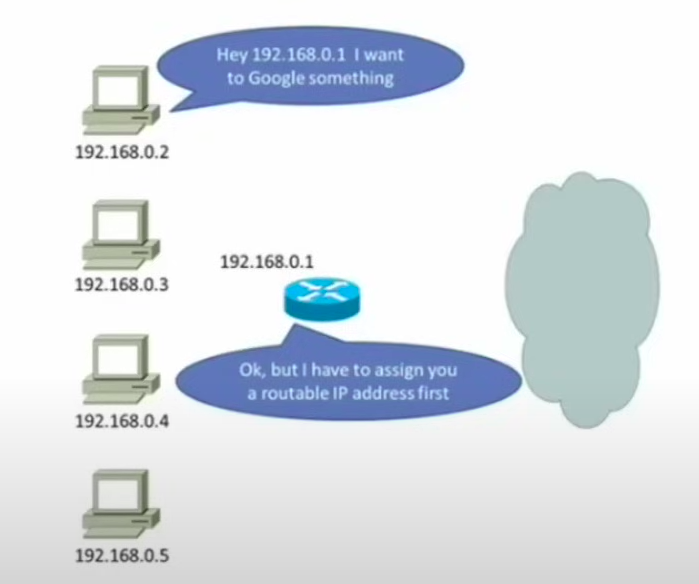
Network address translation (NAT) solves the problem of how to route non routable IP addresses.
As a partial effort to conserve the IPv4 address space, the private IPv4 addressing spaces were developed These address spaces were removed from the public IPv4 address spaces and made non-routable across public IPv4 networks.
Being non-routable prevents the private IPv4 addresses from communicating with remote public networks. NAT very simply solves this problem. A router with NAT enabled will translate a private IP address into a routable public IP address. When the response returns to the router, it passes the response back to the device that requested it.
How does NAT work?
The two categories of NAT:
Static NAT (SNAT)
Each private IP address is assigned to a specific routable public IP address. This relationship is kept and maintained by the NAT enabled router
When a device needs access outside of the local network, the router translates the local IP address to the assigned public IP address When the response comes back, the router will translate the public IP address back into the local one.
SNAT is not flexible and leads to scalability issues. An individual routable IP address must be kept for every device that requires access outside of the local network.
Dynamic NAT (DNAT)
The NAT enabled router dynamically assigns a routable IP address to devices fro a pool of available public IP addresses.
When a device needs access outside of the local network, the router performs the NAT function, only the public IP address comes from a reusable pool of public IP addresses.
As initially designed, DNAT was more flexible than SNAT, but still led to some scalability issues. As more network traffic requires access to remote networks, the pool of available public IP addresses needs to increase or outside access cannot be achieved.
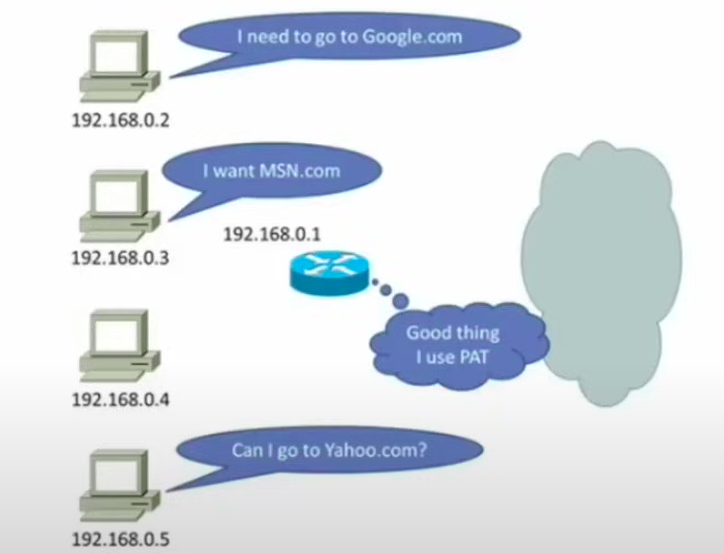
Port address translation (PAT)
PAT is a type of DNAT that was developed to increase the scalability of NAT.
When a local network device requires access to a public network, the NAT enabled router dynamically assigns the public IP address to the device with the addition of dynamically assigning a port number to the end of the public IP address.
The router tracks the IP addresses and port numbers to ensure that network traffic is routed to and from the proper devices.
PAT still requires a pool of public IP addresses, but the pool may only contain one address or it may contain several for a large private network.
This is the preferred method of implementing NAT for two reasons: less public IP addresses are required and it is also easier for administrators to maintain.
The NAT terminology
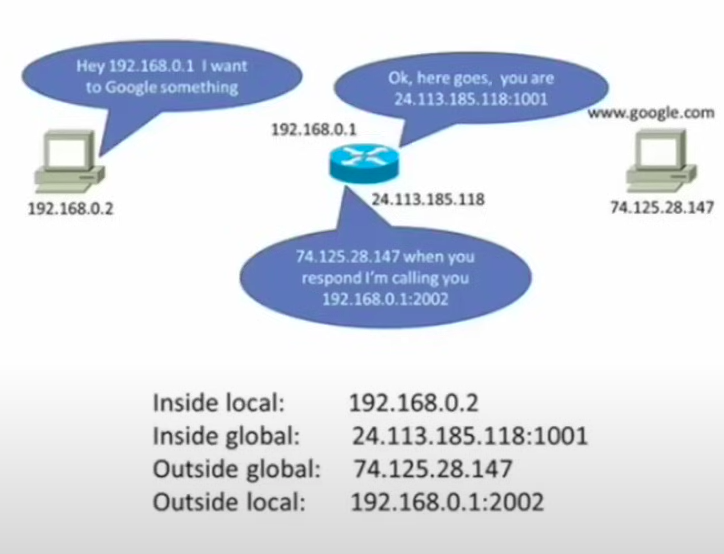
Inside local address: a private IP address on the local network.
- The private IP address assigned to a specific device.
Inside global address: a public IP address referencing an inside device.
- The public IP address assigned to the inside device by the NAT enabled router to allow access outside of the network.
Outside global address: a public IP address referencing an outside device.
- The public IP address assigned to a device outside of the local network.
Outside local address: a private IP address assigned to an outside device.
- The private IP address assigned to an outside device on the interior of the focal network.
To keep expanding your knowledge base about networking and learning with me. Don't forget to subscribe to my newsletter to receive updates about my new learning everyday. Consider following me on LinkedIn. Want to know more about me!! follow me on Instagram!!
Subscribe to my newsletter
Read articles from Shreyas Ladhe directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Shreyas Ladhe
Shreyas Ladhe
I am Shreyas Ladhe a pre final year student, an avid cloud devops enthusiast pursuing my B Tech in Computer Science at Indian Institute of Information Technology Vadodara ICD. I love to learn how DevOps tools help automate complex and recurring tasks. I also love to share my knowledge and my project insights openly to promote the open source aspect of the DevOps community.