What is Cross - Site Scripting ?
 Aayush Srivastava
Aayush Srivastava
Introduction
Cross-site scripting (XSS) is a common web security vulnerability that allows attackers to inject malicious scripts into web pages viewed by other users. This type of attack occurs on the client side, where the goal is to execute harmful code in the victim's web browser by exploiting a legitimate web application.
Web applications that fail to sanitize user input before displaying it are particularly vulnerable to XSS attacks. For instance, consider the following script as a simple example of an XSS attack:
<img src="validImage.png" onclick="javascript:prompt('XSS')" />
I tested this on a simple online To-Do application by adding the script as a to-do item. You can try it out on various applications, such as chat bots, to see how they respond. Remember, the primary goal of this exercise is to learn and understand the mechanics of XSS attacks.
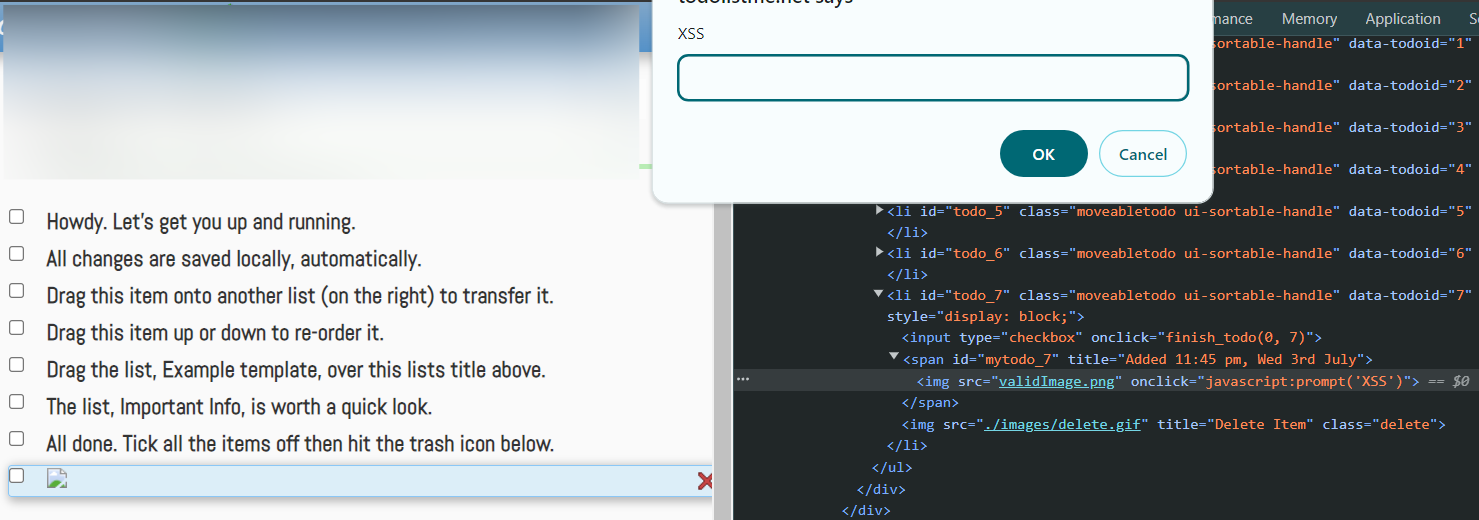
Yaay! You’ve successfully executed an XSS attack. Understanding how these attacks work makes you more aware of the vulnerabilities in web applications and the importance of securing them.
After successfully injecting the script, you’ll see it executed within the application. This demonstrates how easy it can be for an attacker to exploit weaknesses if proper security measures aren’t in place.
Types of XSS
There are 3 major types of XSS attacks :
- Reflected XSS
Reflected XSS, also known as Non-Persistent XSS, is the most common type of XSS attack. In this attack, the payload is part of the HTTP request sent to the web server. The server then reflects this payload back in the HTTP response, incorporating it into the page content. This type of attack is often used to generate malicious links or phishing emails, tricking victims into making requests to the server that execute the injected scripts.
- Stored XSS
Stored XSS, also known as Persistent XSS, is the most damaging type of XSS attack. In this attack, an application receives data from an untrusted source and stores it, allowing the malicious data to be permanently injected into the web application. A common example is a vulnerable comments section, where an attacker can embed malicious HTML tags. These tags become a permanent feature of the page and are executed every time the page is loaded.
- DOM - based XSS
DOM-based XSS is a client-side vulnerability rather than a server-side one. It occurs when JavaScript takes data from an untrusted source and writes it back to the DOM in an unsafe way, such as updating innerHTML without proper sanitization. An attacker can exploit this by modifying input fields in a form to inject malicious scripts, which are then executed when the DOM is updated.
Preventing XSS attacks
Making applications XSS-proof can be complex, especially as the complexity of the application increases. However, to prevent trivial XSS attacks, you can implement a combination of the following practices:
1. Always sanitize text taken from the client side before storing or sending it via HTTP. This ensures that any potentially malicious code is neutralized before it can be executed.
2. Perform encoding on data whenever it is the output of user-controlled input, such as in HTTP responses. This helps prevent the execution of malicious scripts by converting potentially dangerous characters into their encoded equivalents.
3. Effectively use CSP ( Content Security Policy ) to prevent the loading of malicious content on your website. CSP can reduce XSS vulnerabilities by specifying which sources of content are trusted and allowed to be executed.
Conclusion
Cross-site scripting (XSS) is a prevalent and dangerous web security vulnerability that can lead to severe consequences if not properly addressed. Understanding the different types of XSS attacks—Reflected, Stored, and DOM-based—is crucial for both developers and security professionals. By implementing robust security practices, you can significantly reduce the risk of XSS attacks. Staying informed and proactive about web security is essential to safeguarding your applications and protecting your users.
Happy coding and stay secure !
Subscribe to my newsletter
Read articles from Aayush Srivastava directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Aayush Srivastava
Aayush Srivastava
As a web developer, I love creating applications that are both robust and user-friendly. I enjoy diving into discussions about creative solutions for everyday challenges and am always on the lookout for new ideas.