Introduction to Azure Networking: Key Concepts and Best Practices
 Hema Sundharam Kolla
Hema Sundharam KollaTable of contents
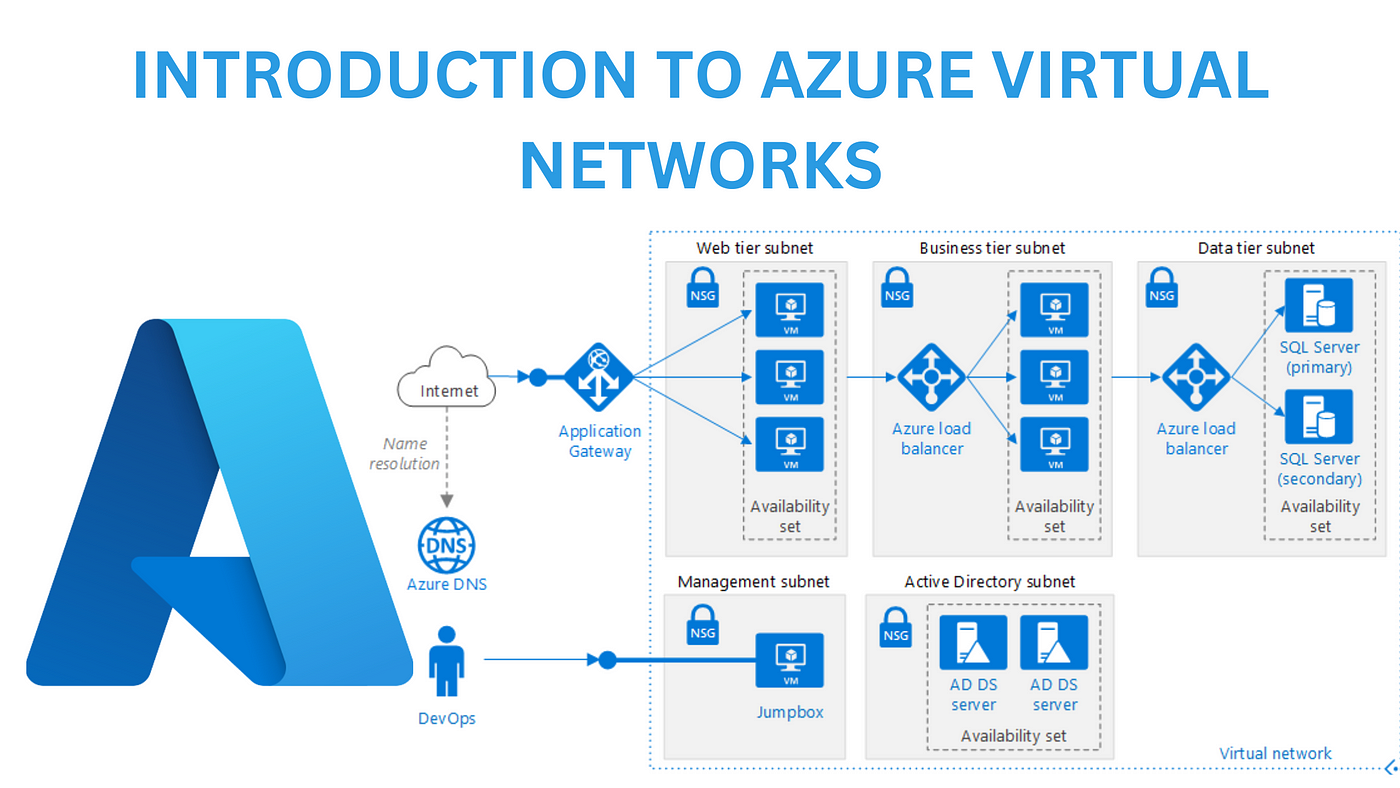
Azure Networking
Virtual Network (VNET)
Azure VNET
Network Security Group (NSG)
Application Security Group (ASG)
Azure Route Table
User-Defined Routes (UDRs)
Azure DNS
Azure Firewall
VNET :
Let us understand this topic with a simple example. Let's say there are two companies, Flipkart and Myntra. They requested their DevOps engineers to create a server at US East 1. The DevOps engineers of both companies created the server at the same data center. Now, suppose for some reason the Myntra website got hacked. Then automatically, the Flipkart website will be easy to hack by the hacker because both are present in the same data center. To overcome these types of concerns, Azure introduced VNET.
Now let's say Flipkart requests a server. Azure will create a virtual network, and for Myntra, Azure will not allow access to the VNET created for Flipkart. However, Azure creates the VNET in the same zone without affecting the Flipkart VNET.
How to effectively use the VNET?
The size of the VNET is measured in IP addresses. This can be defined using CIDR. Let's say 116, which means 65,536 IP addresses. Since this is a large number, we can divide it into parts based on our requirements.
Subnets :
So, we can divide the VNET into subnets. Let's say I had different security for different types of applications. For example, one is a web application accessed by everyone, another is an app that needs to be accessed by the company, and the third is a database accessed by the admin. To manage these, we will arrange a subnet for each and provide different security based on the requirements.
What kind of security?
Nobody from the internet can access my databases, only company employees can access internal applications, and everyone can access web applications, so we need to create subnets and size them based on the CIDR block.
NSG :
Network Security Group can be defined for a subnet or instance level, but it's better to do it at the subnet level or for a specific VM, and it consists of inbound and outbound rules that need to be configured to access the resources.
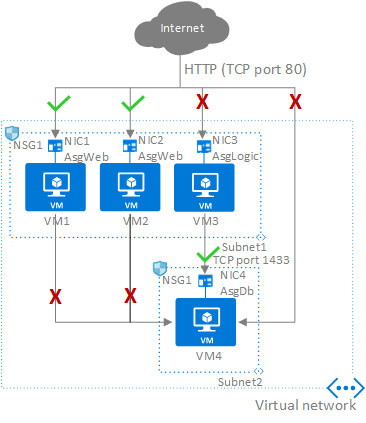
ASG :
Basically, it enhances the capabilities of NSG. Let's say, for example, we need to configure all the resources with NSG, and now the web can't access the database, but the business applications have access to the database. With the help of ASG, we will group all the business applications and give them access to the database. It's better to use a combination of NSG and ASG.
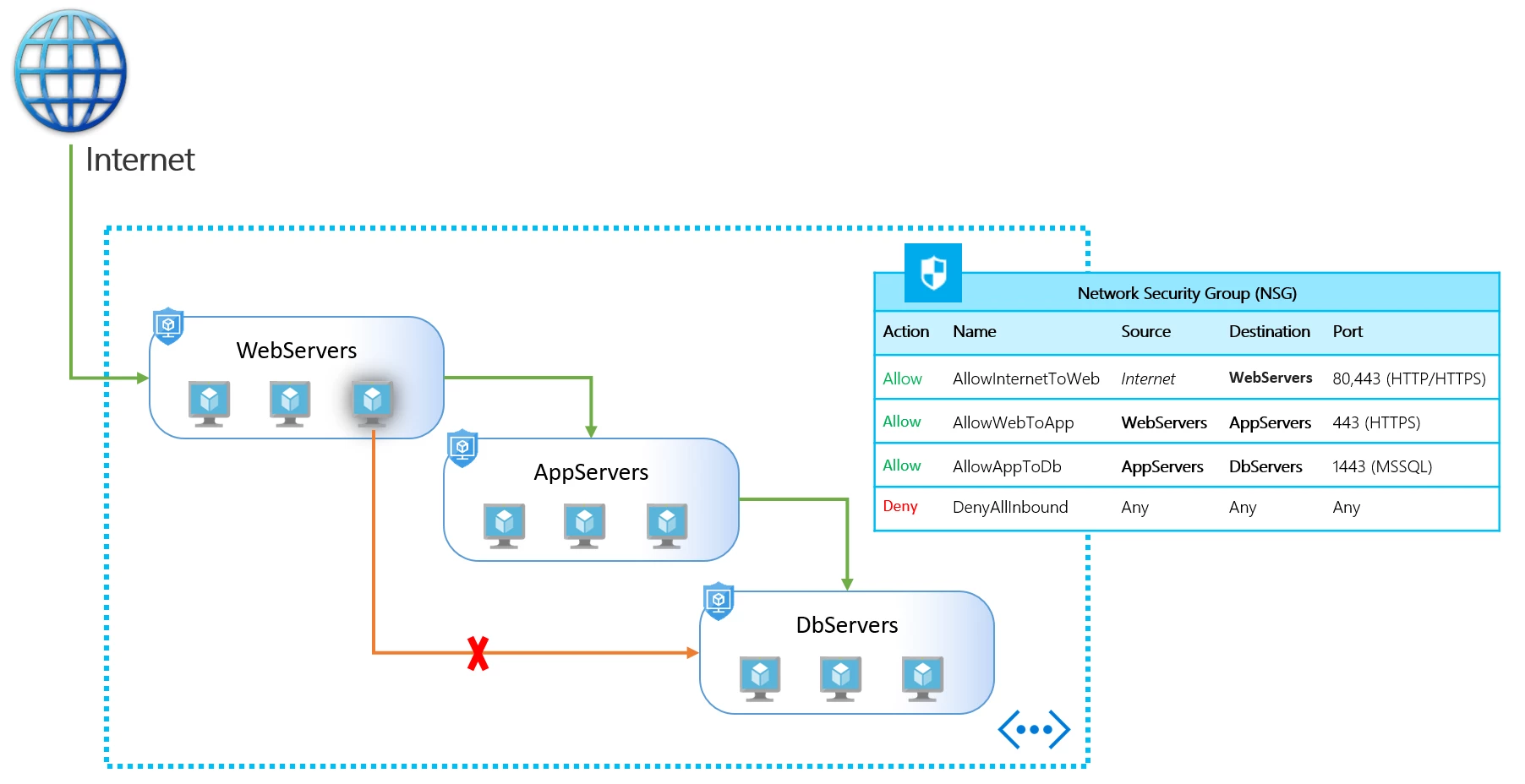
Route Table and User-Defined Routes:
1. Route Table: A route table in Azure is essentially a set of rules (routes) that determine how network traffic is directed. Think of it as a map that tells your network traffic which path to take to reach its destination.
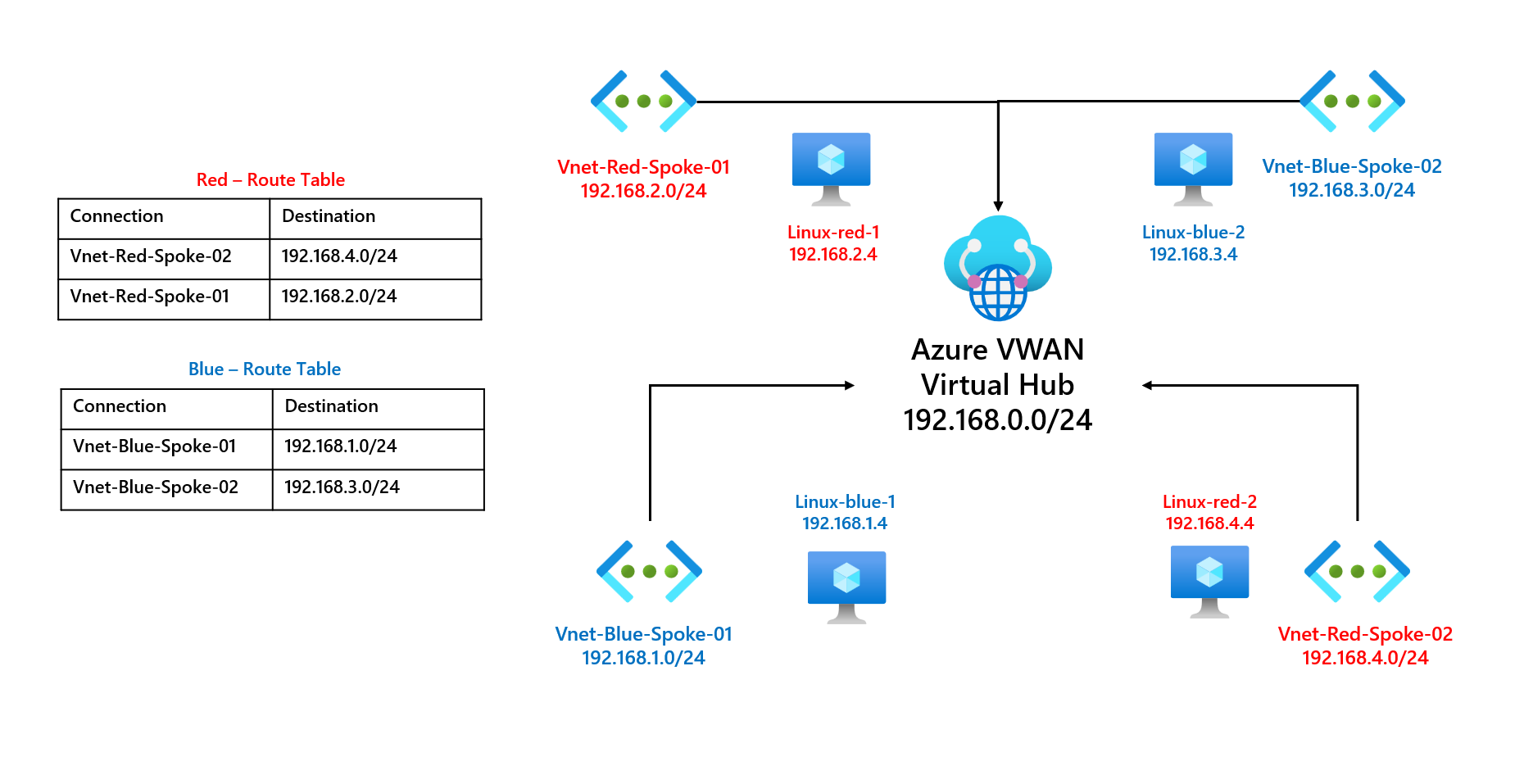
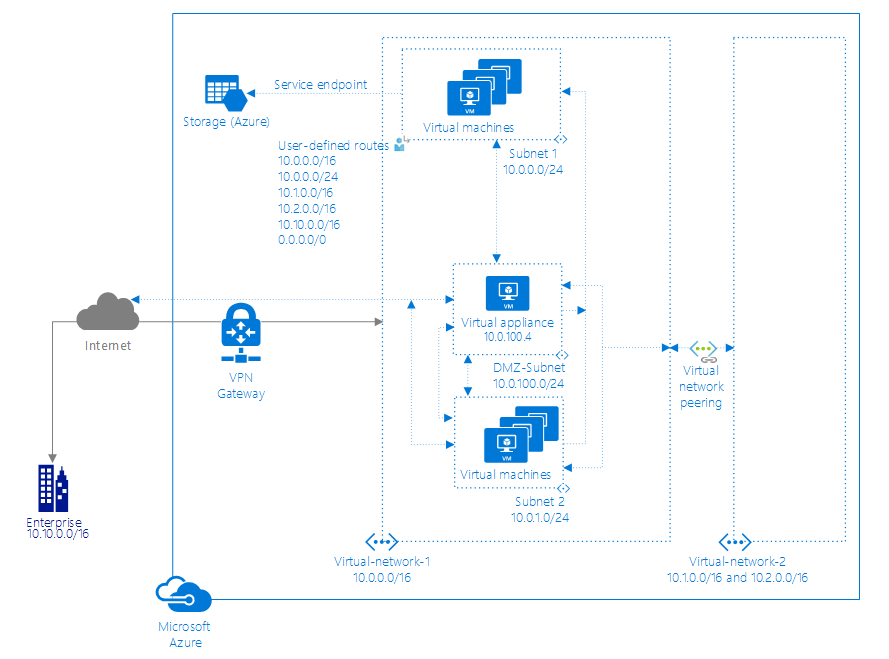
2. User-Defined Routes (UDRs): By default, Azure provides system routes that manage the flow of traffic. However, there might be situations where you need to customize this routing. This is where User-Defined Routes (UDRs) come into play. UDRs allow you to create your own routing rules to direct traffic according to your specific needs.
Let's understand how to set up security with a real-world example :
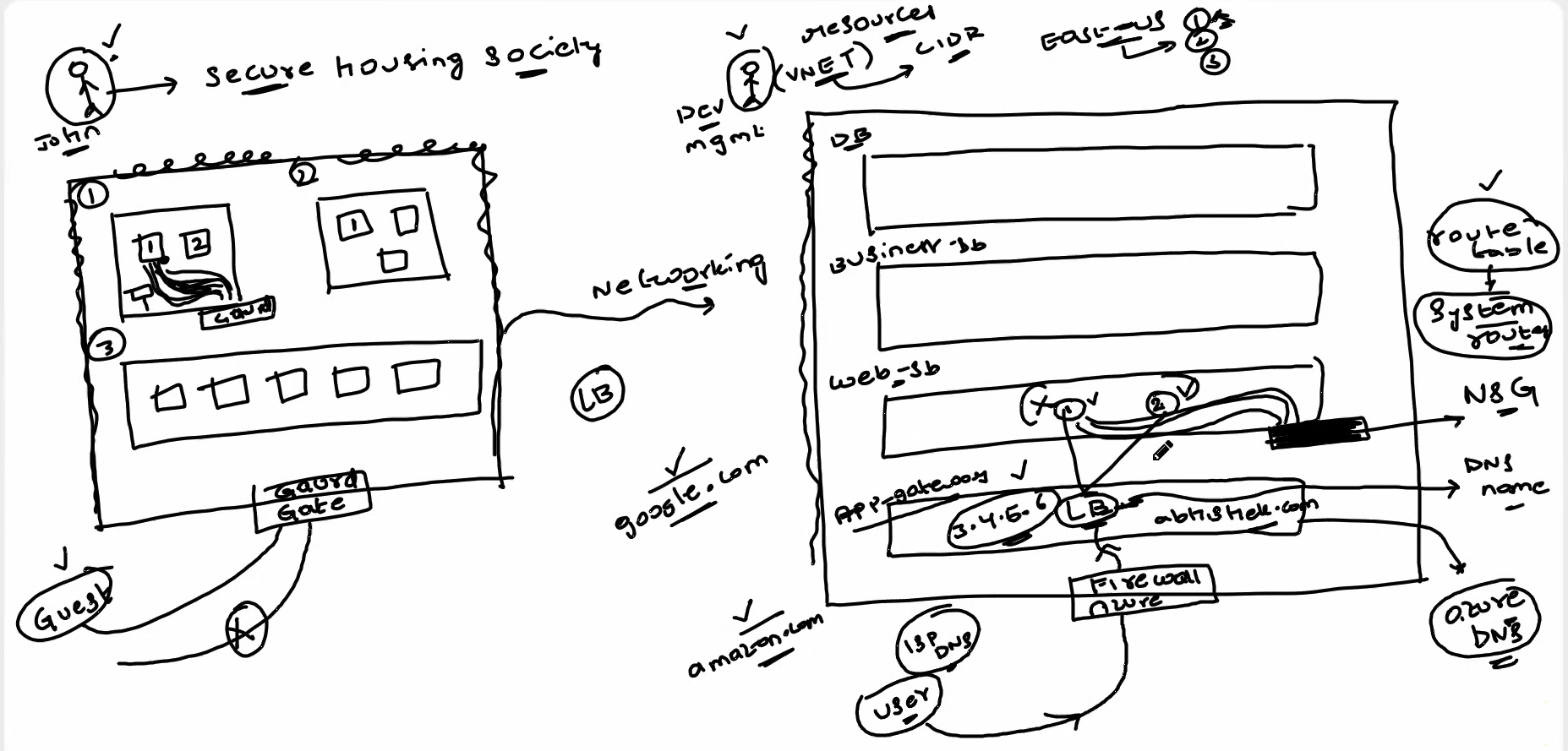
Let's say there is a person named John. He has a piece of land and he built a fence around it. Let's take that land as a virtual network (VNET). He built apartments there, and we can consider these as three types of applications within the VNET. John set up security for the land, which we can take as a Azure Firewall, and arranged for a guard. This guard has all the details of the people living in John's society. Let's consider this as a Route table and system route as a security guard.
Let's dive into the main matter: the VNET consists of a firewall, and any IP address that needs to enter the VNET must be configured with the NSG (Network Security Group), so only authorized IP addresses or people can enter; to determine the path for accessing a particular resource, the route is present in the route table, and each resource has a system route noted in the route table, so using NSG and ASG, we will provide different types of security based on permissions for accessing specific resources.
DNS in Azure :
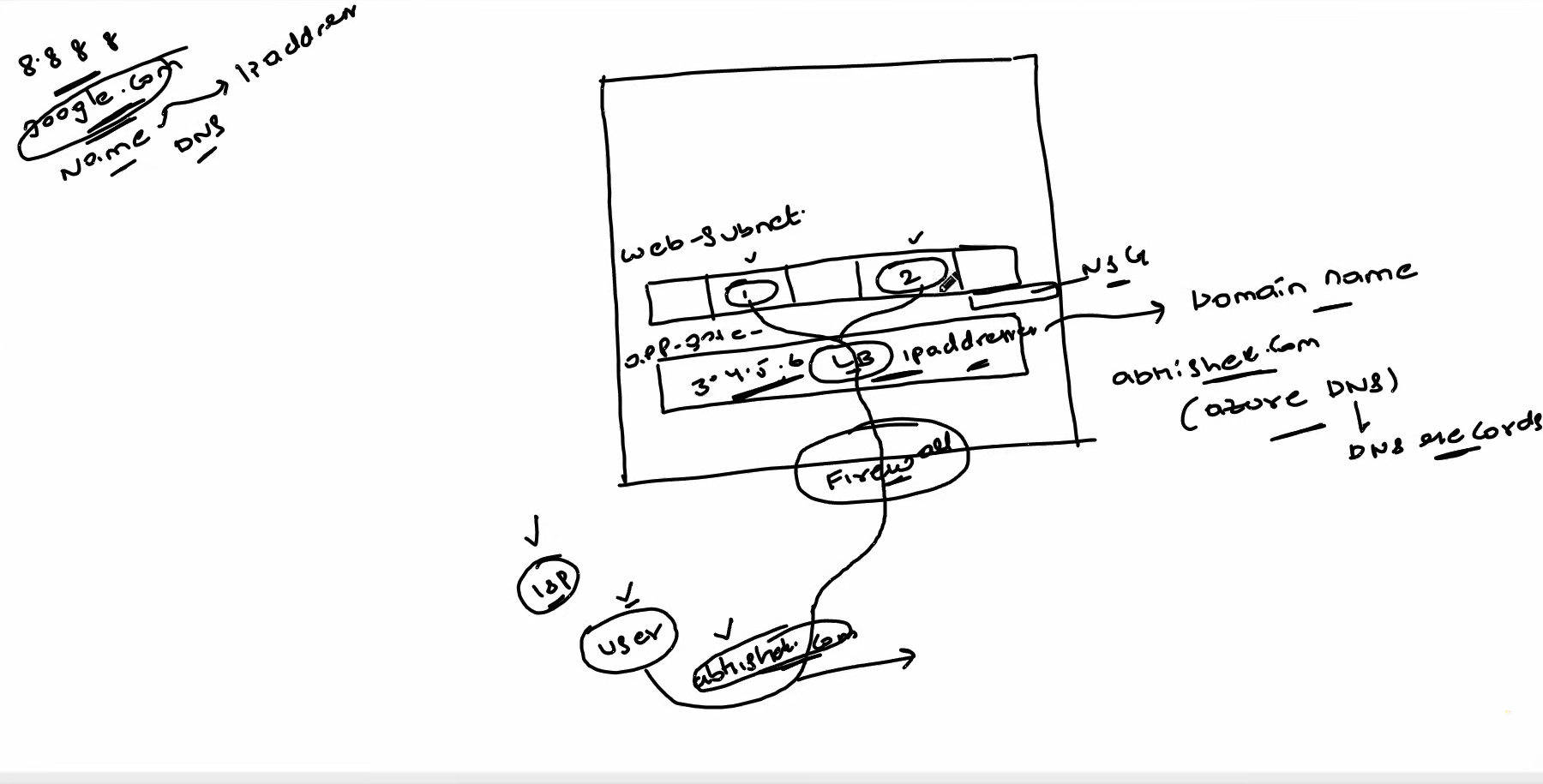
Let's say we search using the names google.com and amazon.in, but we can't access them through their IP addresses. However, we deploy our resources on specific IP addresses, but we can't use IP addresses for searching. To overcome this, we use DNS (Domain Name Service). We buy a domain and configure it with that IP address. Now, we need to deploy amazon.in on Azure and configure our DNS with Azure DNS so that a user can access that resource. After this, a user comes through the ISP (Internet Service Provider) and searches for Abhishek.com. Based on the permissions set by the NSG, the user can access it accordingly.
In conclusion, Azure Networking offers a robust and flexible framework for managing and securing your cloud infrastructure. By leveraging key concepts such as VNETs, subnets, NSGs, ASGs, route tables, and DNS, you can create a highly secure and efficient network environment tailored to your specific needs. Understanding and implementing these best practices will help ensure that your applications and data remain protected while optimizing performance and accessibility. As you continue to explore and utilize Azure's networking capabilities, you'll be well-equipped to handle the complexities of modern cloud-based systems.
Subscribe to my newsletter
Read articles from Hema Sundharam Kolla directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Hema Sundharam Kolla
Hema Sundharam Kolla
I'm a passionate Computer Science student specializing in DevOps, cloud technologies, and powerlifting. I've completed several certifications, including AWS Cloud Practitioner and Google’s Generative AI badge, and I'm currently exploring both AWS and Azure to build scalable, efficient CI/CD pipelines. Through my blog posts, I share insights on cloud computing, DevOps best practices, and my learning journey in the tech space. I enjoy solving real-world problems with emerging technologies and am developing a platform to offer career advice to students. Outside of tech, I'm a competitive powerlifter, constantly striving to improve and inspire others in fitness. Always eager to connect with like-minded individuals and collaborate on projects that bridge technology and personal growth.