Deploying Postfix on AWS EC2: Easy Installation Steps
 Alok Shankar
Alok Shankar
Introduction : Postfix is a popular open-source mail transfer agent (MTA) that can be configured to send emails from your server.
In this blog, I will walk you through installing and configure Postfix in Linux Ec2 instance so that it can be used to send emails by applications those installed on the same server that Postfix is installed on.
Why should we use Postfix as SMTP rely :
Using Postfix as an SMTP relay can be beneficial in various scenarios.
Scenario 1:
An organization has multiple internal applications and servers that need to send emails. These might include web applications, monitoring tools, internal notification systems, and more. Rather than configuring each application to handle its own email delivery, the organization decides to use a centralized SMTP relay server. This relay server will handle all outbound email traffic, providing a single point of control and management.
Scenario 2:
Suppose you manage a cloud server like AWS EC2 on which you have installed applications that need to send email notifications, running a local, send-only SMTP relay server is a good alternative to using a 3rd party email service provider rather than running a full-blown SMTP server.
Use Cases
Transactional Email: Ideal for sending automated emails like notifications, alerts, and confirmations.
Business Communications: Suitable for handling internal and external business email communications.
Bulk Email Sending: Efficiently manages bulk email sending for newsletters, marketing campaigns, etc.
Educational and Research Institutions: Often used by universities and research institutions for secure and reliable email services.
Benefits
· Performance and Efficiency: Handles high volumes efficiently.
· Security: Strong security features to protect against attacks.
· Reliability: Proven stability and robustness.
· Ease of Use: Simple configuration and management.
· Compatibility: Works well with other services and supports standards.
· Scalability: Suitable for small to large-scale setups.
· Community Support: Active community and professional support options.
· Cost-Effective: Free, open-source, and low maintenance costs.
· Logging and Monitoring: Detailed logging and easy integration with monitoring tools.
· Customizability: Highly extensible and customizable.
Installation Steps :
Step 1: Update the System
First, ensure your system is up-to-date.
sudo yum update -y # For Amazon Linux and CentOS
sudo apt update -y # For Ubuntu and Debian
sudo apt upgrade -y # For Ubuntu and Debian
Step 2: Install Postfix
Install Postfix on your EC2 instance.
sudo yum install postfix -y # For Amazon Linux and CentOS
sudo apt install postfix -y # For Ubuntu and Debian
Step 3: Configure Postfix
Open the Postfix configuration file for editing.
sudo vi /etc/postfix/main.cf
Make the following changes in the main.cf file:
Set the mail name: myhostname = your_domain.com If you want that Postfix uses a different hostname than the fully-qualified domain name (FQDN) that is returned by the gethostname() function, add the myhostname parameter:For example, Postfix adds this hostname to header of emails it processes.
Set the domain name: mydomain = your_domain.com If the domain name differs from the one in the myhostname parameter, add the mydomain parameter: mydomain = <example.com\>
Set the origin: myorigin = $mydomain Add the myorigin parameter and set it to the value of mydomain: With this setting, Postfix uses the domain name as origin for locally posted mails instead of the hostname.
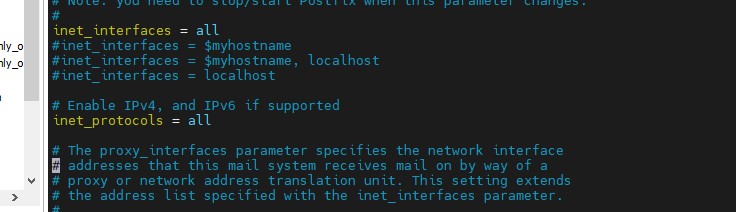
Configure the destination: By default, Postfix receives emails only on the loopback interface. To configure Postfix to listen on specific interfaces, update the inet_interfaces parameter to the IP addresses of these interfaces: inet_interfaces = loopback-only
To configure Postfix to listen on all interfaces, set: inet_interfaces = all
Set the relay host: relayhost = [smtp.yourisp.com]:587
Add the mynetworks parameter, and define the IP ranges of trusted networks that are allowed to send mails: mynetworks = 127.0.0.1/32, [::1]/128, 192.0.2.1/24, [2001:db8:1::1]/64
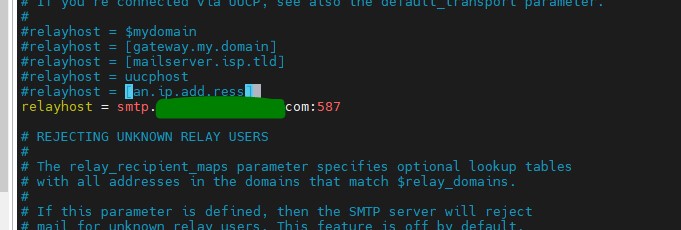
Step 4 : Verify if the Postfix configuration in the main.cf file is correct:
postfix check
Step 5 : Enable the postfix service to start at boot and start it
systemctl enable --now postfix
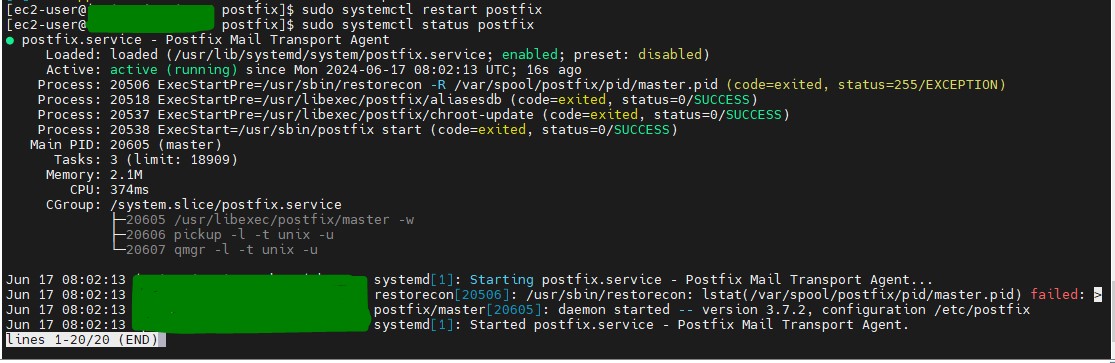
Step 6 : Restart Postfix to apply the changes.
sudo systemctl restart postfix
sudo systemctl status postfix
Step 7 : Test the Configuration
After installing and configuring Postfix on your AWS EC2 instance, it's essential to verify that the setup works correctly by sending a test email. The mailx utility is a powerful tool that you can use for this purpose.
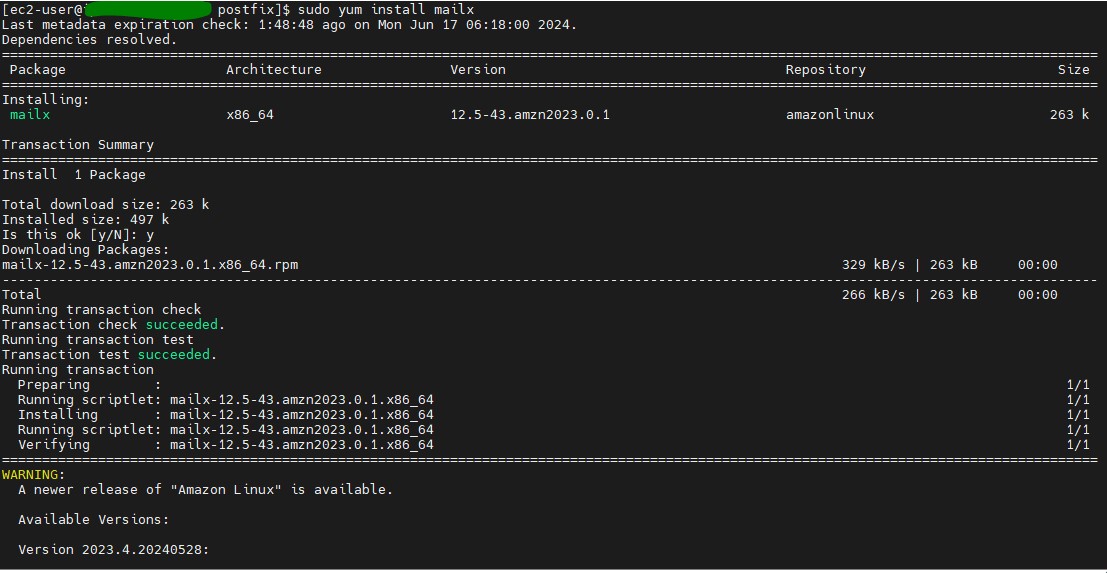
Install mailx if it is not already installed. You can do this by running.
sudo yum install mailx -y # For Amazon Linux, CentOS, or RHEL
sudo apt-get install mailx -y # For Ubuntu or Debian
Sending a Test Email Open your terminal and use the following command to send a test email:
echo "This is a test email body" | mailx -s "Test Email Subject" recipient@example.com
echo "This is a test email body": This part of the command creates the email body.mailx -s "Test Email Subject": This part sets the subject of the email.recipient@example.com: Replace this with the actual recipient's email address.
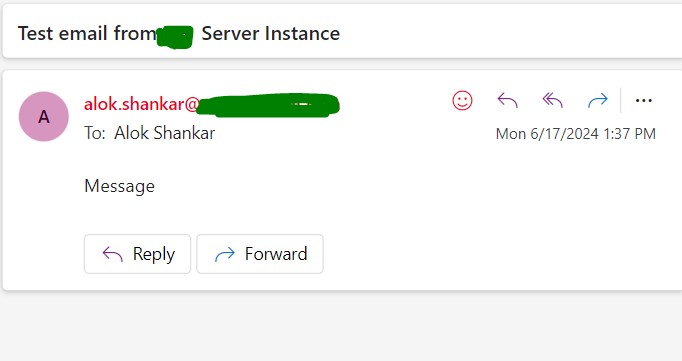
echo "Message" | mail -s "Test email from Server Instance " -r alok.shankar@example.com alok.shankar@example.com
Troubleshoot 1: In case of errors, check the /var/log/maillog file
Verifying the Email Delivery
Check the mail logs to ensure the email was sent successfully. Use the following command to view the logs:
sudo tail -f /var/log/maillog # For Amazon Linux, CentOS, or RHEL sudo tail -f /var/log/mail.log # For Ubuntu or DebianIf you encounter any issues, the log entries can help diagnose problems such as connectivity issues, authentication errors, or misconfigurations.
Troubleshoot 2:
There is no maillog in /var/log/
Postfix configuration is defined in the directory /etc/postfix, especially in the files main.cf and master.cf. However, rather than editing these files directly, you can use a command-line utility postconf that allows you to view and change a configuration setting.
The directive maillog_file determines the name of an optional log file that is written by the Postfix service.
The directive can hold the following values:
• An empty value selects logging to the Syslog.
• A value /dev/stdout determines logging to standard output.
• Otherwise, the value holds an absolute path to the log file (typically, /var/log/postfix.log).
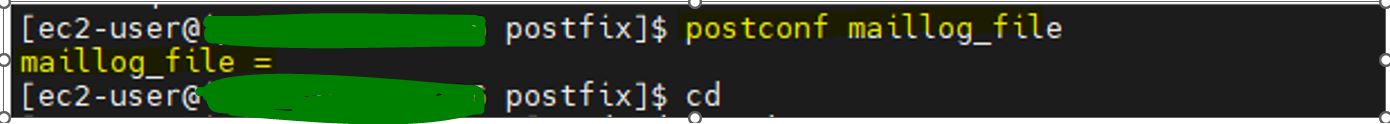
The output shows that Postfix logs into the Syslog
Configuring Logging Without Syslog: If you don't want to use the Syslog daemon for the log maintenance, you can set up Postfix to store logs into the stdout, stderr, or customfile.
Let's change the destination of the Postfix log.
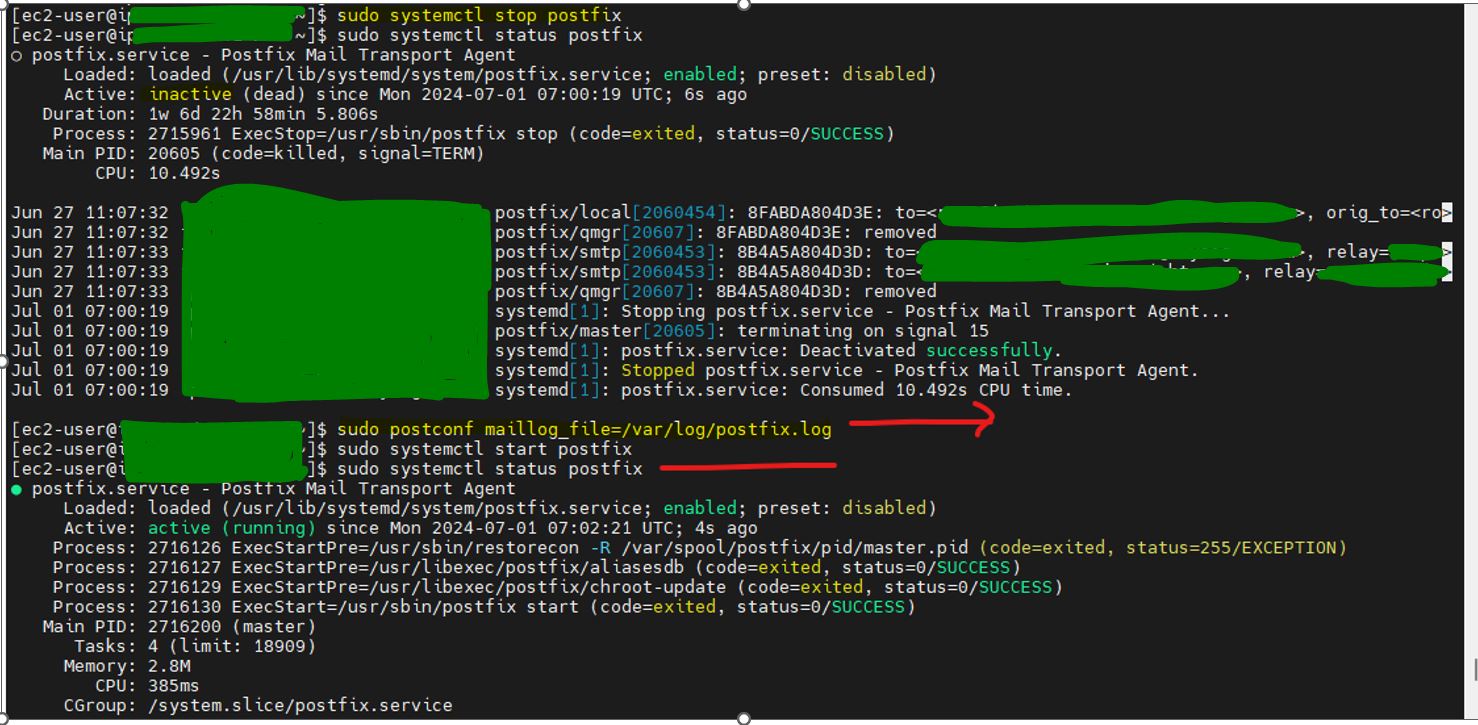
At first, you must stop the Postfix service by executing postfix stop :
sudo systemctl stop postfix
Now, you can change the value of the directive maillog_file to the desired log destination :
sudo postconf maillog_file=/var/log/postfix.log
When you set up the value of the maillog_file, then you must start Postfix with the new configuration:
sudo systemctl start postfix
check status
sudo systemctl status postfix
Verify log folder :
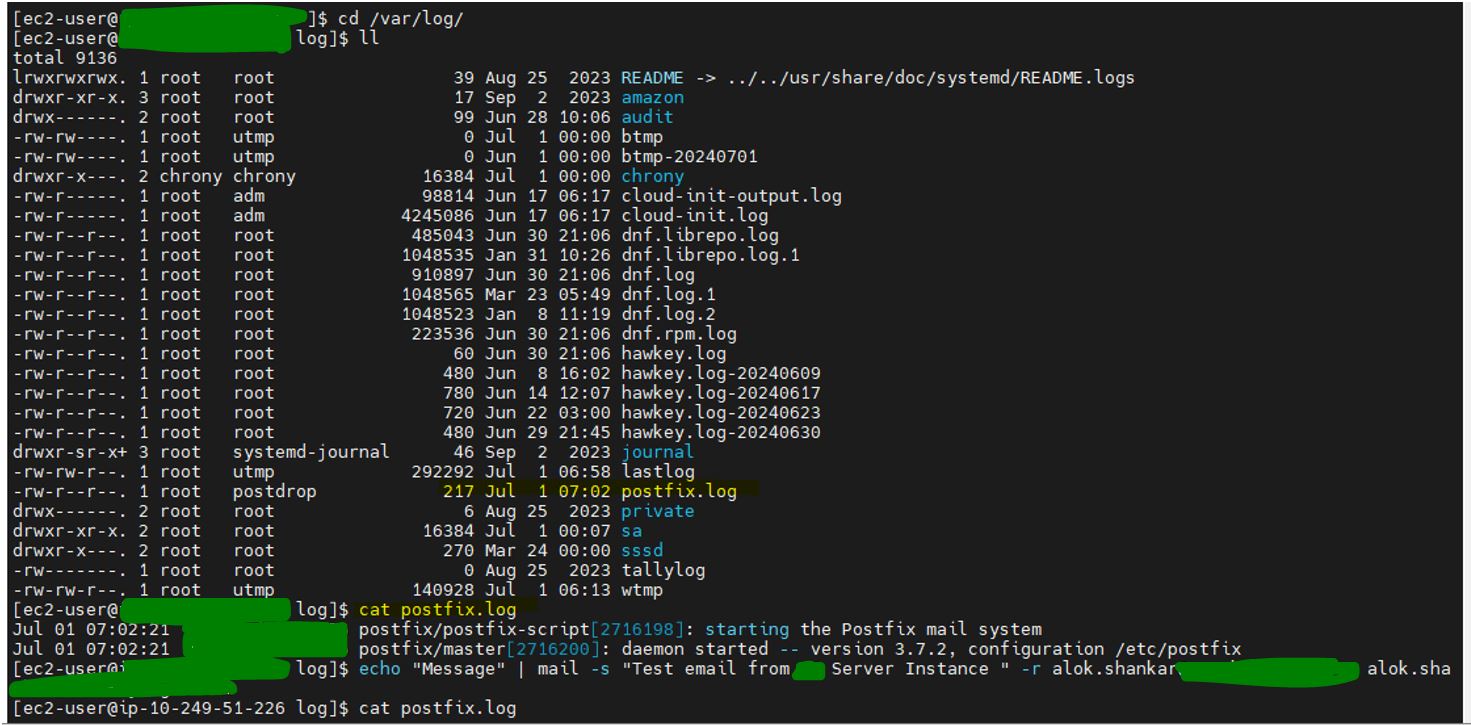
By following these steps, you can configure Postfix to log custom information to a specified file, helping you manage and analyze your email traffic more effectively.
By following above steps, you can ensure that your Postfix server is correctly configured and troubleshoot any issues that arise.
Congratulations, you now have a fully functional and secure Postfix mail server running on an EC2 instance!
Subscribe to my newsletter
Read articles from Alok Shankar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Alok Shankar
Alok Shankar
Dedicated and highly skilled AWS DevOps and Linux professional with over 10+ years of experience in designing, implementing, and maintaining cloud infrastructure and CICD pipelines. Proficient in optimizing processes, automating workflows, and ensuring the reliability and scalability of cloud-based systems. Demonstrated expertise in Kubernetes and containerization technologies. Proven ability to understand and execute the complete deployment lifecycle. Proven expertise in real-time troubleshooting and leading cross functional teams to success.