From Network to Application: Leveraging VM-Series Firewalls for Holistic Advanced Security on AWS
 Sourav Chakraborty
Sourav ChakrabortyAs businesses transition to cloud environments like AWS, protecting private web servers from evolving threats becomes crucial. Traditional security measures alone may not suffice in a dynamic cloud landscape. This blog explores deploying VM-series firewalls for robust protection, details the configuration of security policies, NAT, and route tables, and compares their comprehensive capabilities to a Web Application Firewall (WAF).
Why Use VM-Series Firewalls for AWS Private Web Servers?
VM-series firewalls offer dual protection for both network and application layers, setting them apart from WAFs that primarily safeguard web applications.
Dual-Layer Protection: Network and Application Layers
1. Network Layer Protection:
Traffic Filtering: Inspects and filters traffic based on IP addresses, protocols, and ports.
Advanced Threat Detection: Detects and blocks sophisticated threats such as malware, botnets, and DDoS attacks through deep packet inspection and behavioral analysis.
2. Application Layer Protection:
App-ID Technology: Identifies and controls applications, regardless of port, protocol, or encryption.
Threat Prevention: Provides protection against application-level attacks like SQL injection and cross-site scripting (XSS) through advanced threat prevention capabilities.
Advantages Over Web Application Firewalls (WAFs)
1. Broader Threat Protection:
VM-Series Firewall: Protects against both network-level and application-level threats, providing comprehensive security for your entire AWS environment.
WAF: Primarily focused on application-level threats, such as HTTP-based attacks.
2. Granular Traffic Control:
VM-Series Firewall: Offers control over all traffic types, including non-HTTP/S traffic, and applies security policies based on a broader set of criteria.
WAF: Limited to inspecting and controlling HTTP/S traffic to and from web applications.
3. Network Segmentation and Control:
VM-Series Firewall: Facilitates network segmentation, allowing for detailed security policies per segment, and manages east-west traffic within your AWS environment.
WAF: Does not provide network segmentation or control over non-web traffic.
4. Integrated Security Features:
VM-Series Firewall: Includes features like URL filtering, SSL decryption, and threat intelligence for a multi-layered defense strategy.
WAF: Typically lacks integrated network security features.
Configuring VM-Series Firewalls in AWS
1. Deployment of VM-Series Firewall
Step 1: Launch the VM-Series Firewall
Choose the AMI: Access the AWS Marketplace and select the Palo Alto Networks VM-Series firewall AMI.
Configure Instance: Select an instance type that meets performance requirements (e.g.,
c5n.xlargeorm6i.large).Networking:
Assign the firewall to a VPC.
Allocate ENIs: one for management and others for data (ingress/egress).
Step 2: Setup Management Access
Security Group: Attach a security group that allows management access (e.g., SSH on port 22, HTTPS on port 443).
Elastic IP (Optional): Attach an Elastic IP to the management interface for easier remote access.
I will write a seperate blog with screenshots for AWS part later.
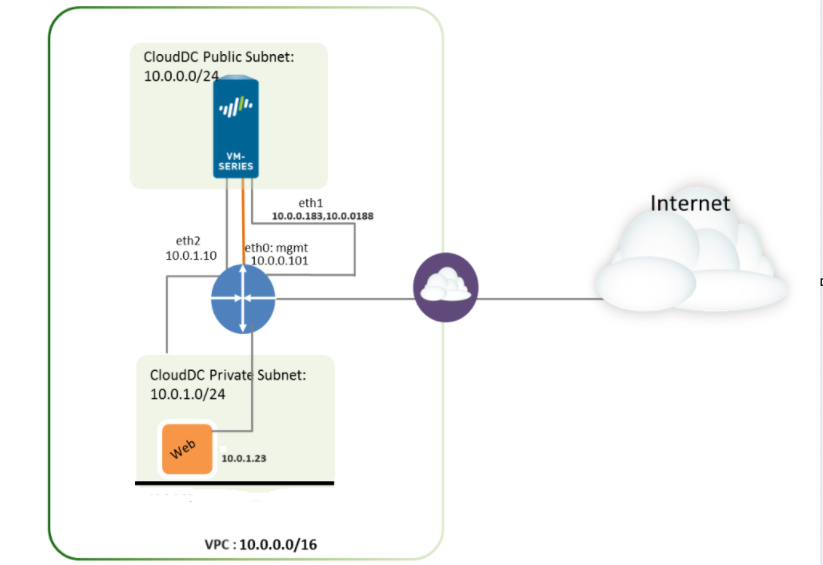
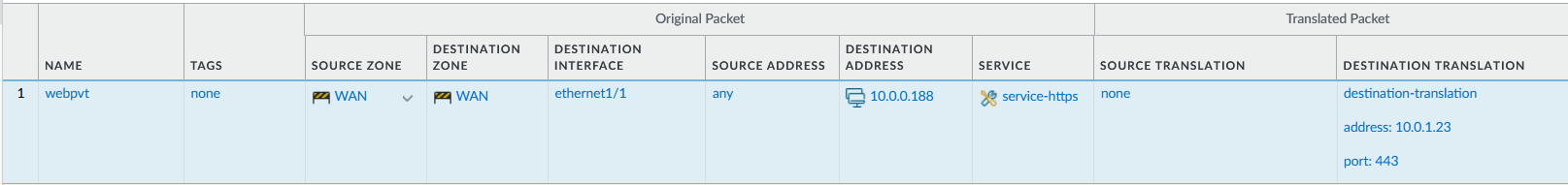
In the following example of a one-to-one destination NAT mapping, users from the zone named WAN access the server 10.0.1.23 in the zone named LAN using the IP address 10.0.0.188 of VM Firewall.
2. Configuring Security Protection
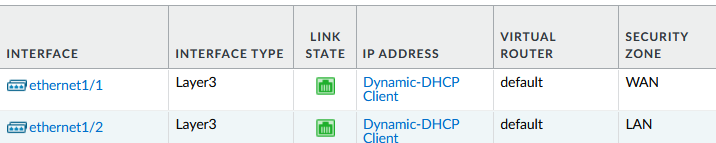
Step 1: Define Security Zones
Create Zones: Define security zones in the firewall management console (e.g., Untrust or WAN for external, Trust pr LAN for internal).
Assign Interfaces: Map the firewall’s ENIs to these zones.
Step 2: Configure Security Policies
Create Policies: Set up security policies for allowed and denied traffic.
Inbound Policy: Allow HTTP/HTTPS traffic from Untrust to Trust zones.
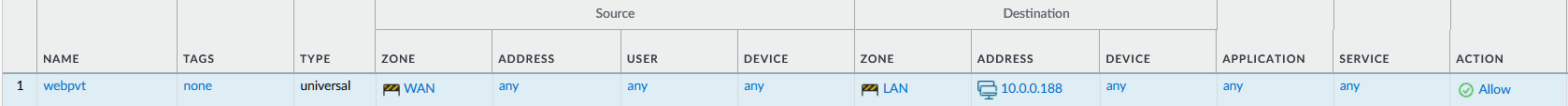
The above example for test purpose only, in prodcution you need to consider addtional parameters.
Outbound Policy: Allow essential outbound traffic from Trust to Untrust zones.
Enable Threat Prevention: Activate threat prevention features like antivirus, anti-spyware, and intrusion prevention on relevant policies.
Step 3: URL Filtering and SSL Decryption
URL Filtering: Set up URL filtering profiles to block malicious or unwanted websites.
SSL Decryption: Implement SSL decryption policies to inspect encrypted traffic.
3. Configuring NAT (Network Address Translation)
Step 1: Define NAT Rules
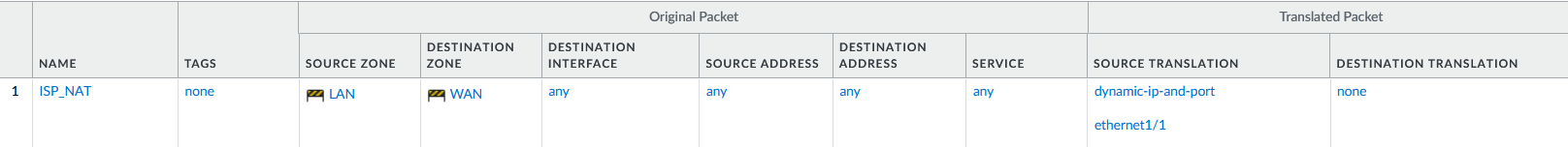
Source NAT:
Purpose: Translate private IPs to public IPs for outbound traffic.
Configuration: Create a NAT rule for translating internal source IPs to the firewall’s external IP address.
Destination NAT:
Purpose: Map external requests to internal private web servers.
Configuration: Create a NAT rule for translating incoming traffic to internal IP addresses.
Example:
Source NAT Rule: Internal clients to the internet.
Source Zone: Trust/LAN
Destination Zone: Untrust/WAN
Source IP: Internal subnet
Translated Address: Firewall's public IP
Destination NAT Rule: External clients to internal web server.
Source Zone: Untrust/WAN
Destination Zone: Trust/LAN
Destination IP: Firewall’s public IP
Translated Address: Internal web server IP
4. Configuring Route Tables for Traffic Routing
Step 1: Create Route Tables
Private Subnets: Configure the private subnet’s route table to route all traffic through the VM-series firewall.
Destination:
0.0.0.0/0Target: ENI of the VM-series firewall.
Public Subnets (if applicable): Ensure that the public subnet’s route table directs traffic to the Internet Gateway.
Step 2: Modify Route Tables
Associate Route Tables: Link the route tables with the appropriate subnets.
Configure Propagation: If using a VPN or Direct Connect, enable route propagation for dynamic updates.
Example Route Table Configuration:
Private Subnet Route Table:
Route:
0.0.0.0/0Target:
eni-xxxxxxxx(ENI of the VM-series firewall)
Public Subnet Route Table (if applicable):
Route:
0.0.0.0/0Target:
igw-xxxxxxxx(Internet Gateway)
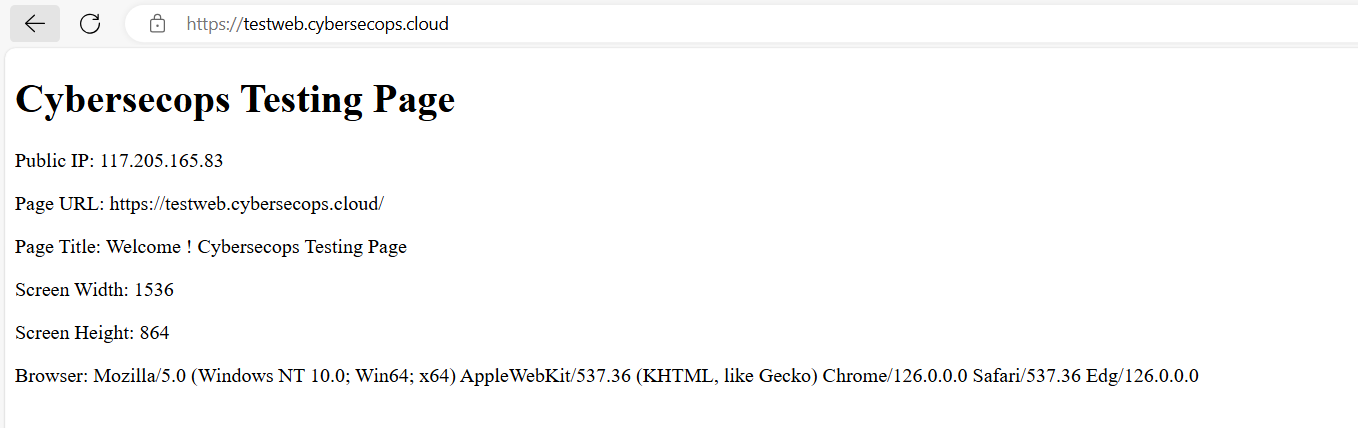
Once VM series firewall and AWS routing is complete ,users can browse the private server by accessing assgined Public IP/DNS for the WAN interface of the firewall.
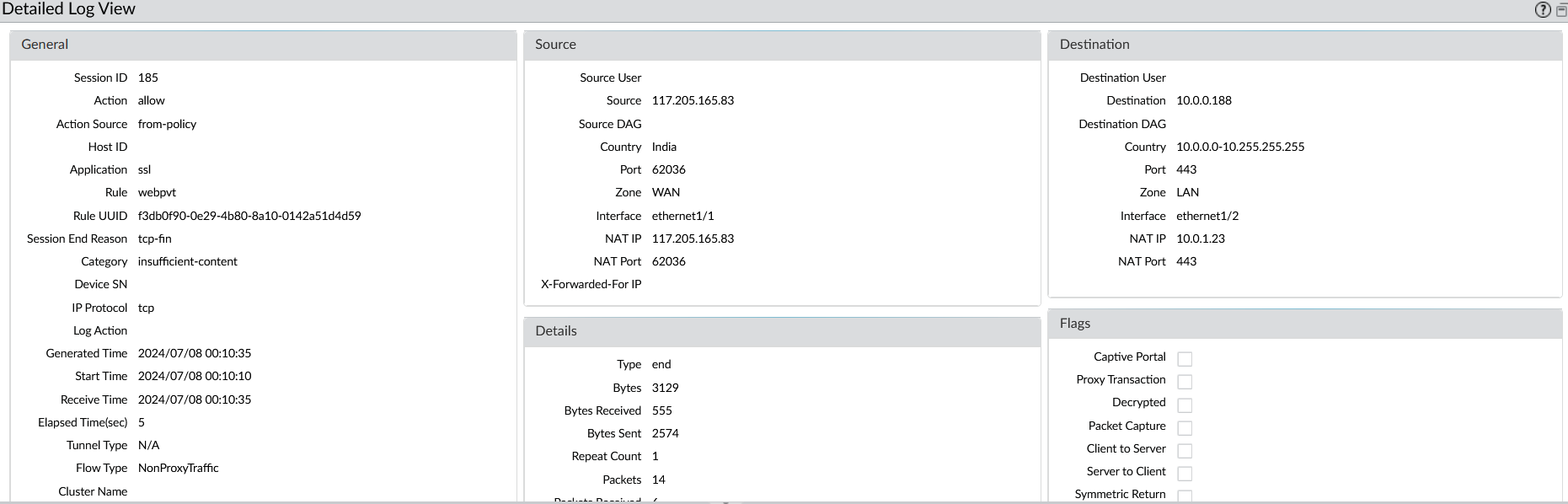
We can capture the traffic details in firewall monitor traffic section
Conclusion
Choosing VM-Series firewalls for your AWS environment ensures a holistic approach to security that covers both network and application layers. Their advanced threat detection, seamless AWS integration, scalability, and granular control make them an ideal solution for protecting your cloud infrastructure. By leveraging VM-Series firewalls, you can achieve robust and adaptable security for your AWS private web servers, safeguarding your assets against a diverse array of threats.
Subscribe to my newsletter
Read articles from Sourav Chakraborty directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
