Cryptographic terms and keywords
 Lakshya Chopra
Lakshya ChopraHere's a simple breakdown of all the commonly used cryptographic primitives and constructions:
Note: This article is mainly concerned with classical cryptography, PQC will soon get attention.
Hashing:
Hashing is a process of mapping data of any size to a fixed-length (or sometimes variable) output. The output, typically known as the digest or hash, is always deterministic (the same data will produce the same hash). Hash functions are one-way, meaning it is computationally infeasible to reverse the hash and retrieve the original data. Additionally, a good hash function has a negligible collision probability (different data producing the same output), uniformity across its output range, and should be fast and efficient to compute. Avalanche effect: A small change in the input results in significant changes in the output, which is also highly desirable. These qualities make a good hash function desirable for various tasks, for example:
Key derivation - PBKDF2, ANSI X9.63/62, HKDF. Can be used for symmetric, mac keys and Initialization Vectors.
Integrity checking for files, zips, downloaded data.
MACs
Signatures (done over hashed form of the message, and not the message itself).
Storage of passwords, passkeys, etc.
Avalanche effect:
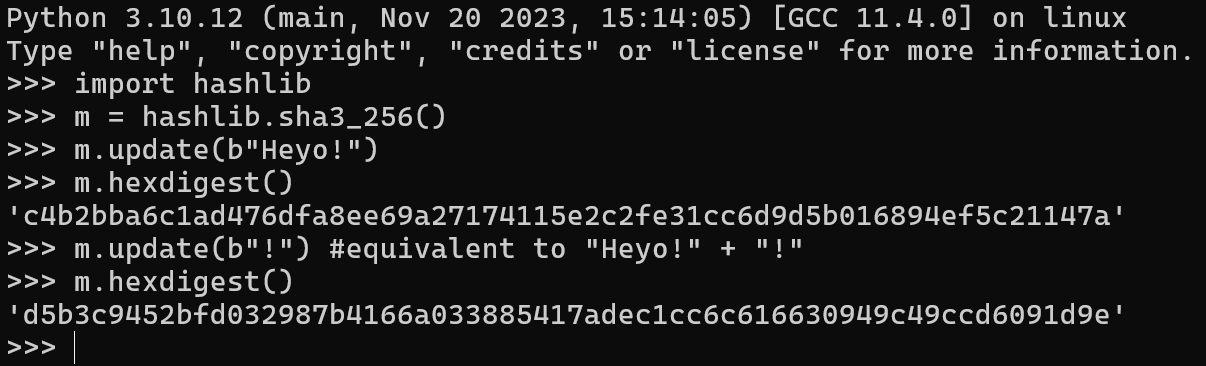
Typically used cryptographic primitives for Hashing:
SHA family:
SHA1
SHA2 (SHA2-256, SHA2-512)
SHA3 (subset of Keccak)
SHA3-256, SHA3-512
SHAKE256, SHAKE512 (two Extensible Output functions)
Keccak (for variable length hashes)
Symmetric Key Ciphers:
Ciphering is the process of encrypting plaintext data into a random-looking form, known as ciphertext, using an encryption key. This data can only be decrypted with a corresponding decryption key. Without this key, it should be computationally infeasible to decrypt the data. In symmetric key ciphers, the same key is used for both encryption and decryption. They are deterministic in nature and exist in the following types:
Block Ciphers - operating on fixed length blocks/groups of plaintext. For example: AES (128/256/512), modes - CTR, CBC, GCM. 3DES
AES256_GCM is the most widely used encryption and integrity mode in TLS.
Stream Cipher: In such algorithms, the plaintext data is encrypted bit by bit with the corresponding bit of the pseudorandom key stream to give one bit of the ciphertext. ChaCha20, Salsa20, SNOW-128 are some examples. ChaCha20-Poly1305 is equivalent to AES-GCM (ciphering with authentication), such algorithms are known as "authenticated encryption with associated data" (AEAD).
AES is often used on devices with dedicated hardware support for the algorithm. However, for devices with limited resources, ChaCha20 is usually faster. Therefore, in a TLS v1.3 connection, many user devices prefer ChaCha20 with Poly1305 for integrity, while servers with hardware acceleration prefer AES.
Message Authentication Codes (MACs):
Message Authentication Codes (MACs) are short tags added to the end of a message. They are used for authentication and integrity checking, ensuring that no one has tampered with the message and that it came from the correct sender. MACs use the same key to generate the tag, making them a form of symmetric cryptography. MACs are usually really fast and thus, may be preferred over DS.
Cryptographic Primitive Hash-Based - HMAC-SHA256/384, HMAC-SHA512
Based on Universal Hashing - UMAC, VMAC, Poly1305 (usually the fastest)
Block Ciphers Based - CMAC, GMAC
Checksums: typically used in error correction and detection codes, like Frame Check Sequences, IPv4 headers, etc.
Public Key Cryptography:
PKC is utilized to safely transfer a symmetric key (used for encrypting critical data), from one end to the other, by making use of asymmetric algorithms, or Key exchanges like Diffie Hellman (or ECDH). The main crux of PKC is that, we are using a publicly available key for encrypting some data, and only the corresponding private key can be used to decrypt it back (reason why it's asymmetric: keys for enc and dec are different).
Cryptographic protocols, primitives & constructions used:
* Diffie Hellman Key Exch. (KEX), following protocols are the extensions of this: ECDH, El Gamal, X3DH, PQXDHE.
* Elliptic Curve Crypt - based on the ECDLP problem, the PKC techniques utilizing this are:
* ECDH(E) - X25519 (Curve25519), CurveP256/384/521.
* ECDSA
* EdDSA - Ed448, Ed25519
ECC is a cryptographic primitive over which the above mentioned techniques/protocols are built upon.
* RSA:
* RSA PKCS#1-15 (from 1 to 15) : a set of standards, techniques that use the RSA crypt primitive.
* RSA PKCS#1.5 (incorporates RSA-OAEP)
* can be used for KEM, KEX, & DSA, RSA KEM
* KEM/DEM paradigm - Key Encaps. Mechanisms are the state of the are protocols today, which instead of directly encrypting the data, allow you to encrypt something else from which some other keys can be derived. KEMs are also the priority of NIST in its standardization of PQC crypt. primitives. They are particularly useful in RSA because they eliminate the need to pad the data to be encrypted. This allows for a value closer to the RSA modulus (2048 bits and greater) to be produced. RSA is most effective at encrypting data that is similar in size to its modulus.
* Encryption Schemes - ECIES, DHIES, DH Ratchet, Signal Protocol, RSA-KEM, PQXDHE
*
Elliptic Curve Integrated Encryption Scheme (ECIES), illustrated above.
RSA-OAEP is used for making the RSA Key Exchange IND-CPA & IND-CCA secure. Plain Old RSA has been deprecated.
Digital Signature Algorithms:
A Digital Signature is a scheme through which the authenticity of a digital message, file, certificate is verified. A valid signature gives the proof that the digital content did in fact come from the correct sender. They differ from MACs since they make use of asymmetric cryptography, wherein the keys for signing and verification are different.
They find their major applications in SSL/TLS (certificates and certverify messages), document signing and Blockchain.
Some major DSA's:
RSA 3072/4096
ECDSA (can be used with a variety of curves)
EdDSA - Ed25519, Ed448
(EdDSA is distinct from ECDSA, despite the fact that they both may use Curve25519).
There are also various Post-Quantum schemes, known for their large key sizes. These come in different forms, including lattice-based, hash-based, and code-based. For example:
MLDSA_44/65/87 (formerly known as Dilithium)
SPHINCS+
Falcon
Public Key Infra (PKI):
This is a combination of DSA and PKC, done to ensure that the asymmetric keys and cipher texts are from the authenticated user/server only. This is used to avoid MITM attacks. Here, an external trusted agency, known as the "Root CA," is utilized to prove the authenticity of the server/user. This is done using digital certificates signed using some DS algorithm. This practice is utilized in TLS/SSL. TLS is used to securely distribute symmetric keys between the client and the server, as well as provide proof that both the client and the server are authentic.
There are various cipher suites that TLS uses for key exchanges: RSA (now discarded in v1.3), ECHDE, PSK (pre-shared key, useful for local networks), and DHE.
For DSA, usually RSA is used, but EdDSA or ECDSA may be also be used.
For symmetric key, AES_128/256 may be used in any of the supported modes. ChaCha20 is also supported.
For hashing (or MAC), SHA256/SHA384 are commonly used.
The reason why RSA was discarded as KEX, is because of it's slowness in generation of keys, and lack of forward secrecy as compared to ECDHE, note ECDHE is distinct from ECDH (ECHDE = Ephemeral ECDH), DHE is another Perfect FS KEX (Ephemeral DH).
HTTPS = HTTP + TLS/SSL.
References
Subscribe to my newsletter
Read articles from Lakshya Chopra directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

