Active Directory Enumeration with Mastertul
 theblxckcicada
theblxckcicada
Before you continue with this blog post, I want to clarify that this content is for educational and ethical purposes only. Do not use these methods on a network you are not authorized to access.
Active Directory(AD) enumeration is like exploring a Windows network's phonebook (Active Directory) to find information on users, groups, computers, and more. This helps system admins improve security and ethical hackers find weaknesses. But remember, it's only okay to do this on a network you have permission to access!
To enumerate this information, you first need to run Impacket's lookupsid.py to list all users, groups, computers, and more. Then, filter out the usernames and store them in a user list file. Next, run impacket's GetNPUsers.py (this attack is called ASREPRoast) to target users with a weak security setting called "Do not require Kerberos preauthentication." This allows the script to potentially capture password information (AesRep hash) without needing the actual password. Alternatively, you can use GetUserSPNs.py to enumerate Service Principal Names (SPNs) associated with user accounts in an Active Directory environment. These two scripts are used to steal users' hashes. You can then run those hashes against Hashcat or John the Ripper to crack them.
When you have found valid credentials, you might want to understand the AD layout. In that case, you should run BloodHound to see which users, groups, and computers have specific permissions. All of this involves a lot of manual work, running one script after another. But what if you could automate this process?
The Cicada Mastertul gives you the flexibility to automate all these tasks and more, such as enumerating SMB shares and downloading their content, checking for WinRM connections, and performing LDAP enumeration. All you need to do is provide valid credentials and let the tool handle the rest, saving you time for other important tasks.
Although I won't cover every technique for using this script, I'll show the basic usage. Perhaps I'll write full documentation for it someday. For now, I'll showcase some examples based on what you want to enumerate. I have used a username (-u) and password (-p) for enumeration in these examples, but you can use an NTLM hash (-H) if you only have that. If you do not provide a flag, it will default to full mode (--full). If you provide a network, each enumeration will be in its respective IP address folder, and everything will be organized. You can find the usage manual by using
python3 cicada-mastertul.py -h
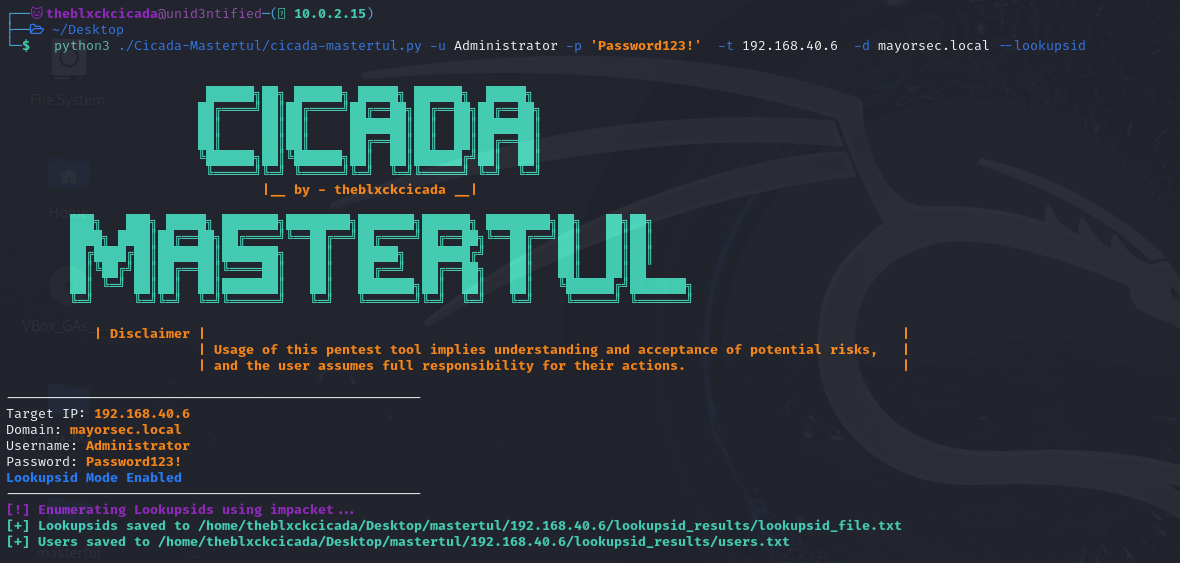
Lookupsid Enumeration
In this case I used a valid IP address instead of a network address to only enumerate a single host
python3 cicada-mastertul.py -u Administrator -p 'Password123!' -t 192.168.40.6 -d mayorsec.local --lookupsid
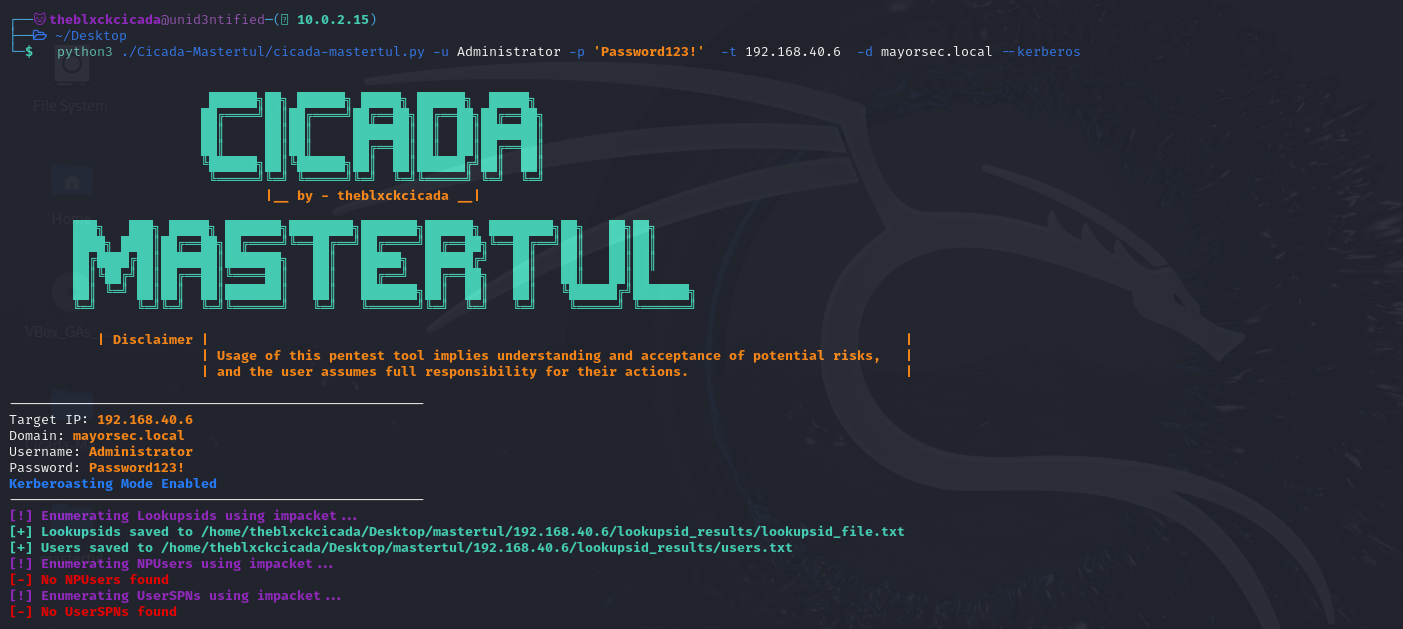
Kerberos Enumeration
Kerberos enumeration includes Impacket's GetNPUsers and GetUserSPNs. If you don't include the (--crack) flag, it will just grab the hashes and not run them against Hashcat. The --crack flag should be used with a wordlist (-w).
python3 cicada-mastertul.py -u Administrator -p 'Password123!' -t 192.168.40.6 -d mayorsec.local --kerberos
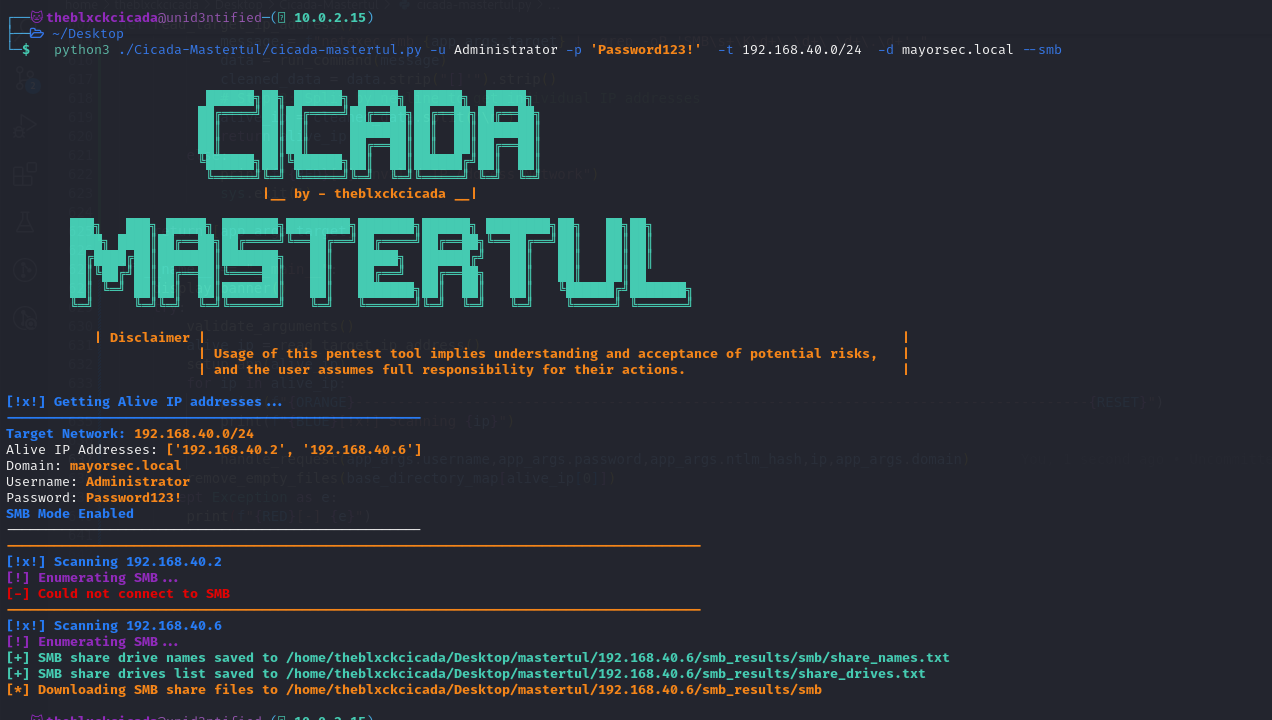
SMB Enumeration
With a network IP address, you can pass that in and let the tool find all IP addresses with smb enabled and enumerate them.
python3 cicada-mastertul.py -u Administrator -p 'Password123!' -t 192.168.40.0/24 -d mayorsec.local --smb
Full Enumeration
Full enumeration runs everything and might take longer depending on the IP addresses list of hosts.
python3 cicada-mastertul.py -u Administrator -p 'Password123!' -t 192.168.40.6 -d mayorsec.local --full
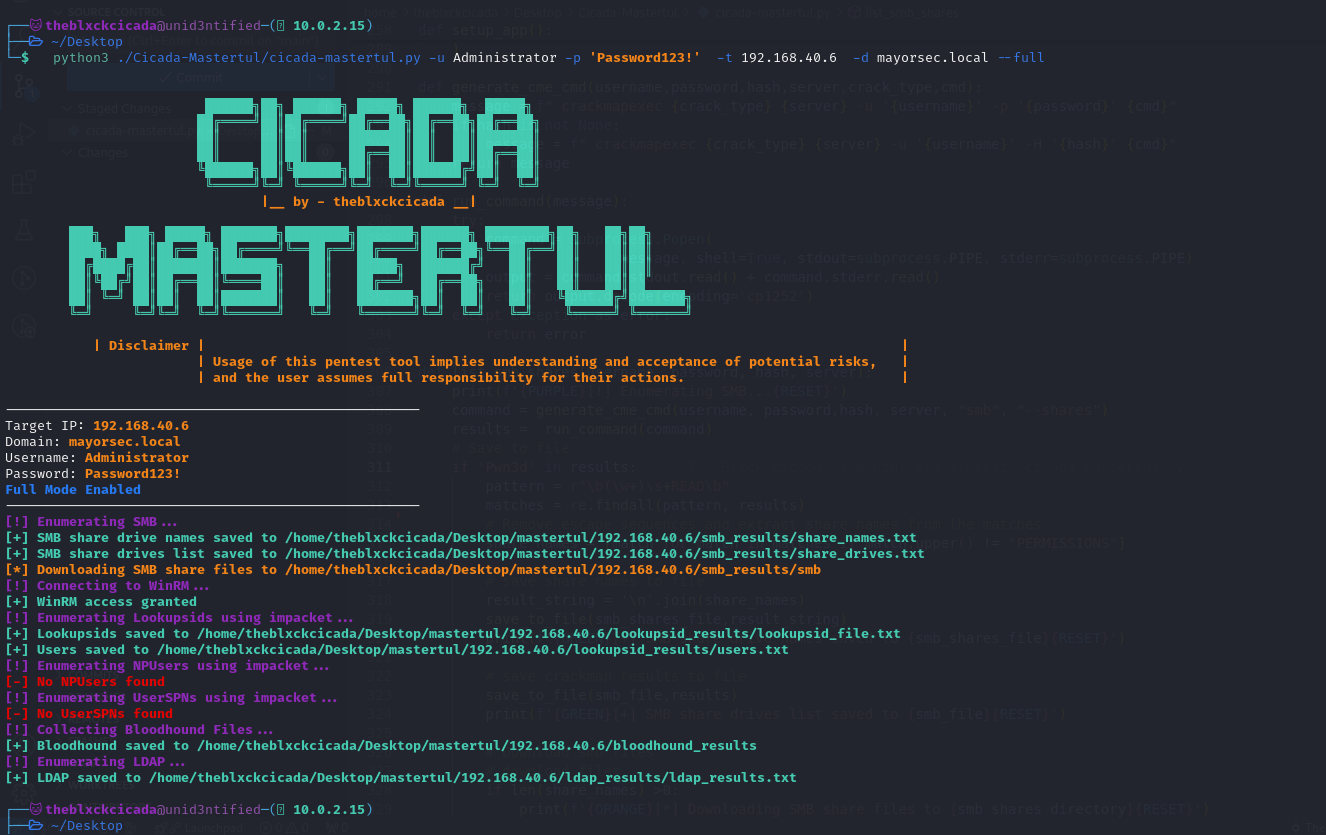
As I explained, these are just examples; you can experiment with the tool and try different things. I hope you enjoy it.
Subscribe to my newsletter
Read articles from theblxckcicada directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
