GPG Encryption/Decryption Quick Guide
 Mukesh Kumar
Mukesh Kumar
To list the existing GPG keys:
gpg --list-secret-keys --keyid-format=long
gpg --list-signatures
gpg -k --keyid-format long
To generate gpg keys(Will ask for pass phrase), these commands will generate the pair of keys i.e. public and private keys
with default values:
gpg --gen-key -> gpg --quick-generate-key 'User Name'To over-ride default values (Key Type and Key length):
gpg --full-generate-key
If you want generate gpg key pairs without passphrase, then do not enter any password when asked in above command while generating secret key.*
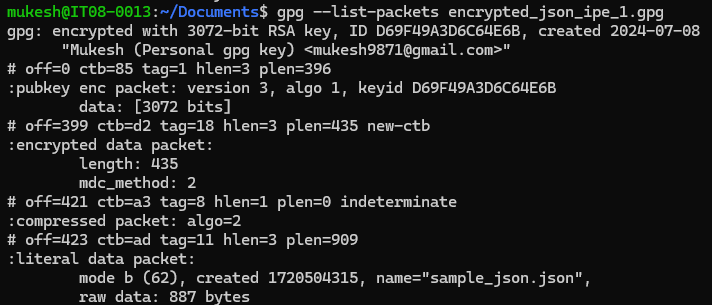
To see the public key using which a encrypted file was encrypted. It can also tell the filename, file size which was encrypted.
If it is password protected:
gpg --pinentry-mode cancel --list-packets your_file.gpg
If it is not password protected:
gpg --list-packets your_file.gpg
Sample output:
Exporting GPG Keys to ASCII format:
You can export your public key in an ASCII-armored format using the --armor and --export options. This format is suitable for email transmission:
gpg --output private.pgp --armor --export-secret-keymukesh.kumar@gmail.com
gpg --output public.pgp --armor --exportmukesh.kumar@gmail.com
Importing ASCII format GPG key:
gpg --import pubkey.asc
To encrypt a file:
Encrypt with default key
gpg -c file.txtTo encrypt a file using specific key:
gpg --yes --quiet -e -r 42076B20635F7B336400105A1E5D8A3E12277BFC -o ./encrypted_json ./sample_json.json
To de-crypt a file:
Decrypt default
gpg -d file.txt.gpgTo de-crypt a file using ascii key by passing the passphrase. Using password protected private key to decrypt. titan is the passphrase here:
gpg --import private.asc gpg --pinentry-mode=loopback --passphrase "titan" --decrypt -o ./decripted_with_asc_1.json ./encrypted_jsonTo de-crypt a file using ascii key. Using non-password protected private key to decrypt:
gpg --import private.asc gpg --decrypt -o ./decripted_with_asc_1.json ./encrypted_json
How to check if a GPG ASC key file is passphrase protected or not:
Analyse the key with command:
gpg --list-packets --verbose private-exported.asc
If it is password protected then it will contain, information like below-
# off=0 ctb=95 tag=5 hlen=3 plen=1413
:secret key packet:
version 4, algo 1, created 1721214374, expires 0
pkey[0]: [3072 bits]
pkey[1]: [17 bits]
iter+salt S2K, algo: 7, SHA1 protection, hash: 2, salt: C86E62022573C26D
protect count: 65011712 (255)
protect IV: 7d b2 86 a1 1e 77 c8 a7 12 8a 36 d2 73 75 a1 70
skey[2]: [v4 protected]
keyid: 3F69AC86232DA776
# off=1416 ctb=b4 tag=13 hlen=2 plen=39
It will contain contain protection.
Whereas if it is non passphrase protected then it will display information like this:
# off=0 ctb=95 tag=5 hlen=3 plen=1368
:secret key packet:
version 4, algo 1, created 1721215136, expires 0
pkey[0]: [3072 bits]
pkey[1]: [17 bits]
skey[2]: [3067 bits]
skey[3]: [1536 bits]
skey[4]: [1536 bits]
skey[5]: [1535 bits]
checksum: dcf8
keyid: 50634AF2DF6522A3
# off=1371 ctb=b4 tag=13 hlen=2 plen=40
Possible error in GPG encryption/decryption:
1. Error: decryption failed: No secret key Reason_1: private key needed for decryption is not available in your keyring. Either key is not imported for it is corrupted. Solution: Import the respective private key.
Reason_2: The secret key is not stored in the default location that GPG expects. Solution: Either move secret key to the default location or specify the location of the secret key when you decrypt the message.
Reason_3: The secret key is encrypted and you do not have the password to decrypt it. Solution: If the secret key is encrypted, you will need to decrypt it using the password. Unlock your private keys only when you need to use them.
"gpg –decrypt –passphrase "
2. Error: Invalid Option Reason: The invalid option or command used for gpg. Solution: Verify and correct the command.
Best Practices for Using the GPG Command:
1. Always backup your keys: Losing your keys, especially your private key, can result in permanent data loss. Regularly backup your ~/.gnupg directory to avoid such scenarios.
2. Use strong passphrases: A strong passphrase can significantly enhance the security of your encrypted data. Consider using a passphrase manager to generate and store strong passphrases.
3. Regularly update GPG: Keeping GPG updated ensures that you have the latest security patches and features.
4. Unlock your private keys only when you need to use them.
List of important GPG commands:
GPG Cheat Sheet
| Flag | Description | Example |
| -c | Encrypts a file with a symmetric cipher. | gpg -c file.txt |
| -d | Decrypts data. | gpg -d file.txt.gpg |
| --gen-key | Generates a new key pair. | gpg --gen-key |
| --import | Imports keys. | gpg --import pubkey.asc |
| --export | Exports keys. | gpg --export -a 'User Name' > public.key |
| --list-keys | Lists the public keys in your keyring. | gpg --list-keys |
| --list-secret-keys | Lists the private keys in your keyring. | gpg --list-secret-keys |
| --delete-key | Deletes a public key. | gpg --delete-key 'User Name' |
| --delete-secret-key | Deletes a private key. | gpg --delete-secret-key 'User Name' |
| --sign | Creates a digital signature. | gpg --sign file.txt |
| --verify | Verifies a digital signature. | gpg --verify sigfile |
| --armor | Creates ASCII armored output. | gpg --armor --export 'User Name' |
| -r | Encrypts for the given user. | gpg -r 'User Name' -e file.txt |
Subscribe to my newsletter
Read articles from Mukesh Kumar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Mukesh Kumar
Mukesh Kumar
I am a Software Development lead in a product based company.