Understanding Virtual Private Network (VPN) and AWS Direct Connect in AWS
 Jasai Hansda
Jasai Hansda
In today's digital age, secure connections are crucial for businesses using cloud services. Amazon Web Services (AWS) offers two main solutions: Virtual Private Network (VPN) and AWS Direct Connect. This article explains their functions, use cases, and benefits.
Virtual Private Network (VPN)
What is a VPN?
A Virtual Private Network (VPN) is a technology that creates a secure and encrypted connection over a less secure network, such as the internet. In the context of AWS, a VPN allows you to securely connect your on-premises (refers to IT infrastructure and software applications that are hosted and maintained by an organization within their own facilities) network or client devices to your AWS Virtual Private Cloud (VPC).
Types Of AWS VPN
1 . Site-to-Site VPN
This type of VPN connection enables you to securely connect your on-premisesnetwork or branch office to your AWS VPC. It uses IPsec (Internet Protocol Security) to establish encrypted tunnels over the internet.
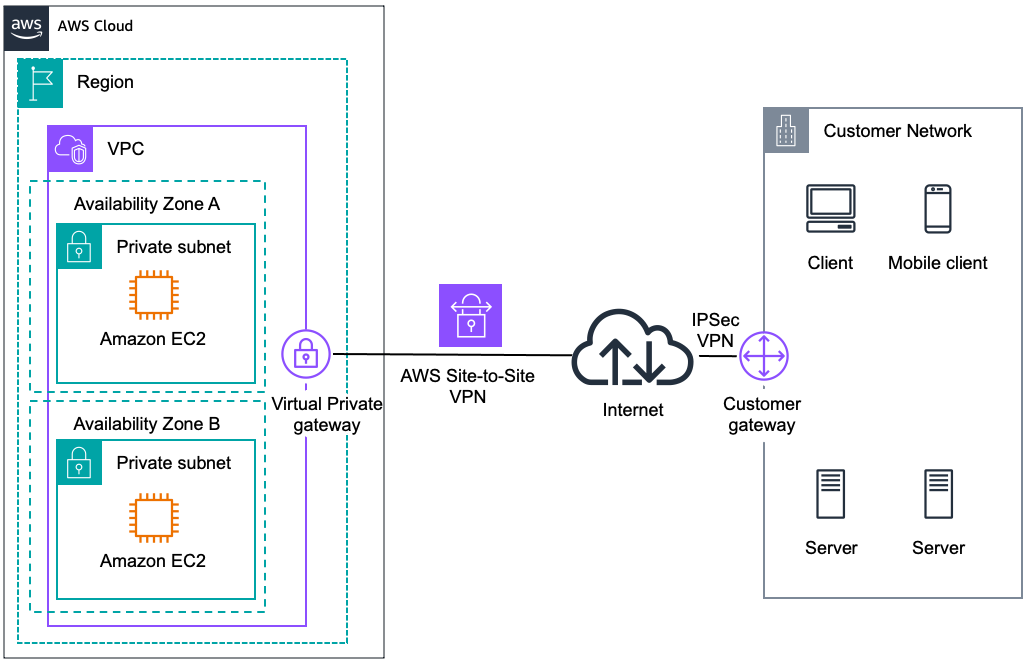
This diagram provides a more detailed view of an AWS Site-to-Site VPN connection, illustrating how a customer’s on-premises network connects securely to an Amazon Virtual Private Cloud (VPC).
Key Components and Their Roles:
AWS Cloud:
- Represents the AWS infrastructure.
Region:
- The geographic area where the VPC and its resources are located.
VPC(Virtual Private Cloud):
A logically isolated section of the AWS cloud where AWS resources can be launched in a virtual network.
This VPC contains two Availability Zones (A and B), each with a PrivateSubnet and Amazon EC2 instances.
Private Subnets:
- Subnets within the VPC that do not have direct access to the internet, providing an additional layer of security for the EC2 instances.
Amazon EC2 Instances:
- Virtual servers hosted within the private subnets.
Virtual Private Gateway:
The VPN concentrator on the AWS side of the Site-to-Site VPN connection.
It terminates the VPN connection to the customer gateway.
AWS Site-to-Site VPN:
- This is the secure tunnel established over the internet between the AWS VPC and the customer’s on-premises network.
Internet:
- The VPN tunnel travels through the internet, encrypted using IPsec, ensuring secure communication between the two networks.
Customer Gateway:
The VPN concentrator on the customer’s side.
It could be a physical device or a software application that connects to the virtual private gateway on the AWS side.
IPsec VPN:
- The security protocol used to create the encrypted tunnel between the customer gateway and the virtual private gateway.
Customer Network:
Represents the customer’s on-premises network.
Includes various client devices (desktops, mobile devices) and servers.
How It Works:
Customer Network:
- Users and servers within the customer’s network communicate securely with resources in the AWS VPC.
Customer Gateway:
- This gateway establishes a secure IPsec VPNconnection over the internet to the virtual private gateway.
Internet:
- The VPN connection travels securely through the internet.
Virtual Private Gateway:
- On the AWS side, this gateway terminates the VPN connection and allows traffic to flow securely into the VPC.
AWS VPC:
- Once inside the VPC, the traffic can reach the EC2 instances within the private subnets in both availability zones.
2 . Client VPN
This setup allows individual client devices to securely access resources within the AWS network from any location. It is particularly useful for remote workers who need access to AWS resources.
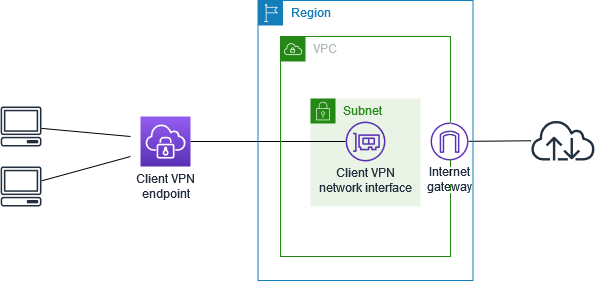
This diagram illustrates a Client VPN connection setup, showing how individual client devices securely connect to an Amazon Virtual Private Cloud (VPC) via a Client VPN endpoint.
Key Components and Their Roles:
Client Devices:
- Represent individual client devices, such as laptops or desktops, that need to connect to the AWS VPC.
Client VPN Endpoint:
The endpoint where the client devices initiate their VPN connections.
It is managed by AWS and serves as the entry pointinto theAWS network.
AWS Cloud:
- Represents the AWS infrastructure where the VPC resides.
Region:
- The specific geographic area where the VPC and its resources are located.
VPC(Virtual Private Cloud):
A logically isolated section of the AWS cloud where AWS resources can be launched in a virtual network.
Contains subnets, network interfaces, and an internet gateway.
-
A segment within the VPC where AWS resources are placed.
In this case, it includes the Client VPN network interface.
Client VPN Network Interface:
- The network interface within the VPC that receives trafficfrom the client VPN endpoint and routes it to the appropriate resources in the VPC.
Internet Gateway:
A gateway that provides a route for traffic between the VPC and the internet.
Allows the VPC to communicate with the internet, enabling the Client VPN endpoint to be reachable from the internet.
How It Works:
Client Devices:
Individual client devices connect to the AWS VPC by establishing a VPN connection to the Client VPN endpoint.
The connection is secure, encrypted, and initiated by the client devices.
Client VPN Endpoint:
This endpoint is the interface where the VPN connections from the client devices terminate.
Managed by AWS, it provides secure access to the VPC.
AWS Cloud (VPC):
- Once the VPN connection is established, traffic from the client devices is routed through the Client VPN network interface within the VPC.
Subnet and Client VPN Network Interface:
- The subnet contains the Client VPN network interface, which handles the traffic from the VPN endpoint and directs it to the appropriate resources within the VPC.
Internet Gateway:
- This gateway facilitates communication between the VPC and the internet, allowing the Client VPN endpoint to be accessible from anywhere.
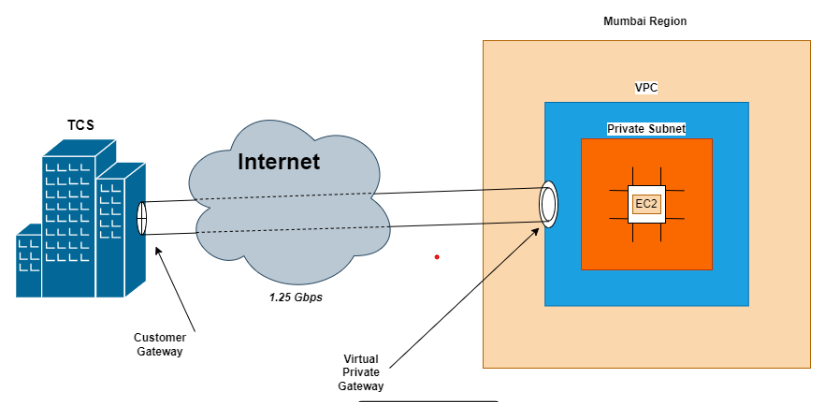
Simplified presentation of site-to-site VPN connection
Limitations of AWS VPN
AWS VPN, both Site-to-Site and Client VPN, offers a robust and secure means to connect on-premises networks or individual devices to AWS resources. However, it comes with certain limitations that users should be aware of:
Performance and Latency:
Bandwidth Limitations: AWS Site-to-Site VPN connections are capped at1.25 Gbps, which may not be enough for high-throughput applications.
Latency: VPN connections over the internet can add latency, affecting performance for latency-sensitive applications.
Complexity in Configuration and Management:
- Setting up and maintaining VPN connections requires a good understanding of networking and security, which can be complex and error-prone.
Single Points of Failure:
- AWS provides high availability with multiple VPN tunnels, but the on-premises equipment (Customer Gateway) can still be a single point of failure if not set up with redundancy.
Cost:
- VPN usage incurs costs, including data transfer fees and charges for VPN connections, which can add up for large-scale or high-traffic deployments.
Scalability:
- Scaling VPN connections can be challenging and may require additional infrastructure and configuration.
Benefits of AWS VPN
Cost-Effective: VPNs are generally more affordable compared to dedicated connections.
Quick Setup: VPN connections can be established quickly, making them ideal for immediate needs.
Flexibility: VPNs can be used to connect multiple locations and devices to AWS.
Use Cases for AWS VPN
Remote Access: Providing secure access to AWS resources for remote employees.
Backup and Disaster Recovery: Establishing secure connections for backup and recovery operations.
Hybrid Cloud Architectures: Integrating on-premises infrastructure with AWS for hybrid cloud deployments.
AWS Direct Connect
What is AWS Direct Connect?
AWS Direct Connect is a cloud service solution that makes it easy to establish a dedicated network connection from your premises to AWS. The connection is established using a direct fiber optic line, bypassing the internet, providing higher bandwidth, lower latency, and more reliable connectivity compared to standard VPN connections which uses public internet.
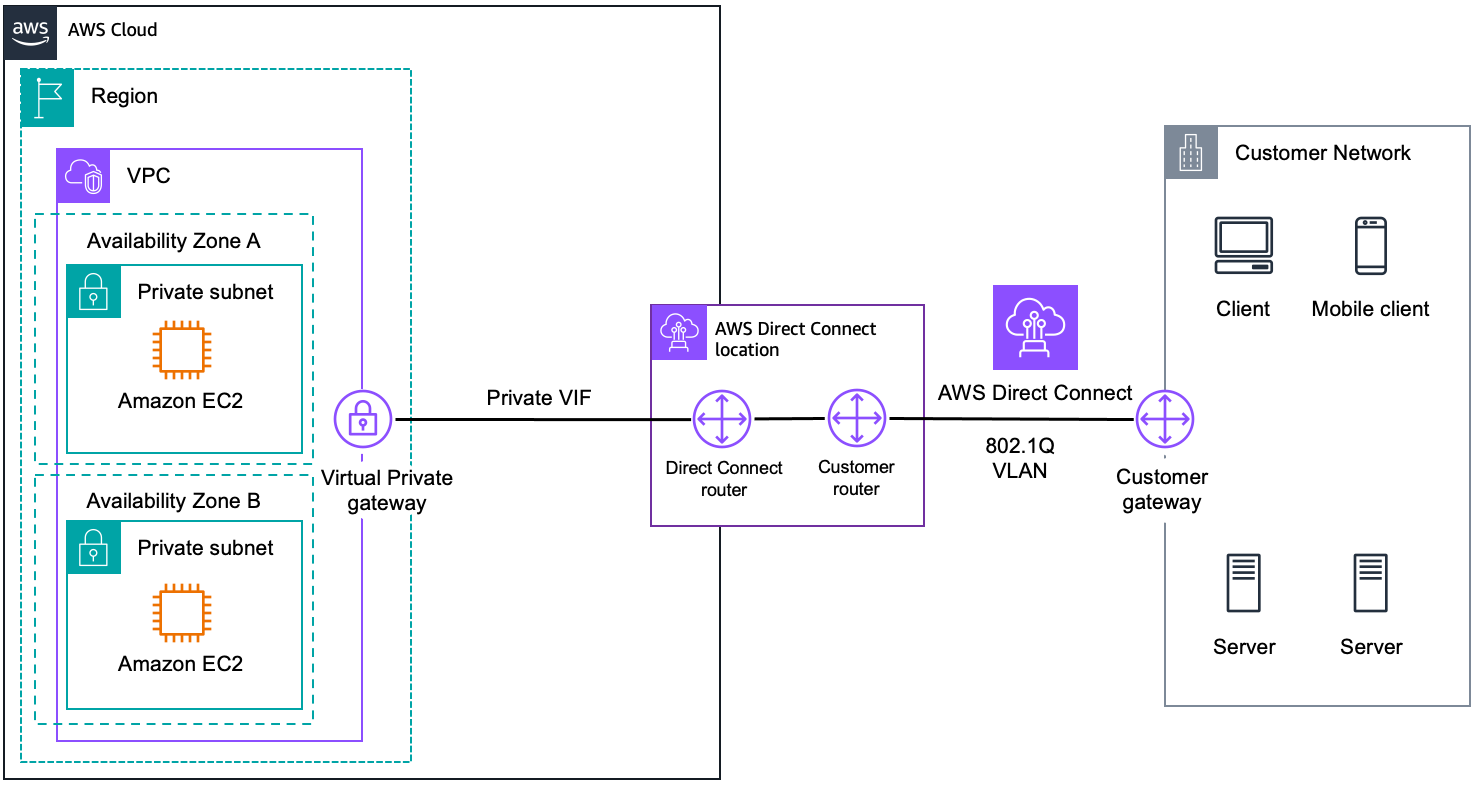
This diagram illustrates an AWS Direct Connect setup, showing how a customer's on-premises network connects directly to an Amazon Virtual Private Cloud (VPC) via AWS Direct Connect.
Key Components and Their Roles:
Customer Network:
Client and Mobile Client: End-user devices that access resources.
Servers: On-premises servers that need to connect to AWS resources.
Customer Gateway:
- The on-premises router or device that connects to the Direct Connect location.
AWS Direct Connect:
Direct Connect Location: A physical location where AWS Direct Connect is available.
Direct Connect Router: AWS router located at the Direct Connect location.
Customer Router: The on-premises router at the customer’s location that connects to the Direct Connect router.
802.1Q VLAN: A virtual local area network (VLAN) tag used for segregating traffic.
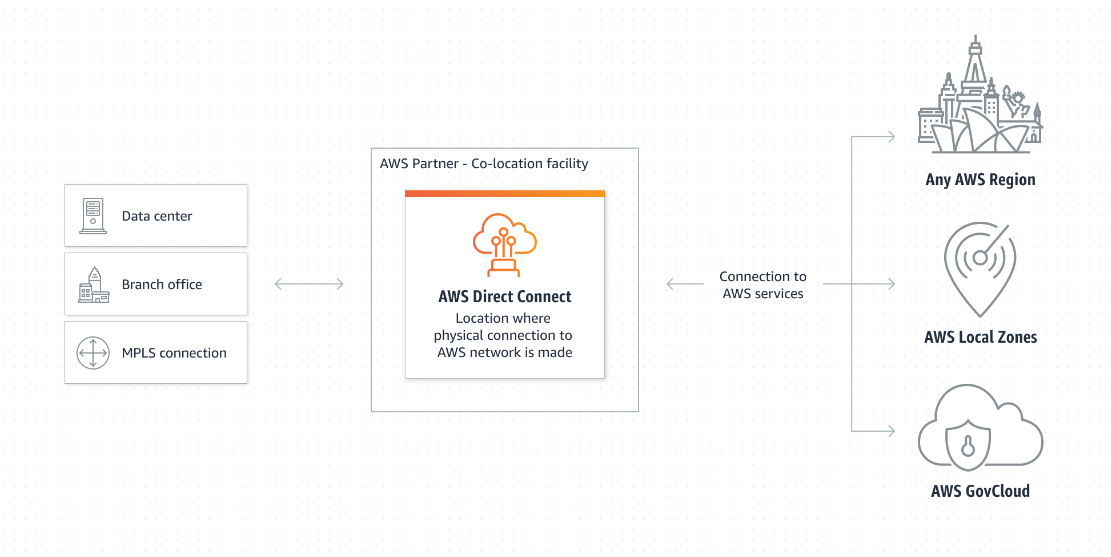
Connect to AWS via AWS Direct Connect
AWS Cloud:
Region: The specific geographic area where the VPC and its resources are located.
VPC (Virtual Private Cloud): A logically isolated section of the AWS cloud where AWS resources are launched.
Private Subnets: Subnets within the VPC that do not have direct access to the internet, providing an additional layer of security for the EC2 instances.
Amazon EC2 Instances: Virtual servers hosted within the private subnets.
Virtual Private Gateway: The VPN concentrator on the AWS side of the Direct Connect connection.
Private VIF (Virtual Interface): A virtual interface that facilitates the connection between the VPC and the Direct Connect location.
How It Works:
Customer Network:
- Users (clients and mobile clients) and servers within the customer's network communicate securely with resources in the AWS VPC.
Customer Gateway:
- This gateway connects to the Direct Connect location via the customer router.
AWS Direct Connect:
The customer router establishes a direct connection to the AWS Direct Connect router at the Direct Connect location.
The connection uses 802.1Q VLAN tagging for segregating traffic.
AWS Cloud (VPC):
Traffic from the Direct Connect location is routed through the Private VIF to the Virtual Private Gateway.
Within the AWS Cloud, the Virtual Private Gateway directs the traffic into the appropriate VPC.
The VPC contains private subnets in multiple Availability Zones (A and B) where the Amazon EC2 instances are hosted.
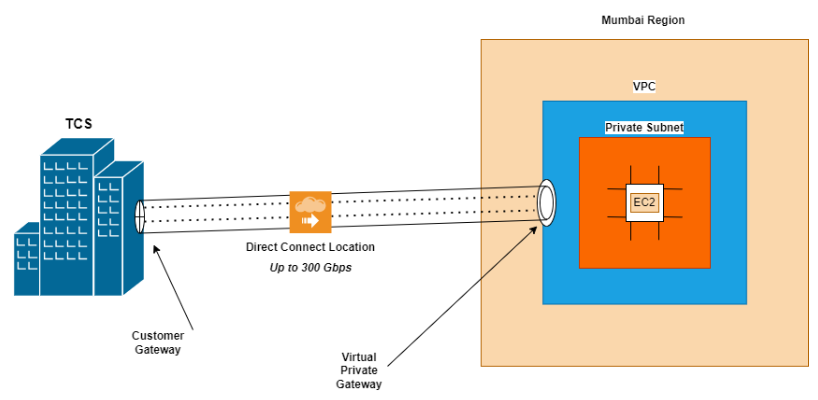
Simplified presentation of AWS Direct Connect
Limitations of AWS Direct Connect
Initial Setup Complexity:
- Requires physical infrastructure setup and high technical expertise.
Geographic Limitations:
- Available only in specific locations; distance from Direct Connect locations can add cost and complexity.
Cost:
- High initial setup costs and ongoing charges for port hours and data transfer.
Scalability:
- Limited by port bandwidth (1 Gbps or 10 Gbps); scaling requires additional ports and infrastructure.
Single Points of Failure:
- Redundancy is crucial to avoid outages. Physical infrastructure is vulnerable to disruptions like cable cuts.
Limited Flexibility:
- Fixed capacity; scaling up or down requires physical changes and can be time-consuming.
Complex Network Management:
- Requires ongoing management for configuration, monitoring, and troubleshooting.
Security Considerations:
- Direct Connect does not encrypt traffic; additional measures are needed for encryption.
AWS Direct Connect offers high performance and reliability but involves significant setup complexity, higher costs, geographic and scalability limitations, potential single points of failure, limited flexibility, and complex network management. Careful planning is essential to ensure it meets organizational needs.
Benefits of AWS Direct Connect
High Performance: Provides consistent, low-latency performance for data transfer. Up to 300 Gbps.
Increased Security: Reduces exposure to the public internet, enhancing security.
Cost Savings: Reduces bandwidth costs by transferring data directly to and from AWS.
Use Cases for AWS Direct Connect
Data-Intensive Applications: Ideal for applications that require high throughput and low latency.
Enterprise Migrations: Facilitates large-scale migrations to AWS.
Hybrid Environments: Supports hybrid cloud architectures with consistent network performance.
AWS VPN vs. AWS Direct Connect
| Feature | AWS VPN | AWS Direct Connect |
| Connectivity Type | Uses public internet with secure IPsec VPN | Dedicated private network connection |
| Performance | Variable; higher latency and potential packet loss | Consistent, low-latency, high-bandwidth, reliable |
| Cost | Lower initial setup; VPN gateway and data transfer fees | Higher initial setup costs; ongoing port and data fees |
| Security | Encrypted over public internet (IPsec) | Not encrypted by default; requires additional measures |
| Scalability | Easier to scale; limited by VPN gateway capabilities | Scaling requires additional ports; limited by port capacity |
| Setup Complexity | Easier and quicker to set up | More complex; involves physical infrastructure setup |
| Availability | Globally available with internet access | Limited to specific AWS Direct Connect locations |
| Use Cases | Smaller businesses, less critical apps, temporary connections | Large-scale data transfers, critical apps, high performance |
Summary
AWS VPN: Cost-effective, quick to set up, suitable for less critical applications.
AWS Direct Connect: Superior performance, reliable, suitable for critical applications, higher cost and complexity.
Conclusion
Both AWS VPN and AWS Direct Connect offer robust solutions for connecting your on-premises environments to AWS. The choice between the two depends on your specific needs, including performance requirements, security considerations, and budget constraints. By understanding the features and benefits of each, you can make an informed decision that aligns with your business objectives.
Subscribe to my newsletter
Read articles from Jasai Hansda directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jasai Hansda
Jasai Hansda
Software Engineer (2 years) | In-transition to DevOps. Passionate about building and deploying software efficiently. Eager to leverage my development background in the DevOps and cloud computing world. Open to new opportunities!