I escalated my app to the cloud !
 Nikhil Mishra
Nikhil Mishra
Context :
I deployed a web app locally, and now I want to move it to the cloud for scalability, reliability, ease of management, and automation.
Here, I am using IaaS.
Major Services used will be :
ELB for Nginx
EC2 instead of local vms
Route 53 for DNS
S3 for artifact storage
Auto Scaling Group
IAM
ACM
The Architecture changes :
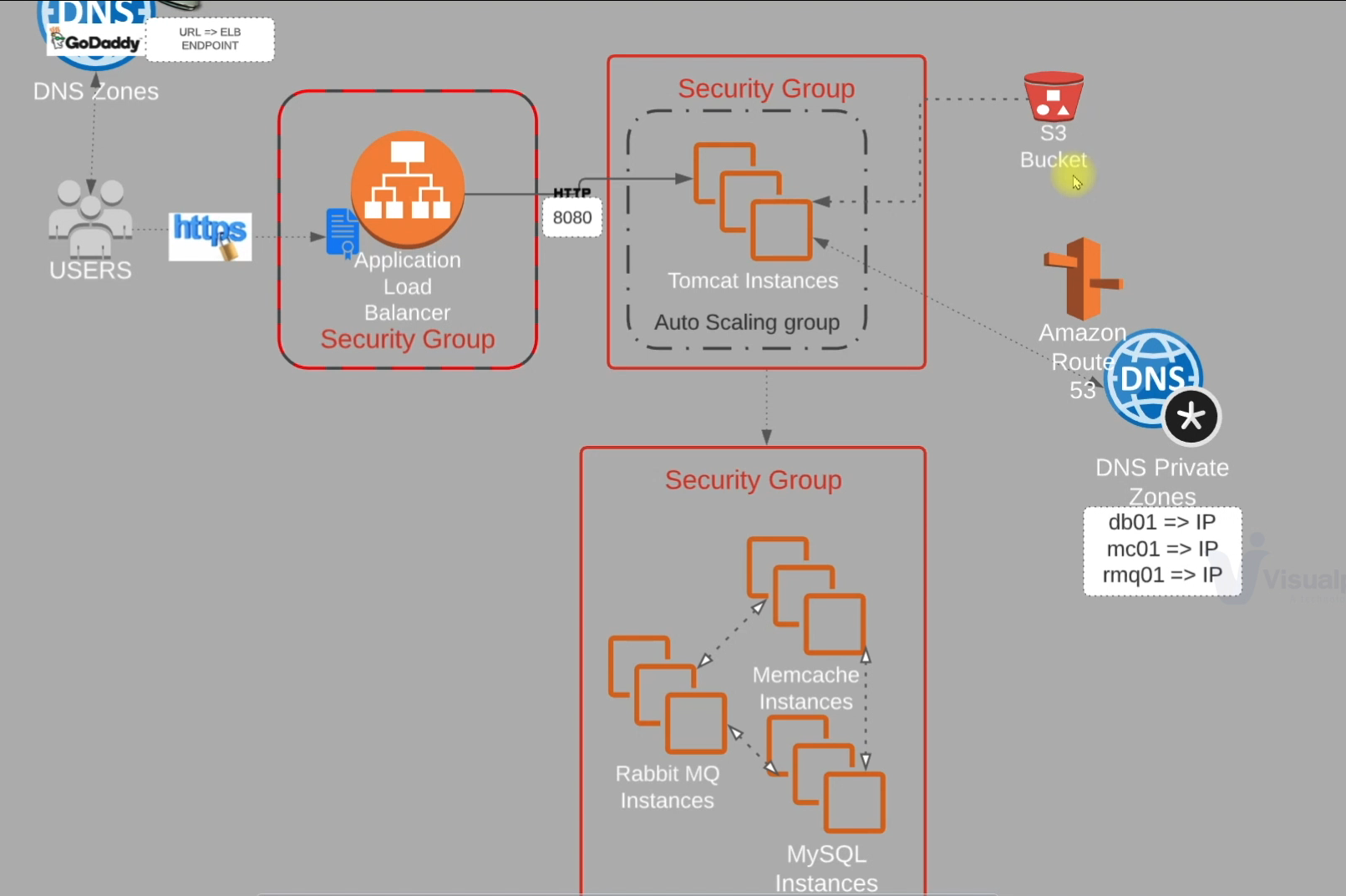
The user will log in through an endpoint hosted on GoDaddy.
They will access the endpoint via HTTPS, with the certificate managed by ACM.
The user will connect to the ELB endpoint, which only permits HTTPS traffic.
The ELB will then route the user to the application server.
The application server consists of Tomcat instances, managed by an autoscaling group that adjusts based on traffic and only allows traffic on port 8080.
The application server requires access to backend servers, managed by a Route 53 private hosted zone.
These backend servers, which include MySQL, RabbitMQ, and Memcache, are in a separate security group and will only allow traffic on their specific ports.
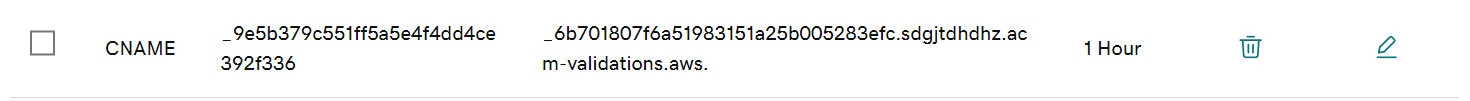
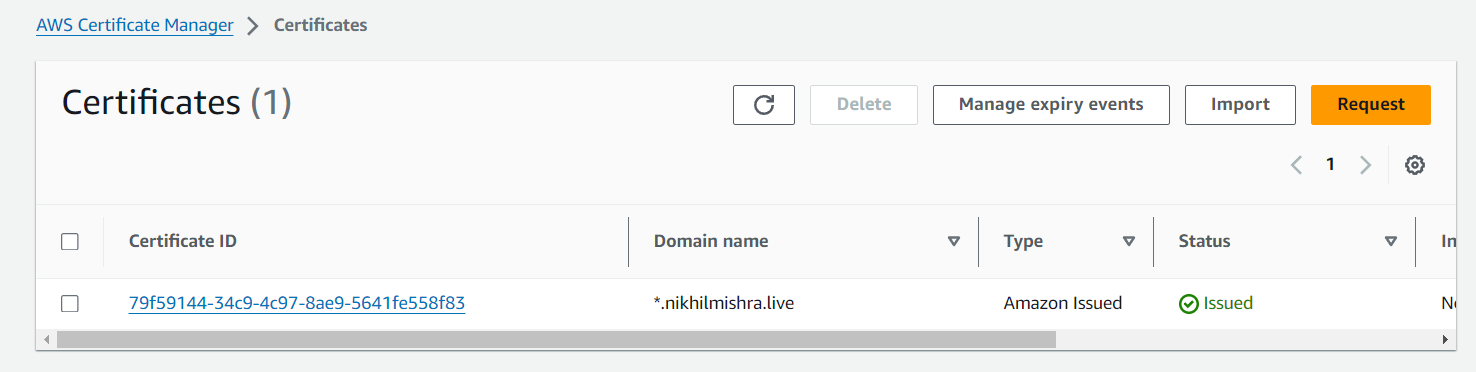
I have a certificate ready in ACM issued by GoDaddy, which I obtained by requesting and adding a CNAME record.
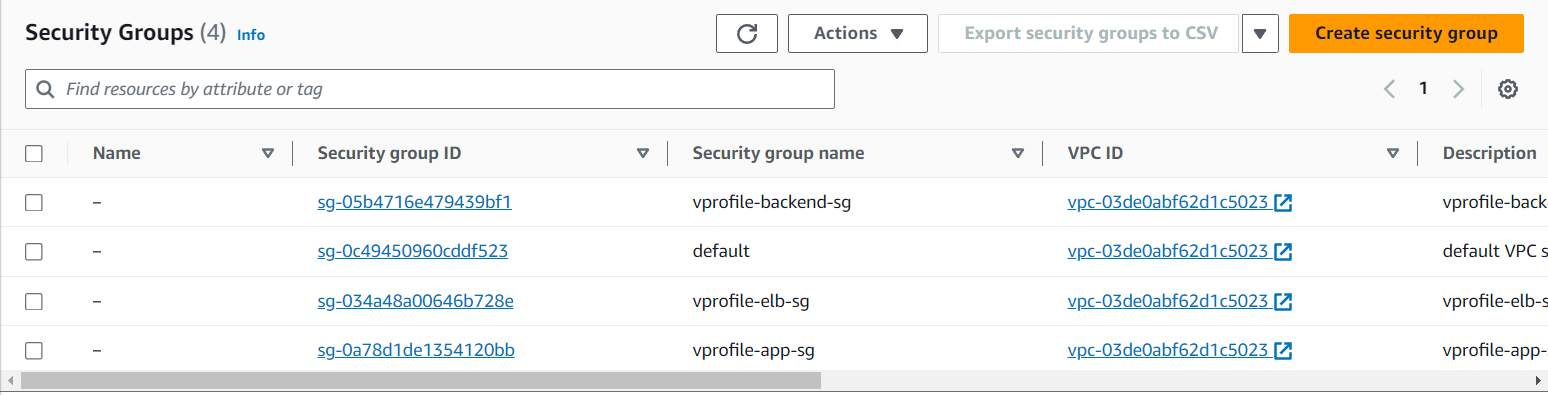
Now I made 3 security groups:
For the load balancer, allowing HTTP and HTTPS traffic.
For the app server, allowing port 8080 from the load balancer's security group. Also added SSH and port 8080 access from my IP.
For the backend, allowing port 3306 for MySQL, 11211 for Memcached, and 5672 for RabbitMQ from the app server's security group. Also allowed all traffic within the group and SSH for validation.
I also have my key ready :
Cloned the repo and got the scripts for launching instances
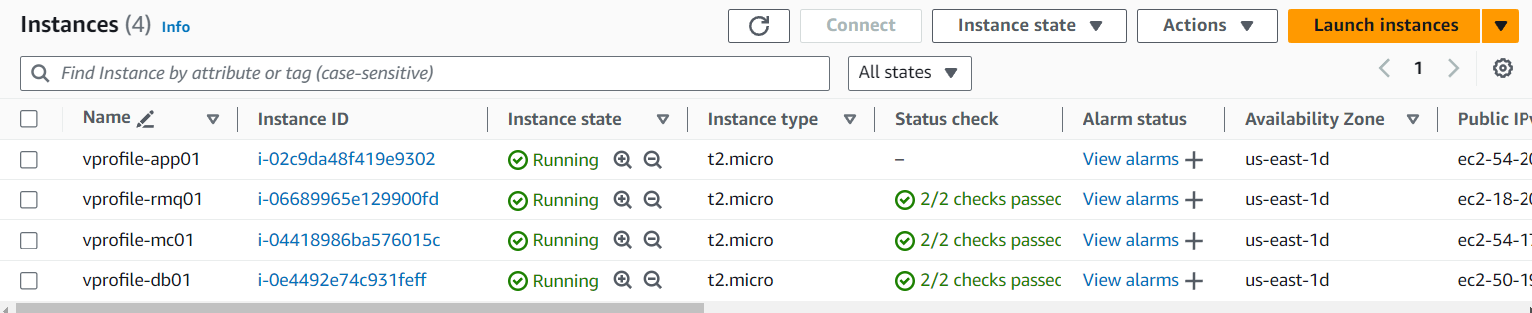
Instances :
Launched DB, memcache, and RabbitMQ with Amazon Linux.
Launched the app server with Ubuntu.
Validated that all services and scripts are working
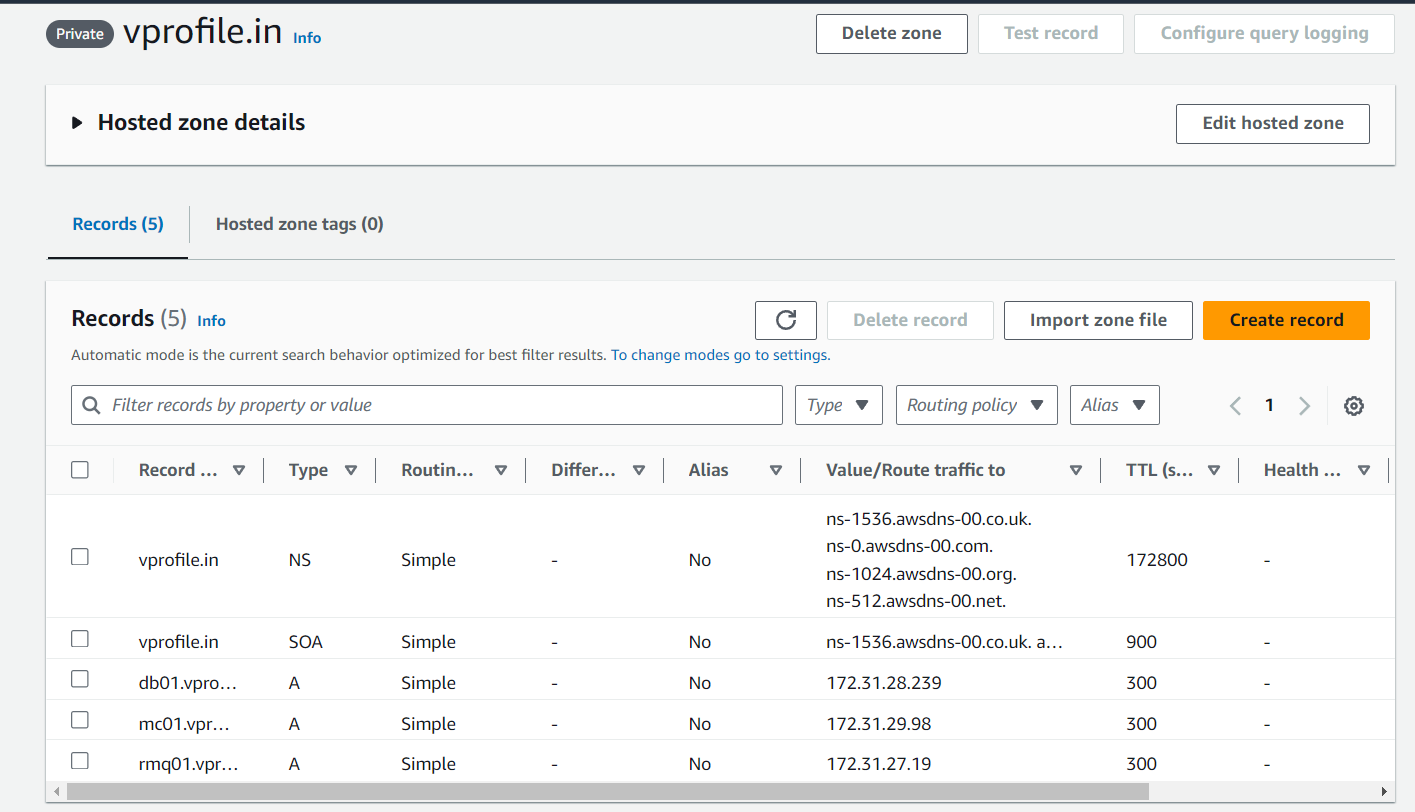
Created a hosted zone with simple routing rules by adding A records for backend servers using their private IPs.
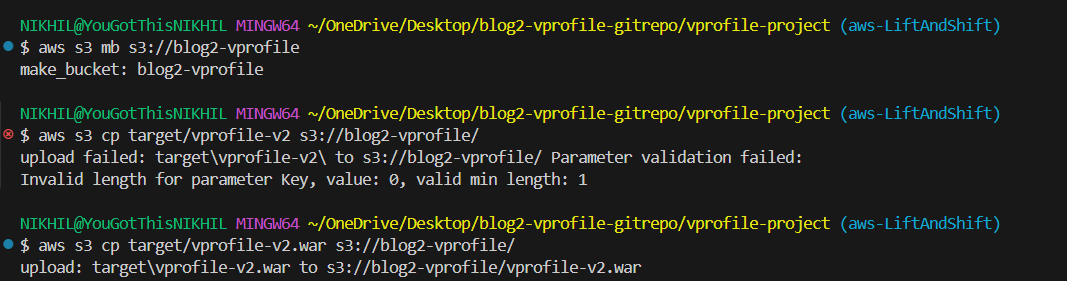
Now, you need to build and upload the artifact.
Update the application.propertiesfile with the correct server routes. Built the arctifact locally using JDK and Maven.
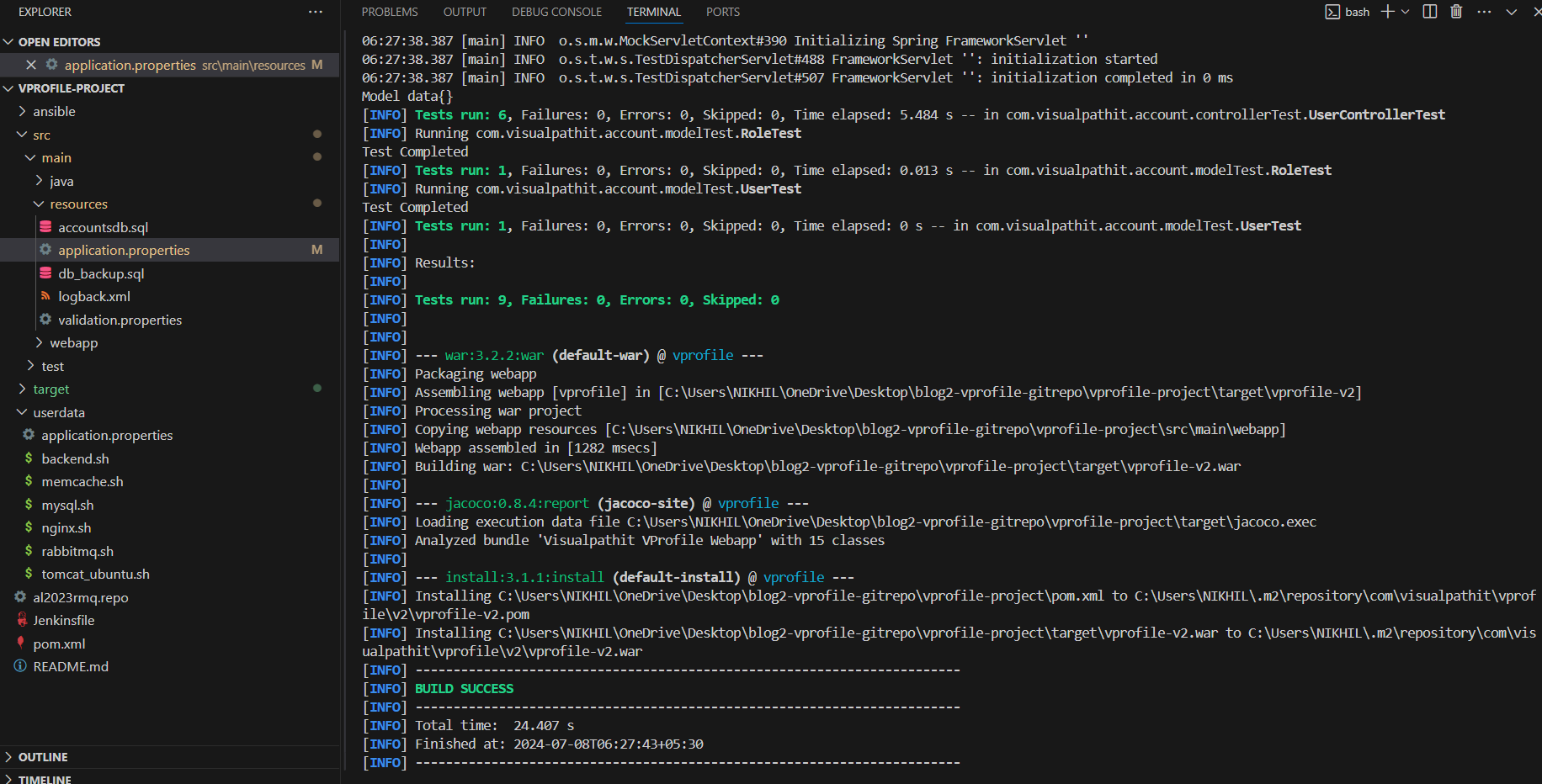
create an IAM user to upload the artifact by creating an S3 bucket and pushing the artifact there.
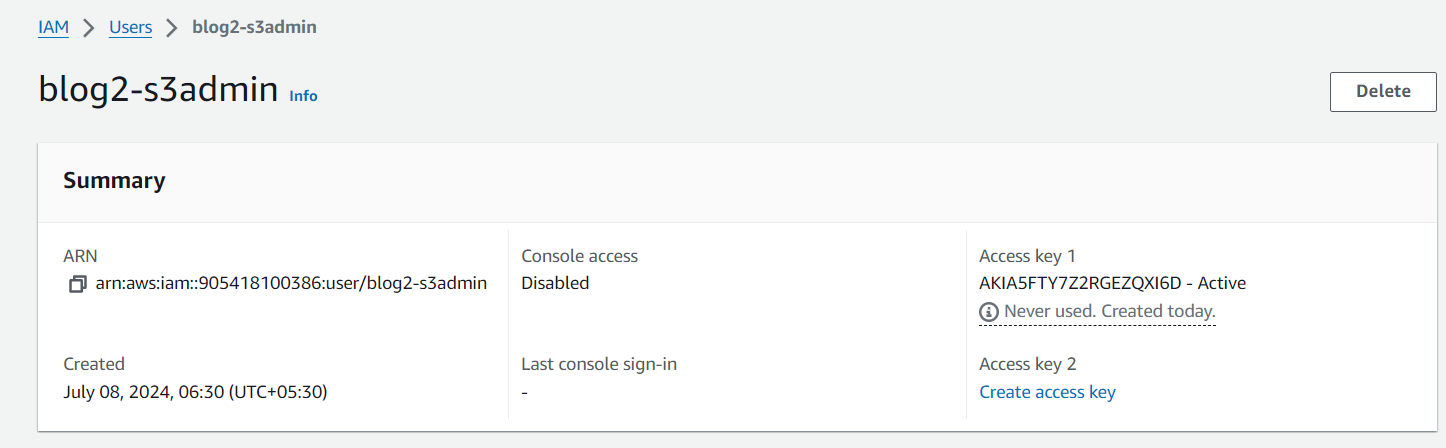
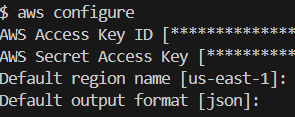
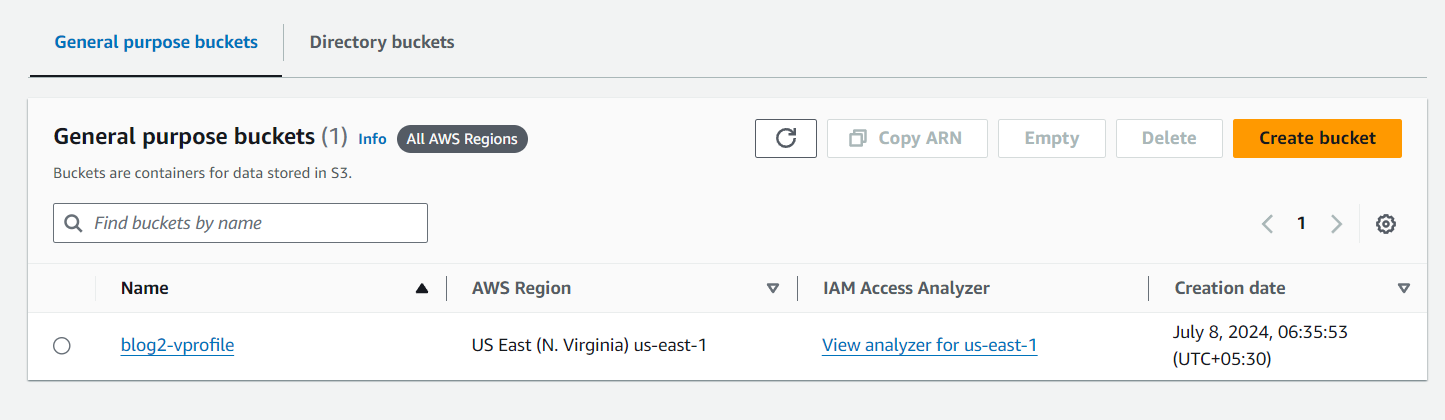
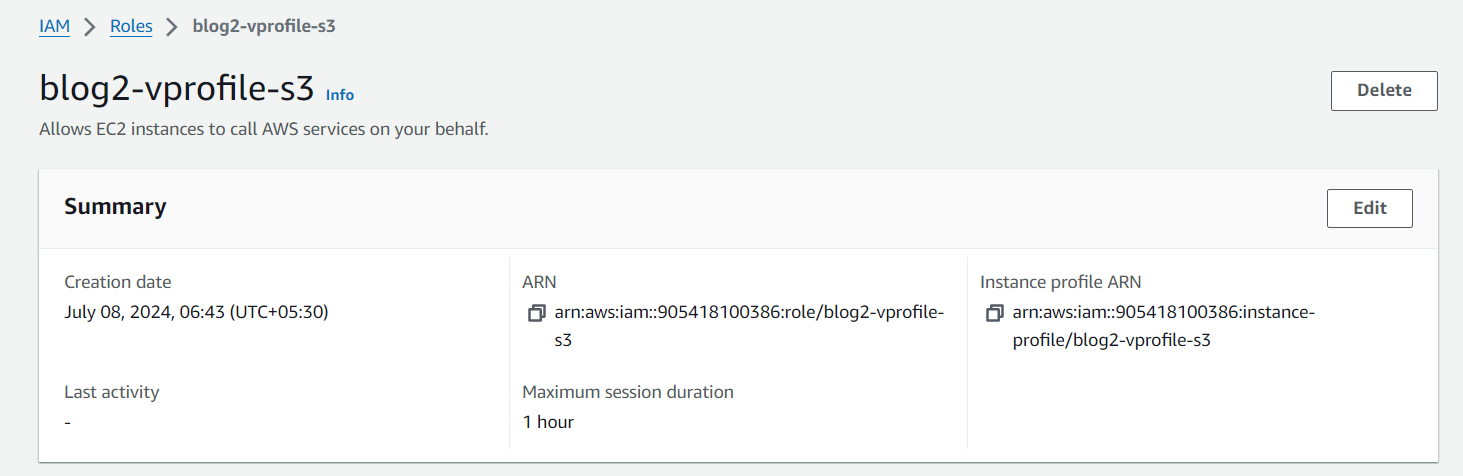
Created an IAM role and gave access to the app server to download the artifact and start the Tomcat service for our app.
Load Balancer :
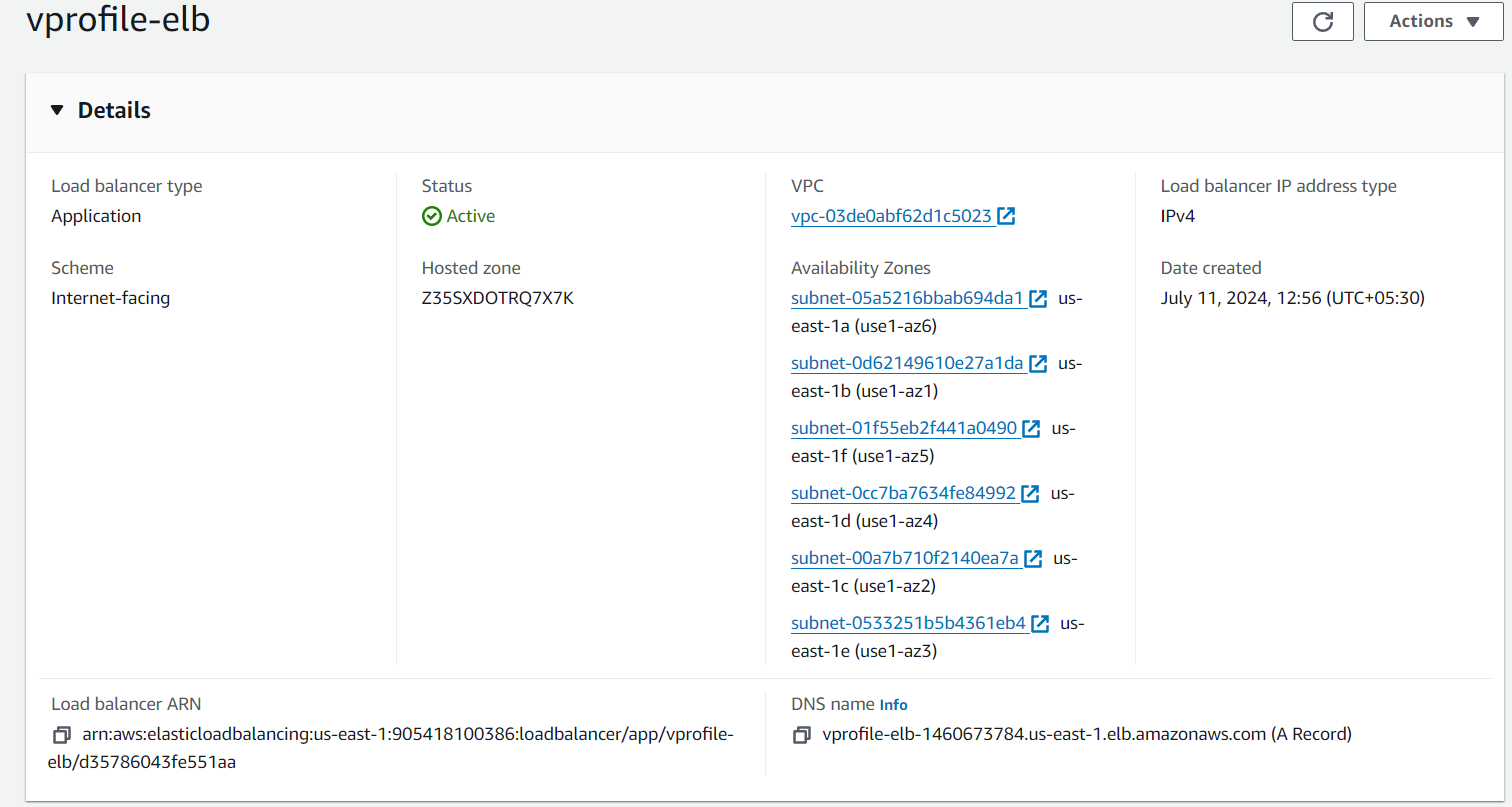
Now, for setting up a load balancer, I created a target group and added our instance that listens on port 8080 as the target. I also set up a health check at /login on port 8080.
I then created an internet-facing application load balancer that is available on all subnets. It listens for both HTTP and HTTPS traffic by adding the target group and certificate.
now, we have our application up and running when we add the elb endpoint to dns as a cname record
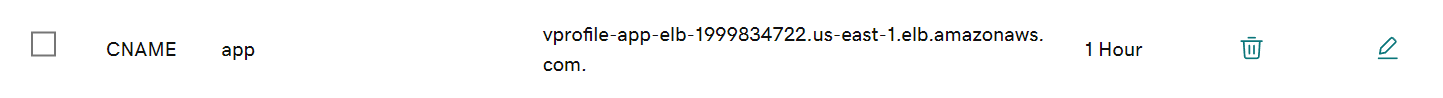
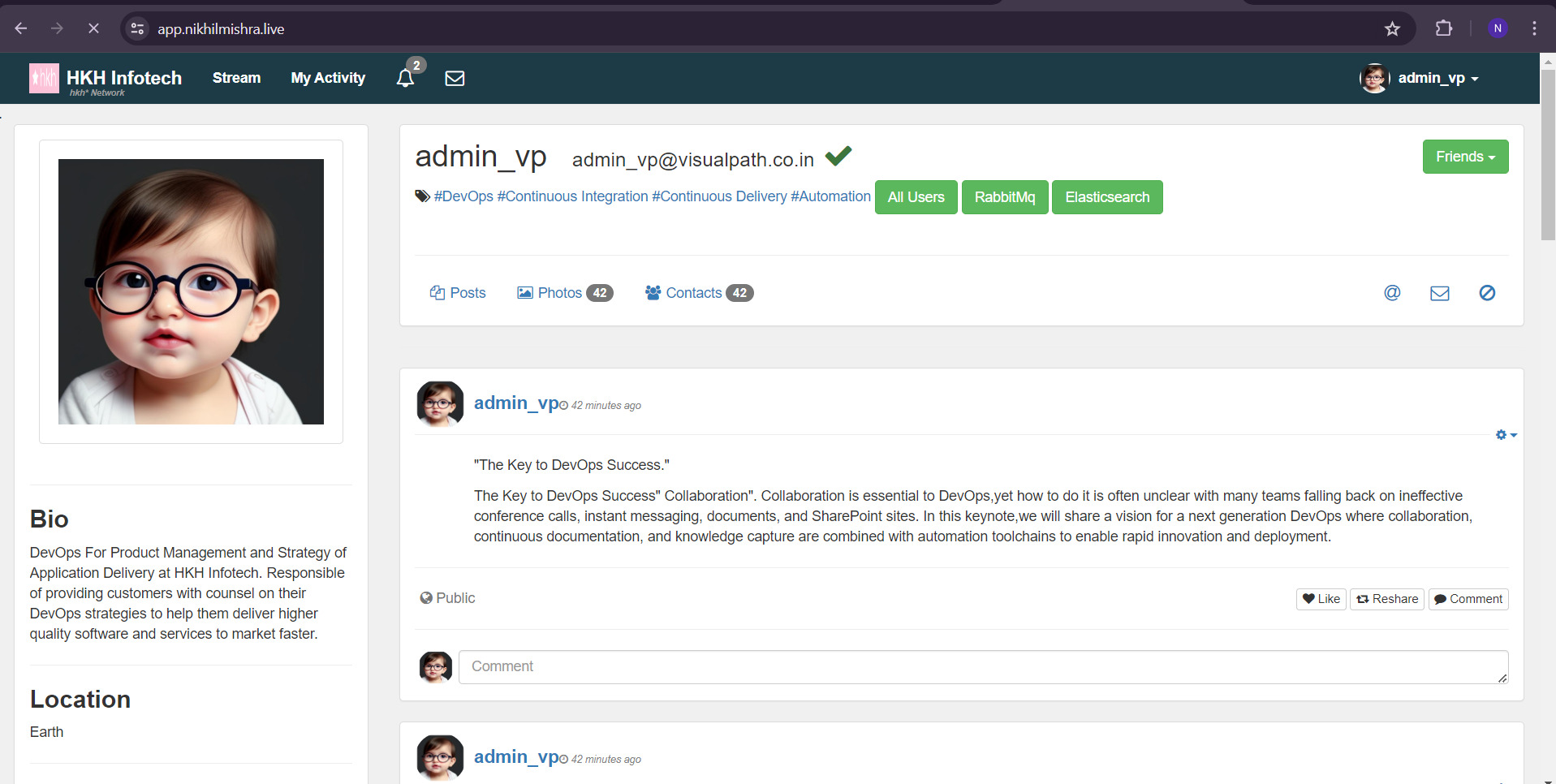
Here's our working app with all services validated
Auto Scaling :
I wanted to make my app ready to scale up based on traffic. To add an auto-scaling group, I first created an AMI of my app instance.
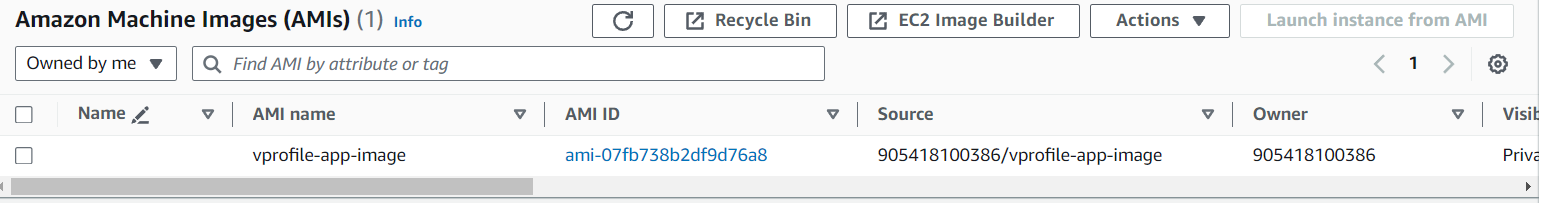
created a launch template using the ami
Then, I created an auto-scaling group with desired triggers and added alarms using SNS.
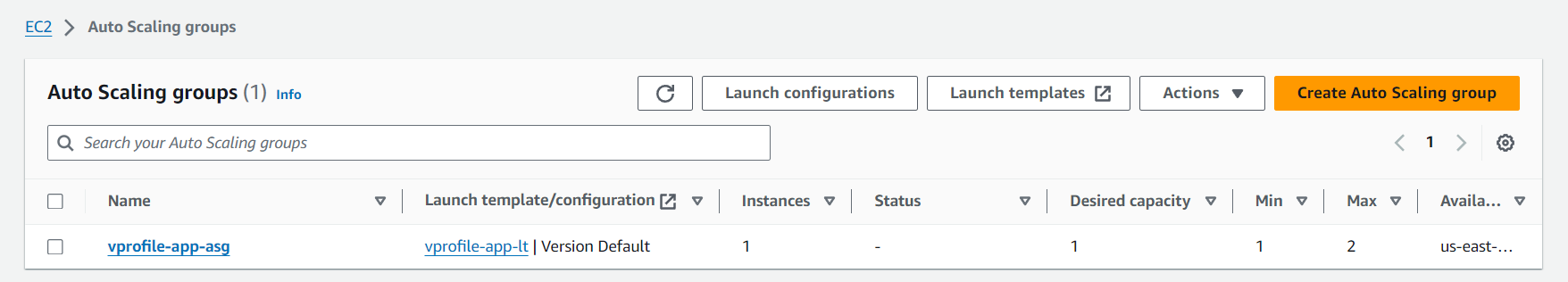
And we are done, here is our webapp working, on cloud :
If you like what Im working on, leave some feedback in comments, a like would be great also subscribe to my newsletter for more such blog delivered straight to your inbox.
Thank you !
Subscribe to my newsletter
Read articles from Nikhil Mishra directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Nikhil Mishra
Nikhil Mishra
I am a student studying in Mumbai University, learning DevOps, looking for opportunities to learn more things by gaining experience at prestigious institutions