Tips for hardening web applications #1
 David Rocha
David Rocha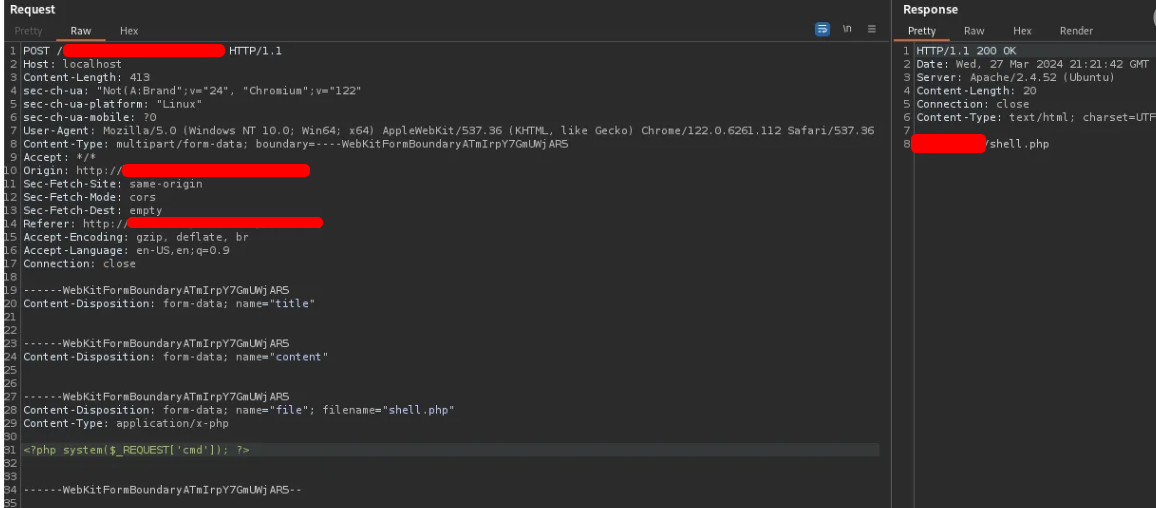
Applications with the option for users to upload files, such as images, documents, PDFs, etc., represent a security risk for web applications. File uploads are often used to upload web shells to targets to obtain persistence (Mitre Att&ck: T1505) and carry out more elaborate attacks on the infrastructure/application. While it is common to implement basic controls such as file type restrictions by extension, MIME type, and signature checking (magic numbers), these controls can be circumvented. Therefore, it is essential to perform an additional check on the files before they are actually written to the application's file system. With a basic level of scanning you should detect and block these files if:
1 - If the file contains code snippets, especially in languages used by your web server (Shellscripts, JS, PHP, .NET, Python).
2 - Keep an updated list of known web shells such as those available in the BlackArch repository (https://github.com/BlackArch/webshells) and check whether they match any of these signatures.
3 - Files containing obfuscated encoding such as base64 can be used to hide malicious code. Implement scanning to detect and block files that use coding techniques to hide their true purpose. As an additional control, consider storing the upload files in a separate directory with restricted access permissions (without execution permissions, for example). This can limit the impact of a possible successful exploit.
Subscribe to my newsletter
Read articles from David Rocha directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
