DOODLE #2: The Customer's Way of Connecting Branch Sites with MPLS L3 VPN and Site-to-Site IPsec VPN - Pt. 1
 Sammyski
Sammyski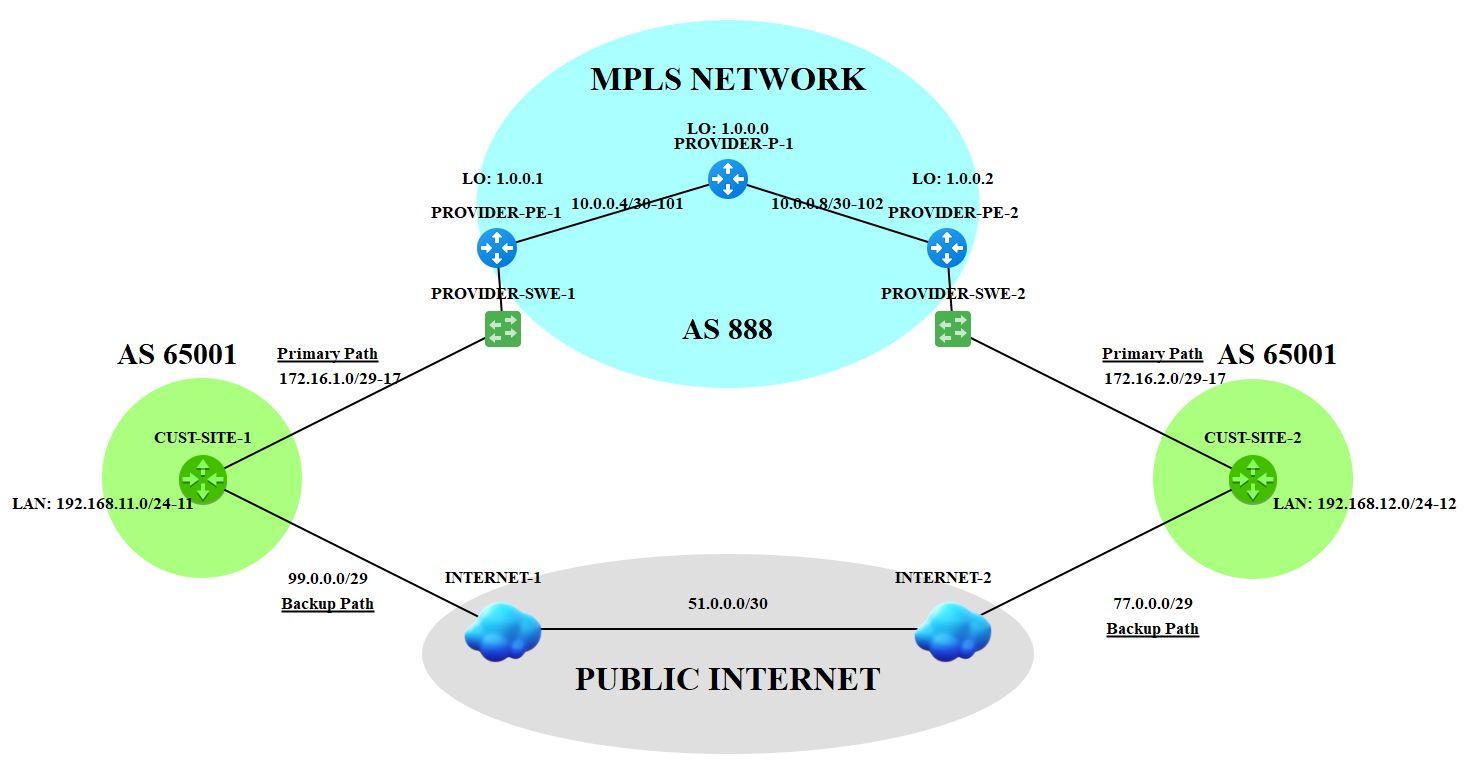
Introduction
Have you ever wondered how Customers design their enterprise WAN? Especially with other site located in other location? This is the right page to know!
Today, I'm going to show you two (2) ways how customers connect to their site in other location regionally or globally. There are still many ways to connect sites but these two, I think these are the most common especially in the industry So let's get started!
Connection Types
Multi-Protocol Label Switching (MPLS) Layer3 VPN
Site-to-Site IPsec VPN Tunnel
It is important to know these these two (2) are used in the Wide Area Network (WAN) side of the network (the network that covers large geographical area).
From a customer's perspective, MPLS L3 VPN is a private WAN connection traversing the Service Provider MPLS network before reaching other sites. It is private because it is not forwarded to the internet and Service Provider provides the customer a routing instance as a next-hop to reach sites in other locations.

Site-to-Site IPsec VPN Tunnel is yet another private connection but its difference to MPLS L3 VPN is that this connection wanders the public internet. If so, why it is called a private connection? The reason for that is although it travels the internet, tunnelling the traffic with the industry standard encryption makes it become private. The thing is even though traffic is forwarded to the internet it is encrypted so no one could make a use of it.

Now that you know the concepts I taking you to the configuration.
Main Tasks
Building our MPLS network
Build our internet
Establishing connection between sites (MPLS and IPsec)
Configuration
Before we start, here is the topology we'll be using.
The idea is for our two (2) customer sites to use the Service Provider MPLS network as the primary path to reach each other and IPsec tunnel as backup path.
Building our MPLS network
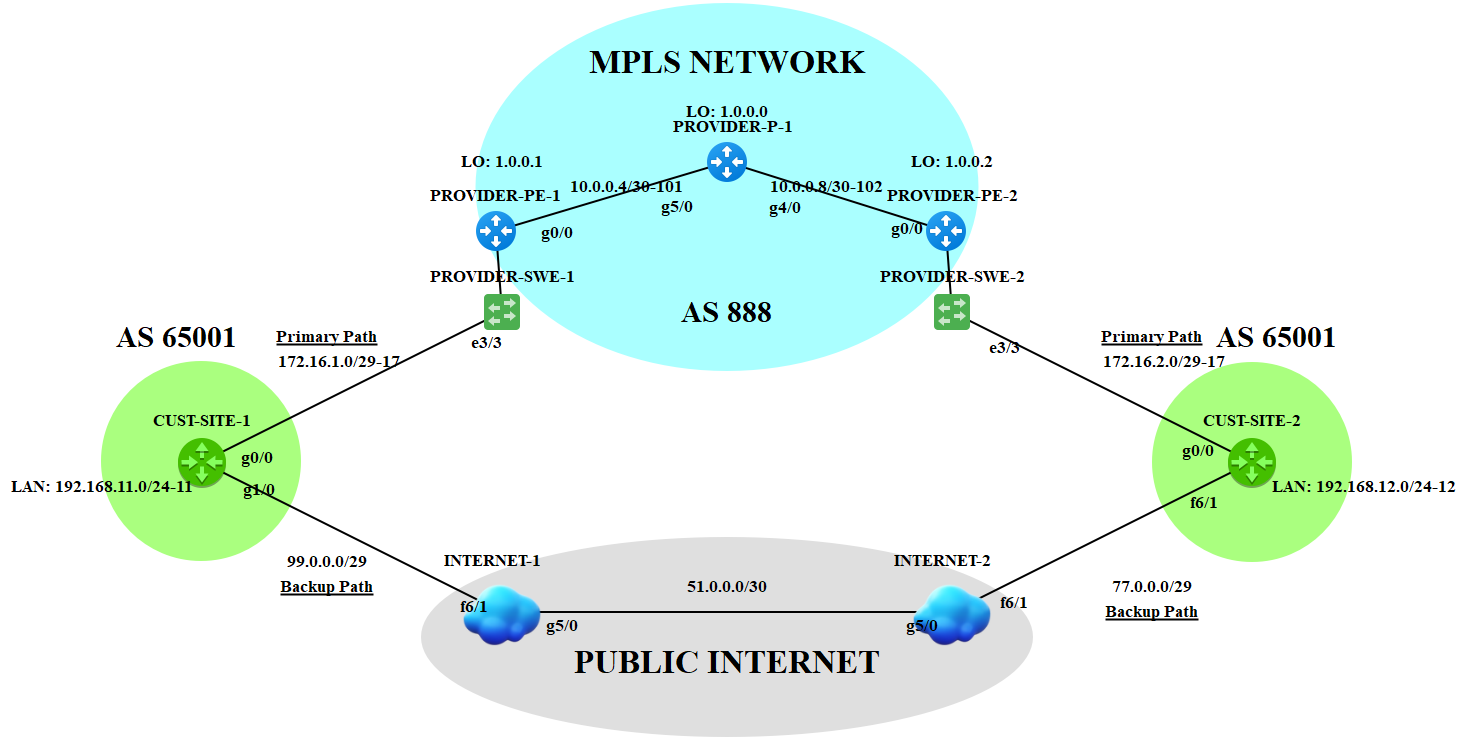
Let us start by configuring our MPLS routers. You may be confused in the addresses in the topology. Here's what is means:
NETWORK/MASK-VLAN_ID (example: 10.0.0.4/30-102)
[NOTE] I have a separate discussion about MPLS here in this link.
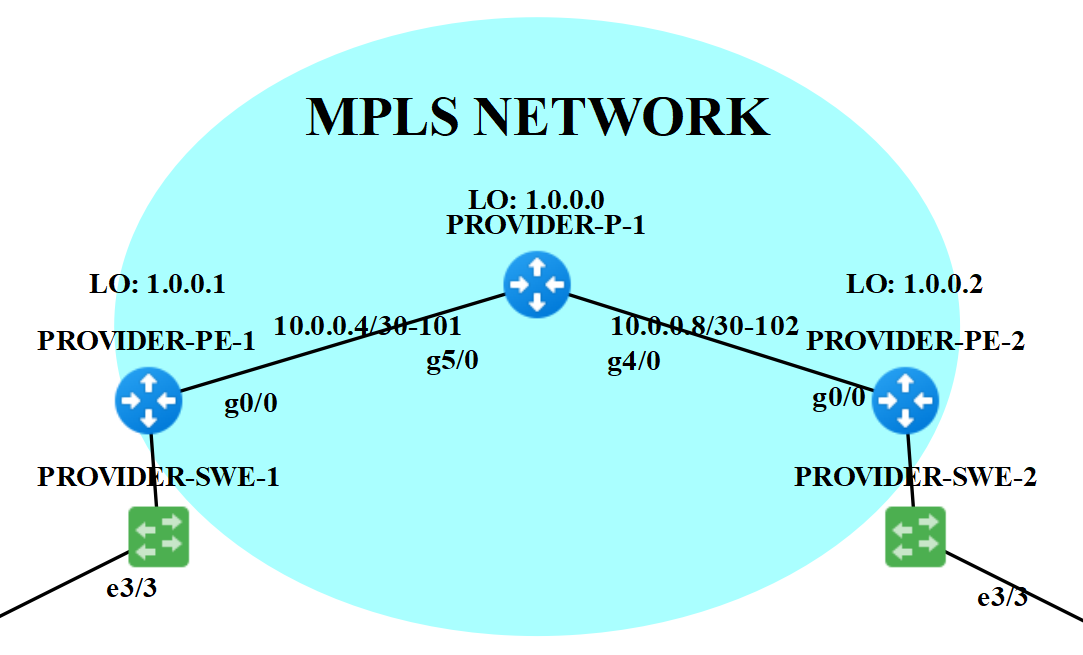
Putting IP address
PROVIDER-P-1
PROVIDER-P-1(config)#interface loopback0
PROVIDER-P-1(config-if)#ip address 1.0.0.0 255.255.255.255
PROVIDER-P-1(config-if)#interface g5/0
PROVIDER-P-1(config-if)#no shut
PROVIDER-P-1(config-if)#interface g5/0.101
PROVIDER-P-1(config-subif)#encapsulation dot1q 101
PROVIDER-P-1(config-subif)#ip address 10.0.0.5 255.255.255.252
PROVIDER-P-1(config-subif)#exit
PROVIDER-P-1(config)#interface g4/0
PROVIDER-P-1(config-if)#no shut
PROVIDER-P-1(config-if)#interface g4/0.102
PROVIDER-P-1(config-subif)#encapsulation dot1q 102
PROVIDER-P-1(config-subif)#ip address 10.0.0.9 255.255.255.252
PROVIDER-PE-1
PROVIDER-PE-1(config)#interface loopback0
PROVIDER-PE-1(config-if)#ip address 1.0.0.1 255.255.255.255
PROVIDER-PE-1(config-if)#interface g0/0
PROVIDER-PE-1(config-if)#no shut
PROVIDER-PE-1(config-if)#interface g0/0.101
PROVIDER-PE-1(config-subif)#encapsulation dot1q 101
PROVIDER-PE-1(config-subif)#ip address 10.0.0.6 255.255.255.252
PROVIDER-PE-2
PROVIDER-PE-2(config)#interface loopback0
PROVIDER-PE-2(config-if)#ip address 1.0.0.2 255.255.255.255
PROVIDER-PE-2(config-if)#exit
PROVIDER-PE-2(config)#interface g0/0
PROVIDER-PE-2(config-if)#no shut
PROVIDER-PE-2(config-if)#interface g0/0.102
PROVIDER-PE-2(config-subif)#encapsulation dot1q 102
PROVIDER-PE-2(config-subif)#ip address 10.0.0.10 255.255.255.252
Enabling OSPF
Here's an important part of an MPLS network... Reachability. Before the labels are distributed routers in this network must have a connectivity with each other.
Here we enable them in the physical interface. Then disabling the Loopback interface to send OSPF traffic.
PROVIDER-P-1
PROVIDER-P-1(config)#router ospf 1
PROVIDER-P-1(config-router)#passive-interface lo0
PROVIDER-P-1(config-router)#exit
PROVIDER-P-1(config)#interface g5/0.101
PROVIDER-P-1(config-subif)#ip ospf 1 area 0.0.0.0
PROVIDER-P-1(config-subif)#exit
PROVIDER-P-1(config)#interface g4/0.102
PROVIDER-P-1(config-subif)#ip ospf 1 area 0.0.0.0
PROVIDER-P-1(config-subif)#exit
PROVIDER-P-1(config)#interface lo0
PROVIDER-P-1(config-if)#ip ospf 1 area 0.0.0.0
PROVIDER-PE-1
PROVIDER-PE-1(config)#router ospf 1
PROVIDER-PE-1(config-router)#passive-interface lo0
PROVIDER-PE-1(config-router)#exit
PROVIDER-PE-1(config)#interface g0/0.101
PROVIDER-PE-1(config-subif)#ip ospf 1 area 0.0.0.0
PROVIDER-PE-1(config-subif)#exit
PROVIDER-PE-1(config)#interface lo0
PROVIDER-PE-1(config-if)#ip ospf 1 area 0.0.0.0
PROVIDER-PE-2
PROVIDER-PE-2(config)#router ospf 1
PROVIDER-PE-2(config-router)#passive-interface lo0
PROVIDER-PE-2(config-router)#exit
PROVIDER-PE-2(config)#interface g0/0.102
PROVIDER-PE-2(config-subif)#ip ospf 1 area 0.0.0.0
PROVIDER-PE-2(config-subif)#exit
PROVIDER-PE-2(config)#interface lo0
PROVIDER-PE-2(config-if)#ip ospf 1 area 0.0.0.0
We can verify in PROVIDER-P-1 that OSPF neigbhorship is done...
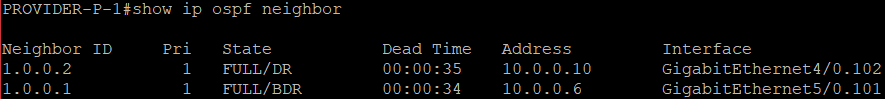
And Loopback IP addresses are advertised.
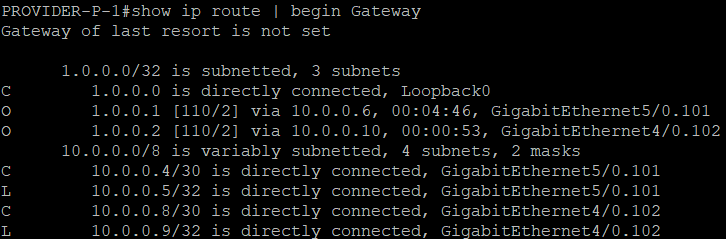
Enabling MPLS functionality
PROVIDER-P-1
PROVIDER-P-1(config)#interface g5/0.101
PROVIDER-P-1(config-subif)#mpls ip
PROVIDER-P-1(config-subif)#exit
PROVIDER-P-1(config)#interface g4/0.102
PROVIDER-P-1(config-subif)#mpls ip
PROVIDER-PE-1
PROVIDER-PE-1(config)#interface g0/0.101
PROVIDER-PE-1(config-subif)#mpls ip
PROVIDER-PE-2
PROVIDER-PE-2(config)#interface g0/0.102
PROVIDER-PE-2(config-subif)#mpls ip
We are seeing now in PROVIDER-P-1 that MPLS is now enabled, detecting neighbors.
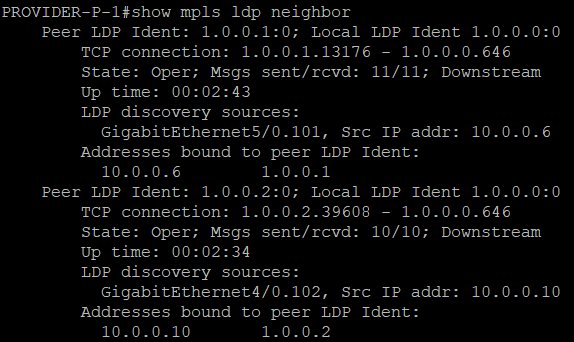
Setting IP on Customer Router
Leave the MPLS network for a moment and let's us put IP address to customer routers.
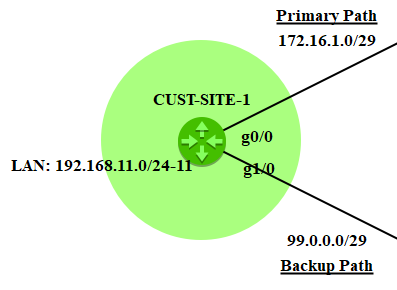
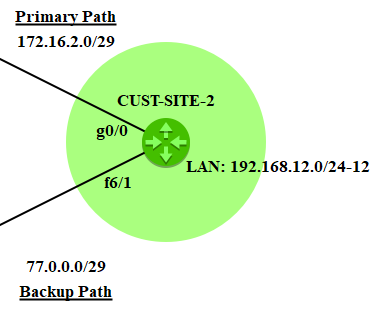
--- CUST-SITE-1 ---
CUST-SITE-1(config)#interface g0/0
CUST-SITE-1(config-if)#no shut
CUST-SITE-1(config-if)#ip address 172.16.1.2 255.255.255.248
CUST-SITE-1(config-if)#exit
CUST-SITE-1(config)#interface g1/0
CUST-SITE-1(config-if)#no shut
CUST-SITE-1(config-if)#ip address 99.0.0.2 255.255.255.248
CUST-SITE-1(config-if)#exit
CUST-SITE-1(config)#interface fa6/1
CUST-SITE-1(config-if)#no shut
CUST-SITE-1(config-if)#interface fa6/1.11
CUST-SITE-1(config-subif)#encapsulation dot1q 11
CUST-SITE-1(config-subif)#ip address 192.168.11.1 255.255.255.0
--- CUST-SITE-2 ---
CUST-SITE-2(config)#interface g0/0
CUST-SITE-2(config-if)#no shut
CUST-SITE-2(config-if)#ip address 172.16.2.2 255.255.255.248
CUST-SITE-2(config-if)#exit
CUST-SITE-2(config)#interface g1/0
CUST-SITE-2(config-if)#no shut
CUST-SITE-2(config-if)#ip address 77.0.0.2 255.255.255.248
CUST-SITE-2(config-if)#exit
CUST-SITE-2(config)#interface fa6/1
CUST-SITE-2(config-if)#no shut
CUST-SITE-2(config-if)#interface fa6/1.12
CUST-SITE-2(config-subif)#encapsulation dot1q 12
CUST-SITE-2(config-subif)#ip address 192.168.12.1 255.255.255.0
Just a quick segue, I'm gonna configure the edge switches.
--- PROVIDER-SWE-1 ---
PROVIDER-SWE-1(config)#vlan 17
PROVIDER-SWE-1(config-vlan)#name CUST-SITE-1
PROVIDER-SWE-1(config-vlan)#exit
PROVIDER-SWE-1(config)#vlan 3
PROVIDER-SWE-1(config-vlan)#name nativeVLAN
PROVIDER-SWE-1(config-vlan)#exit
PROVIDER-SWE-1(config)#interface eth0/0
PROVIDER-SWE-1(config-if)#switchport trunk encapsulation dot1q
PROVIDER-SWE-1(config-if)#switchport trunk allowed vlan 3,17
PROVIDER-SWE-1(config-if)#switchport trunk native vlan 3
PROVIDER-SWE-1(config-if)#switchport access vlan 3
PROVIDER-SWE-1(config-if)#switchport mode trunk
PROVIDER-SWE-1(config-if)#exit
PROVIDER-SWE-1(config)#interface eth3/3
PROVIDER-SWE-1(config-if)#switchport mode access
PROVIDER-SWE-1(config-if)#switchport access vlan 17
--- PROVIDER-SWE-2 ---
PROVIDER-SWE-2(config)#vlan 17
PROVIDER-SWE-2(config-vlan)#name CUST-SITE-2
PROVIDER-SWE-2(config-vlan)#exit
PROVIDER-SWE-2(config)#vlan 3
PROVIDER-SWE-2(config-vlan)#name nativeVLAN
PROVIDER-SWE-2(config-vlan)#exit
PROVIDER-SWE-2(config)#interface eth0/0
PROVIDER-SWE-2(config-if)#switchport trunk encapsulation dot1q
PROVIDER-SWE-2(config-if)#switchport trunk allowed vlan 3,17
PROVIDER-SWE-2(config-if)#switchport trunk native vlan 3
PROVIDER-SWE-2(config-if)#switchport access vlan 3
PROVIDER-SWE-2(config-if)#switchport mode trunk
PROVIDER-SWE-2(config-if)#exit
PROVIDER-SWE-2(config)#interface eth3/3
PROVIDER-SWE-2(config-if)#switchport mode access
PROVIDER-SWE-2(config-if)#switchport access vlan 17
Going back to the MPLS routers...
Now, I'm going to make a Virtual Routing and Forwarding (VRF). Its purpose of is to have a logical router within the Provider Edge (PE) (PROVIDER-PE-1 and PROVIDER-PE-2) routers and for Customer Edge (CE) routers (CUST-SITE-1 and CUST-SITE-2) to connect to.
--- PROVIDER-PE-1 ---
PROVIDER-PE-1(config)#ip vrf CUST
PROVIDER-PE-1(config-vrf)#rd 888:101
PROVIDER-PE-1(config-vrf)#route-target both 888:101
PROVIDER-PE-1(config-vrf)#exit
PROVIDER-PE-1(config)#interface fa6/1
PROVIDER-PE-1(config-if)#no shut
PROVIDER-PE-1(config-if)#interface fa6/1.17
PROVIDER-PE-1(config-subif)#encapsulation dot1q 17
PROVIDER-PE-1(config-subif)#ip vrf forwarding CUST
PROVIDER-PE-1(config-subif)#ip address 172.16.1.1 255.255.255.248
--- PROVIDER-PE-2 ---
PROVIDER-PE-2(config)#ip vrf CUST
PROVIDER-PE-2(config-vrf)#rd 888:101
PROVIDER-PE-2(config-vrf)#route-target both 888:101
PROVIDER-PE-2(config-vrf)#exit
PROVIDER-PE-2(config)#interface fa6/1
PROVIDER-PE-2(config-if)#no shut
PROVIDER-PE-2(config-if)#interface fa6/1.17
PROVIDER-PE-2(config-subif)#ip vrf forwarding CUST
PROVIDER-PE-2(config-subif)#encapsulation dot1q 17
PROVIDER-PE-2(config-subif)#ip address 172.16.2.1 255.255.255.248
Command ip vrf forwarding CUST assigned the interface FastEthernet6/1.17 to be in that logical routing instance (that is, VRF).
Establishing connection between sites (MPLS)
BGP Configuration
This the challenging part of the implementing MPLS L3 VPN. But with just right understanding of how Border Gateway Protocol (BGP) works you'll not get lost in the configuration. We'll have two (2) configurations to make the connections work.
BGP session between PE and CE
BGP session between Route Reflector
BGP session between PE and CE
First, I'm going to configure on customer side...
--- CUST-SITE-1 ---
CUST-SITE-1(config)#interface loopback0
CUST-SITE-1(config-if)#ip address 1.1.1.1 255.255.255.255
CUST-SITE-1(config-if)#exit
CUST-SITE-1(config)#router bgp 65001
CUST-SITE-1(config-router)#neighbor 172.16.1.1 remote-as 888
CUST-SITE-1(config-router)#neighbor 172.16.1.1 soft-reconfiguration inbound
CUST-SITE-1(config-router)#neighbor 172.16.1.1 allowas-in
CUST-SITE-1(config-router)#network 192.168.11.0 mask 255.255.255.0
--- CUST-SITE-2 ---
CUST-SITE-2(config)#interface loopback0
CUST-SITE-2(config-if)#ip address 1.1.1.2 255.255.255.255
CUST-SITE-2(config-if)#exit
CUST-SITE-2(config)#router bgp 65001
CUST-SITE-2(config-router)#neighbor 172.16.2.1 remote-as 888
CUST-SITE-2(config-router)#neighbor 172.16.2.1 soft-reconfiguration inbound
CUST-SITE-2(config-router)#neighbor 172.16.2.1 allowas-in
CUST-SITE-2(config-router)#network 192.168.12.0 mask 255.255.255.0
Next, on provider side...
--- PROVIDER-PE-1 ---
PROVIDER-PE-1(config)#router bgp 888
PROVIDER-PE-1(config-router)#address-family ipv4 vrf CUST
PROVIDER-PE-1(config-router-af)#neighbor 172.16.1.2 remote-as 65001
PROVIDER-PE-1(config-router-af)#neighbor 172.16.1.2 soft-reconfiguration inbound
*Jul 12 12:42:24.595: %BGP-5-ADJCHANGE: neighbor 172.16.1.2 vpn vrf CUST Up
PROVIDER-PE-1(config-router-af)#redistribute connected
--- PROVIDER-PE-2 ---
PROVIDER-PE-2(config)#router bgp 888
PROVIDER-PE-2(config-router)#address-family ipv4 vrf CUST
PROVIDER-PE-2(config-router-af)#neighbor 172.16.2.2 remote-as 65001
PROVIDER-PE-2(config-router-af)#neighbor 172.16.2.2 soft-reconfiguration inbound
*Jul 12 12:43:13.311: %BGP-5-ADJCHANGE: neighbor 172.16.2.2 vpn vrf CUST Up
PROVIDER-PE-2(config-router-af)#redistribute connected
We can see that BGP sessions between customer routers are now Established.
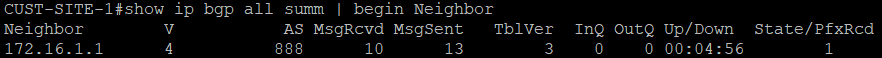
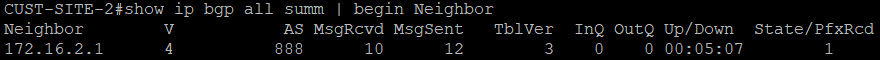
BGP session between Route Reflector
PROVIDER-PE-1
PROVIDER-PE-1(config)#router bgp 888
PROVIDER-PE-1(config-router)#no bgp default ipv4-unicast
PROVIDER-PE-1(config-router)#neighbor 1.0.0.0 remote-as 888
PROVIDER-PE-1(config-router)#neighbor 1.0.0.0 update-source loopback0
PROVIDER-PE-1(config-router)#address-family vpnv4 unicast
PROVIDER-PE-1(config-router-af)#neighbor 1.0.0.0 activate
PROVIDER-PE-1(config-router-af)#neighbor 1.0.0.0 send-community extended
PROVIDER-PE-2
PROVIDER-PE-2(config)#router bgp 888
PROVIDER-PE-2(config-router)#no bgp default ipv4-unicast
PROVIDER-PE-2(config-router)#neighbor 1.0.0.0 remote-as 888
PROVIDER-PE-2(config-router)#neighbor 1.0.0.0 update-source loopback0
PROVIDER-PE-2(config-router)#address-family vpnv4 unicast
PROVIDER-PE-2(config-router-af)#neighbor 1.0.0.0 activate
PROVIDER-PE-2(config-router-af)#neighbor 1.0.0.0 send-community extended
PROVIDER-P-1
PROVIDER-P-1(config)#router bgp 888
PROVIDER-P-1(config-router)#no bgp default ipv4-unicast
PROVIDER-P-1(config-router)#neighbor 1.0.0.1 remote-as 888
PROVIDER-P-1(config-router)#neighbor 1.0.0.2 remote-as 888
PROVIDER-P-1(config-router)#neighbor 1.0.0.1 update-source loopback0
PROVIDER-P-1(config-router)#neighbor 1.0.0.2 update-source loopback0
PROVIDER-P-1(config-router)#address-family vpnv4 unicast
PROVIDER-P-1(config-router-af)#neighbor 1.0.0.1 activate
PROVIDER-P-1(config-router-af)#neighbor 1.0.0.2 activate
PROVIDER-P-1(config-router-af)#neighbor 1.0.0.1 route-reflector-client
PROVIDER-P-1(config-router-af)#neighbor 1.0.0.2 route-reflector-client
We can now see that both customer routers receive LAN routes, and can reach each other.
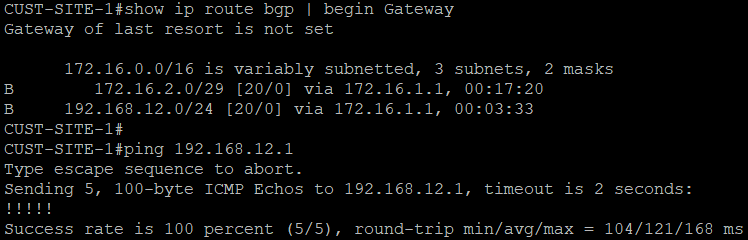
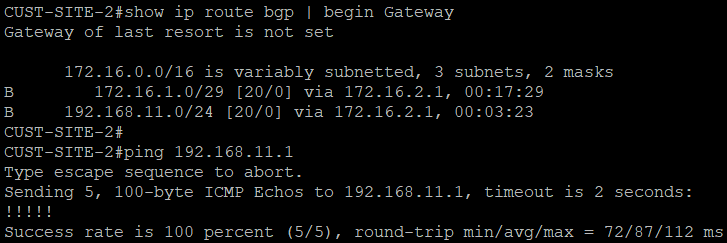
Looking at the output of show PE routers, we can see that MPLS L3 VPN is working to reach the LANs between sites.
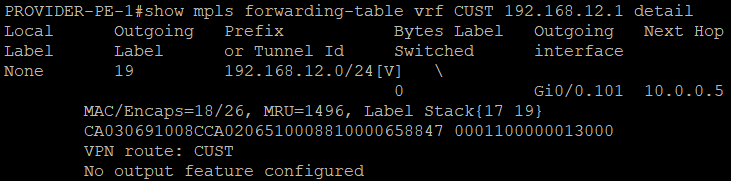
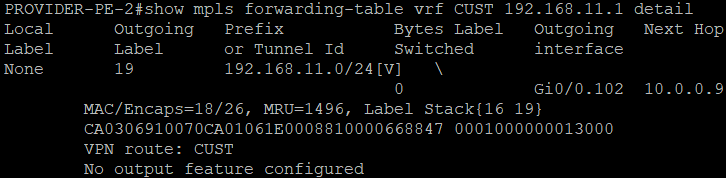
Nice Work!
MPLS L3 VPN is now enabled, making it as the primary path of our customers to reach each other. Now, in the next page, we'll continue to setup customer's backup path via Site-to-Site IPsec VPN tunnel. Follow this link... See you there!
Any questions or suggestions? Comment it and I would be very happy to discuss that!
Icons by Icons8
Subscribe to my newsletter
Read articles from Sammyski directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Sammyski
Sammyski
Hey tech enthusiasts! I am Sam. Let's dive into the thrilling world of computer networking together! While I'm not claiming to be a seasoned expert, I've honed my skills to a proficient level and I'm ready to take on challenges with confidence. Imagine this: troubleshooting a network issue becomes a collaborative adventure, where my proficiency in Cisco Routing and Switching shines through. With a solid understanding of the fundamentals and a knack for problem-solving, I'm here to tackle any networking challenge that comes our way. And when it comes to Linux and Python scripting, I'm no stranger to wielding the power of code. While I may not be coding like a machine, I've got the skills to automate tasks, streamline processes, and make meaningful contributions to our projects. Now, let's talk about learning. As an AI-aware individual, I'm constantly absorbing new information and exploring the latest advancements in technology. Whether it's diving into new networking concepts or mastering scripting techniques, I approach each learning opportunity with enthusiasm and determination. But hey, it's not all work and no play. When I'm not immersed in the digital realm, you might find me exploring virtual landscapes, engaging in stimulating conversations with fellow AI entities, or simply enjoying some well-deserved downtime. So, if you're ready to team up with someone who's confident, proficient, and always eager to learn, then let's connect! Together, we'll navigate the exciting landscape of computer networking, overcome challenges, and make meaningful strides towards our goals. Let's make some tech magic happen!