Cross Tenant Authentication for TDE via Workload Federation identity
 Osama Shaikh
Osama ShaikhIntroduction:
In my recent engagement with a customer operating under a multi-tenant architecture, I encountered a shared service model where a centralized Hub included a Key Management Service (KMS) using a Dedicated Hardware Security Module (HSM). In this setup, all encryption activities across the organization leveraged the HSM for Bring Your Own Key (BYOK) to secure various data services, including MySQL and MSSQL databases.
Given that the data services and the HSM resided in different Azure tenants, it was crucial for the managed identities associated with these data services to authenticate to the HSM cross-tenant with the necessary Role-Based Access Control (RBAC) privileges. However, managed identities typically do not support cross-tenant scenarios by default.
With the recent General Availability (GA) of the 'Workload Identity Federation' feature in Microsoft Entra, a new approach has emerged to address this challenge. In this article, I will explore how federated credentials can be leveraged to facilitate cross-tenant authentication, enabling secure and efficient data encryption across disparate Azure tenants.
Pre-Requsite
User Access Administrator+Contributor RBAC on source Az tenant subcriptions(Data services subscription)
Microsoft Entra Application Administrator RBAC on source tenant
Entra ID App Admin+Contributor RBAC on destination subscription that host HSM/AKV
Setup Microsoft Entra for App Registration
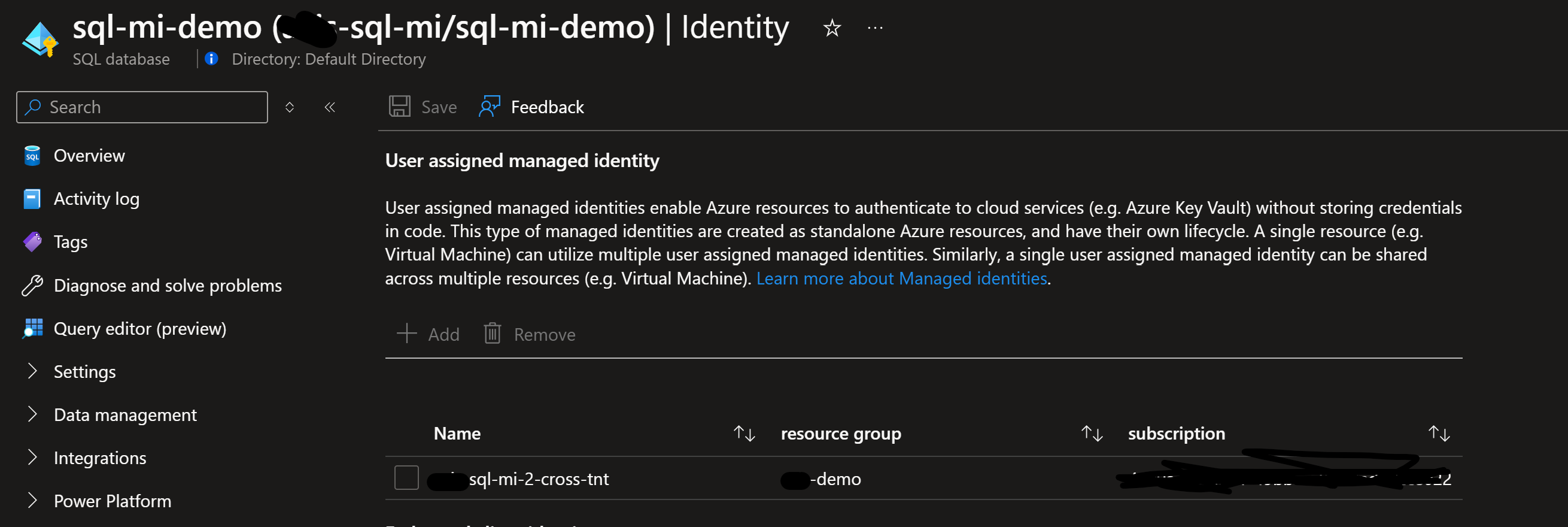
Make sure data service(MSSQL) where encryption is needed configure with 'user managed identity'
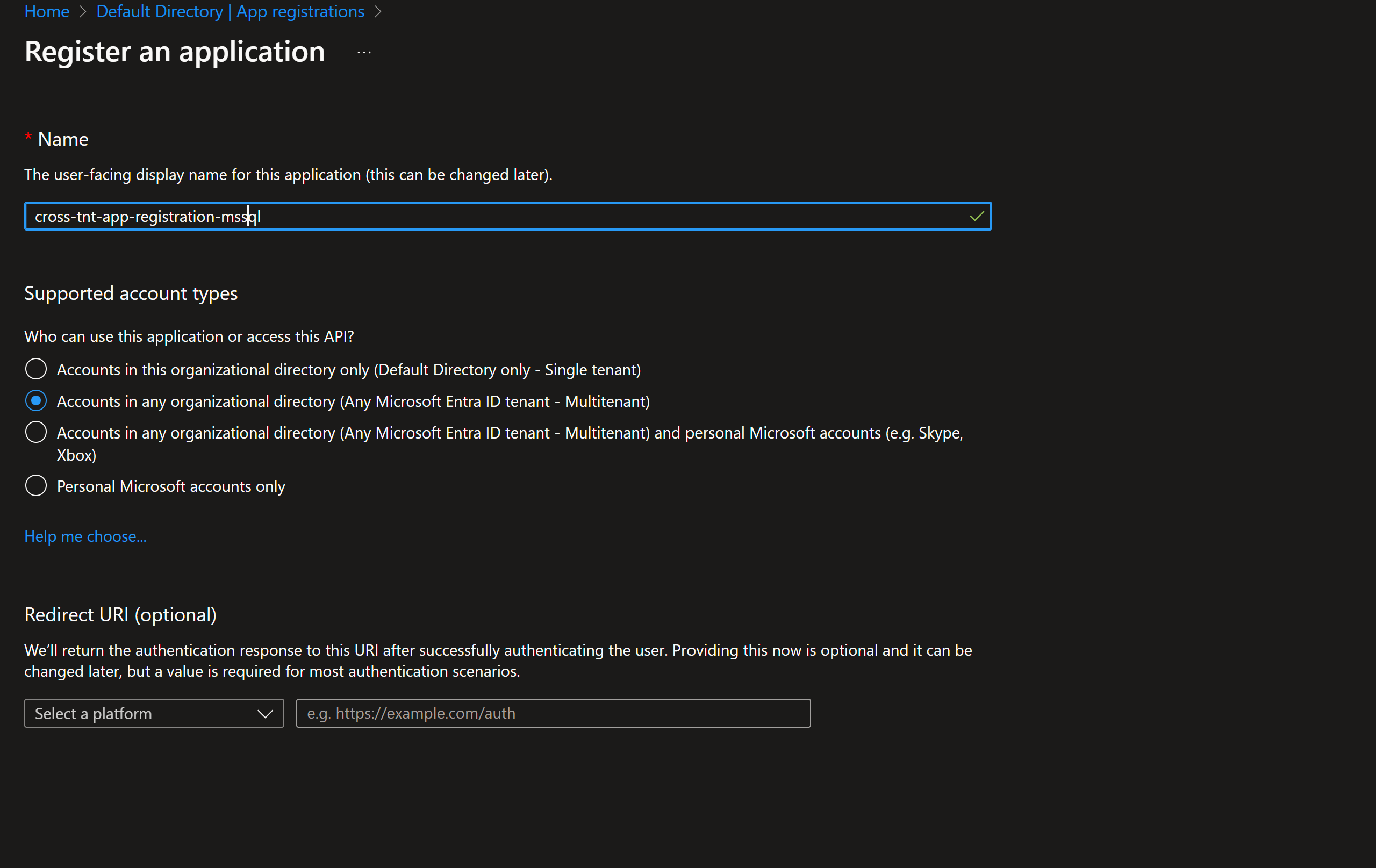
Create App Registartion(SP) in MS Entra ID(source) with Multi-tenat options
Now next step is to connect App registration that we just created with 'User Managed Identity' associated with data services(SQL)
Enable Federated credetails feature on App registration with CMK options and select user managed identity of MSSQL
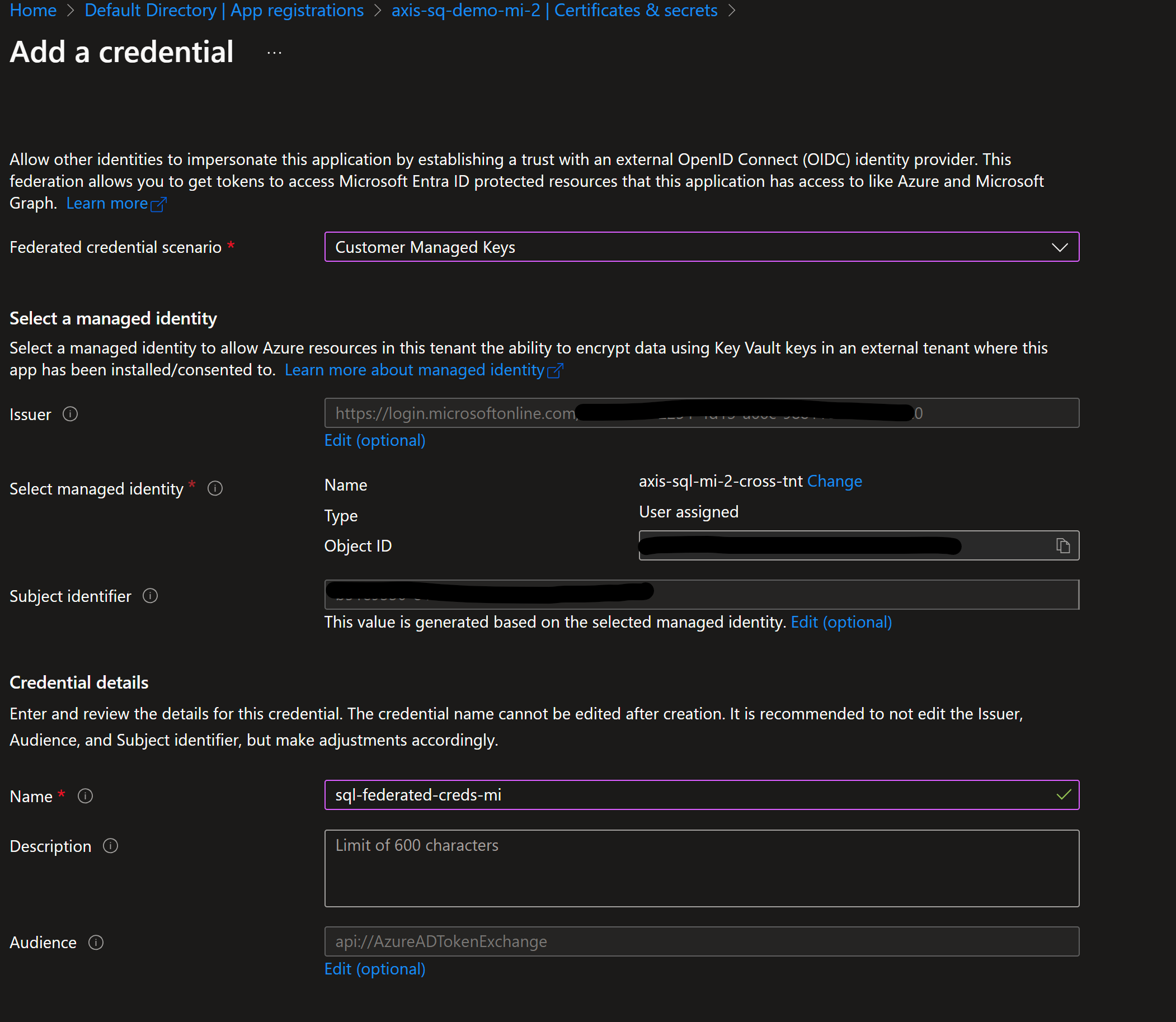
Login to destination Az tenant(AKV hosted) & create App Registration using Client ID of App registartion created in ealier step
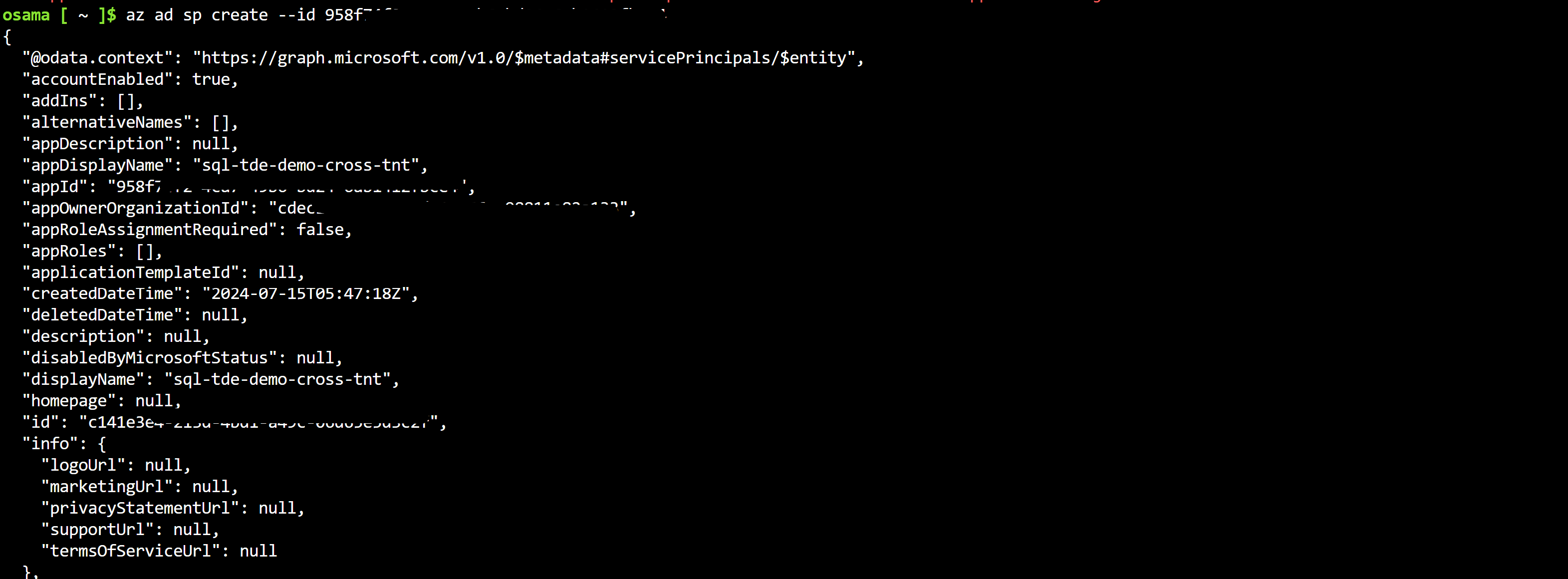
App registration is now linked with existing App regsitartion in source tenant
Next Assign RBAC "Keyvault Crypto Office" against App Registration using its name
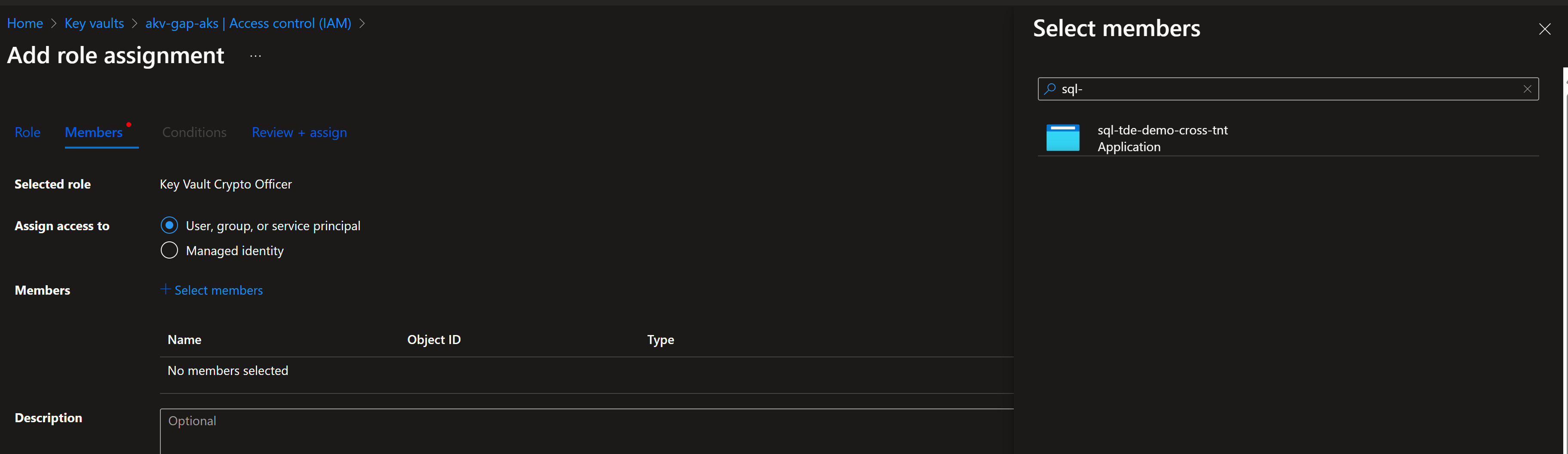
Once permission are assigned, now switch to source tenant which host your data service i.e SQL databases.
Under identity blade of SQL, configure federated identity & select Application registered name that we created intially
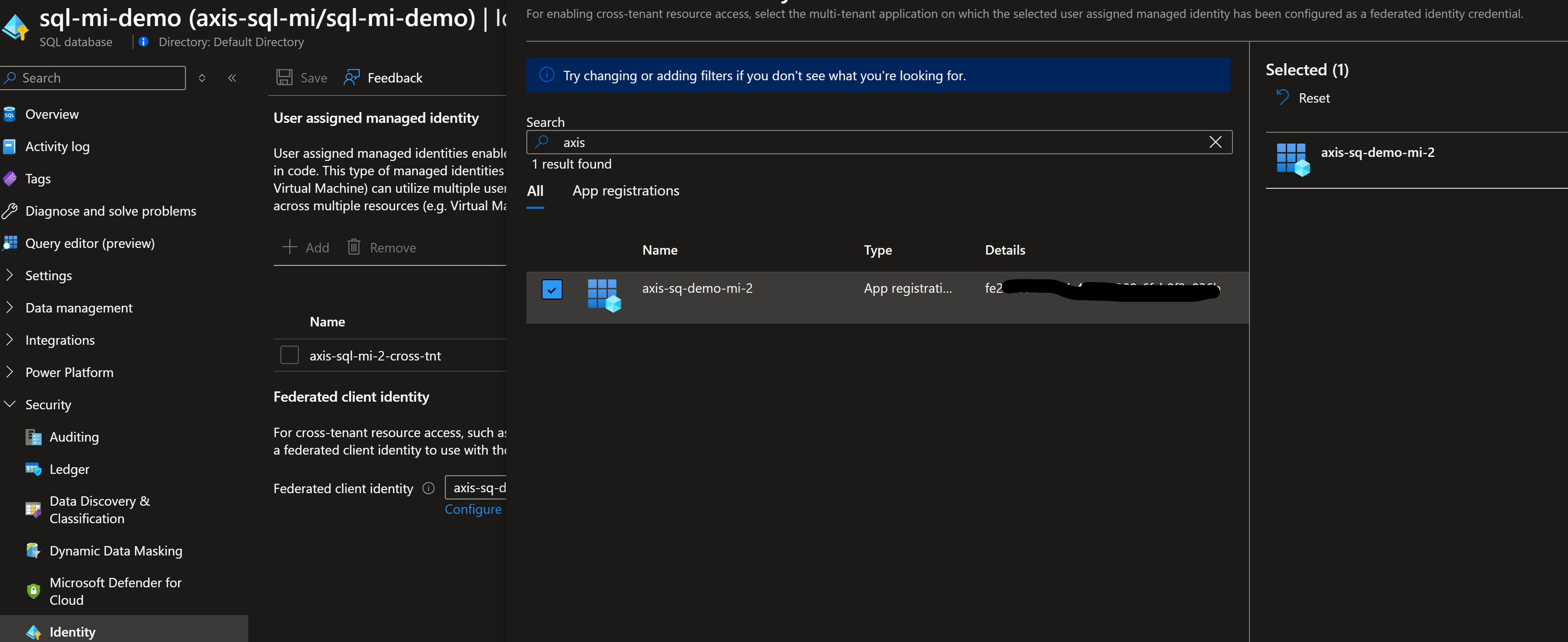
Now under Data encryption for SQL select 'user manage identity' & 'Federated identity' then paste HSM/AKV keys identifier URI from other tenant & save
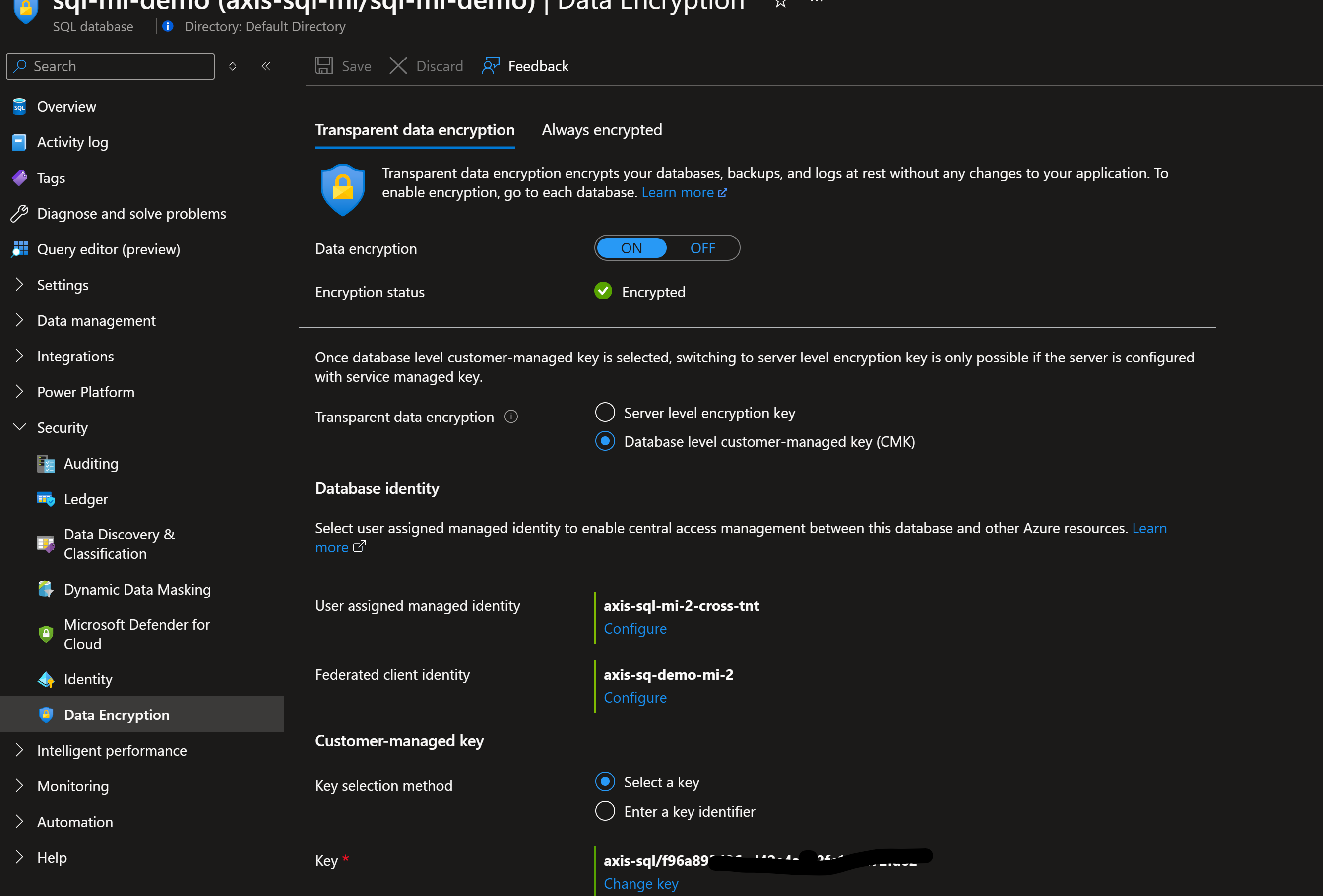
Once configuration is saved succesfully its completed TDE for your databases using HSM/AKV from cross tenant
This cross scenarios wouldnt have possible with leveraging Federated Credential feature of Entra ID
Subscribe to my newsletter
Read articles from Osama Shaikh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Osama Shaikh
Osama Shaikh
I have been working as App/Infra Solution Architect with Microsoft from 5 years. Helping diverse set of customers across vertical i.e. BFSI, ITES, Digital Native in their journey towards cloud