Hunting Bugs with GAU and HTTPX: A Step-by-Step Guide
 prasanna
prasanna 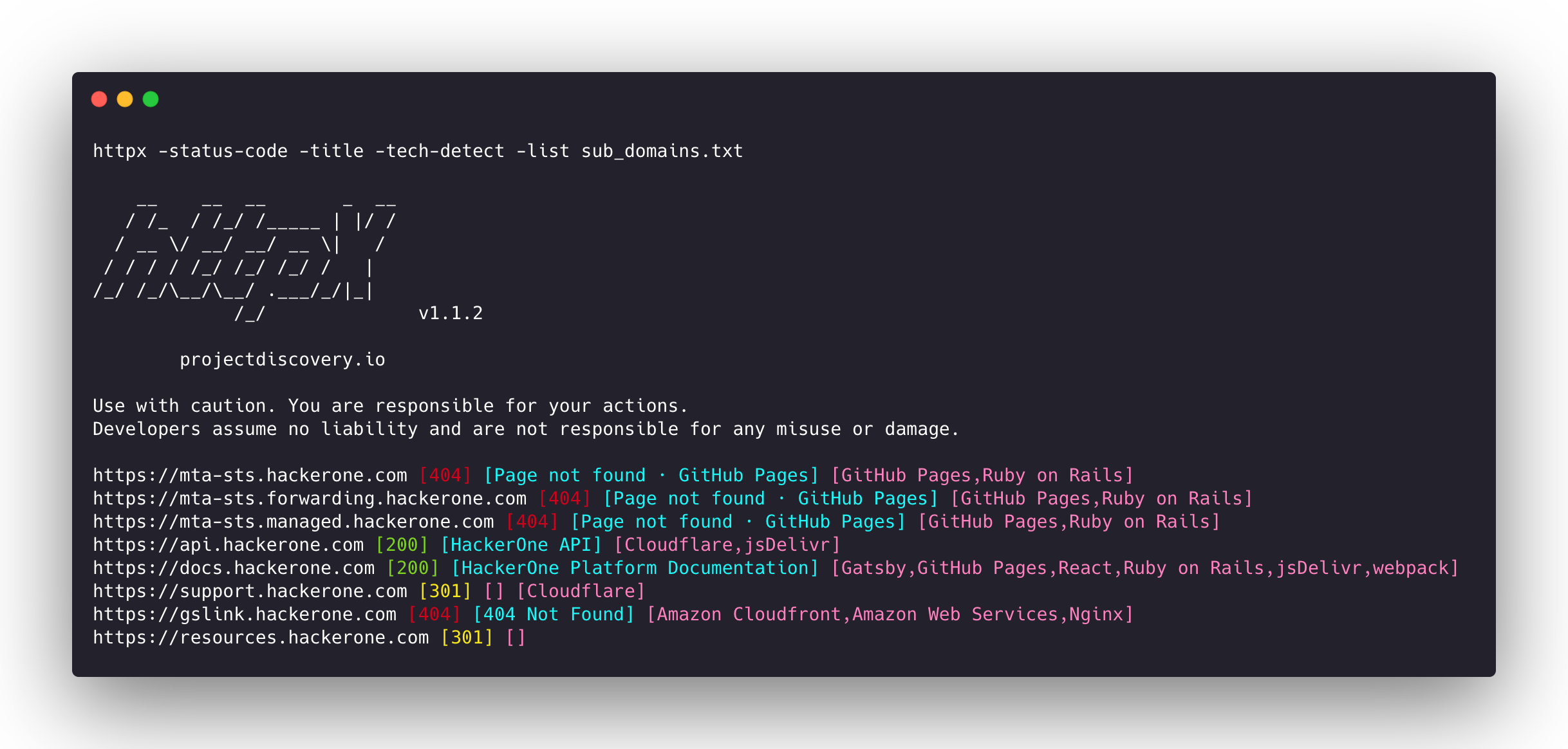
Bug bounty hunting is a thrilling field where security enthusiasts and professionals test their skills against live systems, seeking vulnerabilities that can be reported for rewards. In this guide, we'll explore how to use two powerful tools, GAU (Get All URLs) and HTTPX, to streamline your bug bounty hunting process.
Table of Contents
Introduction to Bug Bounty Hunting
Setting Up Your Environment
Gathering URLs with GAU
Probing URLs with HTTPX
Analyzing the Results
Tips for Effective Bug Bounty Hunting
Conclusion
1. Introduction to Bug Bounty Hunting
Bug bounty programs allow individuals to discover and report security vulnerabilities in applications, websites, and other systems. Companies benefit by having a larger pool of testers, and hunters gain experience, recognition, and monetary rewards.
2. Setting Up Your Environment
Before diving into URL gathering and probing, you'll need to set up your environment. This guide assumes you have a basic understanding of command-line interfaces and have Python installed.
Install GAU
GAU is a powerful tool that extracts URLs from various sources, including Wayback Machine, Common Crawl, and URLScan.
go install github.com/lc/gau/v2/cmd/gau@latest
Install HTTPX
HTTPX is a fast and multi-purpose HTTP toolkit designed for security testing.
go install github.com/projectdiscovery/httpx/cmd/httpx@latest
3. Gathering URLs with GAU
GAU helps you gather URLs from multiple sources, providing a comprehensive list to work with.
Basic Usage
gau example.com
This command will output a list of URLs associated with example.com. You can redirect this output to a file for further processing:
gau example.com > urls.txt
Advanced Options
GAU offers several options to customize your URL gathering:
-subs- Include subdomains in the search-o- Specify an output file-b- Specify sources to blacklist
Example:
gau -subs -o example_urls.txt example.com
4. Probing URLs with HTTPX
With your list of URLs, it's time to probe them using HTTPX. This tool helps you check the status of each URL, find alive hosts, and extract valuable information.
Basic Usage
cat urls.txt | httpx
This command reads URLs from urls.txt and probes them. HTTPX offers many options to customize its behavior:
-status-code- Show HTTP status codes-content-length- Display content length-title- Display page title-tech-detect- Detect technologies used by the target
Example:
cat urls.txt | httpx -status-code -title -tech-detect -o probed_urls.txt
5. Analyzing the Results
Once you've gathered and probed URLs, the next step is analysis. Look for interesting endpoints, unusual HTTP status codes, or unexpected technologies. These could be indicators of potential vulnerabilities.
Filtering and Sorting
Use command-line tools like grep, awk, and sort to filter and sort the results. For example, to find all URLs with a 200 OK status:
grep "200" probed_urls.txt
6. Tips for Effective Bug Bounty Hunting
Stay Updated: Follow security blogs, forums, and Twitter accounts to stay current with new vulnerabilities and techniques.
Document Everything: Keep detailed notes of your findings, methodologies, and tools used.
Respect Scope: Always adhere to the scope defined by the bug bounty program. Engaging out-of-scope targets can lead to legal consequences.
Report Responsibly: Provide detailed, clear, and concise reports to program administrators. Include steps to reproduce, impact assessment, and possible mitigations.
7. Conclusion
Using GAU and HTTPX together can significantly enhance your bug bounty hunting efficiency. By automating URL gathering and probing, you can focus more on analysis and identifying potential vulnerabilities. Remember to always operate within the legal boundaries and ethical guidelines of the bug bounty programs you participate in.
Happy hunting!
If you enjoyed this guide, feel free to share it with your fellow bug bounty hunters. For more tips and tutorials, follow me on Hashnode and stay tuned for future posts!
Subscribe to my newsletter
Read articles from prasanna directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

prasanna
prasanna
I am a software developer and cybersecurity professional. I am passionate about building secure software and helping organizations protect themselves from cyber threats. I have a strong background in programming, security analysis, and incident response.