Implementing NSG rules for the 3-tier architecture
 Dimple Menghani
Dimple MenghaniTable of contents
- Three-tier architecture is a widely used architecture that separates applications into three different layers:
- Web layer, application layer (business logic), and database layer (storage). Each layer serves a specific purpose and operates independently to improve security, scalability, stability, and flexibility.
- Components of 3-Tier Architecture
- Disadvantages of 3-Tier Architecture
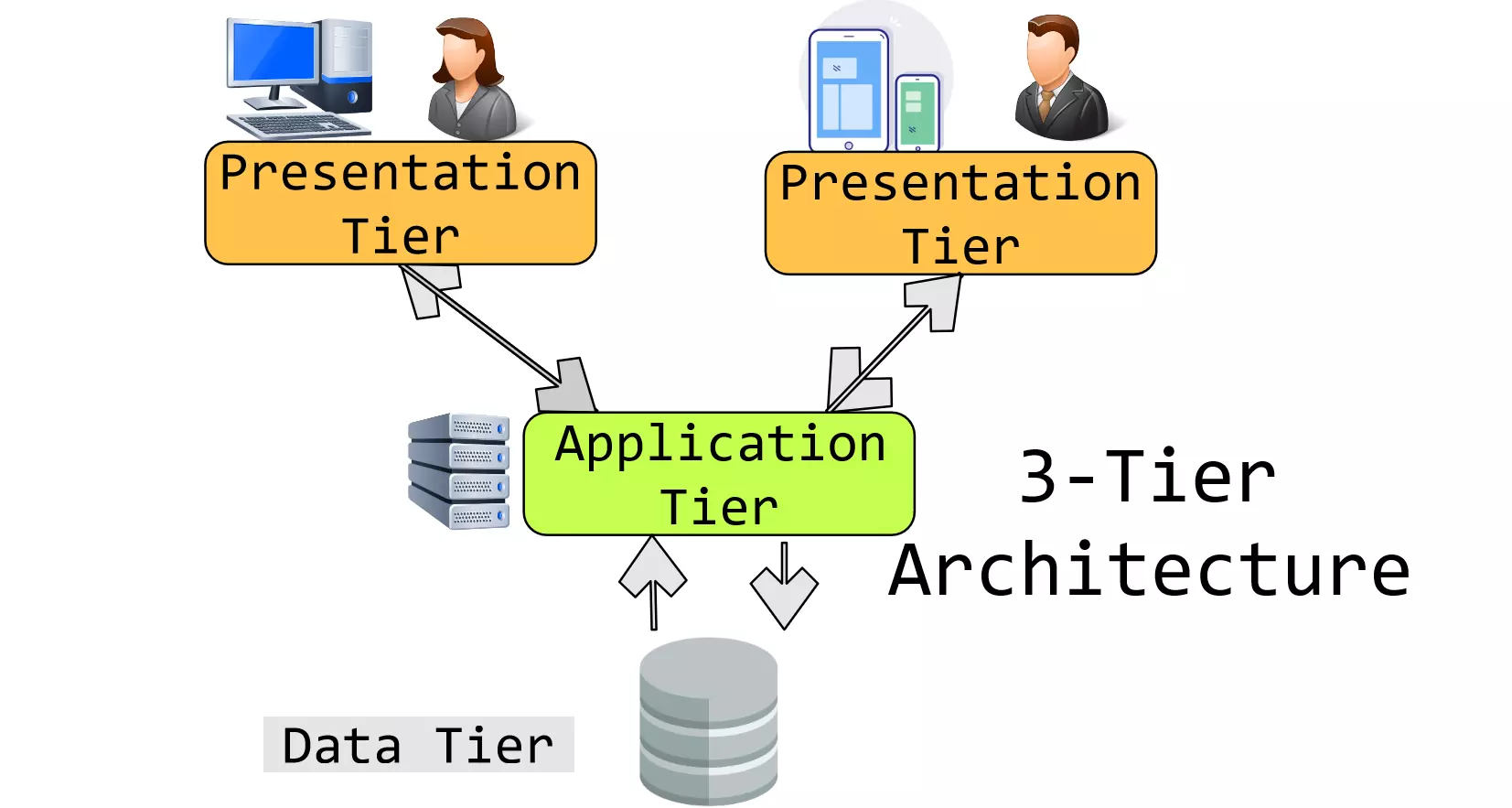
Three-tier architecture is a widely used architecture that separates applications into three different layers:
Web layer, application layer (business logic), and database layer (storage). Each layer serves a specific purpose and operates independently to improve security, scalability, stability, and flexibility.
Components of 3-Tier Architecture
Web Layer:
This layer represents the design and UI components on the client side. Users interact with this layer to send requests through the application layer to the server. It displays the data flow for the users.
Traffic from this layer doesn't reach to database, we apply rules to specify that.
Components: Web interfaces (HTML, CSS, JavaScript), mobile apps, desktop software.
Application layer(business logic):
This layer manages user requests, implements business rules, and user data, it interacts with the data layer as well as the presentation layer.
This layer has no data connection. But it is connected with both the web layer as well as database layer.
Components: Server-side scripting, APIs, middleware, business logic implementations.
Database layer(storage):
This layer is responsible for storing and retrieving data. Manages databases, information systems, or cloud storage.
Internet is not connected to this layer in order to preserve the data breaching. It is also not connected to the Web layer for the same reason.
Components: Database Management Systems (DBMS), data repositories, storage services.
Advantages of 3-Tier Architecture
Scalability: The architecture separates the application process and the data management process, making it easier to evaluate each layer independently
Maintainability: Since changes in one layer have minimal impact on other layers, maintenance and updates become easier.
Flexibility: Architecture allows one layer to be changed or upgraded without affecting other layers
Improved Security: Since the presentation and data layer cannot communicate directly, a well-designed system can act as an internal wall, preventing SQL injection and other malicious attacks.
Disadvantages of 3-Tier Architecture
It is more difficult than the 2-tier client-server model because it is harder to build a 3-tier application than a 2-tier application. Double the communication.
The customer does not store data permanently.
The physical separation of application servers containing business logic functions and database servers containing databases may be something that affects performance.
Implementation Example:
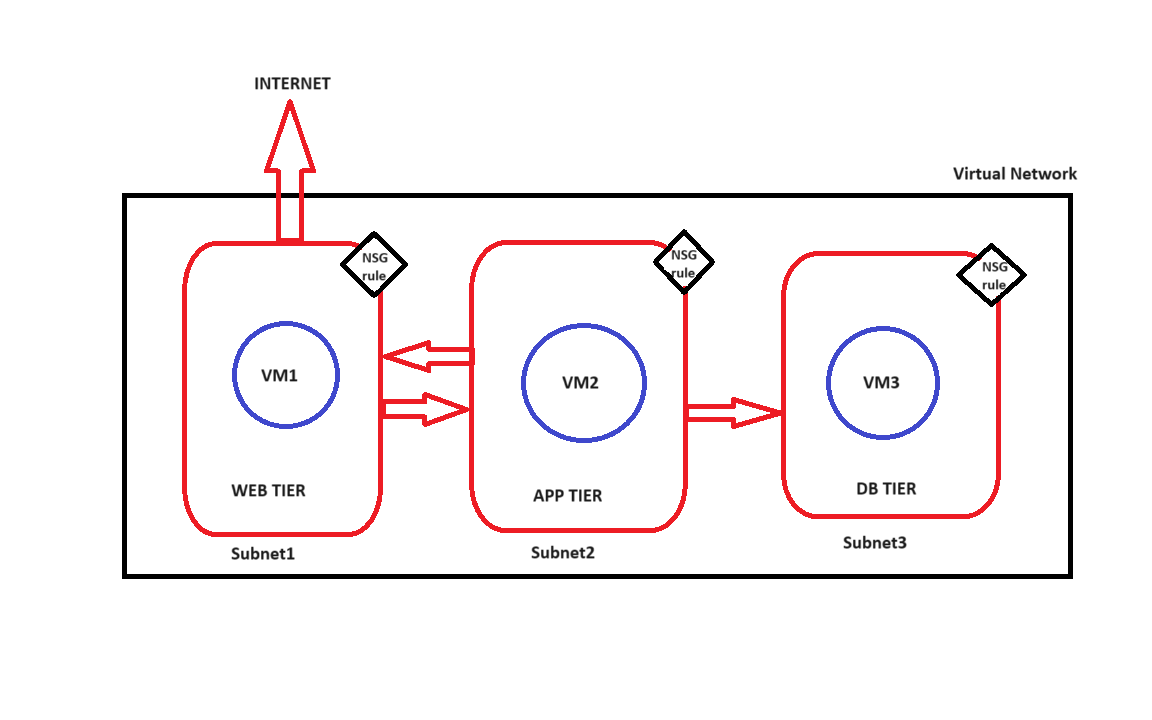
We will be implementing the architecture described above in this blog.
Create Subnets in a Virtual Network (VNet):
Assume we have a VNet with address space
10.0.0.0/16.Web Tier Subnet:
- Address Range:
10.0.1.0/24
- Address Range:
App Tier Subnet:
- Address Range:
10.0.2.0/24
- Address Range:
DB Tier Subnet:
- Address Range:
10.0.3.0/24
- Address Range:
Create a Virtual machine in each subnet respectively.
Create and Assign NSGs:
Web Tier NSG:
- Assign to
10.0.1.0/24
- Assign to
App Tier NSG:
- Assign to
10.0.2.0/24
- Assign to
DB Tier NSG:
- Assign to
10.0.3.0/24
- Assign to
NSG rules should be as follows:
For Web Tie:
Deny traffic to DB tier: Outbound rule
Destination: Private IP of DB tier.
Protocol: Any
Port: Any
Name- According to choice Priority - from 100 to 4096
Source: My IP
For App Tier:
Block internet: Outbound rule
Destination- Service tag->Internet
Source- Service tag -> Virtual Network
Protocol-Any
Port- *
Action- Deny
Name-Deny internet
Priority -from 100 to 4096
For DB tier:
Block internet: Outbound rule
Destination ->Service tag->Internet
Source-> Service tag -> Virtual Network
Protocol-Any
Port- *
Action- Deny
Name-Deny internet
Priority - Priority from 100 to 4096
Deny traffic from DB to Web tier: Outbound rule
Destination-Private IP of Web tier
Protocol-Any
Port-Any
Name- According to choice
Priority - from 100 to 4096 Source: My IP
Action - Deny
Deny traffic from DB to App tier: Outbound rule
Destination- Private IP of Web tier
Protocol- Any
Port-Any
Name- According to choice
Priority - from 100 to 4096 Source- My IP
Action- Deny
These NSG rules are created in NSGs that are attached to each subnet respectively(we can also attach these NSGs with the NIC of the Virtual Machines).
To check if NSG rules are working properly or not we will do that by pinging relevant VMs.
Subscribe to my newsletter
Read articles from Dimple Menghani directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
