Elevating Application Security with Pixee
 Abdellah Kamil
Abdellah Kamil
In the digital age, where software permeates every aspect of our lives, security is a cornerstone of software development. The Audit Management System (AMS)—designed to streamline the auditing process for our company, Cooperative Bank of Oromia, audit department—stood at a crossroads: robust in functionality but vulnerable in security. This blog post chronicles our transformative journey, from a reactive security stance to a proactive, fortified future.
The integration of AppSec tools is a critical component in the development lifecycle, ensuring robust security measures are in place. This blog post offers an in-depth exploration of how these tools work in unison to enhance the security of our software. Let's dive deep!
The Pre-Pixee Era: A Vulnerable Landscape
Our AMS application, a complex system built with Spring Boot for the backend and Angular for the frontend, was developed to automate and manage audit tasks effectively. However, our security measures were rudimentary at best:
AMS Overview:
The application boasted features such as annual planning, audit scheduling, finding registration, real-time tracking, document management, and collaborative tools.
Given the complexity of the project, careful implementation and development are crucial. We designed the app to automate and enhance the accuracy of the auditing process. The audit team will use the application to manage all audit-related tasks efficiently. Auditing within an organization is a highly sensitive operation that can significantly impact its functioning, making robust security measures essential. We prioritize the security of our app to ensure it meets the highest standards.
While many applications require extensive security measures, it is particularly critical for this system due to the sensitivity of audit data. Despite its advanced capabilities, an inadequate approach to security could pose significant risks. Therefore, we'll need meticulously integrated strong security protocols to safeguard the integrity and confidentiality of the audit data.
Despite its advanced capabilities, the lack of a systematic approach to security posed a significant risk, especially given the sensitive nature of audit data.
Lack of AppSec Tools:
In the initial stages of developing the Audit Management System (AMS), our team’s primary focus was on delivering a suite of robust features to enhance the auditing process for the Cooperative Bank of Oromia’s audit department. This focus, however, led to an oversight in application security, as we lacked a dedicated security specialist and our developers, skilled in feature development, were not fully equipped to tackle the complex security challenges inherent in modern software.
Adhering to general best practices and conducting periodic code reviews were our mainstay security measures, but without specialized tools, these methods fell short of addressing the sophisticated threats that could compromise the sensitive nature of audit data. As we progressed, it became evident that integrating dedicated AppSec tools was essential to fortify our system against potential vulnerabilities, ensuring the security of the AMS aligned with its advanced capabilities.
The Turning Point: Discovering AppSec Tools
The realization that our security approach was insufficient led us to seek a solution that could offer more than just vulnerability detection. We needed a tool that could actively contribute to improving our codebase. In our search for application security (AppSec) tools, we found many useful options that could enhance the security of our app. However, most of these tools only provided suggestions, which, while valuable, were not sufficient. We wanted a tool that could do more. That’s when we discovered Pixee:
Pixee Integration Options:
Pixee offered two primary integration options: the Pixee CLI for local development scans and the Pixee GitHub App for continuous integration within our CI/CD pipeline.
We chose the GitHub App for its ability to automate security checks and fixes directly within our development workflow.
Setting Up Pixee:
- The installation process was straightforward. After installing the Pixee GitHub App, we connected it to our repository, and it immediately began scanning our pull requests for vulnerabilities.
Why We Chose Pixee: A Strategic Decision for AMS Security
In the ever-evolving landscape of application security, choosing the right tool can be as critical as writing secure code. When we embarked on our quest to enhance the security of the Audit Management System (AMS), we evaluated several options. Here’s why Pixee emerged as our strategic choice:
I. Automated Code Improvement and Vulnerability Fixes
When we discover the tools, We found Pixeebot isn’t just another security scanner—it’s an intelligent companion that actively contributes to code quality. Here’s how:
Automated Pull Requests: We noticed that Pixee doesn’t stop at flagging vulnerabilities; it takes action. When it detects issues, it automatically creates pull requests with precise fixes. This seamless integration into our development workflow saves time and ensures that security improvements are implemented promptly. We only need to decide whether to accept the pull request or reject the automated suggestion and make our own changes based on the findings. This feature makes a valuable contribution to our development progress.
AI-Driven Insights: Pixee’s AI algorithms analyze code patterns, identify common pitfalls, and suggest improvements. It’s like having a security expert on our team, tirelessly reviewing every line of code. With our developers committing a large number of changes each week, manually analyzing every line within the pull requests is a Herculean task. AppSec tools are not only cost-efficient but also provide precise analysis insights with actionable change suggestions, ensuring our code is robust and secure.
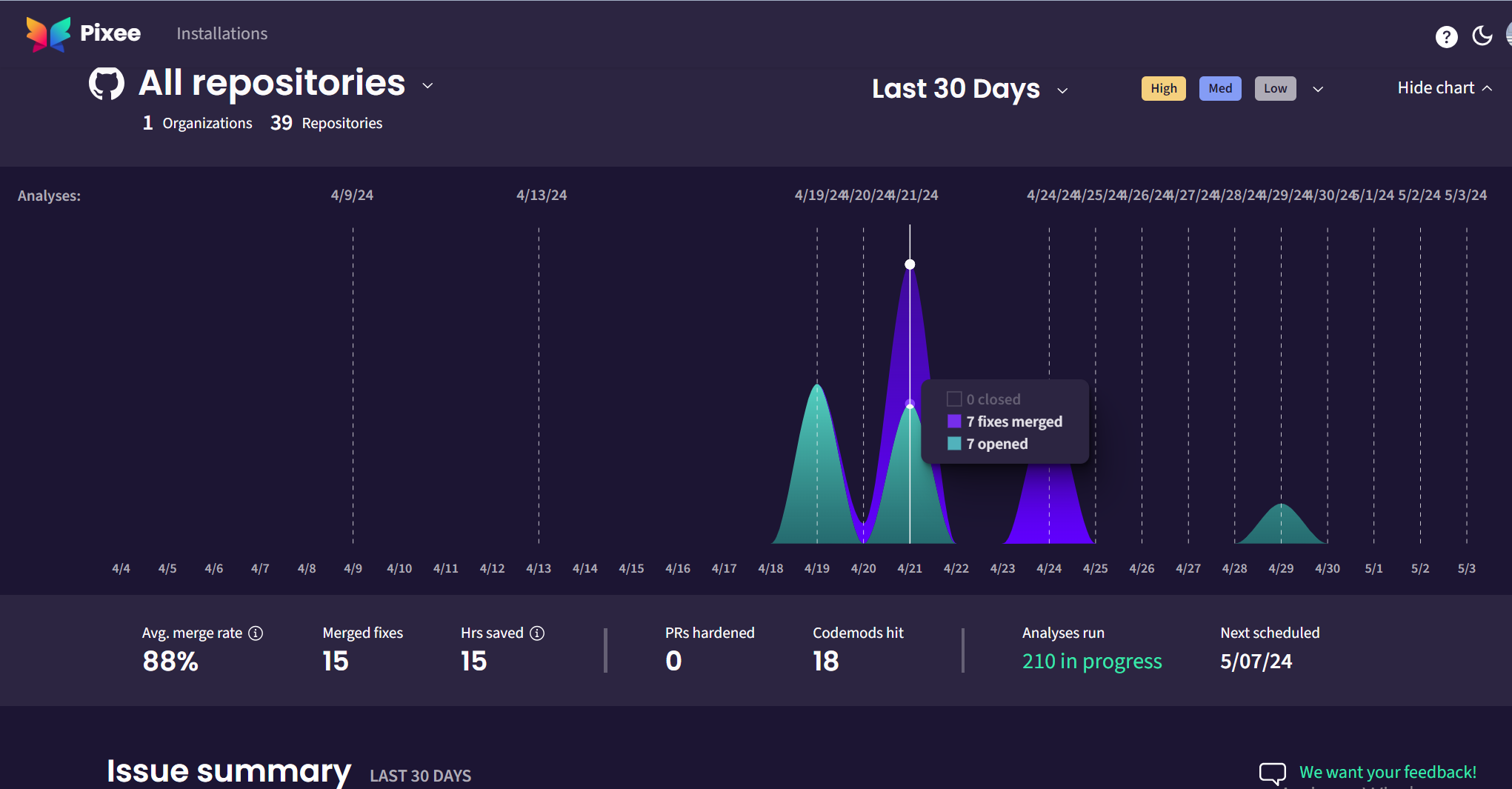
II. GitHub App Integration: A DevOps Dream
Our development process revolves around GitHub, and Pixeebot seamlessly integrates into this ecosystem:
GitHub App: We opted for the Pixeebot GitHub App. Installation was straightforward, and Pixeebot began scanning our pull requests immediately. No manual intervention required—just pure automation.
CI/CD Pipeline Harmony: Pixeebot fits seamlessly into our CI/CD pipeline. It scans code changes during pull requests, ensuring that vulnerabilities are caught before they reach production. Our developers appreciate the real-time feedback.
III. Complementing SonarCloud: A Dynamic Duo
While Pixeebot shines independently, it truly thrives when paired with other tools like Sonar, Semgrep and CodeQL.
Enter SonarCloud:
SonarCloud Scans: SonarCloud dives deep into our codebase, identifying additional security issues. Its rules complement Pixeebot's findings, providing a comprehensive view of our application’s security posture.
Pixeebot-SonarCloud Collaboration: Pixeebot syncs effortlessly with SonarCloud’s results. When SonarCloud detects an issue, Pixeebot steps in with automated fixes. It’s a harmonious collaboration that strengthens our defenses.
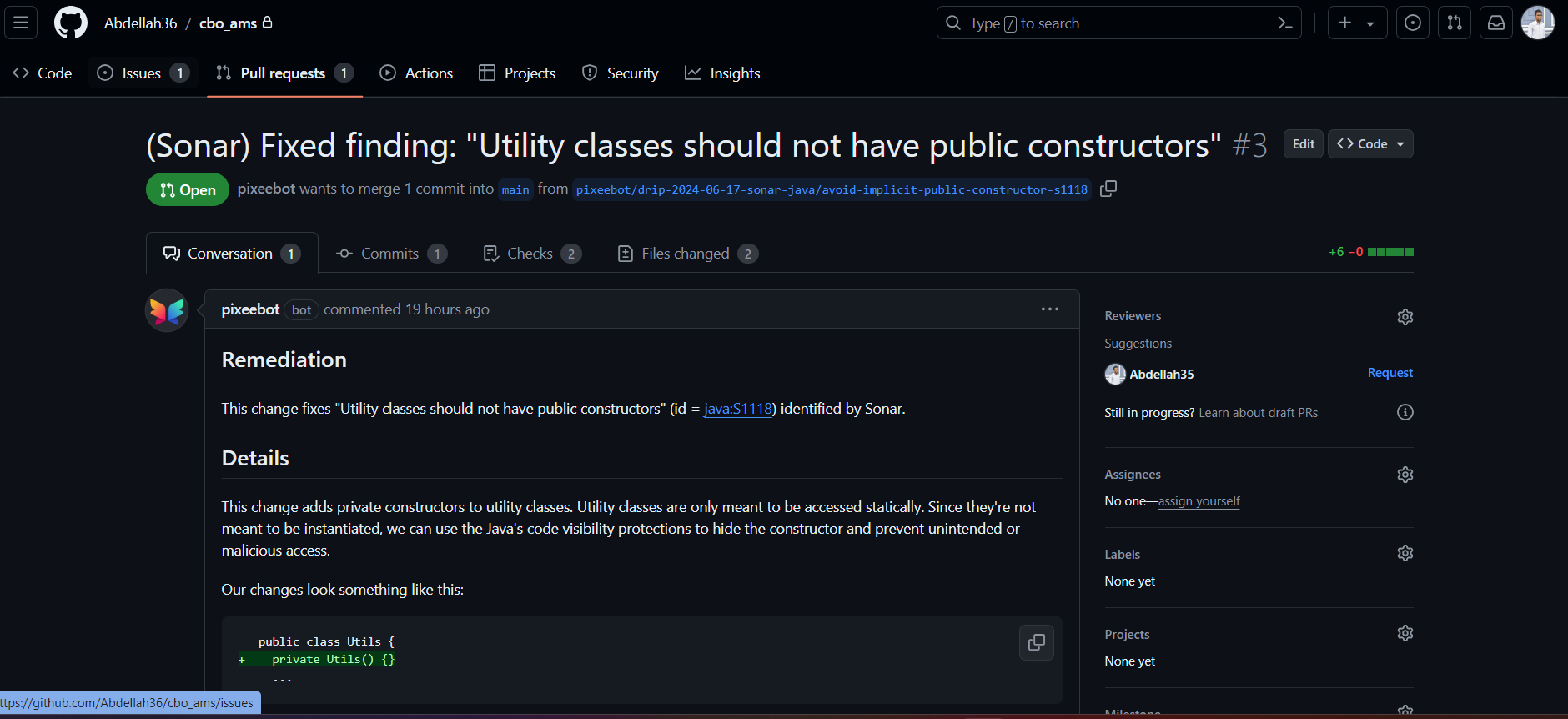
The AMS Security Makeover: Pixee in Action
Assessing the Current State
We began by evaluating the AMS project’s security posture:
Security Configuration: We had basic security measures in place, such as Spring Security for authentication and authorization, but there was a clear need for more comprehensive protection. Additionally, certain configurations, like disabling CSRF protection, can unintentionally introduce vulnerabilities, leading to CSRF attacks.
Development Practices: Our developers used tools like SonarLint for code quality checks, but these were not enough to ensure security.
Pixee’s Impact
Pixee’s introduction marked a significant shift:
Findings Detected: As soon as Pixee was integrated into our workflow, it began its meticulous analysis of the codebase. It quickly proved its mettle by uncovering a range of security issues that had slipped past our traditional reviews. Among these were:
Sandboxed URL Creation Vulnerabilities: Pixeebot identified areas where our application was susceptible to sandboxed URL creation vulnerabilities. These vulnerabilities could allow attackers to exploit the URLs to perform unauthorized actions, compromising the security and integrity of our application.
User Uploaded File Vulnerabilities: Pixeebot also pinpointed risks associated with the handling of user-uploaded files. Without proper checks, such files could be exploited to upload malicious content or scripts, leading to severe security breaches.
Automated Pull Requests: Pixee’s response to these findings was not just to raise alarms but to take proactive measures:
Proactive Fixes: For each issue detected, Pixeebot created automated pull requests with recommended fixes. These pull requests included detailed descriptions of the vulnerabilities and the proposed changes to mitigate them.
Code Improvement Suggestions: Alongside the security fixes, Pixeebot provided code improvement suggestions to enhance the overall quality and maintainability of the codebase.
Review and Merge: The pull requests generated by Pixeebot were designed to be easily reviewed and merged by our development team, ensuring that the fixes could be implemented swiftly and seamlessly.
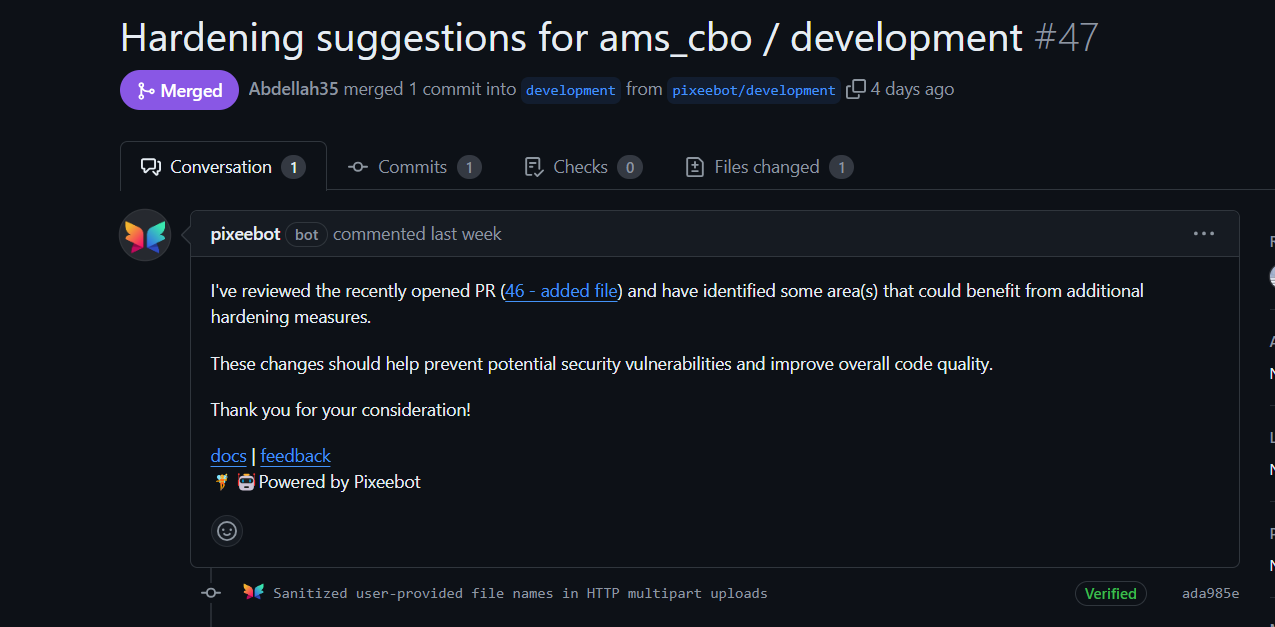
SonarCloud Joins the Party
With SonarCloud integrated, our security analysis deepened:
SonarCloud Scans: SonarCloud’s thorough scans brought additional security concerns to light, complementing Pixeebot’s findings.
Pixeebot Collaboration: Pixeebot seamlessly synced with SonarCloud’s results, automatically generating pull requests for the issues (findings) SonarCloud detected.
Pixee’s Independent Insights
Pixee proved its worth by identifying issues on its own:
User-Provided Filenames: Pixeebot recommended sanitizing filenames in multipart uploads to prevent path traversal attacks. By ensuring that user-provided filenames undergo proper validation and sanitization, we mitigate the risk of malicious actors manipulating file paths and gaining unauthorized access.
Sandboxed URL Creation: Pixeebot highlighted the risk of Server-Side Request Forgery (SSRF) attacks. These occur when an application fetches content from external URLs without proper validation. Pixeebot’s suggestion to sandbox URL creation ensures that our application won’t unwittingly fetch data from potentially malicious sources.
SQL Injection Prevention: Pixeebot also alerted us to the danger of SQL injection. By recommending parameterized queries and input validation, Pixeebot ensures that user inputs are treated as data rather than executable code. This defense mechanism prevents attackers from injecting malicious SQL statements into our database queries.
Reflecting on the Journey
We looked back on our experience with Pixeebot and SonarCloud:
Code Snippet: Below is a real-life example of how Pixeebot’s automated pull requests can enhance the security of our code. In this instance, Pixeebot identified a potential SQL injection vulnerability and suggested a safer approach to constructing our database queries:
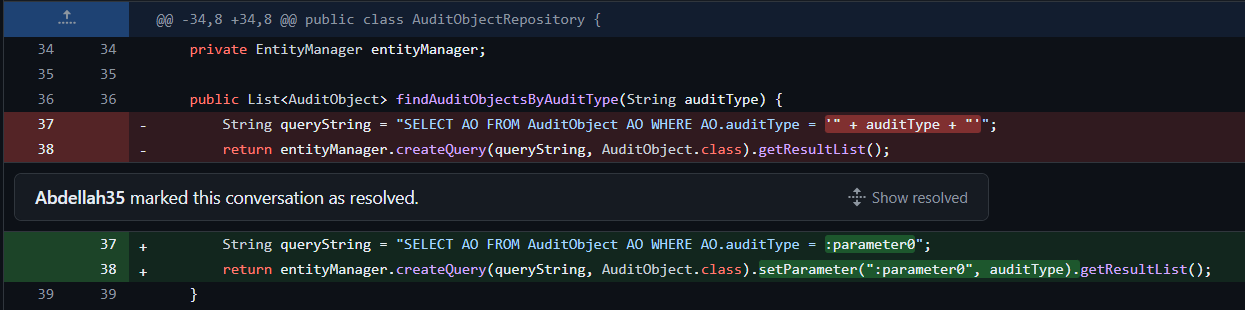
This code snippet illustrates Pixeebot’s suggestion to use parameterized queries, a best practice that significantly reduces the risk of SQL injection by treating user input as a parameter rather than part of the SQL command. By implementing this change, we ensure that our application handles database queries securely, protecting sensitive audit data from malicious exploitation.
Step-by-Step Guide: Installing Pixee for Enhanced Security
So, we’ve talked about the what and the why, and now it’s time for the how. Let’s walk through the process of installing and configuring Pixee.ai, the security ally that’s going to have your code’s back. Here’s a step-by-step guide on how we installed and configured Pixeebot:
Step 1: Installing the Pixeebot GitHub App
Navigate to the Pixeebot GitHub App page: Start by visiting the Pixeebot GitHub App page, here, in the GitHub Marketplace.
Install Pixeebot: Click on the Install button. You’ll be prompted to select which account or organization you want Pixeebot to join forces with.

Configure Repositories: Select the repositories you wish Pixeebot to monitor. For us, it was crucial to include the AMS project repository.
Grant Permissions: Give Pixeebot the necessary permissions to access your private repositories. This step ensures that Pixeebot can scan and create pull requests across all your selected projects.
Step 2: Installing the SonarCloud GitHub App
Find SonarCloud on GitHub Marketplace: Just like Pixeebot, you’ll find SonarCloud in the GitHub Marketplace.
Install SonarCloud: Click on the Install button for SonarCloud and follow the same process as you did for Pixeebot.
Grant Access: Ensure that SonarCloud has access to the repositories you want it to scan. This includes granting permissions similar to those you provided to Pixeebot.
Add Upload Tool Results GitHub Action: Pixeebot fixes issues detected by SonarCloud when repositories have both the Pixeebot and SonarCloud GitHub Apps installed. For public repositories using SonarCloud, Pixeebot retrieves results from sonarcloud.io automatically with no further configuration required from the user. For private repositories using SonarCloud, use the pixee/upload-tool-results-action GitHub Action to synchronize SonarCloud findings with Pixeebot.
By following these steps, we’ve set up a robust security scanning process with Pixeebot and SonarCloud, ensuring that our AMS project is continuously monitored and improved for any security vulnerabilities. 🛠️🔐
And that’s a wrap on setting up your new code guardians, Pixeebot and SonarCloud! If you’re craving more details or need a helping hand through the installation maze, don’t hesitate to check out the official Pixeebot installation documentation here.
Conclusion: A Secure Horizon
The integration of Pixeebot and SonarCloud into the AMS project has been nothing short of revolutionary. Our application is now equipped with a robust, AI-powered defense system that works continuously to identify and fix vulnerabilities.
Automated Security: The combination of Pixeebot and SonarCloud ensures that our code is constantly analyzed and improved, making our application more secure with each commit.
Developer Awareness: Our team has gained a deeper understanding of the importance of automated security tools and how they can significantly reduce the risk of vulnerabilities.
As we continue to develop the AMS application, we do so with the confidence that Pixeebot is safeguarding our code, ensuring that our auditing processes are not only efficient but also secure.
Subscribe to my newsletter
Read articles from Abdellah Kamil directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
