Day 19/40 Days of K8s: ConfigMap and Secret in Kubernetes !! ☸️
 Gopi Vivek Manne
Gopi Vivek Manne
🤔 Need for ConfigMaps and Secrets in Kubernetes?
Let’s just say we have a web application that needs environment variables for configuration. However, managing these variables directly in multiple YAML manifests can become hard and repetitive process. Instead, using ConfigMaps and Secrets provides a standardized approach to store and reference identical environment variables across different manifests seamlessly.
❓How Both are different from each other in k8s?
ConfigMap: Stores the external configuration of the application in the form of key value pairs, inject them at the pod level using different methods.
Ex: non-sensitive data like application configuration.
Secret: Stores the secrets or sensitive data(passwords,tokens) ,inject them at the pod level using different methods.
💁 Scenario
Consider that we have a web application that uses a MongoDB database to store and retrieve data. To ensure proper communication between the web application and the MongoDB Pod, the web app needs specific configuration and credentials.
The ConfigMap will store general configuration data like USERNAME,APP_NAME, APP_ENV, MONGO_HOST and the Secret will store sensitive data like database credentials.
✴ TASK
Now, let's create ConfigMap,Secret,Pod to understand it better.....
- Create the ConfigMap
Stores the external configuration of the application.
kubectl create configmap app-cm --from-literal=firstname=vivek --from-literal=lastname=manne
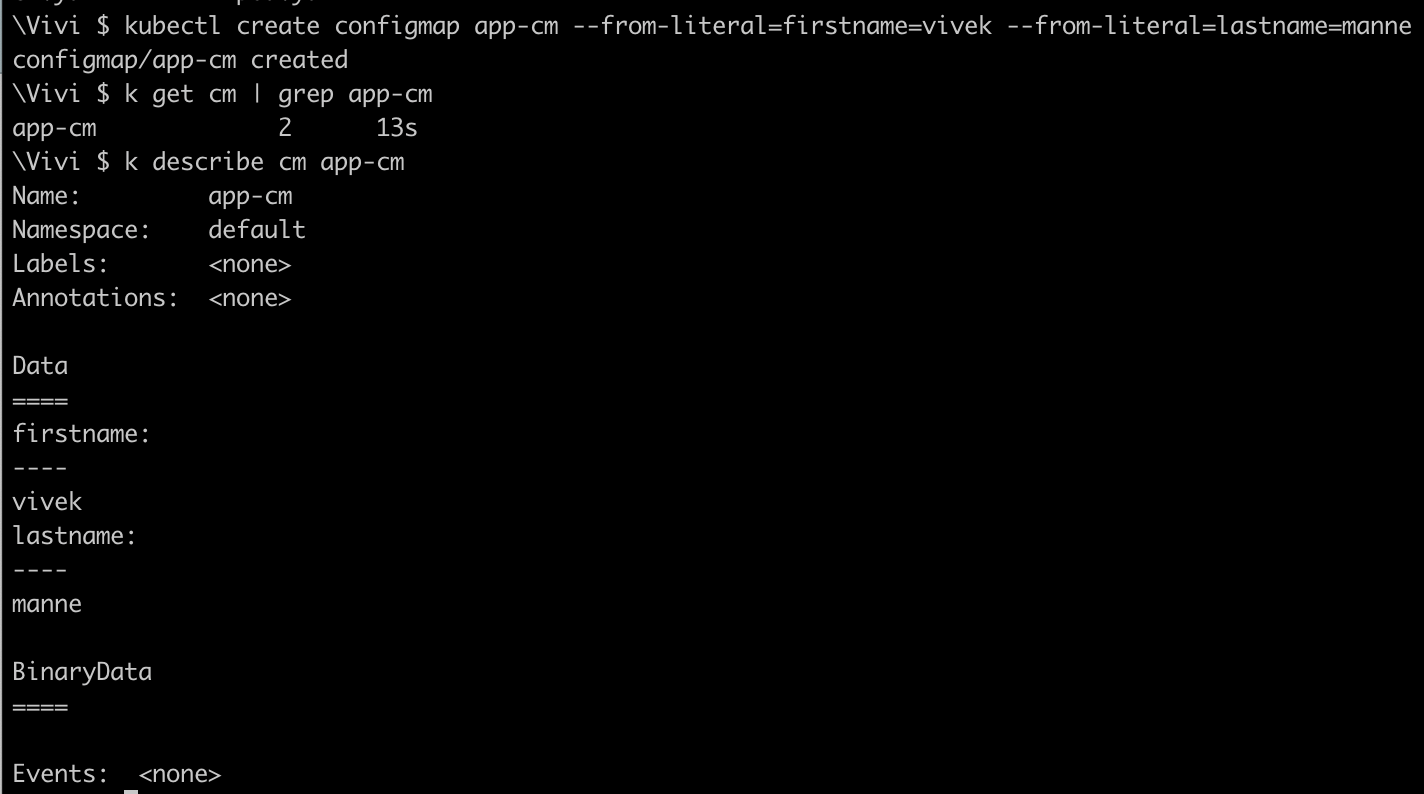
- Create the Secret
Use this imperative command to create generic type of secret.
kubectl create secret generic app-secret --from-literal=username=vivi \
--from-literal=password=CKASeries2024
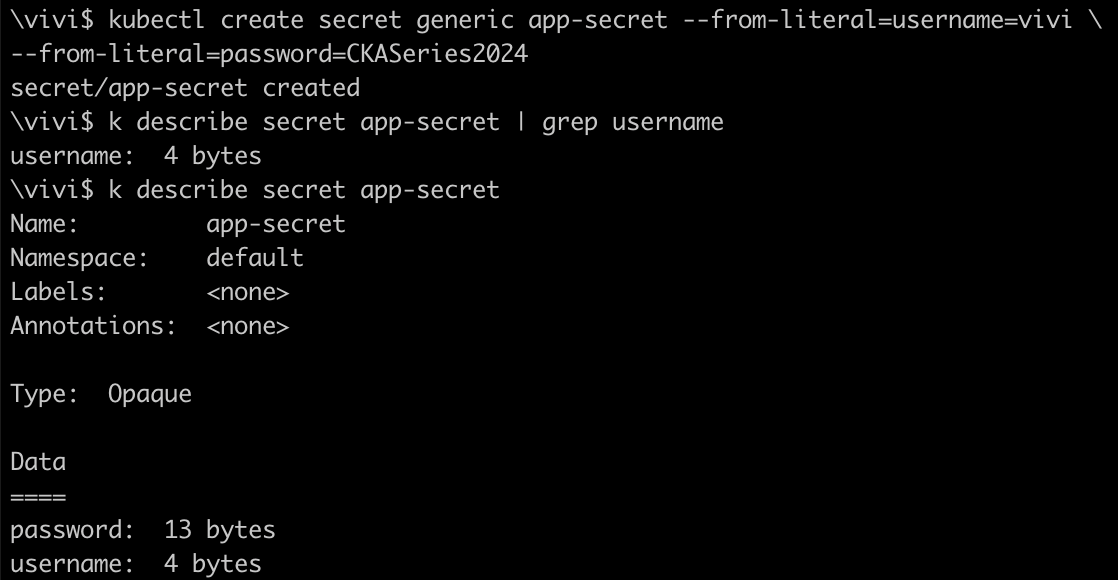
NOTE: By default k8s does the base64 encoding for secrets, anyone who has access to the encoded data can easily decode it but we need to ensure stricter access control,using additional security measures such as encrypting secrets at rest alongside external secret management solutions like Hashicorp vault integration with k8s secrets.
Now, as you can see above that our secrets are base64 encoded.
- Create the pod referencing configMap using attribute configMapKeyRef
apiVersion: v1
kind: Pod
metadata:
name: myapp-pod
labels:
app.kubernetes.io/name: MyApp
spec:
containers:
- name: myapp-container
image: busybox:1.28
env:
- name: FIRSTNAME
valueFrom:
configMapKeyRef:
name: app-cm
key: firstname
- name: LASTNAME
valueFrom:
configMapKeyRef:
name: app-cm
key: lastname
command: ['sh','-c', 'echo The application is running && sleep 3600']
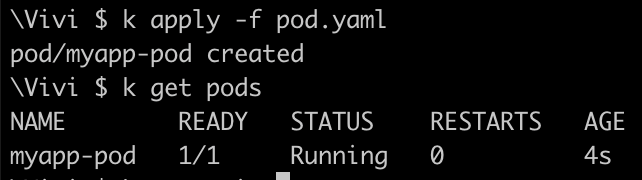
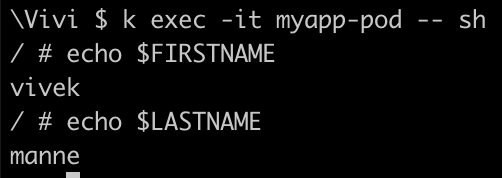
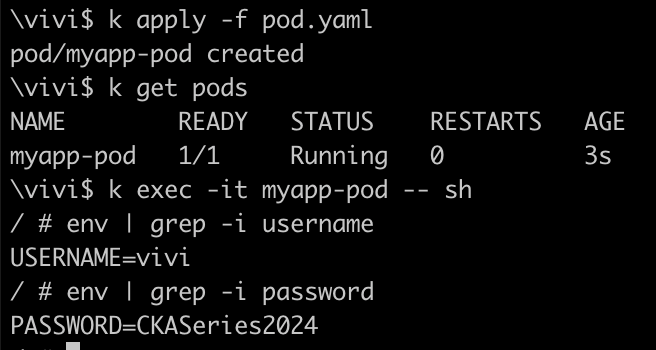
Now, exec into the pod and look for env var
Now, add reference of secret using attribute SecretKeyRef to the pod
Either Configure the existing pod forcefully or delete the pod and recreate once again
apiVersion: v1 kind: Pod metadata: name: myapp-pod labels: app.kubernetes.io/name: MyApp spec: containers: - name: myapp-container image: busybox:1.28 env: - name: FIRSTNAME valueFrom: configMapKeyRef: name: app-cm key: firstname - name: LASTNAME valueFrom: configMapKeyRef: name: app-cm key: lastname - name: USERNAME valueFrom: secretKeyRef: name: app-secret key: username - name: PASSWORD valueFrom: secretKeyRef: name: app-secret key: password command: ['sh','-c', 'echo The application is running && sleep 3600']Now, exec into the pod again and look for env var of secretRef
✴ Different ways to reference configMap data into the pod
Reference env variables inside the pod using valueFrom,
configMapKeyRef,secretKeyRef(As we covered this in the above example)Use
envFromto define all of the ConfigMap's data as container environment variables.Define the ConfigMap name under the volumes section and mount it inside the container at a specified mountPath
✅ Use envFrom to define all of the ConfigMap's data as container environment variables.
Create a Pod using this yaml, here we used configMapRef, secretRef attributes
apiVersion: v1 kind: Pod metadata: name: myapp-pod-1 labels: app.kubernetes.io/name: MyApp spec: containers: - name: myapp-container image: busybox:1.28 envFrom: - configMapRef: name: app-cm - secretRef: name: app-secret command: ['sh','-c', 'echo The application is running && sleep 3600']- Now, exec into the pod and look for env variables
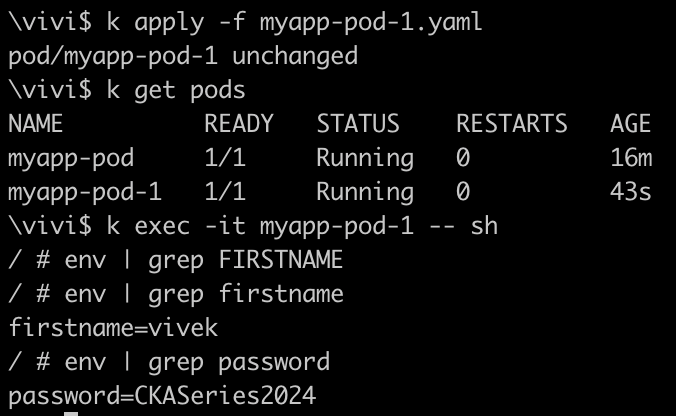
We referenced entire ConfigMap's and Secret's data as container environment variables. The key named firstname from the ConfigMap and key named password from Secret have become the environment variable names in the Pod.
✅ Define the ConfigMap name under the volumes section and mount it inside the container at a specified mountPath
Create a Pod using this yaml,
apiVersion: v1 kind: Pod metadata: name: myapp-pod-2 labels: app.kubernetes.io/name: MyApp spec: containers: - name: myapp-container image: busybox:1.28 volumeMounts: - name: config-volume mountPath: /etc/config - name: secret-volume mountPath: /etc/secret command: ['sh', '-c', 'echo The application is running && sleep 3600'] volumes: - name: config-volume configMap: name: app-cm - name: secret-volume secret: secretName: app-secretNow, exec into the pod and look for env variables inside the container paths we set.
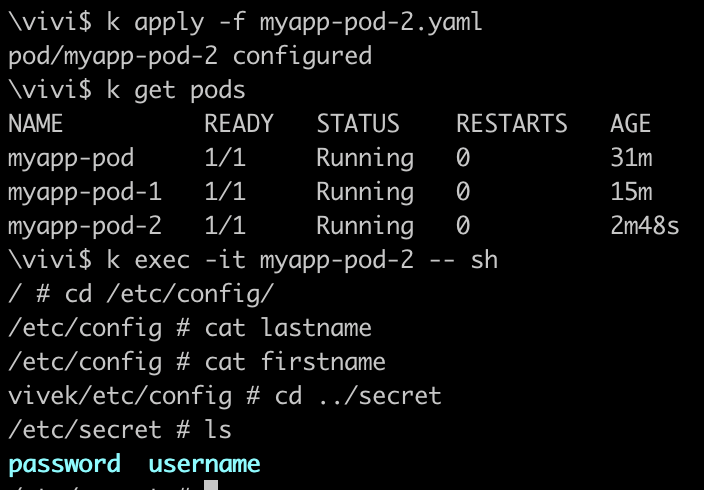
All of these methods provides a different way to utilize ConfigMaps,Secrets within the Pod, depending on our specific requirements.
#Kubernetes #ConfigMap #Secret #40DaysofKubernetes #CKASeries
Subscribe to my newsletter
Read articles from Gopi Vivek Manne directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Gopi Vivek Manne
Gopi Vivek Manne
I'm Gopi Vivek Manne, a passionate DevOps Cloud Engineer with a strong focus on AWS cloud migrations. I have expertise in a range of technologies, including AWS, Linux, Jenkins, Bitbucket, GitHub Actions, Terraform, Docker, Kubernetes, Ansible, SonarQube, JUnit, AppScan, Prometheus, Grafana, Zabbix, and container orchestration. I'm constantly learning and exploring new ways to optimize and automate workflows, and I enjoy sharing my experiences and knowledge with others in the tech community. Follow me for insights, tips, and best practices on all things DevOps and cloud engineering!