Physical Controls in Information Security
 b1d0ws
b1d0ws
Introduction
When it comes to Information Security, most people probably think immediately of logical concepts like network defense through firewalls, data protection through secure applications, remote access restrictions to servers, and others.
However, much is forgotten about the physical controls for these elements, which should be fundamentally applied in any company, considering that if an attacker can physically touch your devices, they can gain access to them.
Some common physical controls that mitigate threats are alarm systems, locks, surveillance cameras, ID cards, and security guards.
The first step to preventing physical access is implementing a site security plan. Site security analyzes all the facilities used by an organization and implements a plan based on the threats and risks relevant to each specific location.
Facility Security
Some organizations use industrial camouflage to protect and hide them from attackers. A common example is the discreet locations companies choose for their data centers.
Many facilities use fences as the first line of defense. Fences act as a deterrent, making access to a facility seem challenging and serving as a real physical defense.
A second common physical control is the placement of protective barriers. Bollards are posts or other obstacles, like those shown below, that prevent vehicles from crossing a certain area. They can look like posts, pillars, or even plants for more discreet security. Some are designed to be removable or mechanically operated to be raised and lowered as needed.

Cameras and Sensors
Camera systems are common methods of physical security control, allowing security professionals and others to observe what is happening in real-time and capture video footage of areas and locations for future use when conducting investigations.
Motion recognition cameras are activated only when motion occurs, thus saving disk space for storing recorded videos.
Object detection cameras and similar technologies can detect specific objects or have specific areas that they monitor for possible changes.
Another type of camera is a closed-circuit television (CCTV) which displays what the camera is seeing on a screen in real-time.
Door Locks
Door locks can use keys, pins, wireless signals, or biometrics. They are one of the most common physical security controls you will find. A cable lock is a common solution to ensure that devices like computers or other hardware are not removed from a location.
Mantraps
Some organizations use access control vestibules (often called mantraps) as a way to ensure that only authorized individuals have access to secure areas and that attackers do not use piggybacking/tailgating attacks to enter places where they should not be.
This system is very similar to the metal detectors used in banks.
Piggybacking and tailgating involve "hitching a ride" with someone who has permission and access, meaning trying to enter a specific area unnoticed by passing along with an authorized person.
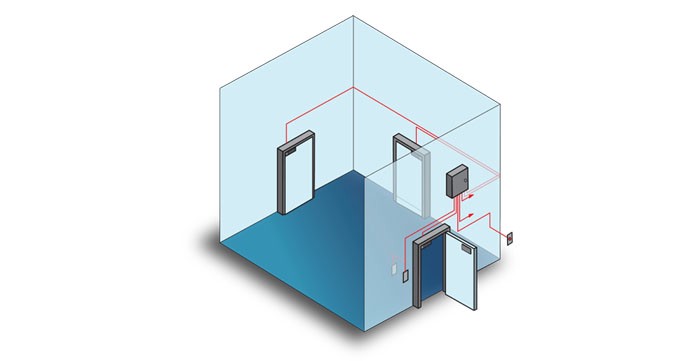
Biometric Readers
They rely on a person's physical characteristics to identify them, with the most common parts being: fingerprint, eyes, and blood vessels in the hand. Biometrics is considered "something you are".
Biometric systems have evaluations on success and failure rates based on 3 metrics called FAR, FRR, and CER, which we will not go into detail about in this article.
Fire Suppression
Fire suppression systems are an important part of site security and help with resilience by reducing the potential for catastrophic fires, protecting employees, data, and buildings of an organization.
There are various types of extinguishers, each specific to a situation. Usually, Chemical Powder and Carbon Dioxide extinguishers are recommended for Class C fires (energized electrical equipment).
Sprinkler (Automatic Shower)
A sprinkler is a device commonly used in firefighting that acts automatically. It consists of a "frame" and a sensitive element called a bulb.
Wet Pipe Sprinkler Systems — The pipes are filled with water up to the sprinkler head and are just waiting for the bulb to melt or break.
Dry Pipe Sprinkler Systems — The pipes are filled with pressurized air and only push water in when needed to fight the fire.
Special Protection Sprinkler Systems — The piping system is filled with gas (HALON, FM-200, or CO2) instead of water.
Shielding
Shielded Twisted Pair (STP) adds a layer of shielding inside the cable to prevent possible damage and modifications.
Faraday Cage — Shielding installed around an entire room that prevents electromagnetic energy from entering or leaving, blocking electromagnetic fields and radio frequency from the room.
TEMPEST — A US government standard for the level of shielding required in a building to ensure that emissions and interference cannot enter or leave the facility. These facilities are also resistant to EMPs (electromagnetic pulses).
Physical Access Control System (PACS)
Components and protocols that facilitate the centralized configuration and monitoring of security mechanisms within offices and data centers. PACS can be implemented as part of a building automation system or as a separate system.
This system grants access to employees who work at or visit a location by electronically authenticating their credentials. Although PACS are IT systems, they must be designed, deployed, and operated in cooperation with the Physical Security teams to successfully meet the company's needs.
Others
Lighting plays a role in both exterior and interior security, being used to deter intruders or to help employees feel safer.
Badges can play several roles in physical security. Besides being processed for entry access via magnetic stripe and radio frequency (RFID) systems, badges often include a photo and other information that can quickly allow staff and guards to determine if the person is who they say they are, what areas and access they should have, and if they are an employee or a guest.
Systems and alarms are used to detect and alert about issues, including unauthorized access, environmental problems, and fires.
Security guards are used in areas where human interaction is necessary or useful. Visitor logs are a common control, used in conjunction with guards, because they provide evidence of who was in the company at a given time in case something suspicious happens.
Enhanced Security Zones and Secure Areas
A hot aisle/cold aisle layout places air intakes and exhausts in alternating aisles to ensure proper airflow, allowing data center designers to know where to supply cold air and where the exhaust needs to be placed.
Network security also plays a role in secure areas, including the use of a screened subnet (often called a demilitarized zone [DMZ]). Subnets rely on security devices like firewalls to provide segmentations that limit the flow of incoming and outgoing traffic, thus keeping higher security zones safe.
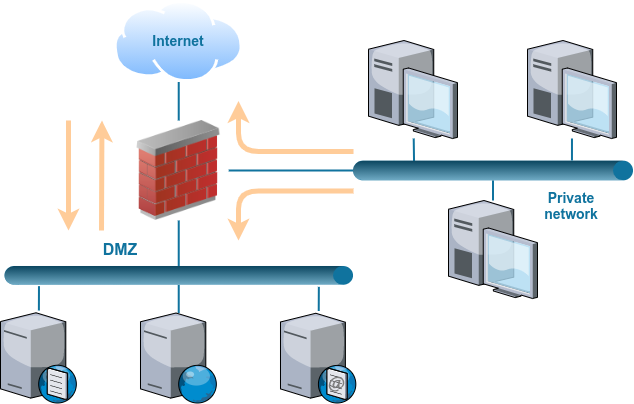
Air-gaps are architectures used to physically segment networks, thus preventing connectivity between them.
Government facilities and other high-security installations may use locks, secure conduits and cable channels, tamper-evident seals, and even cables that can detect access attempts through changes in pressure, changes in shielding conductivity, among other techniques.
Secure Data Destruction
When data reaches the end of its usefulness, the destruction of the media that contains it is an important physical security measure. Secure destruction helps prevent issues with data and information, including intentional attacks like "dumpster diving", as well as unintentional losses through the reuse of media, systems, or other data storage devices.
Methods of Data Destruction
Burning
Most often done in a high-temperature incinerator. Mainly used for paper records, although some incinerators can handle electronic devices. Usually done off-site through a third party, it leaves no recoverable materials.
Shredding
Can be done on-site, supporting paper or devices using an industrial shredder. Traditional paper shredders may allow document recovery, even from cross-cut shredded documents. For high-security environments, burning or pulping may be necessary.
Pulping
Breaking paper documents into wood chips, removing the ink. The materials can be recycled. Completely destroys the documents to prevent recovery.
Pulverizing
Breaking devices into pieces to prevent recovery. The size of the output material can determine the potential for data recovery. Typically, pulverizing results in very small fragments.
Degaussing
Magnetically erases data from tapes and traditional magnetic media like hard drives. Only effective on magnetic media, it will not work on SSDs, flash media, optical media, or paper.
Physical destruction is the most secure way to ensure data destruction, but non-destructive options are often desirable in a commercial environment to allow for the reuse of media or devices.
A final option that many organizations choose to implement for secure destruction is the use of third-party solutions.
Conclusion
It is extremely important that physical access to company data or equipment containing this information is properly protected. If a malicious attacker gains access, irreversible damage could occur.
As mentioned above, there are many controls to ensure that this access is done safely and reliably, whether with automatic or manual controls, or even a mix of both.
It is also crucial to ensure that media no longer in use is properly disposed of to prevent the data contained in them from falling into the wrong hands.
Subscribe to my newsletter
Read articles from b1d0ws directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
