Introduction to MITRE ATT&CK: A Starter Guide
 Harshal Shah
Harshal Shah
In today's digital world, cyberattacks are a constant threat. They can target individuals, businesses, and even critical infrastructure. As cyberattacks evolve and become more sophisticated, security professionals need powerful tools to combat them. Enter the MITRE ATT&CK framework, a game-changer in the cybersecurity landscape.
What are Cyberattacks?
The blog post begins by explaining how cyberattacks have evolved alongside digital systems. As digital systems have become more complex, so too have cyberattacks, making them more challenging to detect and prevent.
What is MITRE?
MITRE is an organization that focuses on developing innovative solutions for national security. Their areas of expertise include cybersecurity, aviation, artificial intelligence, and healthcare.
What is the MITRE ATT&CK Framework?
The MITRE ATT&CK framework (ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge) is a globally accessible knowledge base that details the tactics and techniques used by cyber attackers. This continuously updated framework allows for systematic analysis of cyberattacks, enabling a deeper understanding of attacker behavior at each stage of the attack lifecycle.
Why is the MITRE ATT&CK Framework Important in cyber security field?
The MITRE ATT&CK framework is an essential tool for cyber security professionals because it provides a comprehensive roadmap of cyberattacks. This roadmap helps professionals:
Identify the actions attackers take at each attack stage.
Develop and implement effective attack detection and mitigation techniques.
Map cyberattacks to understand the overall attack scope.
Generate detailed reports on attack incidents.
Archive attack details for future reference and analysis.
Proactively research potential future attacks to develop preventative measures.
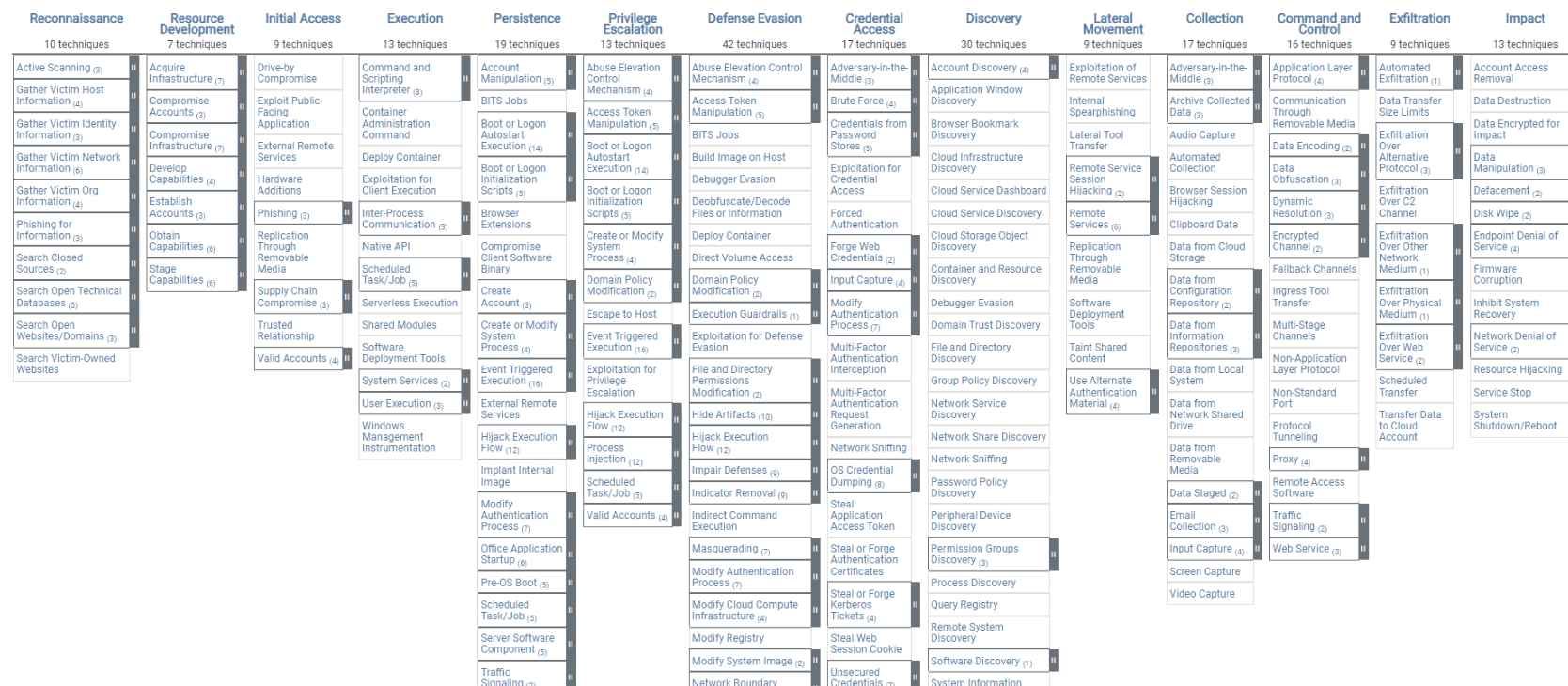
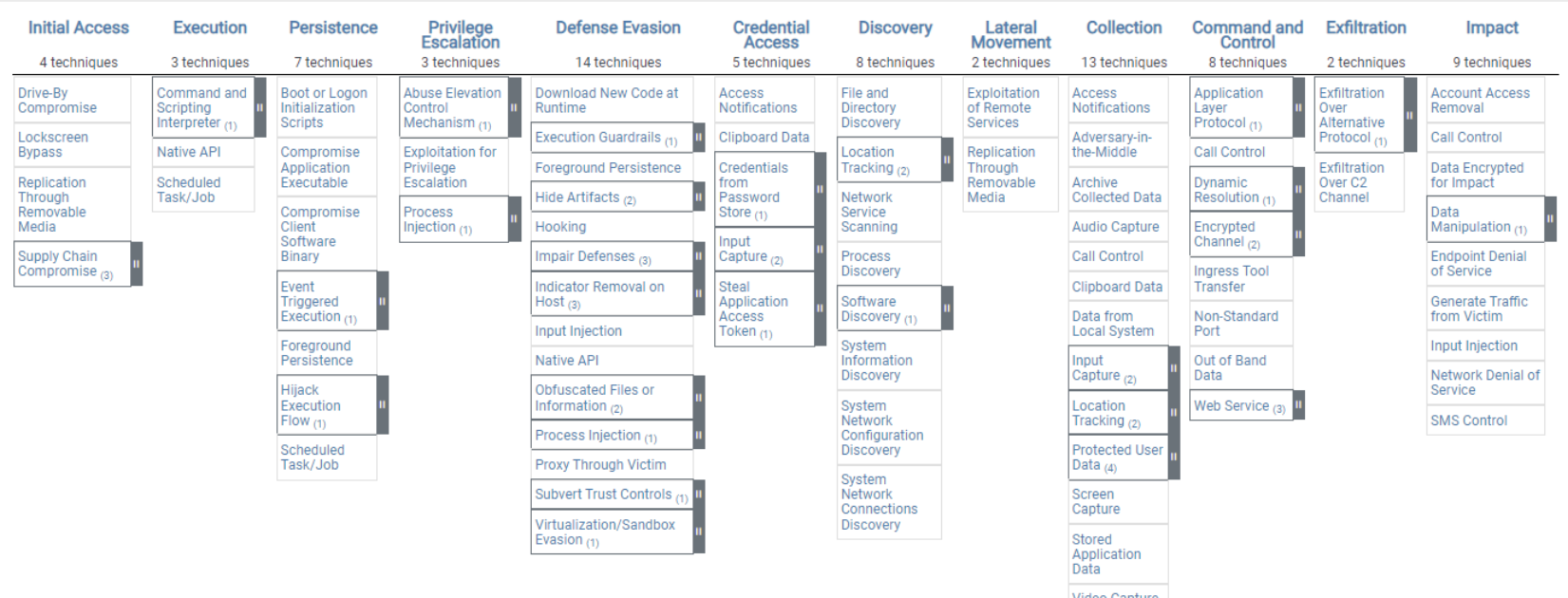
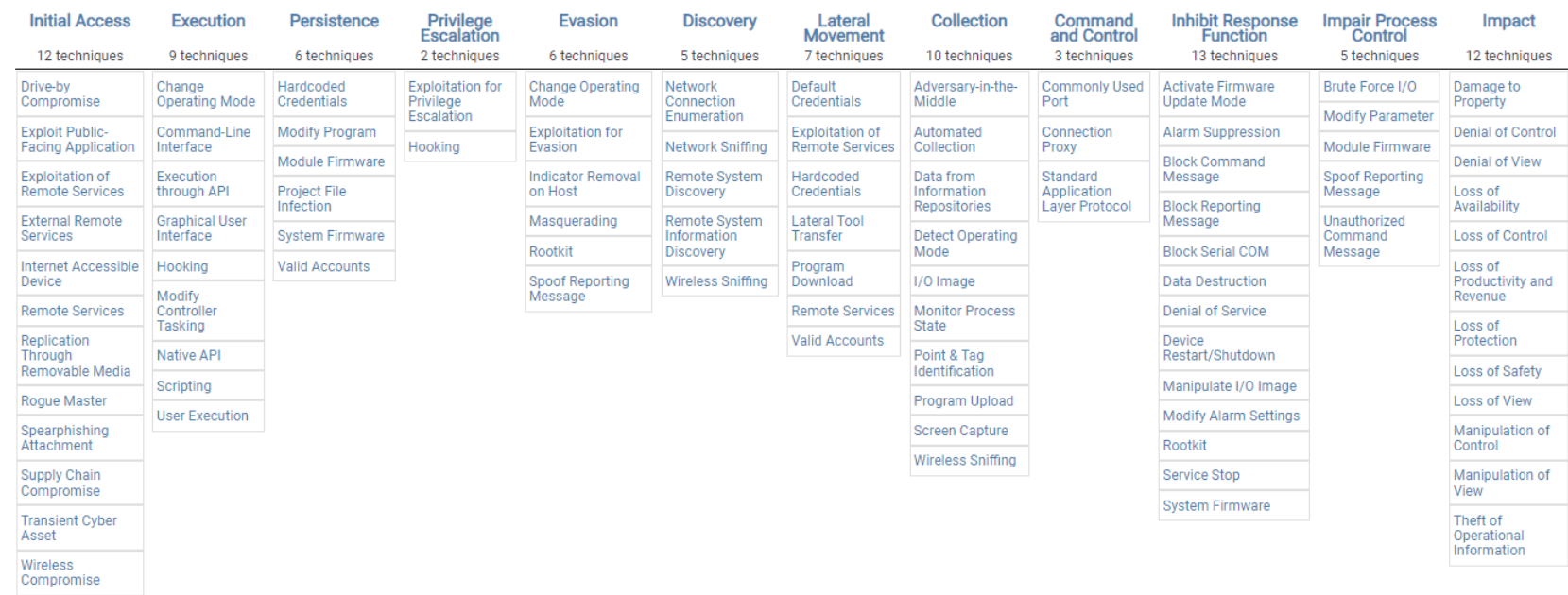
Understanding the MITRE ATT&CK Matrix
The MITRE ATT&CK matrix is a visualization tool that categorizes attacker methods. There are three main matrices, each tailored to a specific platform type:
Enterprise Matrix: This is the most comprehensive matrix, encompassing a wide range of digital systems typically found in large organizations.
Mobile Matrix: This matrix focuses on the cybersecurity of mobile devices, including both personal and corporate devices.
ICS Matrix: Designed for industrial control systems, this matrix provides insights for securing these critical systems.
Each matrix can be further broken down into sub-matrices for even more granular analysis.
Key Components of the MITRE ATT&CK Framework
The blog post dives deeper into the key components of the MITRE ATT&CK framework:
Tactics: These represent the attacker's goals and motivations throughout the attack. Each matrix lists tactics at the top row, providing a high-level overview of attacker objectives.
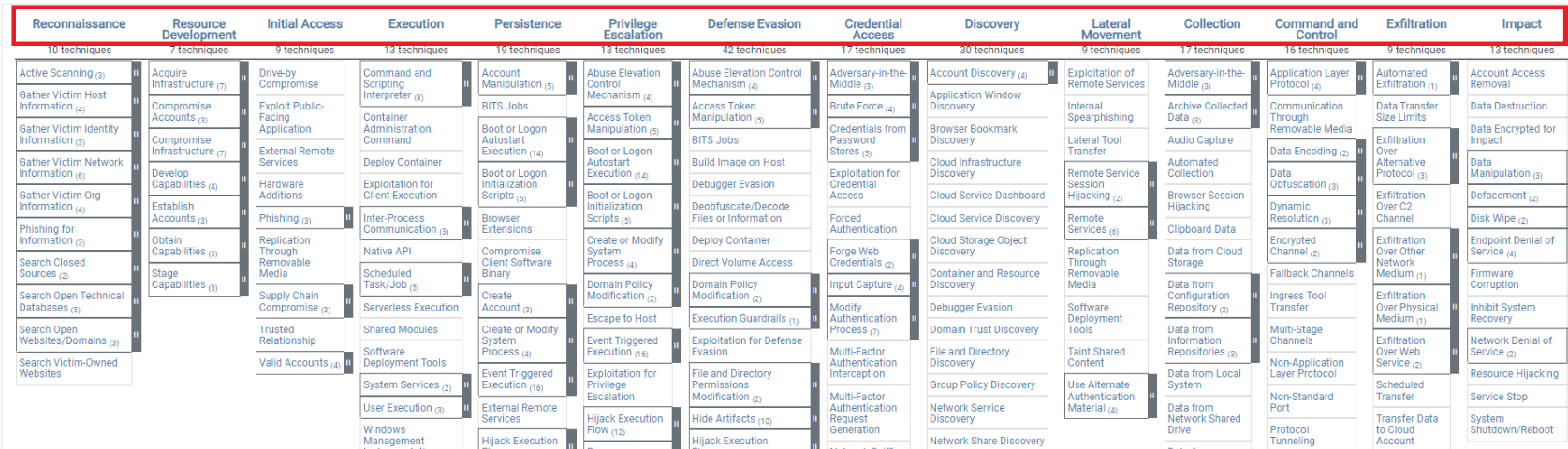
Techniques and Sub-Techniques: Techniques detail the specific methods attackers use to achieve their goals. Sub-techniques provide further granularity within specific techniques.
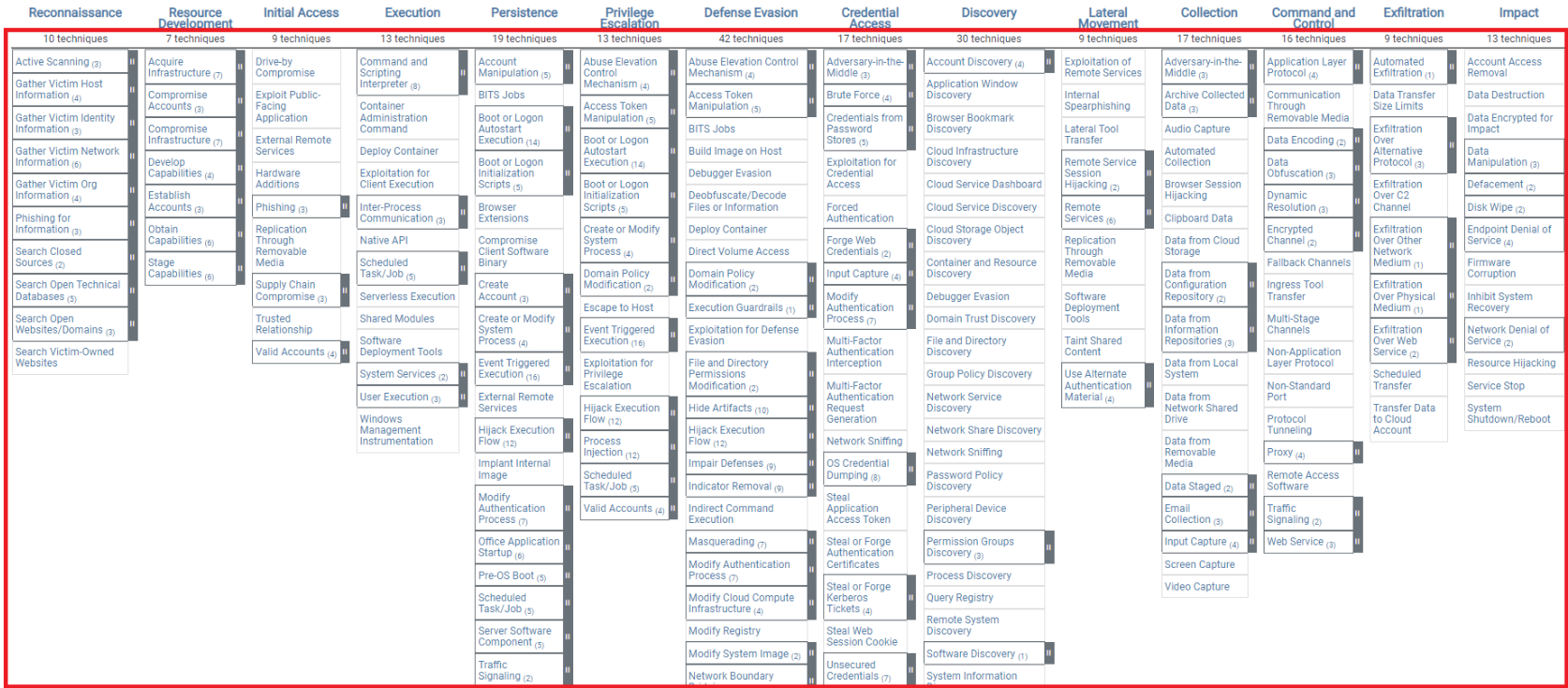
Procedure: The procedure consists of usage examples of techniques/sub-techniques. It simply shows which tool/software was utilized during the implementation of the technique. In other words, it is the explanation of the practical information on the use of the technique.
Mitigations: Mitigations are countermeasures that can be implemented to defend against the techniques listed in the framework.
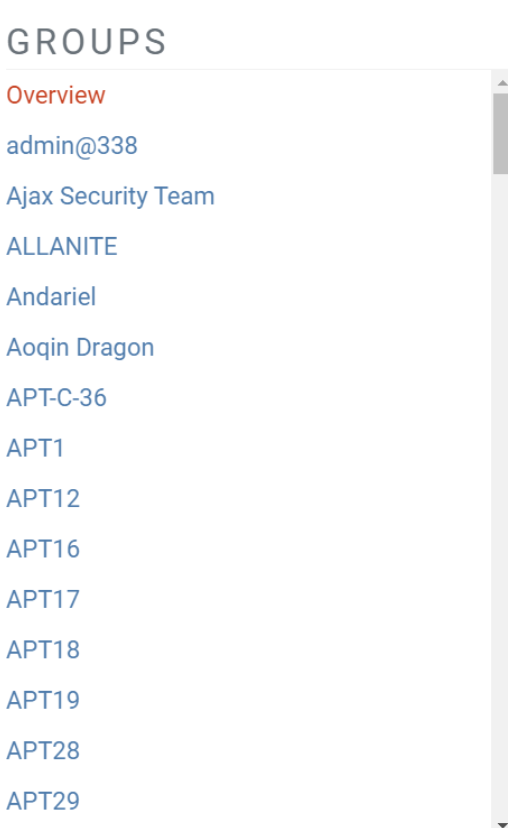
Groups: The framework also includes information about Advanced Persistent Threat (APT) groups. This helps analysts identify which groups are targeting specific systems and the techniques they employ.
Software: The framework catalogs various software programs used by APT groups in their cyberattacks.
Conclusion
The MITRE ATT&CK framework empowers SOC analysts with a wealth of knowledge about attacker behavior. By understanding the framework and its components, analysts can significantly improve their ability to detect, prevent, and respond to cyberattacks.
Additional Resources
The blog post concludes by providing links to the official MITRE ATT&CK website, where you can find the latest information on the framework, including:
Enterprise Matrix: https://attack.mitre.org/matrices/enterprise/
Mobile Matrix: https://attack.mitre.org/matrices/mobile/
ICS Matrix: https://attack.mitre.org/matrices/ics/
Techniques: https://attack.mitre.org/techniques/enterprise/
Mitigations: https://attack.mitre.org/mitigations/enterprise/
Groups: https://attack.mitre.org/groups/
Software: https://attack.mitre.org/software
Subscribe to my newsletter
Read articles from Harshal Shah directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Harshal Shah
Harshal Shah
Navigating the convergence of cybersecurity, DevOps, and cloud landscapes, I am a tech explorer on a mission. Armed with the prowess to secure digital frontiers, streamline operations through DevOps alchemy, and harness the power of the cloud, I thrive in the dynamic intersection of these domains. Join me on this journey of innovation and resilience as we sculpt a secure, efficient, and future-ready tech realm.