Understanding End-to-End Encryption
 Ahmad W Khan
Ahmad W Khan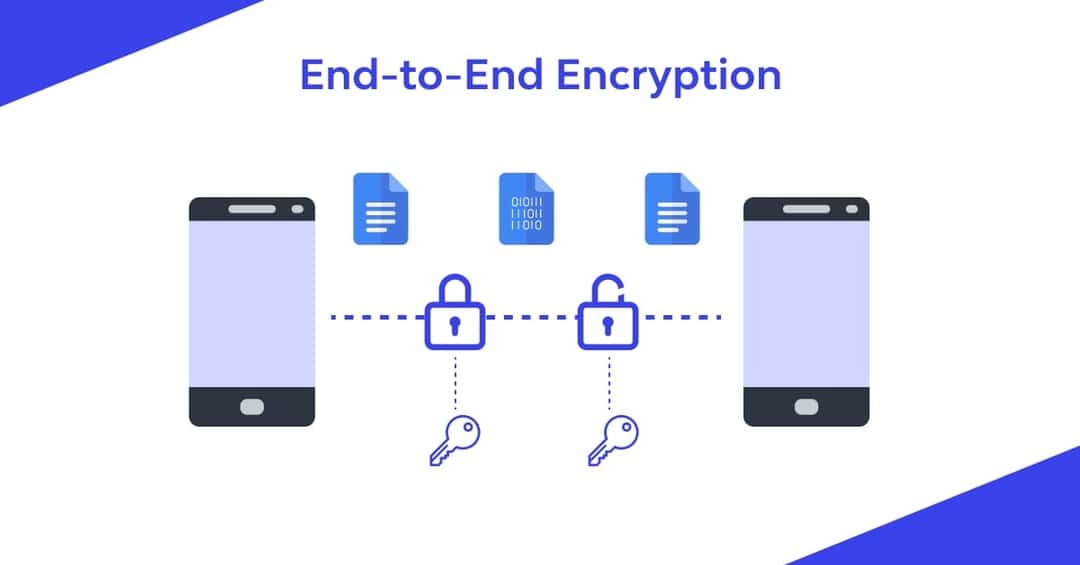
In an era where digital communication has become integral to our daily lives, the need for secure and private messaging has never been more critical. End-to-end encryption (E2EE) stands as a formidable guardian of privacy, ensuring that only the intended recipients can read the transmitted data. WhatsApp, a widely used messaging application, has adopted robust E2EE features to protect user communication. However, the acquisition of WhatsApp by Facebook and its subsequent monetization strategies have raised significant concerns about user privacy and data exploitation. This article explores the technical intricacies of E2EE, its implementation in WhatsApp, and the broader implications for user privacy, emphasizing the adage that "if you are not paying for the product, you are the product."
A Decade in the Trenches
Having spent over a decade in the tech industry, with a heavy focus on back-end, and substantial experience in building large-scale ad tech and mar tech products, I’ve seen firsthand how user data is collected, analyzed, and monetized. The intricacies of E2EE, while robust, are just one part of the larger puzzle of digital privacy. It’s fascinating (and sometimes terrifying) to see how much information can be gleaned from metadata alone. So, while you might enjoy the convenience of free services, it's essential to remain cognizant of the cost to your privacy.
What is End-to-End Encryption?
End-to-end encryption (E2EE) is a secure communication method that prevents third parties from accessing data while it is transferred from one end system to another. The data is encrypted on the sender's device and only decrypted on the recipient's device, ensuring that only the communicating users can read the messages. This method ensures that communication remains private and secure from potential eavesdroppers, including the service providers themselves.
Diffie-Hellman Algorithm
The core mechanism behind E2EE involves cryptographic algorithms and protocols. One of the foundational algorithms in this context is the Diffie-Hellman (DH) key exchange. This method allows two parties to establish a shared secret over an insecure channel without any prior sharing of keys.
Mathematical Foundations
The Diffie-Hellman key exchange relies on the properties of large prime numbers and modular arithmetic. Here's a detailed explanation:
Public Parameters:
- Both parties agree on a large prime number
pand a baseg(a primitive root modulop).
Private Keys:
- Each party generates a private key (
aandb), which are large random numbers.
Public Keys:
They compute their public keys:
A = g^a mod pB = g^b mod p
Exchange and Computation:
These public keys are exchanged over the insecure channel.
Each party then computes the shared secret key using their private key and the other party's public key:
Sender computes
s = B^a mod pReceiver computes
s = A^b mod p
Both calculations yield the same shared secret
sdue to the properties of modular arithmetic.
Example
Consider Alice and Bob who want to establish a shared secret key:
They agree on a large prime
p = 23and baseg = 5.Alice chooses a private key
a = 6and computes her public keyA = 5^6 mod 23 = 8.Bob chooses a private key
b = 15and computes his public keyB = 5^15 mod 23 = 19.They exchange public keys. Alice computes the shared secret
s = 19^6 mod 23 = 2.Bob computes the shared secret
s = 8^15 mod 23 = 2.
Both share the same secret s = 2.
Message Encryption: Symmetric Encryption
Once the shared secret key is established, symmetric encryption algorithms like AES (Advanced Encryption Standard) are used to encrypt messages.
Advanced Encryption Standard (AES)
AES is a symmetric encryption algorithm that encrypts data in fixed-size blocks (128 bits) using keys of varying lengths (128, 192, or 256 bits). It operates on a series of rounds that include substitution, permutation, and mixing of the data and key to produce ciphertext.
Example
A message "Hello, World!" is encrypted using AES with the shared secret key, producing ciphertext that is transmitted over the network. Only the recipient, who has the corresponding secret key, can decrypt the message back into "Hello, World!".
Authentication
To ensure that the message has not been tampered with and is from the intended sender, digital signatures or HMAC (Hash-based Message Authentication Code) can be used.
Digital Signatures
A digital signature is a cryptographic value that is calculated from the data and a private key. The sender signs the message with their private key, and the recipient verifies the signature with the sender’s public key. This ensures the integrity and authenticity of the message.
HMAC
HMAC combines a cryptographic hash function with a secret key. It produces a unique message digest that can be used to verify the integrity and authenticity of the message.
WhatsApp's Implementation of End-to-End Encryption
WhatsApp uses the Signal Protocol, which builds upon the Diffie-Hellman algorithm, to provide end-to-end encryption. Here’s a detailed look at its implementation:
Key Generation and Storage
When you install WhatsApp and register your phone number, it generates a pair of public and private keys for each user. The public key is registered with WhatsApp servers, while the private key remains on the user’s device.
PreKeys
WhatsApp also generates a set of ephemeral keys called "prekeys" that are used for establishing sessions with new contacts without requiring the user to be online. These prekeys are stored on the server.
Session Establishment
When you start a chat with someone, WhatsApp retrieves the recipient’s public key from the server and uses it to establish a secure session using the Extended Triple Diffie-Hellman (X3DH) protocol.
X3DH Protocol
The X3DH protocol involves multiple rounds of key exchanges to ensure forward secrecy and to establish a session key. Forward secrecy ensures that even if a key is compromised, past communications remain secure. The protocol uses a combination of long-term public keys, ephemeral public keys, and signed prekeys to establish the session.
Message Encryption and Decryption
Each message sent in a session is encrypted using a unique session key derived from the shared secret established during the session setup.
Double Ratchet Algorithm
WhatsApp uses the Double Ratchet algorithm to provide continuous forward secrecy and post-compromise security. The Double Ratchet algorithm updates the session key with every message sent and received. This ensures that even if a session key is compromised, future messages remain secure.
Encryption Process
Messages are encrypted using AES256 in CBC (Cipher Block Chaining) mode and authenticated with HMAC-SHA256. Each message includes a message key and a nonce (a number used once) to ensure unique encryption for each message. The encrypted message is transmitted over the network. Only the recipient’s private key can decrypt the message.
Key Rotation
To enhance security, WhatsApp regularly rotates the encryption keys used for a session. This ensures that a compromised key cannot decrypt past messages, maintaining the security of the communication.
Facebook's Acquisition and Monetization of WhatsApp
In 2014, Facebook acquired WhatsApp for approximately $19 billion, aiming to expand its presence in the rapidly growing mobile messaging market. Despite WhatsApp’s commitment to privacy and its E2EE features, Facebook has devised monetization strategies that leverage the platform’s extensive user base.
Metadata Collection
Although messages are end-to-end encrypted and unreadable by Facebook, WhatsApp collects metadata such as:
Contact lists
Time stamps of messages
Frequency of communication
Device information
Location data (if shared)
This metadata can be used to build user profiles and improve the overall service. It can also be valuable for Facebook’s advertising algorithms on its other platforms, helping to deliver targeted ads.
User Data Integration
Facebook’s plans to integrate its messaging platforms (Messenger, Instagram Direct, and WhatsApp) aim to create a unified communication infrastructure. This integration could lead to new monetization opportunities through cross-platform services and features.
WhatsApp Business API
The WhatsApp Business API allows businesses to communicate with customers for notifications, customer service, and other interactions. Businesses pay for messages sent through the API, particularly those not responded to within 24 hours. This creates a revenue stream for WhatsApp without displaying ads to users.
WhatsApp Pay
WhatsApp offers a peer-to-peer payment service in some regions. This service allows users to send and receive money directly through the app. While not a major revenue source yet, it has significant growth potential as digital payments become more popular.
Implications for Users: Privacy Concerns and Data Exploitation
While end-to-end encryption ensures that messages are secure and private, the collection of metadata by WhatsApp poses significant privacy concerns. Metadata can reveal patterns in communication, user behavior, and other sensitive information, which can be used for targeted advertising and other purposes.
Privacy Concerns
Metadata can be used to infer personal details, such as social relationships, habits, and preferences. This can be used to build detailed profiles on users, even without accessing the content of their messages. The collection and exploitation of this data raise significant privacy concerns, especially when handled by large corporations with extensive advertising networks.
Regulatory Scrutiny
The practice of collecting and using metadata has faced significant scrutiny from privacy advocates and regulatory bodies. There have been calls for greater transparency and stricter regulations to protect user privacy. The General Data Protection Regulation (GDPR) in the European Union, for instance, mandates strict guidelines on data collection, usage, and consent.
User Awareness
Users need to be aware of the data being collected and how it is used. It is important to understand the trade-offs between using free services and the privacy implications of data collection. Awareness campaigns and privacy education can empower users to make informed decisions about their digital communication practices.
The Real Cost of Free Services:
The adage "if you are not paying for the product, you are the product" underscores the reality of free digital services. Companies like Facebook monetize user data, even when providing seemingly free services like WhatsApp. This data, particularly metadata, becomes a valuable asset in the digital advertising ecosystem.
The Value of Data
User data, especially detailed metadata, is incredibly valuable in the advertising industry. It allows companies to:
Deliver highly targeted advertisements
Track and analyze user behavior
Develop personalized marketing strategies
Improve product offerings and user experience
The Danger of Data in the Wrong Hands
While data can drive innovation and personalized services, it also poses significant risks if misused or mishandled. In the wrong hands, detailed user profiles can lead to:
Privacy breaches
Identity theft
Unethical manipulation of behavior
Discrimination based on inferred characteristics
The potential for misuse underscores the need for robust data protection measures and ethical data practices.
Conclusion
End-to-end encryption provides robust security for user communication, protecting messages from eavesdroppers and even the service provider. WhatsApp’s implementation of E2EE using the Signal Protocol exemplifies state-of-the-art cryptographic practices. However, Facebook’s acquisition of WhatsApp and its monetization strategies highlight the importance of understanding the broader implications of data privacy, especially concerning metadata collection and usage. Users must remain vigilant about how their data is used and advocate for stronger privacy protections in digital communication.
As we navigate the digital landscape, it is crucial to recognize the true cost of free services. While end-to-end encryption safeguards our messages, the collection and exploitation of metadata remain a significant concern. By staying informed and advocating for privacy rights, we can ensure that our digital communication remains secure and private in an increasingly interconnected world.
References
By understanding the mechanics of end-to-end encryption and the implications of data collection, users can better navigate the digital world and protect their privacy.
If you wanna discuss building a product that respects user's privacy or you want to know more about how your data is being handled by the software you use, in general, then feel free to visit me at AhmadWKhan.com.
Subscribe to my newsletter
Read articles from Ahmad W Khan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
